Access Control
Cognitive Sensing Innovation Comparison Of Cognitive Radio Access Paradigms Infographics PDF

Data Preparation Process Step 2 Discover And Access Data Topics PDF
This slide shows the second step that is involved in the data preparation process i.e. discover and access data along with the details.This is a Data Preparation Process Step 2 Discover And Access Data Topics PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Important To Discover, Collection Of Datasets, Data And Learning You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Empowering Organization With Zero Trust Network Access Topics PDF
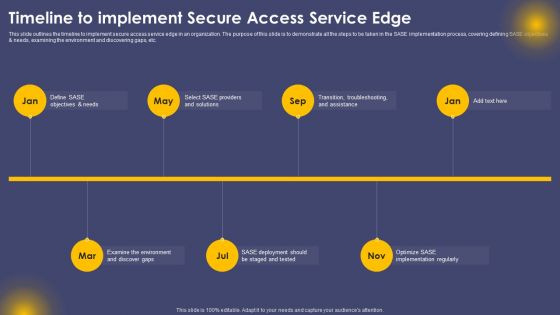
Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF
This slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Find highly impressive Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.
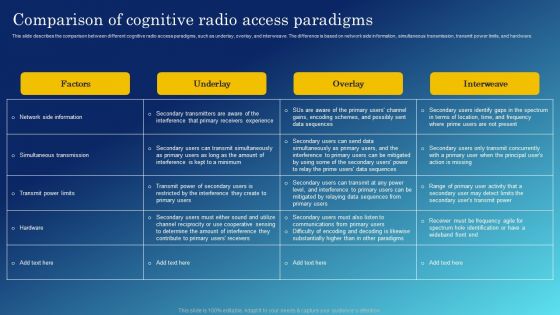
Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF
This slide describes the comparison between different cognitive radio access paradigms, such as underlay, overlay, and interweave. The difference is based on network side information, simultaneous transmission, transmit power limits, and hardware. Get a simple yet stunning designed Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF today and make your presentation stand out from the rest.

Security KPI Dashboard To Manage User Access Ppt Infographic Template Graphics Pictures PDF
Pitch your topic with ease and precision using this Security KPI Dashboard To Manage User Access Ppt Infographic Template Graphics Pictures PDF. This layout presents information on Devices, Security KPI Dashboard, Workspace. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
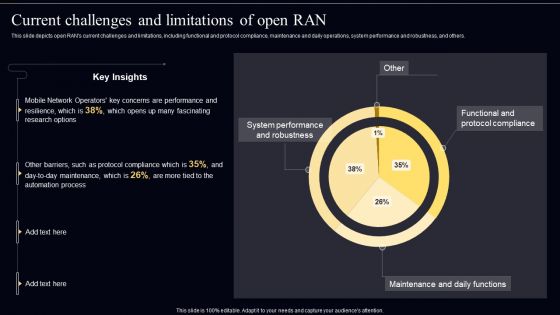
Open Radio Access Network IT Current Challenges And Limitations Of Open Ran Sample PDF
This slide depicts open RANs current challenges and limitations, including functional and protocol compliance, maintenance and daily operations, system performance and robustness, and others. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Open Radio Access Network IT Current Challenges And Limitations Of Open Ran Sample PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Open Radio Access Network IT Current Challenges And Limitations Of Open Ran Sample PDF.

Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Get a simple yet stunning designed Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
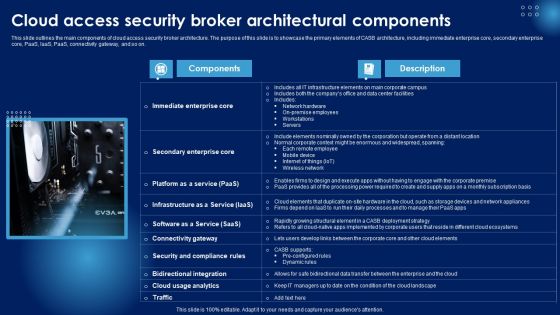
Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Get a simple yet stunning designed Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
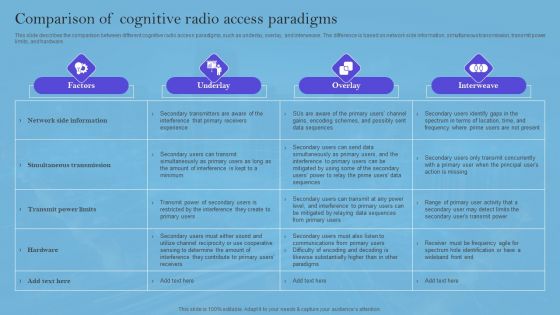
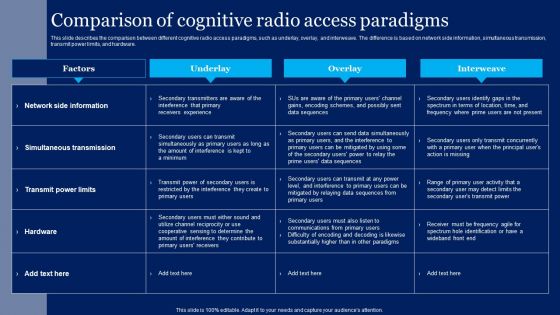
Smart Wireless Sensor Networks Comparison Of Cognitive Radio Access Paradigms Microsoft PDF
This slide describes the comparison between different cognitive radio access paradigms, such as underlay, overlay, and interweave. The difference is based on network side information, simultaneous transmission, transmit power limits, and hardware. Take your projects to the next level with our ultimate collection of Smart Wireless Sensor Networks Comparison Of Cognitive Radio Access Paradigms Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
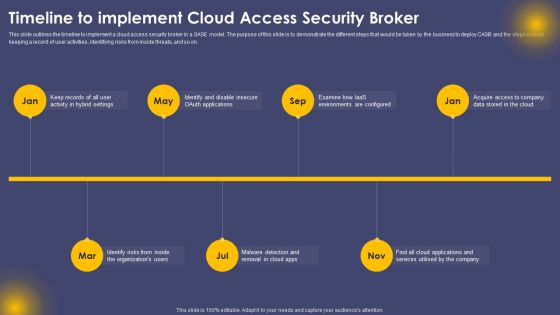
Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Development Guide For 5G World Determine Fixed Wireless Access FWA Offerings For Operators Pictures PDF
This slide provides details regarding fixed wireless access FWA offerings for operators. If you are looking for a format to display your unique thoughts, then the professionally designed Development Guide For 5G World Determine Fixed Wireless Access FWA Offerings For Operators Pictures PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Development Guide For 5G World Determine Fixed Wireless Access FWA Offerings For Operators Pictures PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Open Radio Access Network IT Three Main Pillars Of Open RAN Information PDF
This slide depicts the three main pillars of open random access networks, including O-RAN, virtual RAN, and centralized or cloud RAN. Open RAN refers to many techniques that telecom operators anticipate will overcome vendor lock in. Find highly impressive Open Radio Access Network IT Three Main Pillars Of Open RAN Information PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Open Radio Access Network IT Three Main Pillars Of Open RAN Information PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
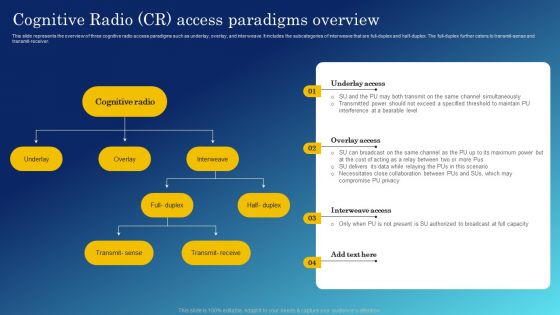
Cognitive Sensing Innovation Cognitive Radio CR Access Paradigms Overview Professional PDF
Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF
This slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
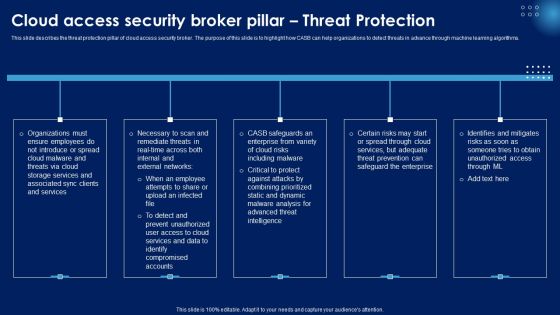
Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
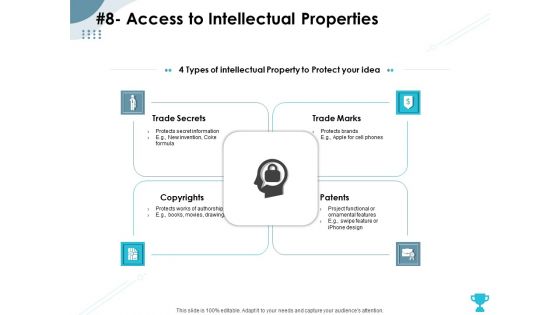
Strategies Take Your Retail Business Ahead Competition 8 Access To Intellectual Properties Rules PDF
Presenting this set of slides with name strategies take your retail business ahead competition 8 access to intellectual properties rules pdf. This is a four stage process. The stages in this process are trade marks, patents, copyrights, trade secrets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
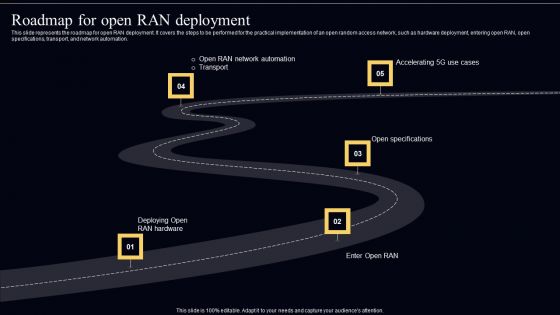
Open Radio Access Network IT Roadmap For Open RAN Deployment Topics PDF
This slide represents the roadmap for open RAN deployment. It covers the steps to be performed for the practical implementation of an open random access network, such as hardware deployment, entering open RAN, open specifications, transport, and network automation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Open Radio Access Network IT Roadmap For Open RAN Deployment Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Open Radio Access Network IT Timeline For Open RAN Deployment Themes PDF
This slide represents the timeline for open random access network deployment, including the steps to be performed to effectively implement open RAN, such as hardware deployment, entering open RAN, open specifications, transport, and network automation. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Open Radio Access Network IT Timeline For Open RAN Deployment Themes PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Document Encryption File Access Vector Icon Ppt PowerPoint Presentation Inspiration Guidelines
Presenting this set of slides with name document encryption file access vector icon ppt powerpoint presentation inspiration guidelines. This is a one stage process. The stages in this process are market asses, strategic market, business. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Projected Access Documents With Key Vector Icon Ppt PowerPoint Presentation Model Samples
Presenting this set of slides with name projected access documents with key vector icon ppt powerpoint presentation model samples. This is a one stage process. The stages in this process are market asses, strategic market, business. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Market Access With Research And Planning Ppt PowerPoint Presentation Icon Graphics Download
Presenting this set of slides with name market access with research and planning ppt powerpoint presentation icon graphics download. This is a eight stage process. The stages in this process are development, strategy, research. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Present like a pro with Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Initiatives For Identity And Access Management Development Plan Six Months Roadmap Elements
Presenting our jaw-dropping initiatives for identity and access management development plan six months roadmap elements. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
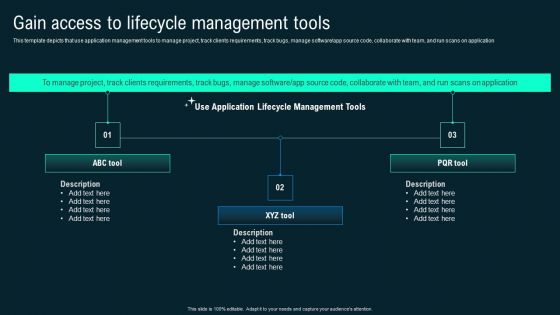
Gain Access To Lifecycle Management Tools Business Application Development Playbook Microsoft PDF
This template depicts that use application management tools to manage project, track clients requirements, track bugs, manage software app source code, collaborate with team, and run scans on application.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Gain Access To Lifecycle Management Tools Business Application Development Playbook Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Gain Access To Lifecycle Management Tools Business Application Development Playbook Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
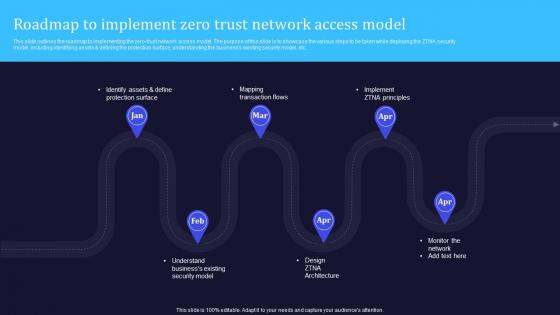
A20 Zero Trust Model Roadmap To Implement Zero Trust Network Access
This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the businesss existing security model, etc. Find a pre-designed and impeccable A20 Zero Trust Model Roadmap To Implement Zero Trust Network Access. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Boost your pitch with our creative Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF.
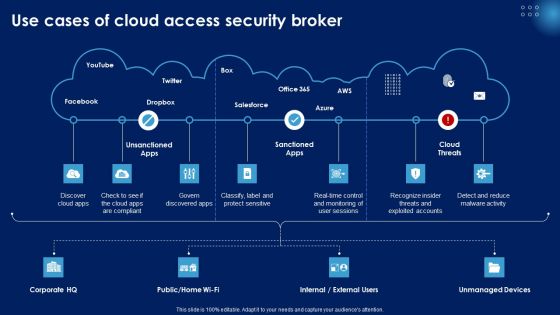
Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF
Find highly impressive Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF today and make your presentation stand out from the rest.
Key Stages For Project Intake Workflow With Discover And Access Ppt PowerPoint Presentation Gallery Icons PDF
Presenting key stages for project intake workflow with discover and access ppt powerpoint presentation gallery icons pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover, assess, plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
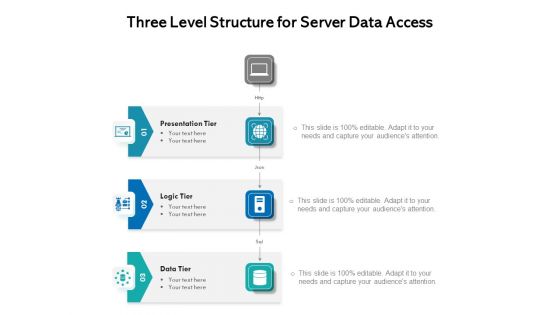
Three Level Structure For Server Data Access Ppt PowerPoint Presentation Gallery Layouts PDF
Presenting three level structure for server data access ppt powerpoint presentation gallery layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including presentation tier, logic tier, data tier. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Training To Access And Manage Google Cloud Google Cloud Computing System Portrait PDF
This slide depicts the Google Cloud training program, including trainer name, schedule, cost, and participant employee names.Deliver an awe inspiring pitch with this creative Training To Access And Manage Google Cloud Google Cloud Computing System Portrait PDF bundle. Topics like Google Cloud, Introduction, Google Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
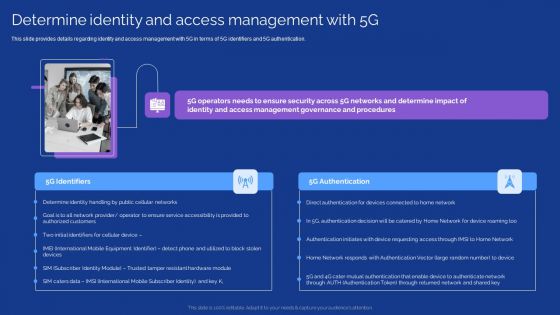
Development Guide For 5G World Determine Identity And Access Management With 5G Ideas PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. Slidegeeks is here to make your presentations a breeze with Development Guide For 5G World Determine Identity And Access Management With 5G Ideas PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
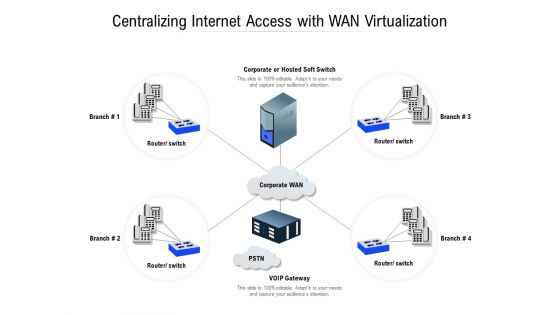
Centralizing Internet Access With WAN Virtualization Ppt PowerPoint Presentation Professional Inspiration
Presenting this set of slides with name centralizing internet access with wan virtualization ppt powerpoint presentation professional inspiration. This is a four stage process. The stages in this process are router, switch, voip gateway, branch, corporate, hosted soft switch, corporate wan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Action Plan Gain Competitive Advantage Access To Intellectual Properties Ppt Gallery Design Ideas PDF
Presenting this set of slides with name action plan gain competitive advantage access to intellectual properties ppt gallery design ideas pdf. This is a four stage process. The stages in this process are trade secrets, trade marks, patents, copyrights. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Initiatives To Build Identity And Access Management Development Plan Four Quarter Roadmap Clipart
Presenting our innovatively-structured initiatives to build identity and access management development plan four quarter roadmap clipart Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Successful Initiatives To Identity And Access Management Development Plan Four Quarter Roadmap Infographics
Presenting our innovatively-structured successful initiatives to identity and access management development plan four quarter roadmap infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Initiatives For Identity And Access Management Development Plan Development Plan Half Yearly Roadmap Rules
Presenting our innovatively-structured initiatives for identity and access management development plan development plan half yearly roadmap rules Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
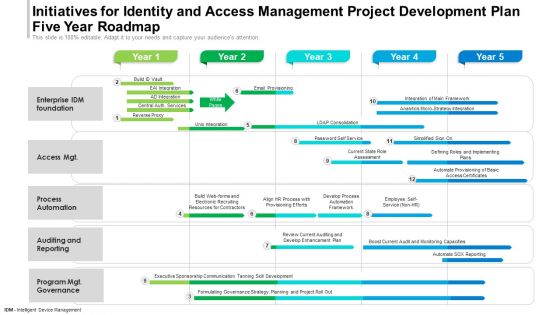
Initiatives For Identity And Access Management Project Development Plan Five Year Roadmap Summary
Presenting our innovatively-structured initiatives for identity and access management project development plan five year roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Components Of Brand Portfolio Strategy For Better Access To New Markets And Consumers Information PDF
This slide covers the fundamental principles of creating an effective brand communication strategy. It includes guidelines such as building and leveraging strong corporate bonds, defining strategic objectives for brands, employing simple and clear brand architecture, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Components Of Brand Portfolio Strategy For Better Access To New Markets And Consumers Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Components Of Brand Portfolio Strategy For Better Access To New Markets And Consumers Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Components Of Brand Portfolio Strategy For Better Access To New Markets And Consumers Formats PDF
This slide covers the fundamental principles of creating an effective brand communication strategy. It includes guidelines such as building and leveraging strong corporate bonds, defining strategic objectives for brands, employing simple and clear brand architecture, etc. This Components Of Brand Portfolio Strategy For Better Access To New Markets And Consumers Formats PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Components Of Brand Portfolio Strategy For Better Access To New Markets And Consumers Formats PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today

Initiatives For Identity And Access Management Development Plan Five Year Roadmap Ideas
Introducing our initiatives for identity and access management development plan five year roadmap ideas. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Key Factors To Identify And Access Management Technique Strategy Elements PDF
This slide shows essential factors of IAM strategy. The purpose of this slide is to highlight essential activities for implementing IAM strategy model. It include factors such as authentication, authorization and user management , etc Persuade your audience using this Key Factors To Identify And Access Management Technique Strategy Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Management, Repository. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
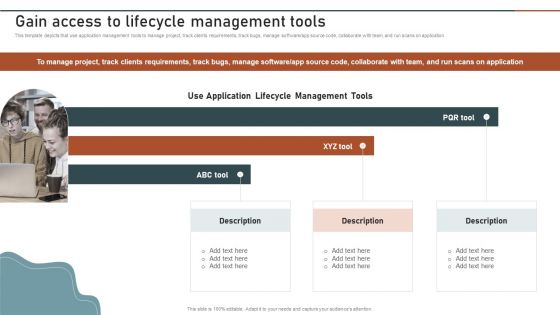
Enterprise Software Application Gain Access To Lifecycle Management Tools Infographics PDF
This template depicts that use application management tools to manage project, track clients requirements, track bugs, manage software or app source code, collaborate with team, and run scans on application. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Enterprise Software Application Gain Access To Lifecycle Management Tools Infographics PDF can be your best option for delivering a presentation. Represent everything in detail using Enterprise Software Application Gain Access To Lifecycle Management Tools Infographics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Identity Access Management Capability Maturity Model Ppt PowerPoint Presentation Ideas File Formats Cpb
Presenting this set of slides with name identity access management capability maturity model ppt powerpoint presentation ideas file formats cpb. This is an editable Powerpoint six stages graphic that deals with topics like identifying emerging risks to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Reasons For Increase In Demand Of Identify And Access Management Technique Sample PDF
This slide shows business drivers for increasing demand of IAM strategy. The purpose of this strategy is to highlight reasons for increasing usage of IAM strategy. It include drivers such as merger and acquisitions and security system breaches, etc. Presenting Reasons For Increase In Demand Of Identify And Access Management Technique Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security System Breaches, Regulatory System Expectations, Limited Budget Amount. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Slidegeeks is here to make your presentations a breeze with Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
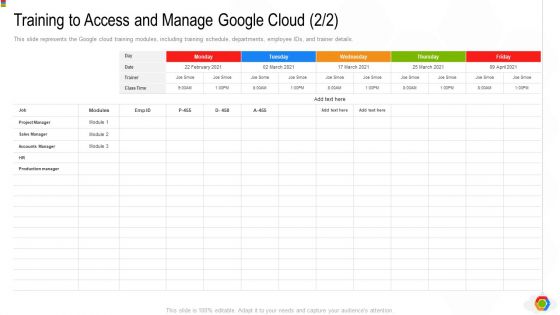
Google Cloud Console IT Training To Access And Manage Google Cloud Sales Ppt Styles Clipart PDF
This slide represents the Google cloud training modules, including training schedule, departments, employee IDs, and trainer details. Deliver and pitch your topic in the best possible manner with this google cloud console it training to access and manage google cloud sales ppt styles clipart pdf. Use them to share invaluable insights on project manager, sales manager, accounts manager, trainer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
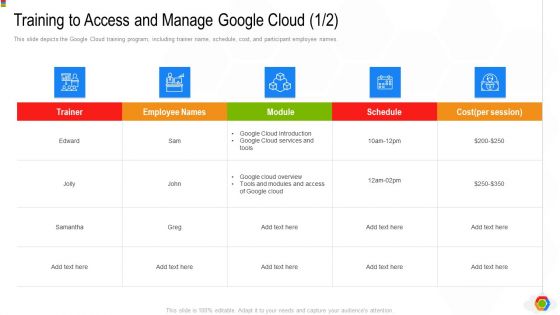
Google Cloud Console IT Training To Access And Manage Google Cloud Cost Ppt Ideas Guide PDF
This slide depicts the Google Cloud training program, including trainer name, schedule, cost, and participant employee names. Deliver an awe inspiring pitch with this creative google cloud console it training to access and manage google cloud cost ppt ideas guide pdf bundle. Topics like trainer, cost, cloud services, module, schedule can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF
This slide depicts the risk based approach of open RAN to cybersecurity. The O RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O RAN systems cyber resilience. Get a simple yet stunning designed Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
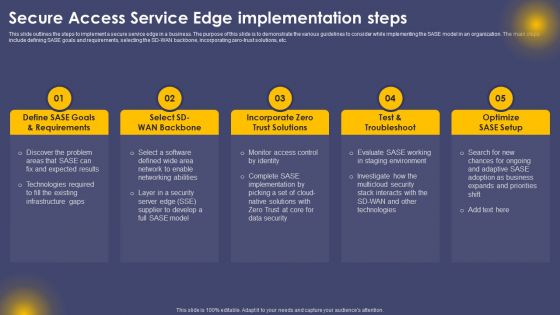
Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF
This slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Get a simple yet stunning designed Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Uplift Capital Raising Pitch Deck Remote Access To Live Coaching And Training Ideas PDF
The following slide highlights the platform which allows athletes to have access coaching and training at remote locations. Slidegeeks is here to make your presentations a breeze with Uplift Capital Raising Pitch Deck Remote Access To Live Coaching And Training Ideas PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
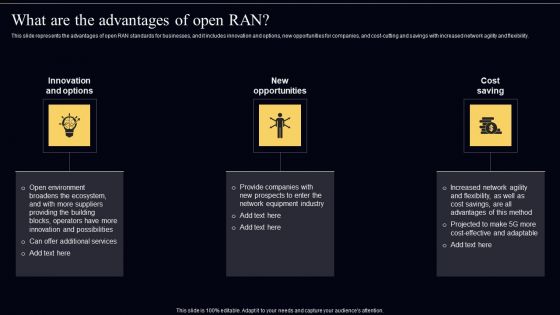
Open Radio Access Network IT What Are The Advantages Of Open RAN Mockup PDF
This slide represents the advantages of open RAN standards for businesses, and it includes innovation and options, new opportunities for companies, and cost cutting and savings with increased network agility and flexibility. Explore a selection of the finest Open Radio Access Network IT What Are The Advantages Of Open RAN Mockup PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Open Radio Access Network IT What Are The Advantages Of Open RAN Mockup PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
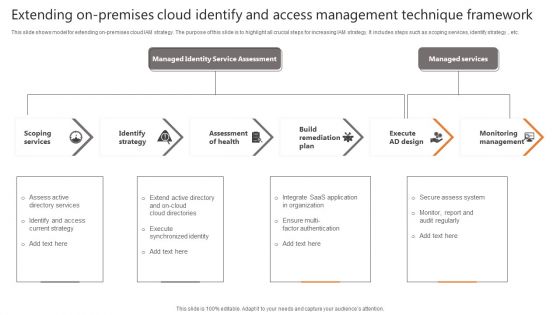
Extending On-Premises Cloud Identify And Access Management Technique Framework Formats PDF
This slide shows model for extending on-premises cloud IAM strategy. The purpose of this slide is to highlight all crucial steps for increasing IAM strategy. It includes steps such as scoping services, identify strategy , etc. Persuade your audience using this Cloud-Based Identify And Access Management Technique Best Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Scoping Services, Identify Strategy, Assessment Of Health. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home