Access Control

Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Zero Trust Model Top Tenets Of Zero Trust Network Access Model
Find highly impressive Zero Trust Model Top Tenets Of Zero Trust Network Access Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Top Tenets Of Zero Trust Network Access Mode for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP
Find highly impressive Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
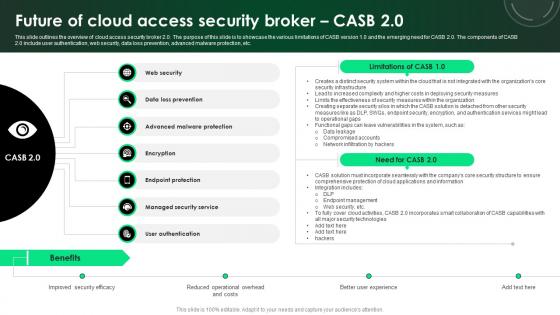
CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0 for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
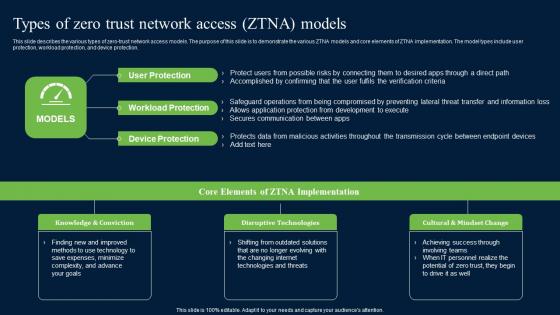
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
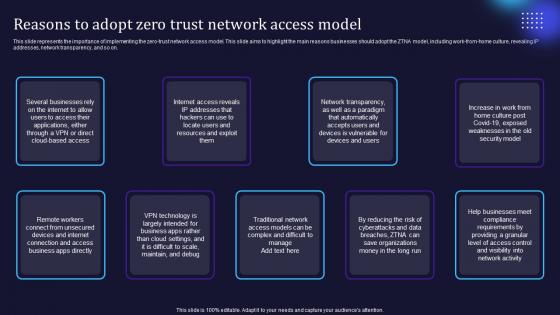
Zero Trust Model Reasons To Adopt Zero Trust Network Access Model
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Do you know about Slidesgeeks Zero Trust Model Reasons To Adopt Zero Trust Network Access Model These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Gain Access To Lifecycle Design And Develop Customized Software Guides Template Pdf
This template depicts that use application management tools to manage project, track clients requirements, track bugs, manage software app source code, collaborate with team, and run scans on application Make sure to capture your audiences attention in your business displays with our gratis customizable Gain Access To Lifecycle Design And Develop Customized Software Guides Template Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
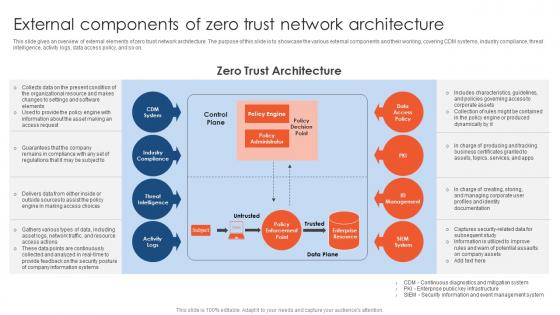
Zero Trust Network Access External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Retrieve professionally designed Zero Trust Network Access External Components Of Zero Trust Network Architecture to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
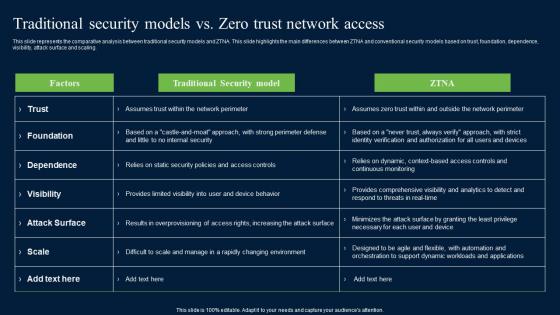
Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Right Of Access To Private Land Ppt PowerPoint Presentation Pictures Ideas
This is a right of access to private land ppt powerpoint presentation pictures ideas. This is a three stage process. The stages in this process are access rights, access management, business.

Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Types Of Zero Trust Network Access Ztna Models Software Defined Perimeter SDP
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Zero Trust Network Access Ztna Models Software Defined Perimeter SDP. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP.
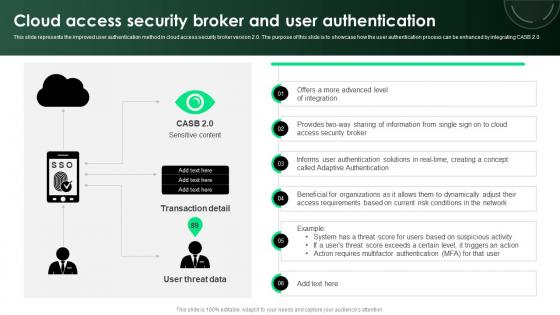
CASB 2 0 IT Cloud Access Security Broker And User Authentication
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Cloud Access Security Broker And User Authentication to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

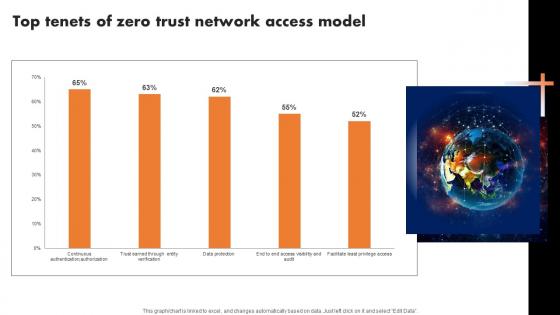
Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf today and make your presentation stand out from the rest

On Ramp Option 2 Applications And Data Zero Trust Network Access
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks is here to make your presentations a breeze with On Ramp Option 2 Applications And Data Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
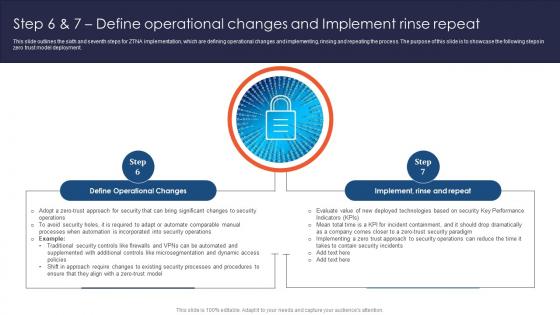
Zero Trust Network Access Step 6 And 7 Define Operational Changes And Implement Rinse Repeat
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Step 6 And 7 Define Operational Changes And Implement Rinse Repeat and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

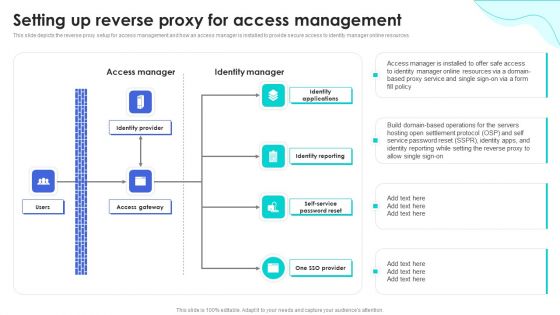
Setting Up Reverse Proxy For Access Management Reverse Proxy For Load Balancing Elements PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources.Deliver an awe inspiring pitch with this creative Setting Up Reverse Proxy For Access Management Reverse Proxy For Load Balancing Elements PDF bundle. Topics like Access Manager, Identity Manager, Identity Provider can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Zero Trust Network Access Ppt Powerpoint Presentation Complete Deck With Slides

Zero Trust Network Access Key Points To Choose Zero Trust Solution
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This Zero Trust Network Access Key Points To Choose Zero Trust Solution from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
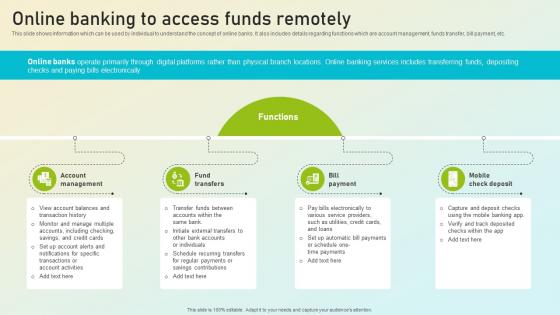
Beginners Guide To Commercial Online Banking To Access Funds Remotely Fin SS V
This slide shows information which can be used by individual to understand the concept of online banks. It also includes details regarding functions which are account management, funds transfer, bill payment, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Beginners Guide To Commercial Online Banking To Access Funds Remotely Fin SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Beginners Guide To Commercial Online Banking To Access Funds Remotely Fin SS V today and make your presentation stand out from the rest
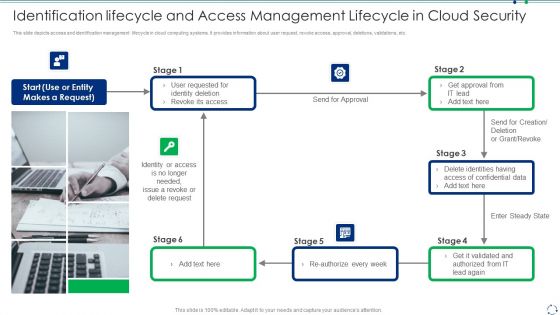
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
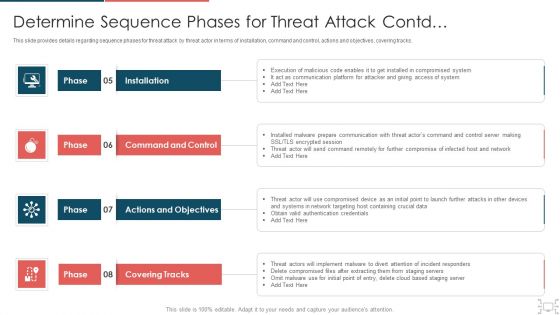
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Network Access Microsegmentation Overview And Working In ZTNA Model
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Find a pre-designed and impeccable Zero Trust Network Access Microsegmentation Overview And Working In ZTNA Model. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
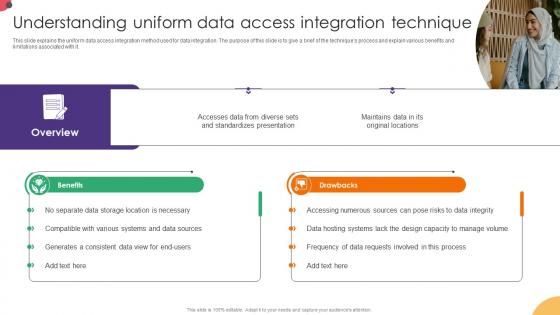
Understanding Uniform Data Access Integration Technique Data Integration Strategies For Business
This slide explains the uniform data access integration method used for data integration. The purpose of this slide is to give a brief of the techniques process and explain various benefits and limitations associated with it. This modern and well-arranged Understanding Uniform Data Access Integration Technique Data Integration Strategies For Business provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
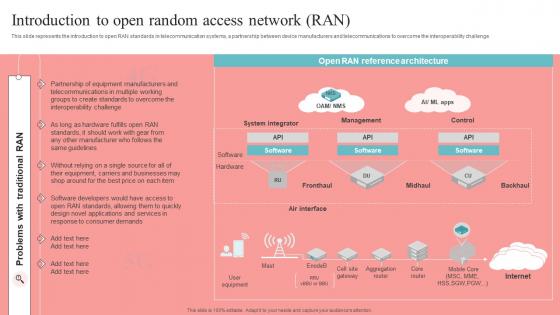
Introduction To Open Random Access Network Unlocking The Potential Of Open RAN Designs Pdf
This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Find highly impressive Introduction To Open Random Access Network Unlocking The Potential Of Open RAN Designs Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Introduction To Open Random Access Network Unlocking The Potential Of Open RAN Designs Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

CASB 2 0 IT Cloud Access Security Broker Pillar Data Security
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. The CASB 2 0 IT Cloud Access Security Broker Pillar Data Security is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
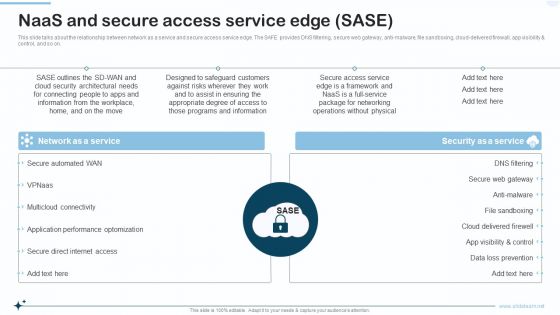
Naas Integrated Solution IT Naas And Secure Access Service Edge SASE Designs PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti malware, file sandboxing, cloud delivered firewall, app visibility and control, and so on. Presenting Naas Integrated Solution IT Naas And Secure Access Service Edge SASE Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Network As A Service, Security As A Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
6 Sigma Project Access Appraisal Management Capacity Management Ppt PowerPoint Presentation File Picture
This is a 6 sigma project access appraisal management capacity management ppt powerpoint presentation file picture. This is a six stage process. The stages in this process are 6 sigma project, access appraisal management, capacity management.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
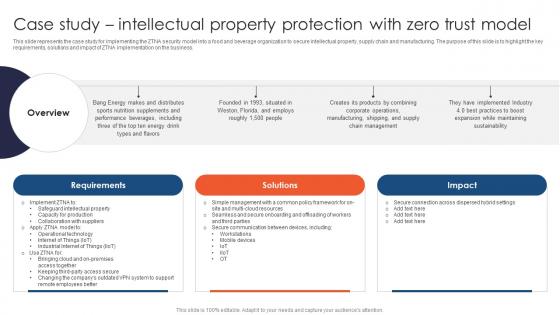
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Reverse Proxy Server IT Setting Up Reverse Proxy For Access Management Ppt Ideas Guide PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources. Presenting reverse proxy server it setting up reverse proxy for access management ppt ideas guide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like access manager, identity manager, identity applications, identity reporting, access gateway, identity provider. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
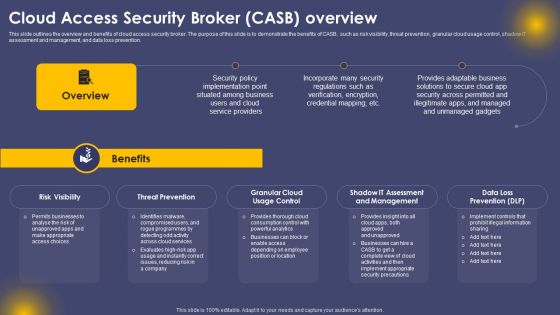
Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF today and make your presentation stand out from the rest.

Integrating Naas Service Model To Enhance Naas And Secure Access Service Edge Sase Mockup PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Integrating Naas Service Model To Enhance Naas And Secure Access Service Edge Sase Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Integrating Naas Service Model To Enhance Naas And Secure Access Service Edge Sase Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
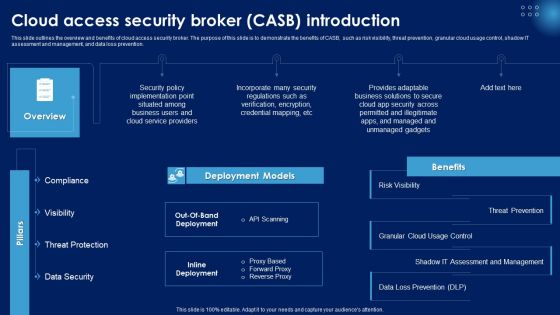
Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF.

Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF.
Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources. Create an editable Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
User Access And Validation Vector Icon Ppt Powerpoint Presentation Slides Slideshow
This is a user access and validation vector icon ppt powerpoint presentation slides slideshow. This is a four stage process. The stages in this process are password, access approval, authentication icon.
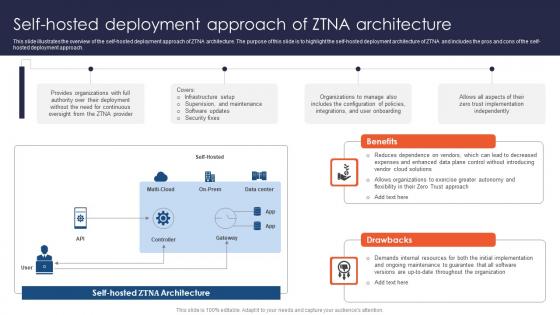
Zero Trust Network Access Self Hosted Deployment Approach Of ZTNA Architecture
This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Present like a pro with Zero Trust Network Access Self Hosted Deployment Approach Of ZTNA Architecture. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
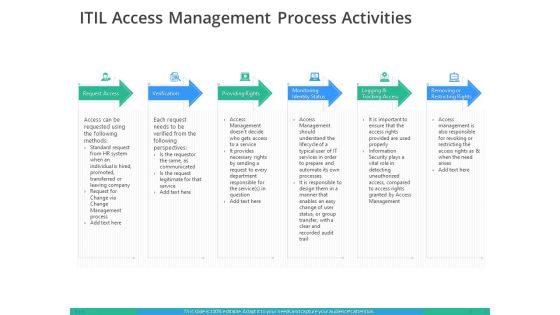
IT Infrastructure Library Permission Administration ITIL Access Management Process Activities Demonstration PDF
Deliver an awe-inspiring pitch with this creative it infrastructure library permission administration itil access management process activities demonstration pdf bundle. Topics like request access, verification, providing rights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Latest Key Trends Of Identify And Access Management Technique Clipart PDF
This slide shows current key trends of identification and access management strategy for automating business processes. It include trends such as high accessibility and user experience , etc. Persuade your audience using this Latest Key Trends Of Identify And Access Management Technique Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Accessibility Scope, Flexible Infrastructure, Hybrid Platform. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Integrating Naas Service Model Naas And Secure Access Service Edge Sase Ppt Model Picture PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. The Integrating Naas Service Model Naas And Secure Access Service Edge Sase Ppt Model Picture PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
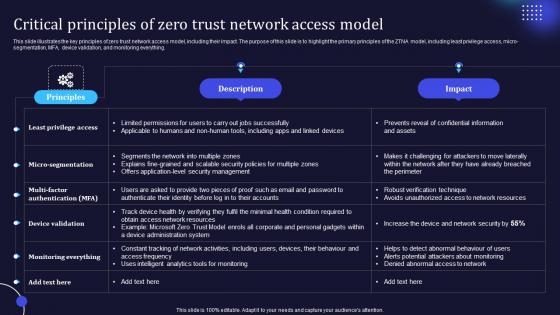
Zero Trust Model Critical Principles Of Zero Trust Network Access Model
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Critical Principles Of Zero Trust Network Access Model is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Critical Principles Of Zero Trust Network Access Model and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Firm Productivity Administration BI Design And Development Access Ppt PowerPoint Presentation Show Examples PDF
Presenting this set of slides with name firm productivity administration bi design and development access ppt powerpoint presentation show examples pdf. This is a four stage process. The stages in this process are web based access, component based architecture, service oriented architecture, ssl security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

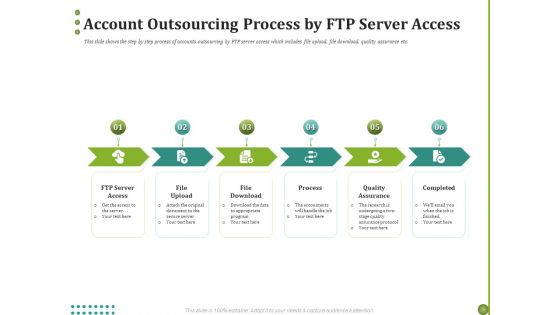
Managing CFO Services Account Outsourcing Process By FTP Server Access Ppt Styles Smartart PDF
Presenting this set of slides with name managing cfo services account outsourcing process by ftp server access ppt styles smartart pdf. This is a six stage process. The stages in this process are file upload, file download, completed, quality assurance, process, ftp server access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
BPO Managing Enterprise Financial Transactions Account Outsourcing Process By FTP Server Access Download PDF
Presenting this set of slides with name bpo managing enterprise financial transactions account outsourcing process by ftp server access download pdf. This is a six stage process. The stages in this process are server, access, process, quality, assurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Outsource Bookkeeping Service Manage Financial Transactions Account Outsourcing Process By FTP Server Access Clipart PDF
Presenting this set of slides with name outsource bookkeeping service manage financial transactions account outsourcing process by ftp server access clipart pdf. This is a six stage process. The stages in this process are server, access, process, quality, assurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Process Flow Of Business Operations Access Management Technical Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name process flow of business operations access management technical ppt powerpoint presentation complete deck. The topics discussed in these slides are access management, technical management, application management, facilities management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
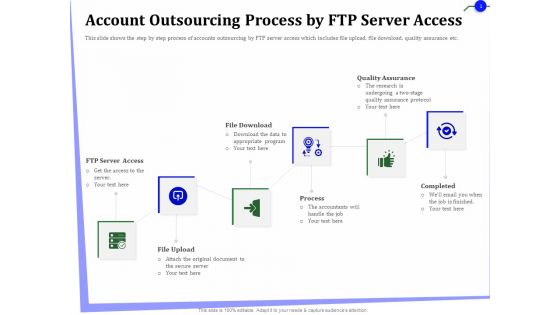
Outsourcing Of Finance And Accounting Processes Account Outsourcing Process By FTP Server Access Rules PDF
Presenting this set of slides with name outsourcing of finance and accounting processes account outsourcing process by ftp server access rules pdf. This is a six stage process. The stages in this process are server, access, process, quality, assurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Difference Identity Access Management Ppt PowerPoint Presentation Professional Design Inspiration Cpb
Presenting this set of slides with name difference identity access management ppt powerpoint presentation professional design inspiration cpb. This is a five stage process. The stages in this process are difference identity access management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
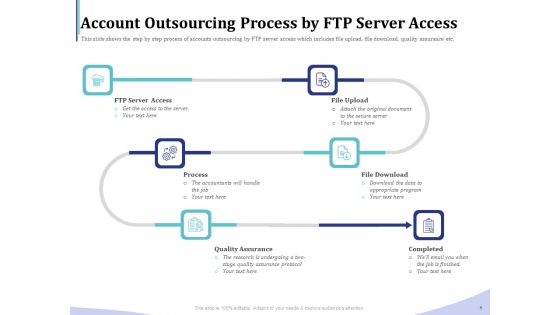
Accounting Bookkeeping Services Account Outsourcing Process By FTP Server Access Ppt Infographics Deck PDF
Presenting this set of slides with name accounting bookkeeping services account outsourcing process by ftp server access ppt infographics deck pdf. This is a six stage process. The stages in this process are server, access, process, quality, assurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategy To Be Adopted 3 Restrict Access To Physical Devices Ppt Infographic Template Mockup PDF
This is a strategy to be adopted 3 restrict access to physical devices ppt infographic template mockup pdf. template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategy to be adopted 3 restrict access to physical devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Evolution Architectural Technology Addressing 5G Era Spectrum Bands Access And Pricing Elements PDF
This slide provides details regarding various 5G era spectrum in terms of 5G spectrum bands, spectrum access and spectrum pricing. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Addressing 5G Era Spectrum Bands Access And Pricing Elements PDF Use them to share invaluable insights on Spectrum Bands, Spectrum Access, Spectrum Pricing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
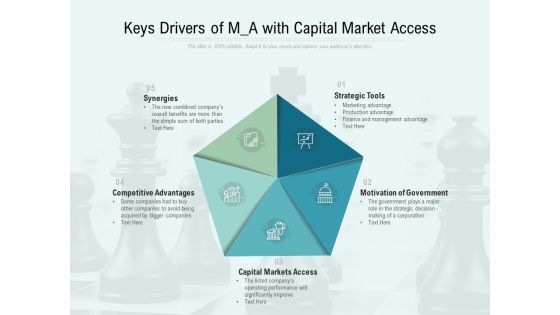
Keys Drivers Of M A With Capital Market Access Ppt PowerPoint Presentation Outline Layout
Presenting this set of slides with name keys drivers of m a with capital market access ppt powerpoint presentation outline layout. This is a five stage process. The stages in this process are strategic tools, motivation of government, capital markets access, competitive advantages, synergies. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Identify Groups For Distribution And Prepare For Test Group Access Graphics PDF
This template covers milestones for software or application testing phase such as Identify groups for distribution and Prepare for test group access.Deliver an awe inspiring pitch with this creative Identify Groups For Distribution And Prepare For Test Group Access Graphics PDF bundle. Topics like Quality Assurance, Functionality Testing, Accessibility Testing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hand Sign With Cross For Banned Access Ppt PowerPoint Presentation Inspiration Format PDF
Presenting this set of slides with name hand sign with cross for banned access ppt powerpoint presentation inspiration format pdf. The topics discussed in these slide is hand sign with cross for banned access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Wireless Network Security System To Prevent Unauthorized Access To Internet Elements PDF
Presenting wireless network security system to prevent unauthorized access to internet elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system to prevent unauthorized access to internet. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home