Access Control

IT Infrastructure Library Permission Administration Responsibility Matrix ITIL Access Management Rules PDF
Presenting it infrastructure library permission administration responsibility matrix itil access management rules pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like process, access manager, level support. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Be Adopted 3 Restrict Access To Physical Devices Guidelines PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 3 restrict access to physical devices guidelines pdf to provide visual cues and insights. Share and navigate important information on strategy to be adopted 3 restrict access to physical devices guidelines pdf stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 3 restrict access to physical devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Infrastructure Library Permission Administration ITIL Access Management Objectives Template PDF
This is a it infrastructure library permission administration itil access management objectives template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like manage access to services based on policies and actions elaborated in information security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security For Network Protection From Unauthorized Access Vector Icon Ppt PowerPoint Presentation File Summary PDF
Presenting this set of slides with name security for network protection from unauthorized access vector icon ppt powerpoint presentation file summary pdf. This is a three stage process. The stages in this process are security for network protection from unauthorized access vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vector Icon Showing Network Access Denial On Mobile Ppt PowerPoint Presentation Styles Grid PDF
Presenting this set of slides with name vector icon showing network access denial on mobile ppt powerpoint presentation styles grid pdf. This is a three stage process. The stages in this process are vector icon showing network access denial on mobile. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Layered Framework With Data Access Ppt PowerPoint Presentation File Format Ideas PDF
Presenting this set of slides with name layered framework with data access ppt powerpoint presentation file format ideas pdf. This is a three stage process. The stages in this process are data layer, data access layer, business layer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Approaches To Implement Zero Trust Network Access Ppt Layouts Shapes PDF
This slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Approaches To Implement Zero Trust Network Access Ppt Layouts Shapes PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Approaches To Implement Zero Trust Network Access Ppt Layouts Shapes PDF.
7 Petal Diagram For Access Of Remote Workers Ppt PowerPoint Presentation Icon Professional PDF
Presenting 7 petal diagram for access of remote workers ppt powerpoint presentation icon professional pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including 7 petal diagram for access of remote workers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Access Of Smart Door Vector Icon Ppt PowerPoint Presentation File Examples PDF
Presenting access of smart door vector icon ppt powerpoint presentation file examples pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including access of smart door vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Identity Access Management Architecture Ppt PowerPoint Presentation Outline Objects Cpb Pdf
Presenting this set of slides with name identity access management architecture ppt powerpoint presentation outline objects cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like identity access management architecture to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Five Stages Of Software Testing With Scanning And Maintaining Access Ppt PowerPoint Presentation Pictures Slides
Presenting this set of slides with name five stages of software testing with scanning and maintaining access ppt powerpoint presentation pictures slides. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Biometric Device For Security Access System Icon Ppt PowerPoint Presentation Ideas Picture PDF
Presenting biometric device for security access system icon ppt powerpoint presentation ideas picture pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including biometric device for security access system icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Access To Protect Cyber Threat System Ppt PowerPoint Presentation Visual Aids Diagrams PDF
Presenting security access to protect cyber threat system ppt powerpoint presentation visual aids diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including security access to protect cyber threat system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
procedure of record keeping system with ease of access ppt powerpoint presentation icon master slide
Presenting this set of slides with name procedure of record keeping system with ease of access ppt powerpoint presentation icon master slide. This is a four stage process. The stages in this process are records management policy, retention schedule, choose the right solution, ease of access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF today and make your presentation stand out from the rest.

User Access Management Process Ppt PowerPoint Presentation Summary Graphic Images Cpb
Presenting this set of slides with name user access management process ppt powerpoint presentation summary graphic images cpb. This is an editable Powerpoint six stages graphic that deals with topics like user access management process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
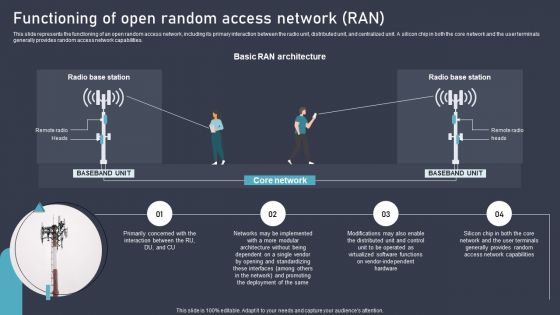
O RAN Architecture Functioning Of Open Random Access Network RAN Clipart PDF
This slide represents the functioning of an open random access network, including its primary interaction between the radio unit, distributed unit, and centralized unit. A silicon chip in both the core network and the user terminals generally provides random access network capabilities. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. O RAN Architecture Functioning Of Open Random Access Network RAN Clipart PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Lime Investor Fundraising Elevator Lime Electric Scooter Service Access Ppt Outline Slides PDF
Mentioned slide provides information about the company access covering details about the presence in low-income area, National PayNearMe collaboration and cash payments acceptability. Deliver and pitch your topic in the best possible manner with this lime investor fundraising elevator lime electric scooter service access ppt outline slides pdf. Use them to share invaluable insights on text based unlocking, national paynearme, cash payments accepted and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
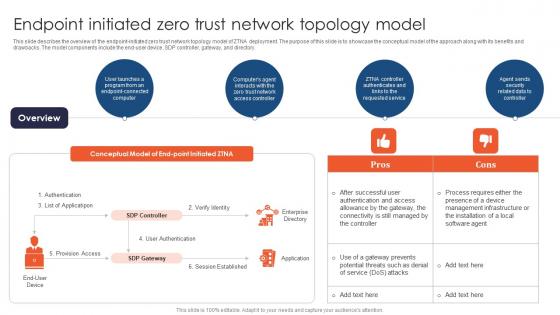
Endpoint Initiated Zero Trust Network Topology Model Zero Trust Network Access
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Endpoint Initiated Zero Trust Network Topology Model Zero Trust Network Access will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
CCTV Access On Mobile Phone Vector Icon Ppt PowerPoint Presentation Pictures Deck PDF
Presenting this set of slides with name cctv access on mobile phone vector icon ppt powerpoint presentation pictures deck pdf. This is a three stage process. The stages in this process are cctv access on mobile phone vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
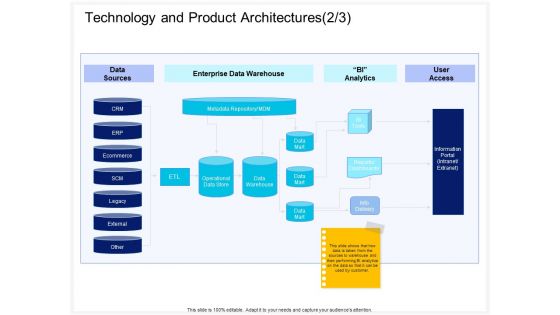
Enterprise Problem Solving And Intellect Technology And Product Architectures Access Summary PDF
Presenting this set of slides with name enterprise problem solving and intellect technology and product architectures access summary pdf. This is a one stage process. The stages in this process are data sources, enterprise data warehouse, bi analytics, user access, crm, erp, ecommerce, scm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Business Value Identity Access Management Ppt PowerPoint Presentation Model Professional Cpb
Presenting this set of slides with name business value identity access management ppt powerpoint presentation model professional cpb. This is an editable Powerpoint four stages graphic that deals with topics like business value identity access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Enterprise Identity Access Management Ppt PowerPoint Presentation Infographic Template Templates Cpb
Presenting this set of slides with name enterprise identity access management ppt powerpoint presentation infographic template templates cpb. This is an editable Powerpoint four stages graphic that deals with topics like enterprise identity access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Access Management Process Flow Ppt PowerPoint Presentation Professional Layout Ideas Cpb
Presenting this set of slides with name access management process flow ppt powerpoint presentation professional layout ideas cpb. This is an editable Powerpoint four stages graphic that deals with topics like access management process flow to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
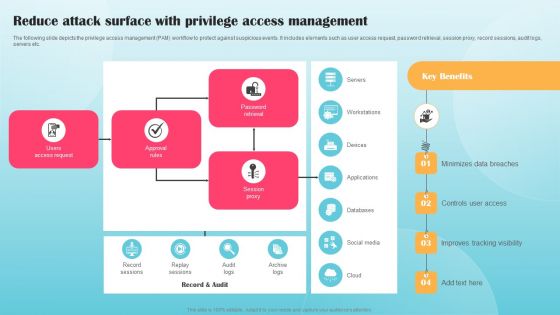
Reduce Attack Surface With Privilege Access Management Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Want to ace your presentation in front of a live audience Our Reduce Attack Surface With Privilege Access Management Ppt PowerPoint Presentation Diagram Graph Charts PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Identity Based Security Access Management Ppt PowerPoint Presentation Gallery Background Cpb
Presenting this set of slides with name identity based security access management ppt powerpoint presentation gallery background cpb. This is an editable Powerpoint five stages graphic that deals with topics like identity based security access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Initiatives For Identity And Access Management Project Development Plan Three Months Roadmap Formats
We present our initiatives for identity and access management project development plan three months roadmap formats. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched initiatives for identity and access management project development plan three months roadmap formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
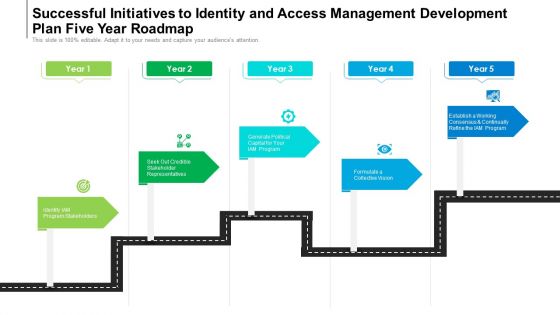
Successful Initiatives To Identity And Access Management Development Plan Five Year Roadmap Infographics
We present our successful initiatives to identity and access management development plan five year roadmap infographics. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched successful initiatives to identity and access management development plan five year roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Initiatives For Building Identity And Access Management Development Plan Five Year Roadmap Ideas
We present our initiatives for building identity and access management development plan five year roadmap ideas. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched initiatives for building identity and access management development plan five year roadmap ideas in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Initiatives For Identity And Access Management Development Plan Three Months Roadmap Introduction
We present our initiatives for identity and access management development plan three months roadmap introduction. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched initiatives for identity and access management development plan three months roadmap introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
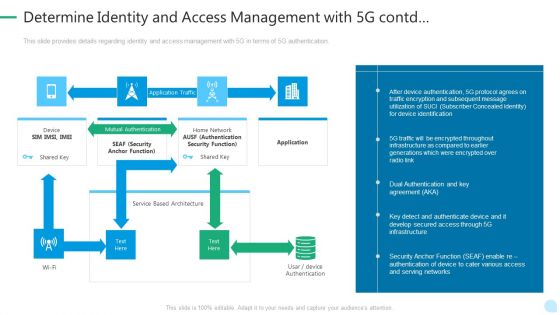
5G Network Technology Determine Identity And Access Management With 5G Contd Ppt Outline Background PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver an awe inspiring pitch with this creative 5g network technology determine identity and access management with 5g contd ppt outline background pdf bundle. Topics like security, develop, infrastructure, protocol can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Seven Stages Process Integration Access Discovery Reporting Delivery Ppt PowerPoint Presentation Portfolio Designs
This is a seven stages process integration access discovery reporting delivery ppt powerpoint presentation portfolio designs. This is a seven stage process. The stages in this process are process integration, integration of processes, integration of procedure.
File Sharing And Document Management Access Change Review Ppt PowerPoint Presentation Slides Icons
This is a file sharing and document management access change review ppt powerpoint presentation slides icons. This is a five stage process. The stages in this process are document review, document analysis, document evaluation.
Customer Authentication Process Flow Of Verification Factors For Safe Access Vector Icon Infographics PDF
Showcasing this set of slides titled customer authentication process flow of verification factors for safe access vector icon infographics pdf. The topics addressed in these templates are customer authentication process flow of verification factors for safe access vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
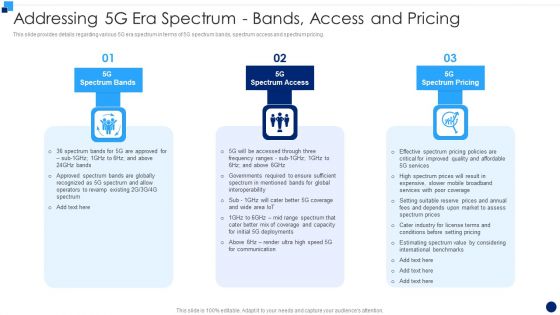
Developing 5G Wireless Cellular Network Addressing 5G Era Spectrum Bands Access And Pricing Sample PDF
This slide provides details regarding various 5G era spectrum in terms of 5G spectrum bands, spectrum access and spectrum pricing. This is a Developing 5G Wireless Cellular Network Addressing 5G Era Spectrum Bands Access And Pricing Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Spectrum Bands, Spectrum Access, Spectrum Pricing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
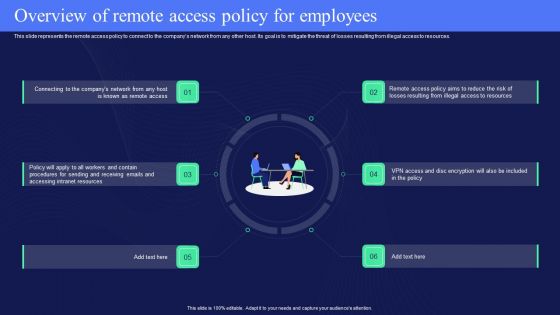
IT Policies And Procedures Overview Of Remote Access Policy For Employees Template PDF
This slide represents the remote access policy to connect to the companys network from any other host. Its goal is to mitigate the threat of losses resulting from illegal access to resources. Retrieve professionally designed IT Policies And Procedures Overview Of Remote Access Policy For Employees Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Customer Identity Access Management API Structure With Icons Ppt File Smartart PDF
This slide represents the CIAM API architecture for social media including elements like multifactor authentication, profile registration and update etc. Showcasing this set of slides titled customer identity access management api structure with icons ppt file smartart pdf. The topics addressed in these templates are data stores, client applications, multifactor authentication, access management, social media. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Office Door With Security Access Panel Image Ppt PowerPoint Presentation Icon Topics PDF
Persuade your audience using this office door with security access panel image ppt powerpoint presentation icon topics pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including office door with security access panel image. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

M Banking System Improving Consumer Percent Of Households That Have Access To Smartphones Mockup PDF
Following slide displays global stats about percent of households that have access to smartphones. Household characteristics covered in this slide are age and income. Deliver and pitch your topic in the best possible manner with this m banking system improving consumer percent of households that have access to smartphones mockup pdf. Use them to share invaluable insights on household characteristic, fully banked, household income and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Identity Access Management Challenges Ppt PowerPoint Presentation Show Graphic Tips Cpb
Presenting this set of slides with name identity access management challenges ppt powerpoint presentation show graphic tips cpb. This is an editable Powerpoint four stages graphic that deals with topics like identity access management challenges to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Cloud Computing Ppt PowerPoint Presentation Infographic Template Slide Cpb
Presenting this set of slides with name identity access management cloud computing ppt powerpoint presentation infographic template slide cpb. This is an editable Powerpoint four stages graphic that deals with topics like identity access management cloud computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Strategy Ppt PowerPoint Presentation Infographics Infographic Template Cpb
Presenting this set of slides with name identity access management strategy ppt powerpoint presentation infographics infographic template cpb. This is an editable Powerpoint five stages graphic that deals with topics like identity access management strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Identity Access Management Cloud Computing Ppt PowerPoint Presentation Infographic Template Tips Cpb Pdf
Presenting this set of slides with name identity access management cloud computing ppt powerpoint presentation infographic template tips cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like identity access management cloud computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Technologies Ppt PowerPoint Presentation Portfolio Good Cpb Pdf
Presenting this set of slides with name identity access management technologies ppt powerpoint presentation portfolio good cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like identity access management technologies to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Identity Access Management Governance Ppt PowerPoint Presentation Summary Images Cpb Pdf
Presenting this set of slides with name identity access management governance ppt powerpoint presentation summary images cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like identity access management governance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Strategy Ppt PowerPoint Presentation Professional Slide Portrait Cpb Pdf
Presenting this set of slides with name identity access management strategy ppt powerpoint presentation professional slide portrait cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like identity access management strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Open Access Key Lock Icon Ppt PowerPoint Presentation Portfolio Designs Download
This is a open access key lock icon ppt powerpoint presentation portfolio designs download. This is a three stage process. The stages in this process are computer software, operating system, open source.

5G Network Technology Addressing 5G Era Spectrum Bands Access And Pricing Ppt Outline Layout Ideas PDF
This slide provides details regarding various 5G era spectrum in terms of 5G spectrum bands, spectrum access and spectrum pricing. Presenting 5g network technology addressing 5g era spectrum bands access and pricing ppt outline layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 5g spectrum bands, 5g spectrum access, 5g spectrum pricing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
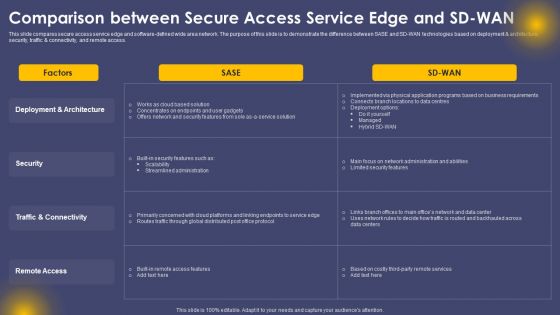
Comparison Between Secure Access Service Edge And Sd Wan Ppt Outline Guide PDF
This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Find a pre designed and impeccable Comparison Between Secure Access Service Edge And Sd Wan Ppt Outline Guide PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Big Data Security Model With Identity And Access Management Ppt PowerPoint Presentation Inspiration Good PDF
Pitch your topic with ease and precision using this big data security model with identity and access management ppt powerpoint presentation inspiration good pdf. This layout presents information on identity and access management, data protection and privacy, infrastructure security and integrity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

5G Evolution Architectural Technology Determine Identity And Access Management With 5G Contd Microsoft PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Determine Identity And Access Management With 5G Contd Microsoft PDF Use them to share invaluable insights on Uthentication, Security Function, Based Architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

How Does Cloud Security Work Identity And Access Management IAM Professional PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a How Does Cloud Security Work Identity And Access Management IAM Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Accessibility, Security, Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Presenting Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Accessibility, Knowledge, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Be Adopted 3 Restrict Access To Physical Devices Pictures PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 3 restrict access to physical devices pictures pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 3 restrict access to physical devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Open Radio Access Network IT Relationship Between Open RAN And Private 5G Themes PDF
This slide depicts the relationship between an open random access network and private 5G. With the help of an open random access network, many organizations would be able to adopt private 5G at lower costs. This Open Radio Access Network IT Relationship Between Open RAN And Private 5G Themes PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Open Radio Access Network IT Relationship Between Open RAN And Private 5G Themes PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
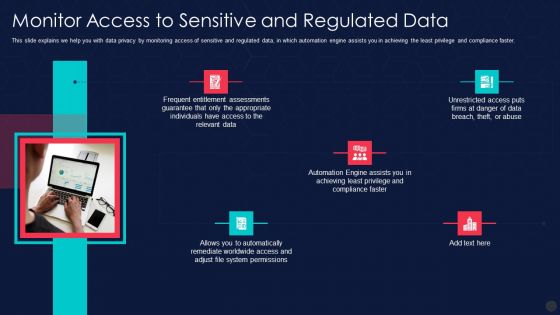
Information Privacy IT Monitor Access To Sensitive And Regulated Data Structure PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. This is a information privacy it monitor access to sensitive and regulated data structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitor access to sensitive and regulated data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
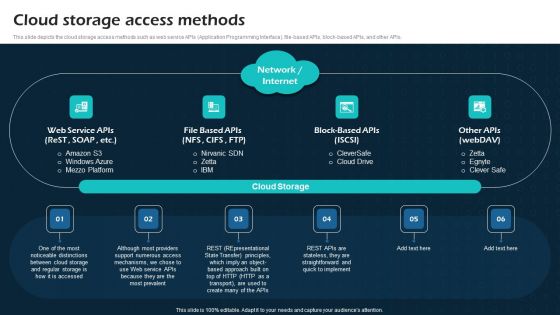
Cloud Storage Access Methods Virtual Cloud Network IT Ppt Styles Slide Download PDF
This slide depicts the cloud storage access methods such as web service APIs Application Programming Interface, file based APIs, block-based APIs, and other APIs. Presenting this PowerPoint presentation, titled Cloud Storage Access Methods Virtual Cloud Network IT Ppt Styles Slide Download PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Storage Access Methods Virtual Cloud Network IT Ppt Styles Slide Download PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Storage Access Methods Virtual Cloud Network IT Ppt Styles Slide Download PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
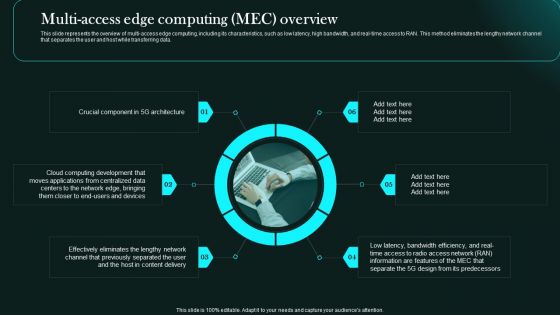
Multi Access Edge Computing Mec Overview 5G Network Functional Architecture Portrait PDF
This slide represents the overview of multi-access edge computing, including its characteristics, such as low latency, high bandwidth, and real-time access to RAN. This method eliminates the lengthy network channel that separates the user and host while transferring data.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Multi Access Edge Computing Mec Overview 5G Network Functional Architecture Portrait PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Multi Access Edge Computing Mec Overview 5G Network Functional Architecture Portrait PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
7 Petal Diagram For Cloud Access With Secure Authentication Ppt PowerPoint Presentation File Designs PDF
Persuade your audience using this 7 petal diagram for cloud access with secure authentication ppt powerpoint presentation file designs pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including 7 petal diagram for cloud access with secure authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home