Access Control
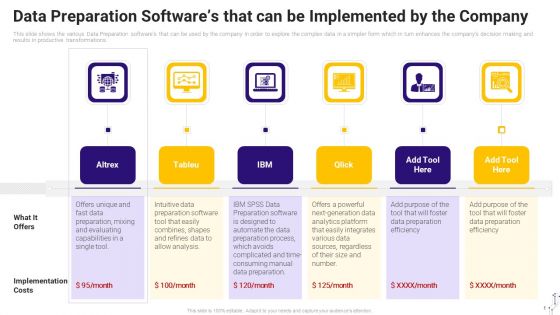
Effective Data Arrangement For Data Accessibility And Processing Readiness Data Preparation Softwares That Can Be Implemented Themes PDF
This slide shows the various Data Preparation softwares that can be used by the company in order to explore the complex data in a simpler form which in turn enhances the companys decision making and results in productive transformations. Presenting effective data arrangement for data accessibility and processing readiness data preparation softwares that can be implemented themes pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data preparation softwares that can be implemented by the company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective Data Arrangement For Data Accessibility And Processing Readiness Importance Of Data Preparation In The Company Demonstration PDF
This slide shows the importance of effective and efficient data preparation in the company such as to filter unstructured and disordered data, connect data from real-time multiple data sources, ensure quick and accurate reporting of data etc. This is a effective data arrangement for data accessibility and processing readiness importance of data preparation in the company demonstration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like importance of data preparation in the company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Data Arrangement For Data Accessibility And Processing Readiness Implementing Data Preprocessing Handling Missing Data Inspiration PDF
This slide shows the different methods that can be used to handle the missing data during the data preparation i.e. ignoring the missing record, filling the missing values manually and filling using This is a effective data arrangement for data accessibility and processing readiness implementing data preprocessing handling missing data inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ignoring the missing record, filling the missing values manually, filling using computed values. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Data Management To Make Information Accessible And Ready For Processing Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty six slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
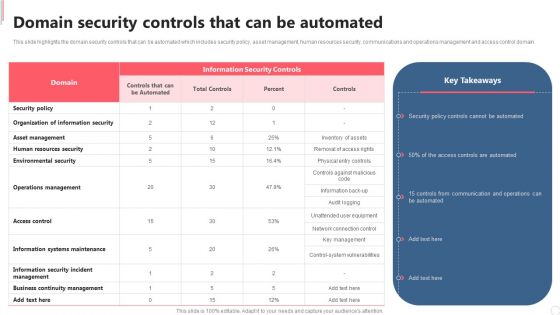
Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF.

Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain.Find highly impressive Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
Business Analyst Diagrams And Controlling PowerPoint Templates Backgrounds For Slide
We present our business analyst diagrams and controlling PowerPoint templates backgrounds for slide.Use our Circle Charts PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Download and present our Arrows PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience. Present our Business PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Present our Flow Charts PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire.Use these PowerPoint slides for presentations relating to Access, arrow, background, banner, blue, bright, business, chart, circle, concept, conceptual, connection, corporate, cycle, design, different, element, graphic, group, idea, illustration, part, process, shape, strategy, template, vector, web, website. The prominent colors used in the PowerPoint template are Green, Gray, White.
Business Analyst Diagrams And Controlling PowerPoint Templates Backgrounds For Slides
We present our business analyst diagrams and controlling PowerPoint templates backgrounds for slides.Download and present our Circle Charts PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Use our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Use our Process and Flows PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Flow Charts PowerPoint Templates because These PowerPoint Templates and Slides will give the updraft to your ideas. See them soar to great heights with ease.Use these PowerPoint slides for presentations relating to Access, arrow, background, banner, blue, bright, business, chart, circle, concept, conceptual, connection, corporate, cycle, design, different, element, graphic, group, idea, illustration, part, process, shape, strategy, template, vector, web, website. The prominent colors used in the PowerPoint template are Blue, Gray, Black.
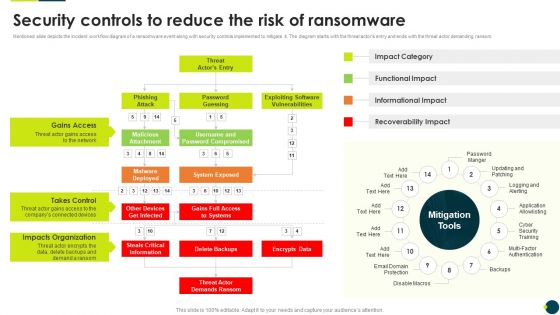
IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF bundle. Topics like Gains Access, Takes Control, Impacts Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

System Stack With User Interface And Host Controller Ppt PowerPoint Presentation Summary Show PDF
Presenting this set of slides with name system stack with user interface and host controller ppt powerpoint presentation summary show pdf. The topics discussed in these slides are application, access protocols, sdp, upper layer stack, lower layer stack, host controller, user interface, voice codec. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Controlling And Innovating Product Leader Responsibilities Addressing Product Discovery Initiatives Adopted Rules PDF
This slide provides information regarding product discovery initiatives adopted by team working remotely in terms of synchronous alignment, implementing central hub, accessible platform, etc. Presenting controlling and innovating product leader responsibilities addressing product discovery initiatives adopted rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like synchronous alignment, implementing central hub, accessible platform. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Controller Extension Cash Flow Management In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Controller Extension Cash Flow Management In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Controller Extension Cash Flow Management that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Methodologies For Developing SDN Ethane Evolution Of SDN Controllers Template Pdf
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. Retrieve professionally designed Methodologies For Developing SDN Ethane Evolution Of SDN Controllers Template Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
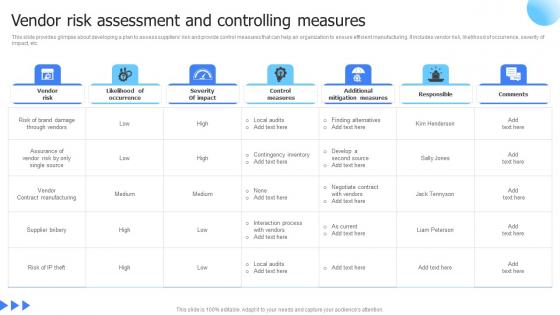
Leveraging Advanced Manufacturing Vendor Risk Assessment And Controlling Measures Topics Pdf
This slide provides glimpse about developing a plan to assess suppliers risk and provide control measures that can help an organization to ensure efficient manufacturing. It includes vendor risk, likelihood of occurrence, severity of impact, etc. Retrieve professionally designed Leveraging Advanced Manufacturing Understanding Scheduling Phase In Production Template Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
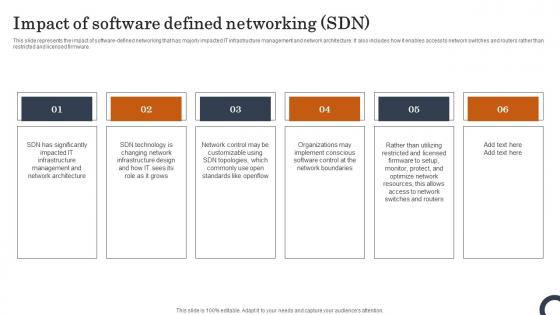
Impact Of Software Defined Networking SDN Evolution Of SDN Controllers Rules Pdf
This slide represents the impact of software-defined networking that has majorly impacted IT infrastructure management and network architecture. It also includes how it enables access to network switches and routers rather than restricted and licensed firmware. This Impact Of Software Defined Networking SDN Evolution Of SDN Controllers Rules Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Impact Of Software Defined Networking SDN Evolution Of SDN Controllers Rules Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Business Analyst Diagrams And Controlling Ppt PowerPoint Templates Backgrounds For Slides
We present our business analyst diagrams and controlling ppt PowerPoint templates backgrounds for slides.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Present our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Use our Flow Charts PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Present our Circle Charts PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime. Download our Ring Charts PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use.Use these PowerPoint slides for presentations relating to Access, arrow, background, banner, blue, bright, business, chart, circle, concept, conceptual, connection, corporate, cycle, design, different, element, graphic, group, idea, illustration, part, process, shape, strategy, template, vector, web, website. The prominent colors used in the PowerPoint template are Green, Gray, Black.
Business Analyst Diagrams And Controlling Ppt 7 PowerPoint Templates Backgrounds For Slides
We present our business analyst diagrams and controlling ppt 7 PowerPoint templates backgrounds for slides.Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Arrows PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download and present our Flow Charts PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Present our Circle Charts PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Use our Ring Charts PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need.Use these PowerPoint slides for presentations relating to Access, arrow, background, banner, blue, bright, business, chart, circle, concept, conceptual, connection, corporate, cycle, design, different, element, graphic, group, idea, illustration, part, process, shape, strategy, template, vector, web, website. The prominent colors used in the PowerPoint template are Blue, Gray, Black.
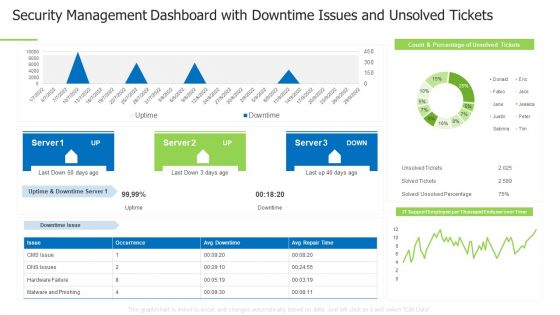
Techniques And Strategies To Reduce Security Management Risks Security Management Dashboard Information PDF
Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management dashboard information pdf bundle. Topics like logical access control, physical access control, access control categories can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
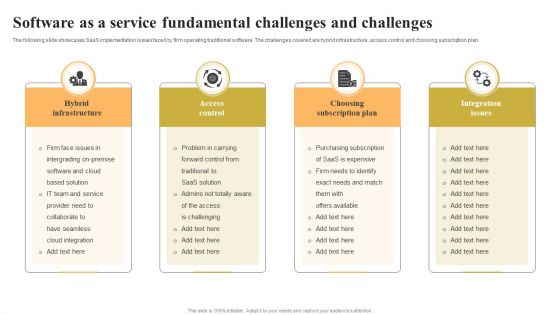
Software As A Service Fundamental Challenges And Challenges Background PDF
The following slide showcases SaaS implementation issues faced by firm operating traditional software. The challenges covered are hybrid infrastructure, access control and choosing subscription plan. Presenting Software As A Service Fundamental Challenges And Challenges Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Access Control, Choosing Subscription, Integration Issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
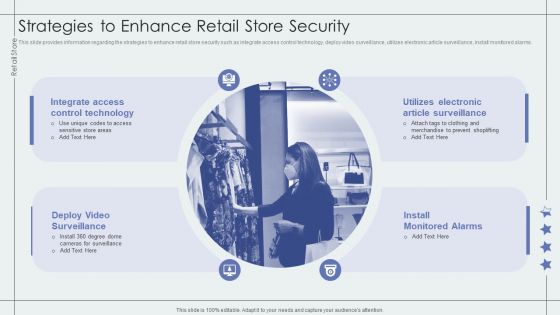
Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.Deliver an awe inspiring pitch with this creative Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF bundle. Topics like Integrate Access, Control Technology, Prevent Shoplifting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
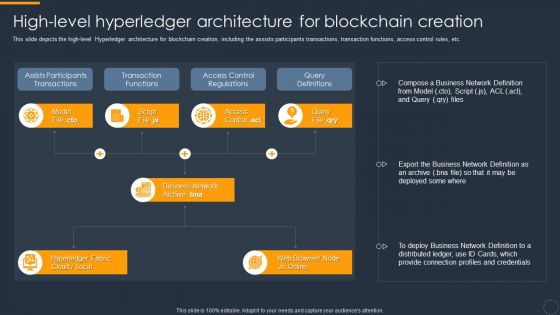
Cryptocurrency Ledger High Level Hyperledger Architecture For Blockchain Creation Topics PDF
This slide depicts the high level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Deliver an awe inspiring pitch with this creative Cryptocurrency Ledger High Level Hyperledger Architecture For Blockchain Creation Topics PDF bundle. Topics like Access Control Regulations, Transaction Functions, Assists Participants Transactions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Remote Summary PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management plan steps in detail remote summary pdf bundle. Topics like requirement for additional, remote access control, control security status can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
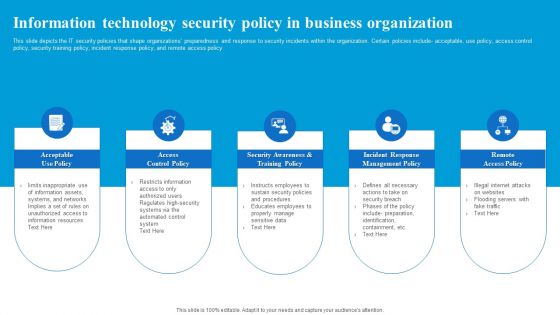
Information Technology Security Policy In Business Organization Download PDF
This slide depicts the IT security policies that shape organizations preparedness and response to security incidents within the organization. Certain policies include acceptable, use policy, access control policy, security training policy, incident response policy, and remote access policy. Presenting Information Technology Security Policy In Business Organization Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Access Control Policy, Acceptable Use Policy, Remote Access Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf
This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf today and make your presentation stand out from the rest
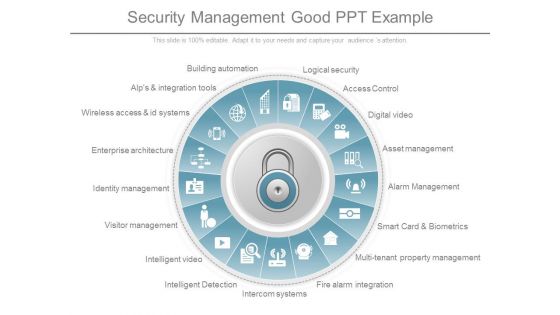
Security Management Good Ppt Example
This is a security management good ppt example. This is a thirteen stage process. The stages in this process are logical security, access control, digital video , asset management, alarm, management, multi tenant property management, fire alarm integration.

Digital Signature Management Powerpoint Slide Deck
This is a digital signature management powerpoint slide deck. This is a four stage process. The stages in this process are identification and authentication, access control, incident response, digital signature management.

Automation Management For Business Ppt Presentation Images
This is a automation management for business ppt presentation images. This is a eight stage process. The stages in this process are task automation, visitor management, elevator, resources provisioning, building management, service orchestration, intercom, access control.

Information Security System Ppt Powerpoint Topics
This is a information security system ppt powerpoint topics. This is a seven stage process. The stages in this process are network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security, information.
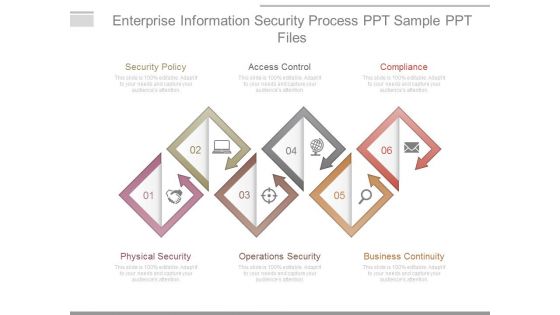
Enterprise Information Security Process Ppt Sample Ppt Files
This is a enterprise information security process ppt sample ppt files. This is a six stage process. The stages in this process are security policy, access control, compliance, physical security, operations security, business continuity.

Example Of Conceptual Systems Ppt Powerpoint Guide
This is a example of conceptual systems ppt powerpoint guide. This is a five stage process. The stages in this process are security policy, access control, consequences strategy, core strategy, security awareness.

Identification And Authentication Powerpoint Slide Deck
This is a identification and authentication powerpoint slide deck. This is a four stage process. The stages in this process are incident response, identification and authentication, access control, digital signature management.
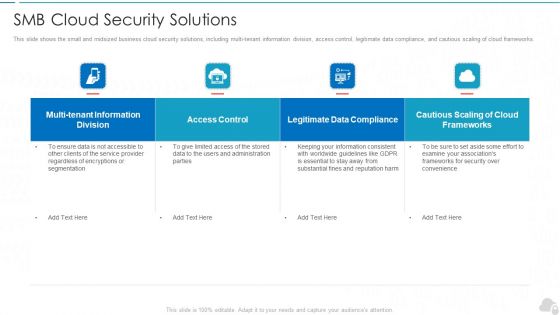
Smb Cloud Security Solutions Cloud Computing Security IT Ppt Portfolio Files PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. Deliver an awe inspiring pitch with this creative smb cloud security solutions cloud computing security it ppt portfolio files pdf bundle. Topics like access control, frameworks, legitimate data compliance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.
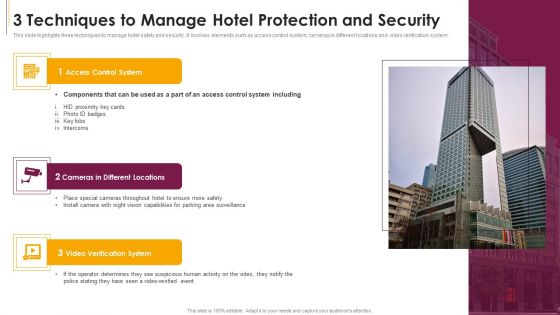
3 Techniques To Manage Hotel Protection And Security Sample PDF
This slide highlights three techniques to manage hotel safety and security. It involves elements such as access control system, cameras in different locations and video verification system.Presenting 3 Techniques To Manage Hotel Protection And Security Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Access Control System, Cameras In Different Locations, Verification System This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Cloud Network Security Challenges Sample PDF
The slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures Persuade your audience using this Key Cloud Network Security Challenges Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Insecure Access Control Points, Data Breaches, Data Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Overcoming Challenges In Conveyance And Safety Plan For Large Events Clipart Pdf
This slide provides information regarding the usage of a communication plan to address challenges in managing the security of large events. Major challenges covered in the slide relate to planning, access control and rapport management. Pitch your topic with ease and precision using this Overcoming Challenges In Conveyance And Safety Plan For Large Events Clipart Pdf. This layout presents information on Planning Communication, Access Control, Rapport Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
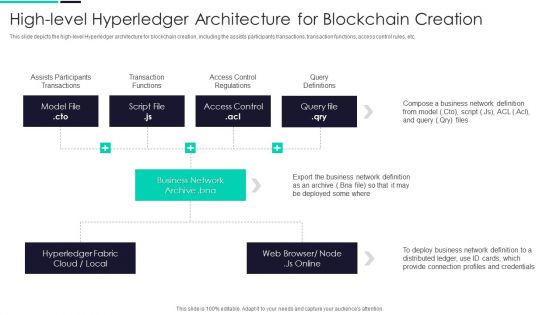
Blockchain And DLT Framework High Level Hyperledger Architecture For Blockchain Creation Graphics PDF
This slide depicts the high-level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. This is a Blockchain And DLT Framework High Level Hyperledger Architecture For Blockchain Creation Graphics PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Assists Participants Transactions, Transaction Functions, Access Control Regulations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategic Tips To Improve Physical Data Center Management Security Download PDF
This slide highlights tips to improve security of physical datacentre by having a thorough understanding of security measures and service level agreements. It covers secure location, physical access controls with building management security. Presenting Strategic Tips To Improve Physical Data Center Management Security Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Location, Physical Access Controls, Secure Building Management Systems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Process Management System Features To Streamline Business Process Summary PDF
This slide covers the features of business process management system to monitors and maintains processes to ensure optimal efficiency. The features are visual process diagramming tool, role based access control, SSO and administrator features. Presenting Business Process Management System Features To Streamline Business Process Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Visual Process, Diagramming Tool, Role Based, Access Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf
This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc. Showcasing this set of slides titled Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf. The topics addressed in these templates are Risk Assessment, Cybersecurity Governance, Access Controls. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

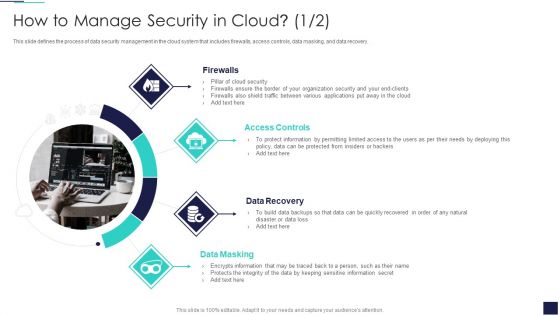
Cloud Security Assessment How To Manage Security In Cloud Cont Demonstration PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery.This is a Cloud Security Assessment How To Manage Security In Cloud Cont Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, Access Controls, Data Masking You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Manage Security In Cloud Background PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting How To Manage Security In Cloud Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Firewalls, Access Controls, Data Recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Controls, Data Recovery, Data Masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Challenges In Cloud Security Portrait PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting Key Challenges In Cloud Security Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Daniel Of Service, Compliance Violations, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
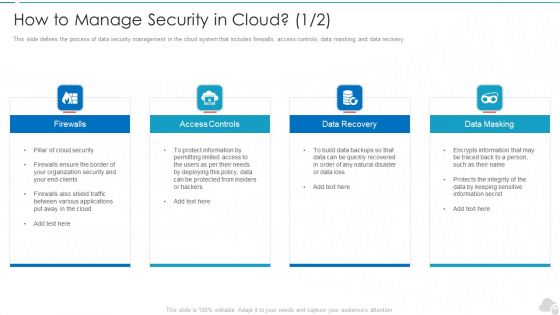
How To Manage Security In Cloud Cloud Computing Security IT Ppt Model Graphic Images PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting how to manage security in cloud cloud computing security it ppt model graphic images pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like firewalls, access controls, data recovery, data masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
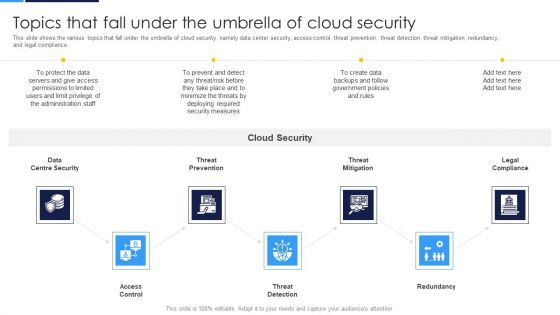
Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance.This is a Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threat Prevention, Access Control, Centre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
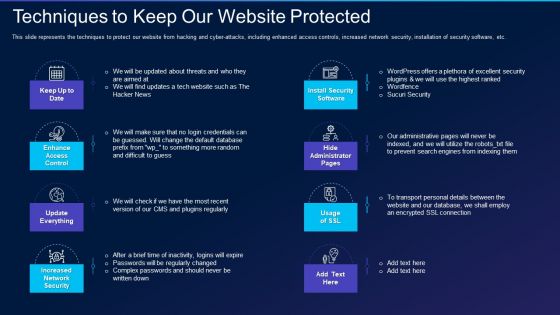
Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Key Challenges In Cloud Security Ppt Gallery Guidelines PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. This is a Cloud Information Security Key Challenges In Cloud Security Ppt Gallery Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compliance Violations, Access Control, Daniel Service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
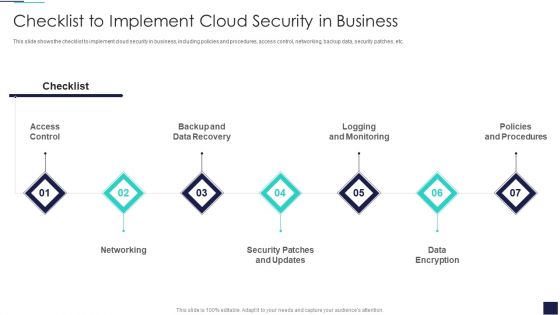
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. This is a Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Threat Prevention, Threat Detection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
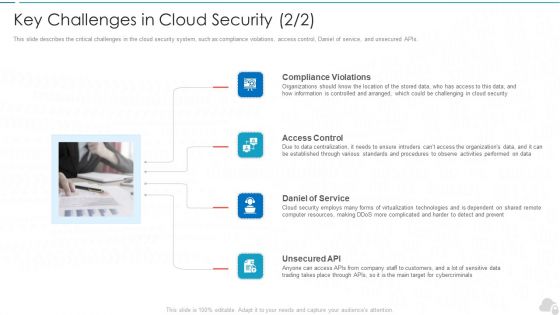
Key Challenges In Cloud Security Cloud Computing Security IT Ppt Infographic Template Graphics Example PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting key challenges in cloud security cloud computing security it ppt infographic template graphics example pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like compliance violations, access control, daniel of service, unsecured api. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs.Presenting Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Compliance Violations, Access Control, Daniel Of Service In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
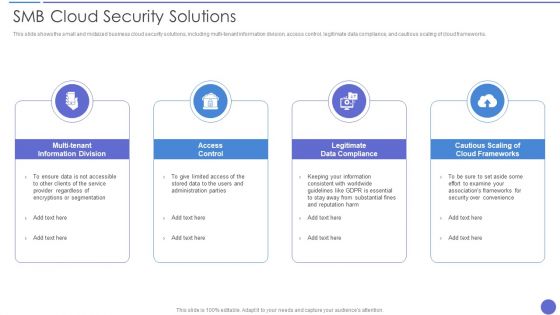
Smb Cloud Security Solutions Download PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. This is a Smb Cloud Security Solutions Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Legitimate Data Compliance, Cloud Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Topics That Fall Under The Umbrella Of Cloud Security Cloud Computing Security IT Ppt Model Example Introduction PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. Presenting topics that fall under the umbrella of cloud security cloud computing security it ppt model example introduction pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data centre security, threat prevention, access control, threat detection, threat mitigation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security SMB Cloud Security Solutions Ppt Show Files PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. Presenting Cloud Information Security SMB Cloud Security Solutions Ppt Show Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multi Tenant, Access Control, Information Division. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home