Safety Plan
CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Make sure to capture your audiences attention in your business displays with our gratis customizable CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
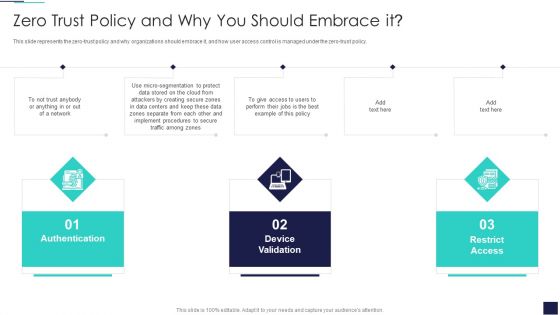
Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Vertical Chart For Solution Powerpoint Slide Designs
This is a vertical chart for solution powerpoint slide designs. This is a six stage process. The stages in this process are business, success, management, strategy, security.

Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF.
House Locked Security PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our House Locked Security PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Future PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way. Download and present our Finance PowerPoint Templates because You can Create a matrix with our PowerPoint Templates and Slides. Feel the strength of your ideas click into place. Download and present our Security PowerPoint Templates because You can Score a slam dunk with our PowerPoint Templates and Slides. Watch your audience hang onto your every word. Present our Money PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to A key in a lock with house, security, future, business, finance, money. The prominent colors used in the PowerPoint template are Yellow, Brown, Green.

Bulb Design For Creative Thinking Process Powerpoint Ideas
This is a bulb design for creative thinking process powerpoint ideas. This is a five stage process. The stages in this process are idea bulls, security, business, strategy, success.
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

With Cloud Technique We Can Share Data Securely PowerPoint Templates Ppt Backgrounds For Slides 0613
Display your drive on our With Cloud Technique We Can Share Data Securely PowerPoint Templates PPT Backgrounds For Slides. Invigorate the audience with your fervour. Drive your team towards excellence. Steer them there with our success PowerPoint Templates. Drive your passion with our business PowerPoint Templates. Steer yourself to achieve your aims.

Security Key On Heart Love PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Security Key On Heart Love PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Use our Festival PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience. Download and present our Security PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Use our Stars PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use.Use these PowerPoint slides for presentations relating to Heart lock great valentine security, security, shapes, festival, stars, curves and lines. The prominent colors used in the PowerPoint template are Red, White, Yellow.
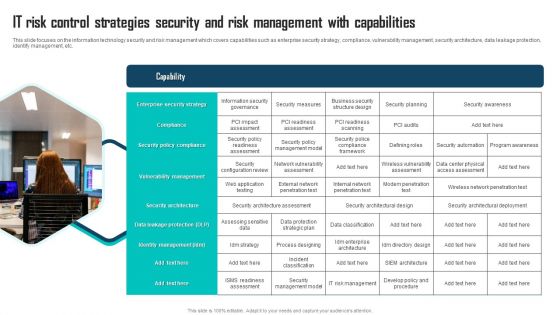
IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF
This slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Presenting IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Enterprise Security Strategy, Compliance, Security Policy Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
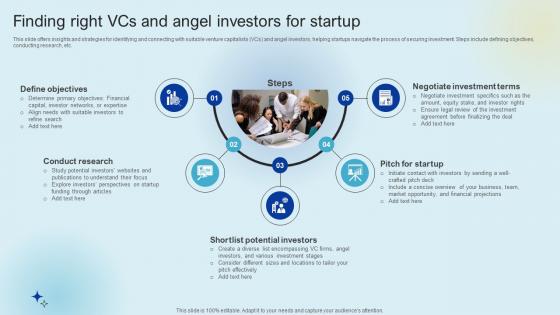
Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V
This slide offers insights and strategies for identifying and connecting with suitable venture capitalists VCs and angel investors, helping startups navigate the process of securing investment. Steps include defining objectives, conducting research, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
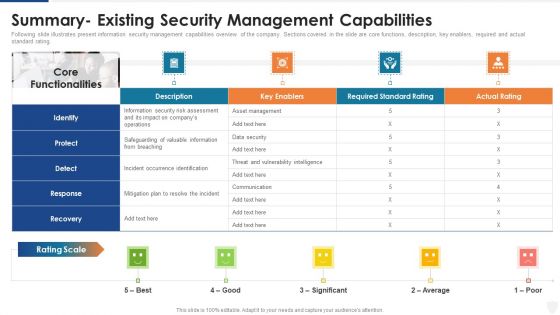
Summary Existing Security Management Capabilities Ppt Outline Themes PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative summary existing security management capabilities ppt outline themes pdf bundle. Topics like security, information, average can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Variance Analysis Techniques And Models Worksheet For Work Policy Analysis Pictures PDF
This slide covers a policy gap analysis method. It also includes various sections such as, policy, gap desareacription, action required and person responsible details. Pitch your topic with ease and precision using this variance analysis techniques and models worksheet for work policy analysis pictures pdf. This layout presents information on security policy, asset classification and control, physical and environmental security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
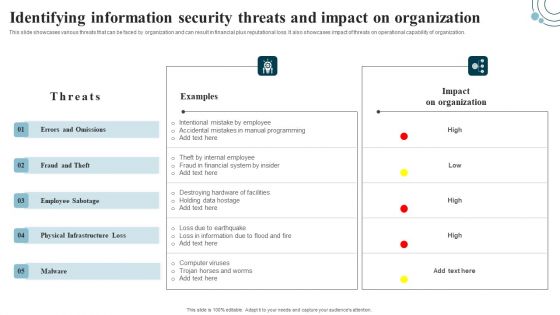
Developing IT Security Strategy Identifying Information Security Threats And Impact On Download PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. There are so many reasons you need a Developing IT Security Strategy Identifying Information Security Threats And Impact On Download PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
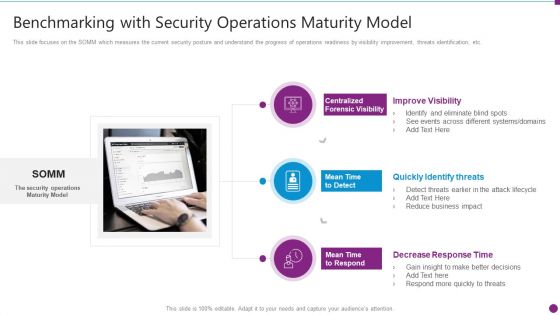
Security Information And Event Management Strategies For Financial Audit And Compliance Benchmarking With Security Guidelines PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting security information and event management strategies for financial audit and compliance benchmarking with security guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improve visibility, quickly identify threats, decrease response time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
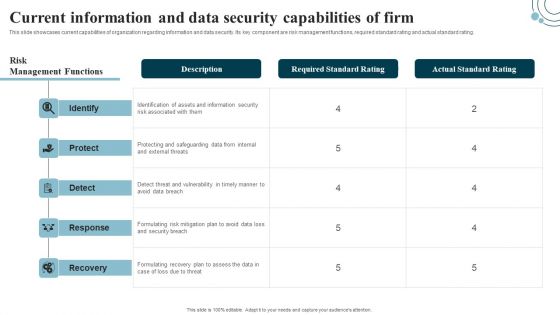
Developing IT Security Strategy Current Information And Data Security Capabilities Designs PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Developing IT Security Strategy Current Information And Data Security Capabilities Designs PDF from Slidegeeks and deliver a wonderful presentation.
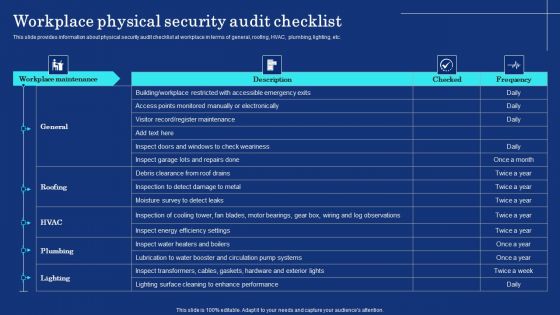
Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF
This slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. This Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cyber Security Implementation Framework Staff Training Schedule With Cost Ppt PowerPoint Presentation Pictures Slideshow PDF
Presenting this set of slides with name cyber security implementation framework staff training schedule with cost ppt powerpoint presentation pictures slideshow pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module, supplier relationship management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Continuity Strategies Information Security Ppt PowerPoint Presentation Gallery Structure Cpb
Presenting this set of slides with name continuity strategies information security ppt powerpoint presentation gallery structure cpb. This is an editable Powerpoint three stages graphic that deals with topics like continuity strategies information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Security Strategy Ppt PowerPoint Presentation Portfolio Infographic Template Cpb
Presenting this set of slides with name data security strategy ppt powerpoint presentation portfolio infographic template cpb. This is an editable Powerpoint three stages graphic that deals with topics like data security strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Develop Information Security Strategy Ppt PowerPoint Presentation Portfolio Information Cpb
Presenting this set of slides with name develop information security strategy ppt powerpoint presentation portfolio information cpb. This is an editable Powerpoint four stages graphic that deals with topics like develop information security strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
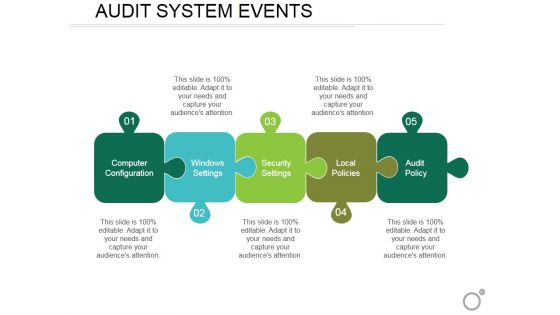
Audit System Events Ppt PowerPoint Presentation Professional Display
This is a audit system events ppt powerpoint presentation professional display. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.

Dollar Coin In Lifebouy Business Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Dollar Coin In Lifebouy Business Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Money PowerPoint Templates because you are the star of your enlightened team. Present our Finance PowerPoint Templates because you have configured your targets, identified your goals as per priority and importance. Use our Security PowerPoint Templates because you can Unravel the desired and essential elements of your overall strategy. Download and present our Business PowerPoint Templates because The foundation of the structure of your business is resilient and dependable. Convey this confidence to your colleagues and assure them of a great and enduring future. Download our Signs PowerPoint Templates because they are the stepping stones of our journey till date.Use these PowerPoint slides for presentations relating to Coin in lifebouy, money, finance, security, business, signs. The prominent colors used in the PowerPoint template are Yellow, Red, White. We assure you our Dollar Coin In Lifebouy Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Perfect. Customers tell us our signs PowerPoint templates and PPT Slides are Wonderful. You can be sure our Dollar Coin In Lifebouy Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Gorgeous. People tell us our money PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Presenters tell us our Dollar Coin In Lifebouy Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 will save the presenter time. People tell us our finance PowerPoint templates and PPT Slides are Graceful.

Implementation Of Strong Password Policy IT Security IT Ppt Styles Topics PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Presenting implementation of strong password policy it security it ppt styles topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementation of strong password policy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Implementation Of Strong Password Policy Ppt Summary Gridlines PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. This is a it security implementation of strong password policy ppt summary gridlines pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation of strong password policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
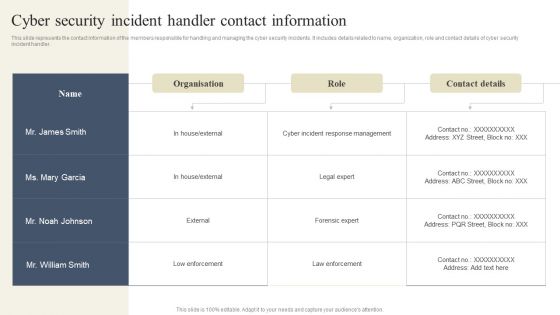
CYBER Security Breache Response Strategy Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Slidegeeks is here to make your presentations a breeze with CYBER Security Breache Response Strategy Cyber Security Incident Handler Contact Information Summary PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
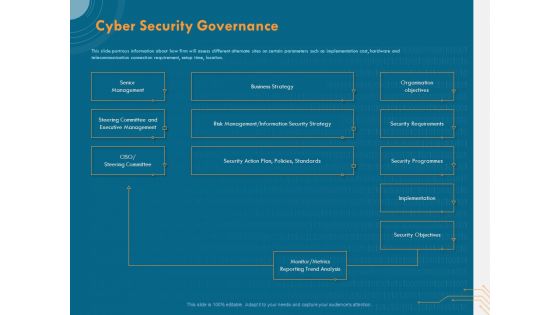
Cyber Security Implementation Framework Cyber Security Governance Ppt PowerPoint Presentation Layouts Master Slide PDF
Presenting this set of slides with name cyber security implementation framework cyber security governance ppt powerpoint presentation layouts master slide pdf. The topics discussed in these slides are senior management, steering committee and executive management, business strategy, organisation objectives, security requirements. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Home Security Systems PowerPoint Templates And PowerPoint Themes 1012
Home Security Systems PowerPoint Templates And PowerPoint Themes 1012-With these pre-designed chains you can visualize almost any type of concept, chronological process or steps of your strategies. This Targets the Security of Home, Business as illustrated by image. This Template points to the Chain Security which can be showed by alarm clock, dollars and house.-Home Security Systems PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Great For Home Security, Security, Business, Shapes, Symbol, Background

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Businesses Digital Technologies E Business Infrastructure Scope Topics PDF
This is a businesses digital technologies e business infrastructure scope topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like services and cloud management, it security and compliance, flexibility, costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
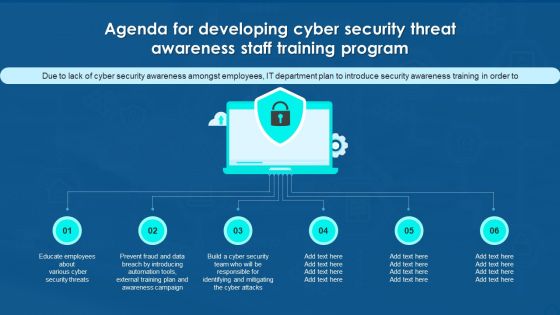
Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF
This is a Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security And Surveillance Company Profile Business Development Strategy Icons PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings.Presenting Security And Surveillance Company Profile Business Development Strategy Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Professional Channels, National Operations, Remove Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Framework Car Dashboard Indicator PowerPoint Presentation
Define the concept of target achievement and success with this exclusive PPT slide. To display this concept we have used graphic of target board and dart. This PPT slide also defines the concept of bull's eye condition. Use this PPT for business and marketing target related presentations.

Cloud Based Computing Analysis Types Of Services Offered By Consulting Firm Download PDF
This slide covers the broader services offered by consulting firm such as managing data centres, multi-cloud services, manged security services. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cloud Based Computing Analysis Types Of Services Offered By Consulting Firm Download PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
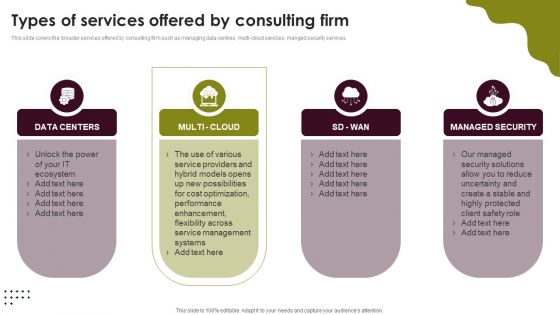
Cloud Computing Scalability Types Of Services Offered By Consulting Firm Elements PDF
This slide covers the broader services offered by consulting firm such as managing data centres, multi-cloud services, manged security services. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cloud Computing Scalability Types Of Services Offered By Consulting Firm Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Multi Cloud Infrastructure Management Types Of Services Offered By Consulting Firm Download PDF
This slide covers the broader services offered by consulting firm such as managing data centres, multi-cloud services, manged security services. This Multi Cloud Infrastructure Management Types Of Services Offered By Consulting Firm Download PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
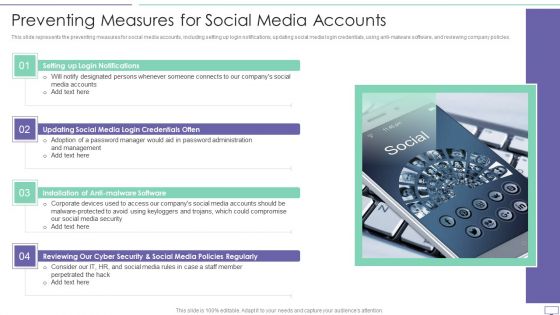
IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
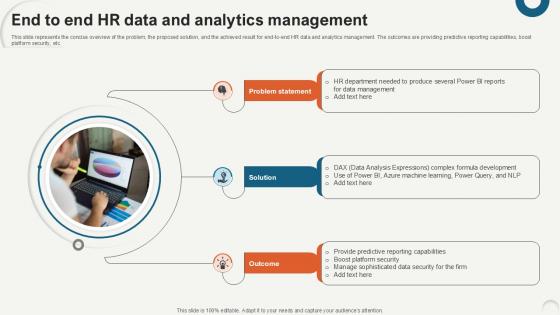
End To End HR Data And Analytics Data Analytics For Informed Decision Ppt Sample
This slide represents the concise overview of the problem, the proposed solution, and the achieved result for end-to-end HR data and analytics management. The outcomes are providing predictive reporting capabilities, boost platform security, etc. If you are looking for a format to display your unique thoughts, then the professionally designed End To End HR Data And Analytics Data Analytics For Informed Decision Ppt Sample is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download End To End HR Data And Analytics Data Analytics For Informed Decision Ppt Sample and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
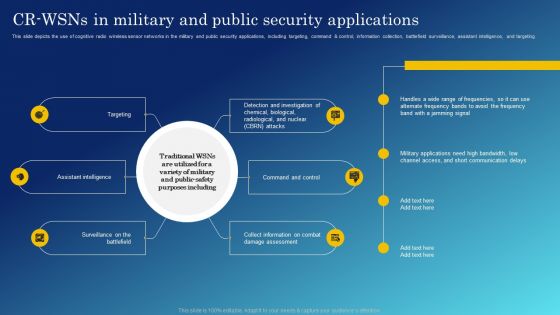
Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF
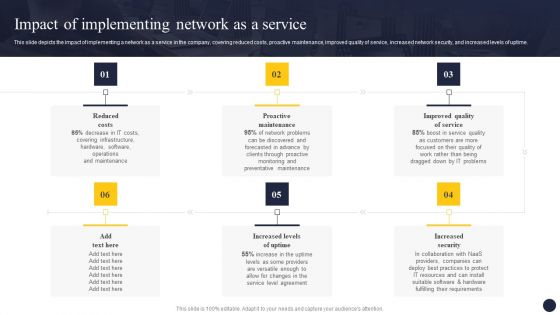
Integrating Naas Service Model To Enhance Impact Of Implementing Network As A Service Portrait PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. This Integrating Naas Service Model To Enhance Impact Of Implementing Network As A Service Portrait PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
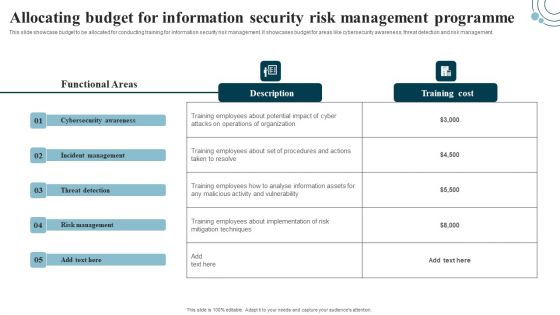
Developing IT Security Strategy Allocating Budget For Information Security Risk Background PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Allocating Budget For Information Security Risk Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Want to ace your presentation in front of a live audience Our CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Challenges Faced By The Firm While Managing Policies In Multi Cloud Environment Download PDF
This slide covers the challenges faced by the firm in managing multi cloud policies such as access, security, quota, budget, regulations, utilizations and many more. This is a Challenges Faced By The Firm While Managing Policies In Multi Cloud Environment Download PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Optimization, Security, Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategy To Provide Layered Security Across Networks Elements PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Presenting Strategy To Provide Layered Security Across Networks Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Network, Applications, Device. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
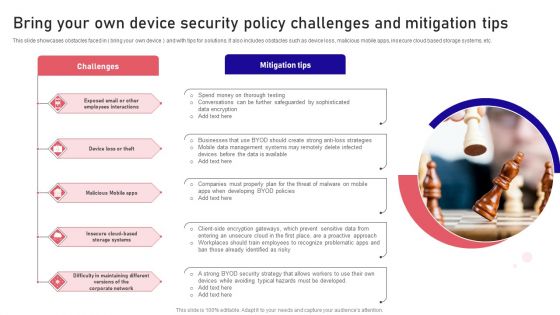
Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF
This slide showcases obstacles faced in bring your own device and with tips for solutions. It also includes obstacles such as device loss, malicious mobile apps, insecure cloud based storage systems, etc. Presenting Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Challenges, Mitigation Tips, Malicious Mobile. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
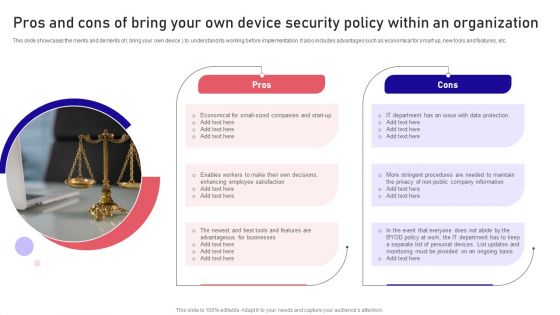
Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF
This slide showcases the merits and demerits of bring your own device to understand its working before implementation. It also includes advantages such as economical for smart up, new tools and features, etc. Presenting Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Data Protection, Organization, Company Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Consumer Retention Techniques Strategies To Improve Calling Experience To Increase Microsoft PDF
This slide shows the strategies that can be used by the medical facility or institution in order to improve the patient calling experience such as avoid overbooking, speed up patient intake process, use a mobile queue system, use secure messaging offer multiple scheduling options etc. Deliver an awe inspiring pitch with this creative consumer retention techniques strategies to improve calling experience to increase microsoft pdf bundle. Topics like offer patient portal, offer useful information hold message, use auto attendants and ivr, analyze patient feedback, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Challenges Faced By Information Technology Enabled Services Icons PDF
This slide covers the challenges faced by the information technology enabled services company during providing these services to the customers. It includes data security and privacy, high attrition rate, absence of policy reforms, etc. Presenting Challenges Faced By Information Technology Enabled Services Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Absence Of Policy Reforms, Data Security And Privacy, High Attrition Rates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Implementing Security Management Strategy To Mitigate Risk Roadmap Diagrams PDF
Presenting implementing security management strategy to mitigate risk roadmap diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Implementing Security Management Strategy To Mitigate Risk Timeline Rules PDF
Presenting implementing security management strategy to mitigate risk timeline rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
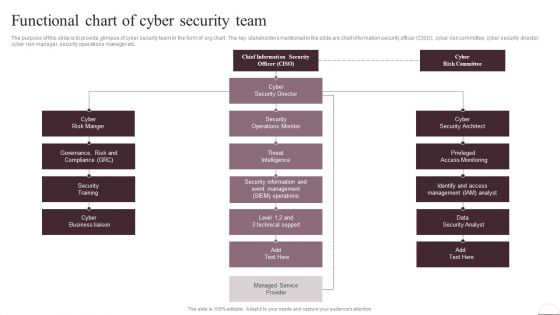
Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
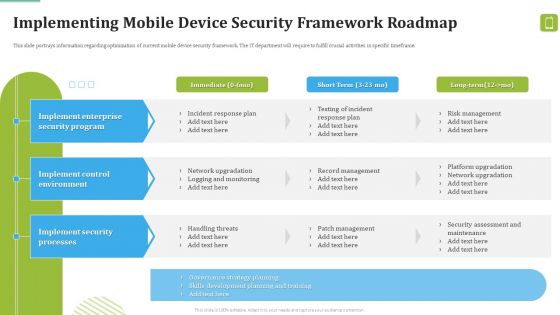
MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF bundle. Topics like Implement Enterprise, Security Program, Implement Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Dollar House With Key Locked Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Dollar House With Key Locked Security PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Money PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Use our Finance PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download and present our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to Money house with key, Money, Finance, Security, Business, Signs. The prominent colors used in the PowerPoint template are Yellow, Green, Black.
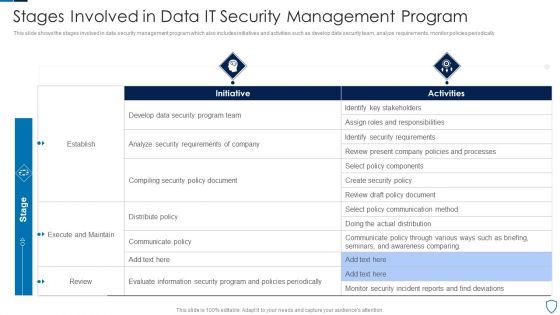
Stages Involved In Data IT Security Management Program Diagrams PDF
This slide shows the stages involved in data security management program which also includes initiatives and activities such as develop data security team, analyze requirements, monitor policies periodically.Pitch your topic with ease and precision using this Stages Involved In Data IT Security Management Program Diagrams PDF This layout presents information on Identify Stakeholders, Security Requirements, Execute Maintain It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
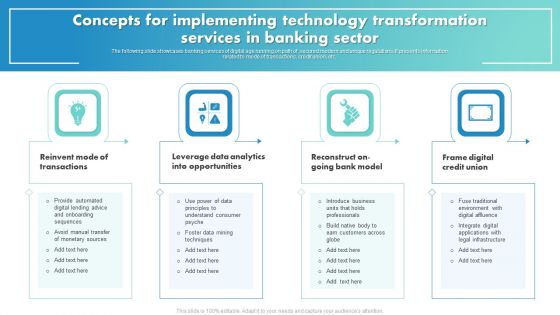
Concepts For Implementing Technology Transformation Services In Banking Sector Clipart PDF
The following slide showcases banking services of digital age running on path of secured modern and unique regulations. It presents information related to mode of transactions, credit union, etc. Persuade your audience using this Concepts For Implementing Technology Transformation Services In Banking Sector Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Leverage Data Analytics, Opportunities, Frame Digital, Credit Union. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
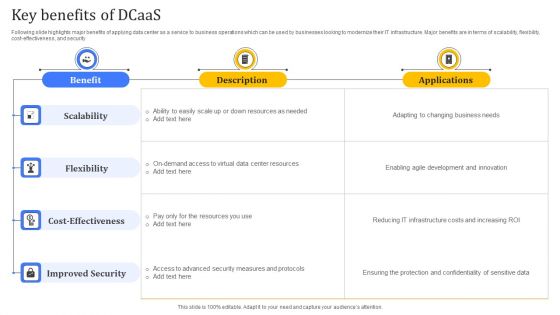
Key Benefits Of Dcaas Diagrams PDF
This slide depicts a dashboard which can be used to monitor the key performing indicators related to data center as a service model. The key performing indicators are items by status, counts by model attributes, item count by customer type, physical vs virtual system Showcasing this set of slides titled Key Benefits Of Dcaas Diagrams PDF. The topics addressed in these templates are Scalability, Flexibility, Cost Effectiveness, Improved Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Requirements For Successful Common Data Environment Ppt Infographics Summary PDF
The following slide showcases key requirements to build common data environment. The requirements covered are building information management, data security, data availability and defining roles and responsibilities. Presenting Requirements For Successful Common Data Environment Ppt Infographics Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Building Information Management, Data Availability, Data Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
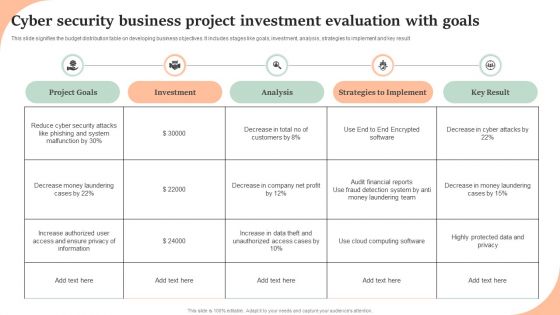
Cyber Security Business Project Investment Evaluation With Goals Structure PDF
This slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Showcasing this set of slides titled Cyber Security Business Project Investment Evaluation With Goals Structure PDF. The topics addressed in these templates are Project Goals, Investment, Analysis, Strategies To Implement, Key Result. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Four Revenue Building Approaches To Boost Sales Ways For Ecommerce Business Elements PDF
Following slide outlines different revenue building ways for e commerce businesses. Optimize site speed, mobile commerce, managing shipping cost and focusing on website security are the ways which will assist e commerce businesses to boost sales. Showcasing this set of slides titled four revenue building approaches to boost sales ways for ecommerce business elements pdf. The topics addressed in these templates are commerce, cost, sales. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

 Home
Home