Safety Plan
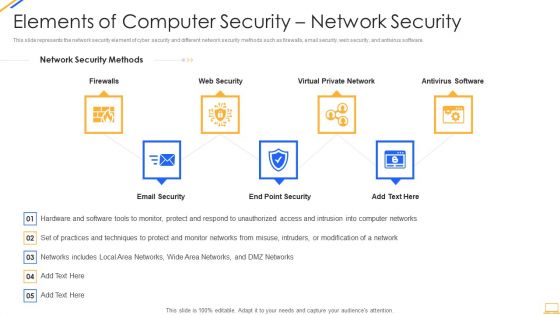
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Stock Photo New Business Strategy Secure Your Savings Concept Images Photos
Dreams Generate Thoughts, Thoughts Generate Ideas. Give Them Life With Our stock photo new business strategy secure your savings concept images photos Powerpoint Templates. Dreams Are The Start Of Many A Journey. Pave The Way With Our Money Powerpoint Templates.

Online Security Ppt PowerPoint Presentation Pictures Layout Ideas Cpb
This is a online security ppt powerpoint presentation pictures layout ideas cpb. This is a four stage process. The stages in this process are online security.

Information Security Elements Of Data Security Network Security Ppt Visual Aids Infographics PDF
This slide represents the network security element of data security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting information security elements of data security network security ppt visual aids infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like customer, market, product, opportunities, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
PowerPoint Design Slides Strategy Swot Analysis Ppt Slides
PowerPoint Design Slides Strategy Swot Analysis PPT Slides Business Power Points--These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer Server With Cloud Shape Structure PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Computer Server With Cloud Shape Structure PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Business PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Download and present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Technology PowerPoint Templates because It will get your audience in sync. Download our Success PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience.Use these PowerPoint slides for presentations relating to One computer server with a cloud shape, business, communication, security, technology, success. The prominent colors used in the PowerPoint template are Blue, White, Black.
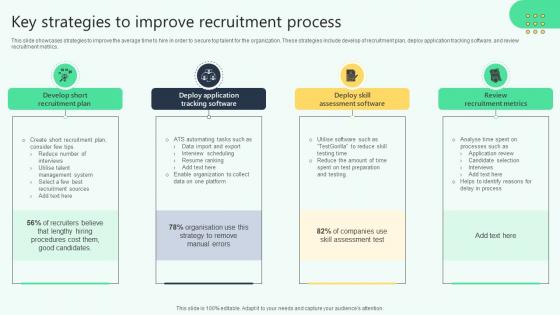
Key Strategies To Improve Recruitment Process Analysing Hr Data For Effective Decision Making
This slide showcases strategies to improve the average time to hire in order to secure top talent for the organization. These strategies include develop of recruitment plan, deploy application tracking software, and review recruitment metrics. Find a pre-designed and impeccable Key Strategies To Improve Recruitment Process Analysing Hr Data For Effective Decision Making. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

IT Security Risk Management Approach Introduction Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fifty two slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Security Camera System Company Profile Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty two slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Padlock With Metallic Chain Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Padlock With Metallic Chain Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please. Download and present our Chains PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to Padlock with metal chain, security, signs, chains, business, success. The prominent colors used in the PowerPoint template are Yellow, Gray, White.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
Strategies To Mitigate Cyber Security Risks Staff Training Schedule With Cost Ppt Icon Graphic Images PDF
Presenting this set of slides with name strategies to mitigate cyber security risks staff training schedule with cost ppt icon graphic images pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. This is a IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Failed Human Insights, Right Time Automation, High Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Forex Under Umbrella Marketing Business PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Forex Under Umbrella Marketing Business PowerPoint Templates PPT Backgrounds For Slides 1112.Download our Business PowerPoint Templates because this template can project the path to sucess that you have charted. Download our Success PowerPoint Templates because individual components well researched and understood in their place. Download our Security PowerPoint Templates because the Venn graphic comprising interlinking circles geometrically demonstate how various functions operating independantly, to a large extent, are essentially interdependant. Download and present our Marketing PowerPoint Templates because honesty is the best policy has an ardent follower in you. Download our Finance PowerPoint Templates because you envisage some areas of difficulty in the near future. The overall financial situation could be a source of worry.Use these PowerPoint slides for presentations relating to Forex under umbrella, business, success, security, marketing, finance. The prominent colors used in the PowerPoint template are Red, Black, Green. People tell us our Forex Under Umbrella Marketing Business PowerPoint Templates PPT Backgrounds For Slides 1112 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Presenters tell us our PowerPoint templates and PPT Slides are Youthful. Presenters tell us our Forex Under Umbrella Marketing Business PowerPoint Templates PPT Backgrounds For Slides 1112 are Tranquil. Use our finance PowerPoint templates and PPT Slides are Nice. We assure you our Forex Under Umbrella Marketing Business PowerPoint Templates PPT Backgrounds For Slides 1112 are Beautiful. The feedback we get is that our umbrella PowerPoint templates and PPT Slides are Wistful.
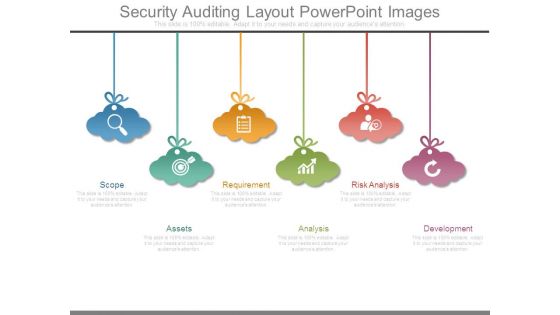
Security Auditing Layout Powerpoint Images
This is a security auditing layout powerpoint images. This is a six stage process. The stages in this process are scope, assets, requirement, analysis, risk analysis, development.

Our Services Template 2 Ppt PowerPoint Presentation Diagram Graph Charts
This is a our services template 2 ppt powerpoint presentation diagram graph charts. This is a four stage process. The stages in this process are business, digital advertising, digital care package, security maintenance, marketing and analytics, marketing, icons.
Security Analysis Ppt PowerPoint Presentation Infographics
This is a security analysis ppt powerpoint presentation infographics. This is a two stage process. The stages in this process are business, finance, growth, analysis, success.

Stock Photo Business Model Strategy Protect Your Savings Stock Images
Our Sales Concepts Go Back To School Bus Business Images And Graphics Powerpoint Templates Abhor Doodling. They Never Let The Interest Flag.
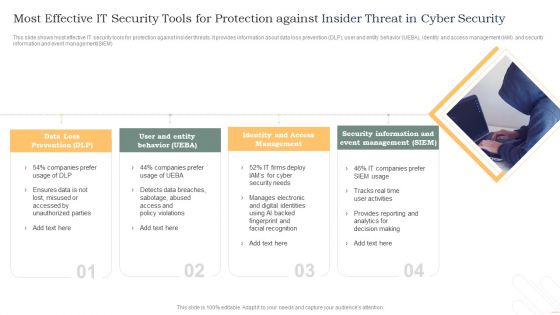
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Automation Tools Integration Security Orchestration Automation And Response Layer Structure PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. This is a IT Security Automation Tools Integration Security Orchestration Automation And Response Layer Structure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Investigation, Findings, Remediation, Visualization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Gap Identification Current Approach Process Flaws And Cost Ppt Show Model PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. This is a gap identification current approach process flaws and cost ppt show model pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology controls, management, planning, requirements, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Robotic Process Automation With AI Application In Commerce Business Graphics Pdf
Mentioned slide provides insight about robotic process automation with AI capabilities application in business to increase customer engagement. It includes key components such as guidance throughout online shopping, warehouse logistics management, transaction security, supply planning, etc. Showcasing this set of slides titled Robotic Process Automation With AI Application In Commerce Business Graphics Pdf. The topics addressed in these templates are Online Shopping, Warehouse Logistics Management, Transaction Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategies To Mitigate Cyber Security Risks Determining Roles And Responsibilities For Risk Handling Ideas PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining roles and responsibilities for risk handling ideas pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
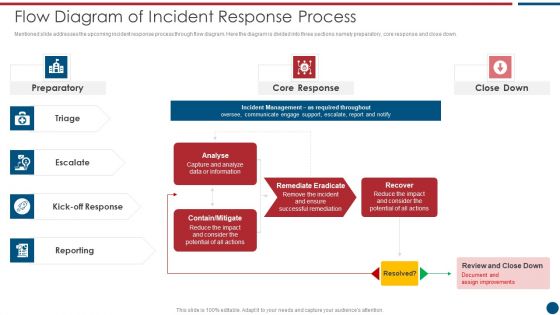
Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
8 Cycle Representation Of Security Policy Ppt PowerPoint Presentation Gallery Grid PDF
Persuade your audience using this 8 cycle representation of security policy ppt powerpoint presentation gallery grid pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 cycle representation of security policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comparing Two Choices Diagram For Security Policy Orchestration Ppt PowerPoint Presentation Gallery Design Templates PDF
Persuade your audience using this comparing two choices diagram for security policy orchestration ppt powerpoint presentation gallery design templates pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including comparing two choices diagram for security policy orchestration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template
Heres a predesigned Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template for you. Built on extensive research and analysis, this one-pager template has all the centerpieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template Download now.

Strategies To Mitigate Cyber Security Risks Impact Analysis Effective Security Management Introduction PDF
Presenting this set of slides with name strategies to mitigate cyber security risks impact analysis effective security management introduction pdf. The topics discussed in these slides are focus areas, security requirement, access rights authorized, incidents damaging, actual access violations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF today and make your presentation stand out from the rest.
Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. Slidegeeks has constructed Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Strategies To Mitigate Cyber Security Risks Selecting Security Incident Management Software Ppt Styles Influencers PDF
Presenting this set of slides with name strategies to mitigate cyber security risks selecting security incident management software ppt styles influencers pdf. This is a one stage process. The stages in this process are security incident forms, automated workflows, centralized platform, access rights, api integration, information security prevention, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Agenda Of SIEM Ppt Pictures Model PDF
This is a agenda of siem ppt pictures model pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management, Security Intelligence, Services, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Team Communication Strategies Temporary Hire Ppt PowerPoint Presentation Model Graphic Images
This is a team communication strategies temporary hire ppt powerpoint presentation model graphic images. This is a five stage process. The stages in this process are team communication strategies, temporary hire.

Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF
This slide showcases bring your own device policy and best practices for effective management and security. It also includes maintenance requirements, data encryption, policy compliance, etc. Persuade your audience using this Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Software Installed, Maintenance Requirement, Encryption . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
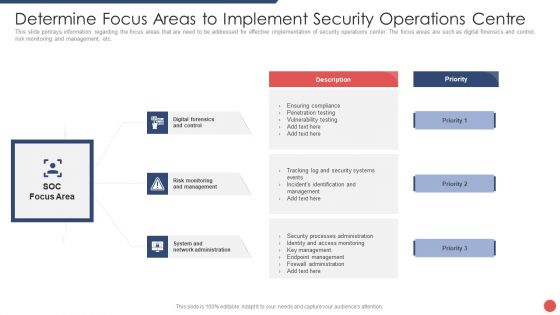
Security Functioning Centre Determine Focus Areas To Implement Security Operations Centre Demonstration PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security functioning centre determine focus areas to implement security operations centre demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk monitoring, management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
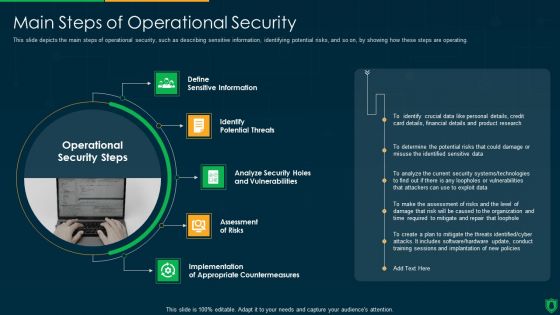
Info Security Main Steps Of Operational Security Ppt PowerPoint Presentation File Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a info security main steps of operational security ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like define sensitive information, identify potential threats, assessment risks, implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Presenting Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Human Error, Natural Disaster, Deliberate Software Attacks, Environmental Control Failures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
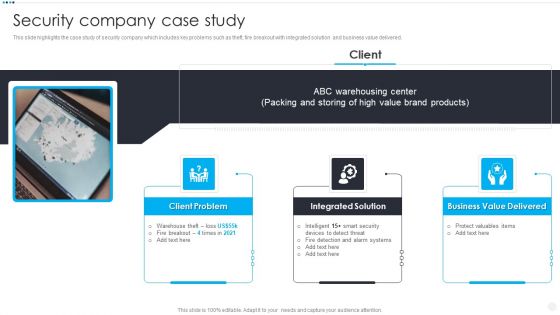
Smart Home Security Solutions Company Profile Security Company Case Study Brochure PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. Presenting Smart Home Security Solutions Company Profile Security Company Case Study Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like High Value Brand, Client Problem Storing, Integrated Solution Warehousing, Business Value Delivered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risks Organizations, Data Business, Serious Repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
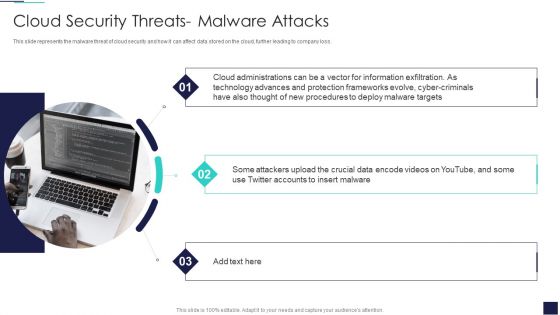
Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.This is a Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Rival Organizations, Cybercriminals, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Why To Automate The IT Security Process Pictures PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. This is a IT Security Automation Tools Integration Why To Automate The IT Security Process Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Better Threat Detection, Faster Containment, Improve Productivity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Table Of Contents Ppt Professional Graphic Tips PDF
Presenting security functioning centre table of contents ppt professional graphic tips pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like dashboard, impact analysis, incident management, security operations centre, technologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Cyber Threats Digital Era Gap Identification Current Approach Process Ppt Outline Objects PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era gap identification current approach process ppt outline objects pdf. Use them to share invaluable insights on gap identification current approach process flaws and cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

RPA Discovery Procedure Security Steps Brochure PDF
Following slide exhibits steps for robotic process automation security. Purpose of this slide is to use business automation efficiently that prevents data leakage and fraud. It includes pointers such as bot actions accountability, avoid fraud, secure log integrity etc. Presenting RPA Discovery Procedure Security Steps Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Bot Actions Accountability, Avoid Errors And Fraud, Secure Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
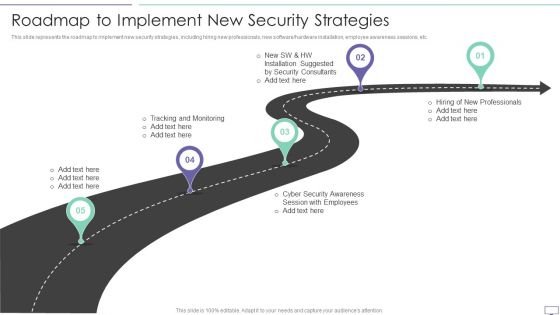
IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software hardware installation, employee awareness sessions, etc.This is a IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking And Monitoring, Security Awareness, Installation Suggested. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
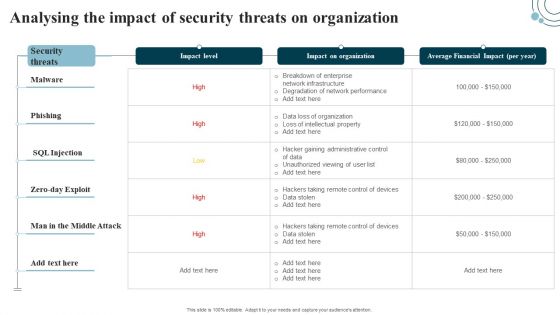
Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Revenue Distribution By Products Digital Marketings Strategies PPT PowerPoint CP SS V
This slide showcases aerospace company revenue distribution by products and services such as commercial airplanes, defense space and security, Global services and organization capital. Do you know about Slidesgeeks Revenue Distribution By Products Digital Marketings Strategies PPT PowerPoint CP SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Find highly impressive CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Mitigate Cyber Security Risks Business Impact Assessment Ppt Pictures Summary PDF
Presenting this set of slides with name strategies to mitigate cyber security risks business impact assessment ppt pictures summary pdf. This is a three stage process. The stages in this process are strengths, weaknesses, loss impact, primary business function, bcp representative, number employees, executive dexter hastings, department, function. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Info Security Latest Threats In Information Security Ppt PowerPoint Presentation Gallery Shapes PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a info security latest threats in information security ppt powerpoint presentation gallery shapes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like most recent, cyber threats reported, dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
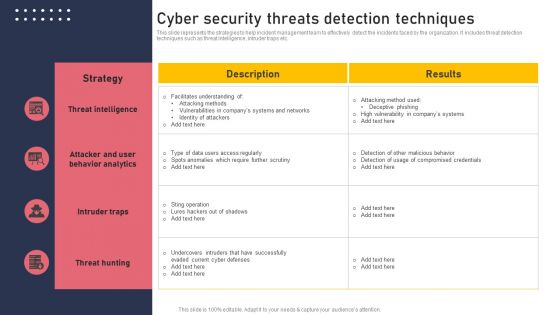
Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Security Analysis Ppt PowerPoint Presentation File Format Ideas
This is a security analysis ppt powerpoint presentation file format ideas. This is a one stage process. The stages in this process are security analysis, growth, strategy, management, business.

Developing IT Security Strategy Budget For Information Security Risk Management Information PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. This Developing IT Security Strategy Budget For Information Security Risk Management Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Budget For Information Security Risk Management Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.

 Home
Home