Safety Plan
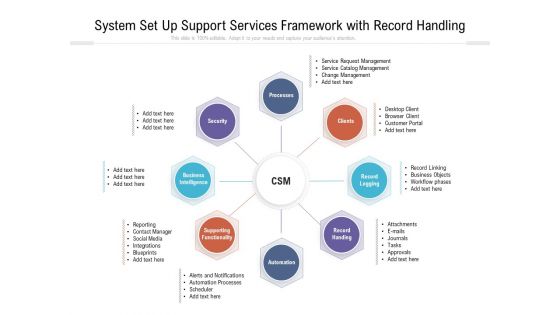
System Set Up Support Services Framework With Record Handling Ppt PowerPoint Presentation Gallery Inspiration PDF
Persuade your audience using this system set up support services framework with record handling ppt powerpoint presentation gallery inspiration pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including security, processes, business intelligence, supporting functionality, automation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Strategy Model 3d Image Of Blue And Black Chain Be Different Stock Images
With Our Business Strategy Model 3d Image Of Blue And Black Chain Be Different Stock Images Powerpoint Templates You Will Be Doubly Sure. They Possess That Stamp Of Authority.

Stock Photo Business Unit Strategy Wrench To Loosen Nuts And Bolts Clipart Images
Etch it in their brain with our stock photo business unit strategy wrench to loosen nuts and bolts clipart images. Embed your concept in their minds. Blast a forehand with our construction. Your ideas will go right down the line.

Stock Photo Develop Business Strategy Machine Tools Nuts And Bolts Pictures
Feel the force with our stock photo develop business strategy machine tools nuts and bolts pictures. They bring out the essential you. Our construction are always there for you. They will certainly come to your assistance.
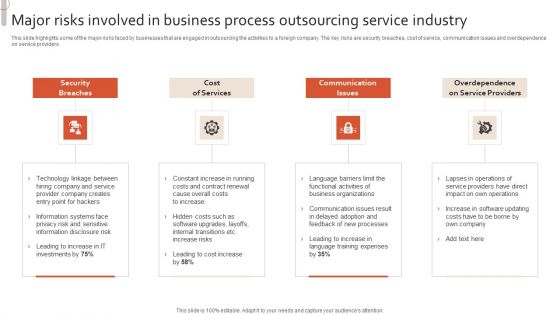
Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF
This slide highlights some of the major risks faced by businesses that are engaged in outsourcing the activities to a foreign company. The key risks are security breaches, cost of service, communication issues and overdependence on service providers. Presenting Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Breaches, Cost Services, Communicationi Ssues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Ocean Water Supervision Post It Notes Infographics PDF
This is a ocean water supervision post it notes infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, financing, technical, securities, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
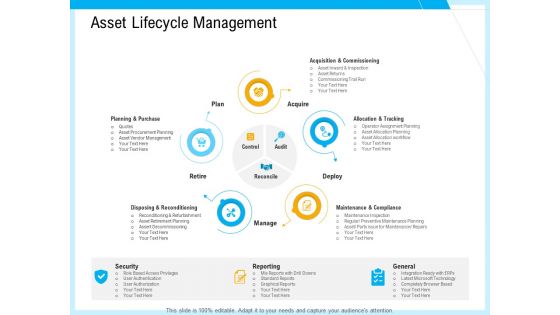
IT And Cloud Facilities Management Asset Lifecycle Management Ppt Summary Influencers PDF
This is a it and cloud facilities management asset lifecycle management ppt summary influencers pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan, acquire, reconcile, control, audit, deploy, manage, retire, security, reporting, general. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Technology Guide For Serverless Computing Cloud Management Tasks Introduction PDF
Presenting technology guide for serverless computing cloud management tasks introduction pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, planning, capabilities, awareness, monitor capacity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Current Operational Process Improvement Challenges The Company Is Facing Ideas PDF
This slide shows some of the current Operational Process Improvement challenges and issues that are faced by the company. Deliver an awe inspiring pitch with this creative current operational process improvement challenges the company is facing ideas pdf bundle. Topics like business, management, process development, improvement plan, security risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
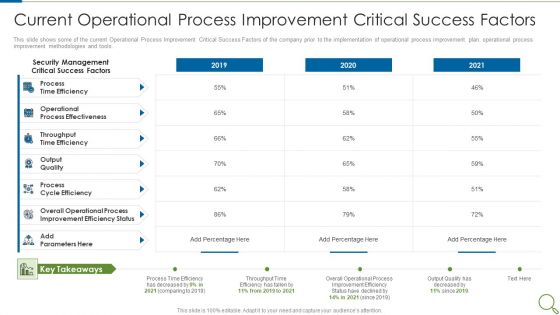
Current Operational Process Improvement Critical Success Factors Topics PDF
This slide shows some of the current Operational Process Improvement Critical Success Factors of the company prior to the implementation of operational process improvement plan, operational process improvement methodologies and tools. Deliver and pitch your topic in the best possible manner with this current operational process improvement critical success factors topics pdf. Use them to share invaluable insights on process, output quality, security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF
This slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. Boost your pitch with our creative Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Business Growth And Strategies PowerPoint Templates Ppt Backgrounds For Slides 0513
Establish your dominion with our Business Growth And Strategies PowerPoint Templates PPT Backgrounds For Slides. Rule the stage with your thoughts. Your ideas demand attention. Our success PowerPoint Templates will get it done. Your listeners will never doodle. Our business PowerPoint Templates PowerPoint Templates will hold their concentration.
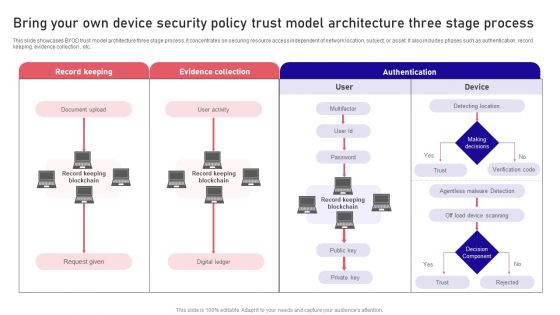
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

ITIL Strategy Service Excellence Client Standards Checklist Contd Ppt PowerPoint Presentation Styles Example PDF
Presenting this set of slides with name itil strategy service excellence client standards checklist contd ppt powerpoint presentation styles example pdf. This is a one stage process. The stages in this process are genuine anti spam solution, vendor supported server, licensed firewall between internal, secured encryption, wireless data traffic, environment, high speed internet access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart
With Our Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart Powerpoint Templates You Will Be Doubly Sure. They Possess That Stamp Of Authority. Our Security Powerpoint Templates Do It In Double Quick Time. Speed Up The Process In A Tangible Way.

Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF
This slide showcases software that can help organization to monitor and manage the information security. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc. Explore a selection of the finest Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
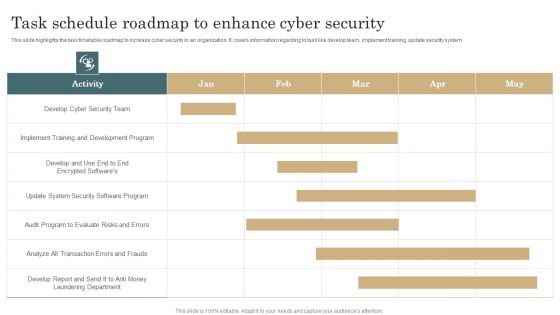
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Advance IT Service Areas Where Ml Will Deliver Strong Outcomes Organization Rules PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. This is a advance it service areas where ml will deliver strong outcomes organization rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security detection and prevention, fraud detection and prevention, research. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
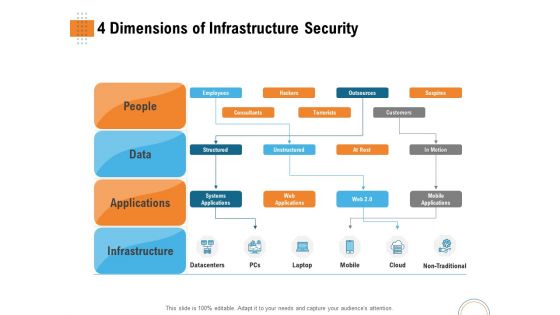
Utilizing Infrastructure Management Using Latest Methods 4 Dimensions Of Infrastructure Security Introduction PDF
Presenting utilizing infrastructure management using latest methods 4 dimensions of infrastructure security introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like people, data, applications, infrastructure, datacentres, mobile, cloud, non traditional. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Capability Strategy With Service Delivery Ppt Icon Gridlines PDF
Persuade your audience using this it capability strategy with service delivery ppt icon gridlines pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including information security, operations, enterprise mobility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
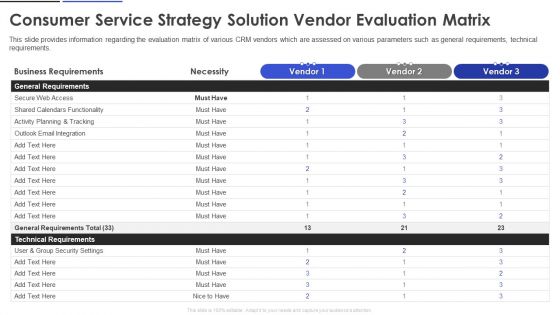
Consumer Service Strategy Solution Vendor Evaluation Matrix Infographics PDF
This slide provides information regarding the evaluation matrix of various CRM vendors which are assessed on various parameters such as general requirements, technical requirements. Deliver and pitch your topic in the best possible manner with this Consumer Service Strategy Solution Vendor Evaluation Matrix Infographics PDF. Use them to share invaluable insights on Secure Web Access, Technical Requirements, Business Requirements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Data Enablement Framework And Security Training Program Icons PDF
This slide illustrates three day training workshop for data enablement and data security. It includes audience, objectives, data governance, data security, etc. Presenting Data Enablement Framework And Security Training Program Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Data Foundation, Security Model Introduction, User Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
NIST Cybersecurity Framework For Cloud Security Icon Background PDF
Persuade your audience using this NIST Cybersecurity Framework For Cloud Security Icon Background PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including NIST Cybersecurity, Framework, Cloud Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
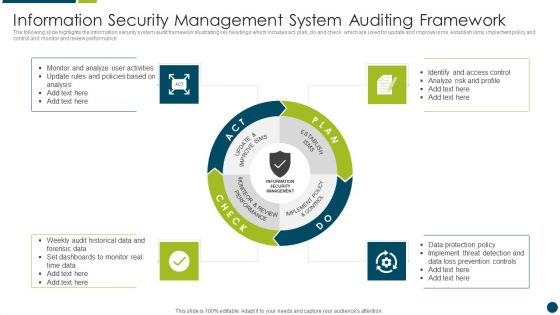
Information Security Management System Auditing Framework Microsoft PDF
The following slide highlights the information security management system audit checklist illustrating matrix consisting of domain, objective, description, identification and audit for information security policies, information security organization and human resource security Showcasing this set of slides titled Information Security Management System Auditing Framework Microsoft PDF. The topics addressed in these templates are Information Security Organization, Information Security Policies, Human Resource Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting
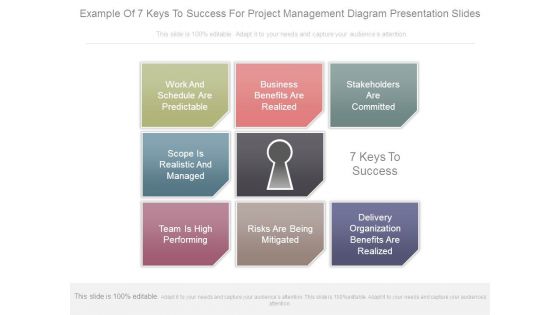
Example Of 7 Keys To Success For Project Management Diagram Presentation Slides
This is a example of 7 keys to success for project management diagram presentation slides. This is a eight stage process. The stages in this process are work and schedule are predictable, business benefits are realized, stakeholders are committed, scope is realistic and managed, 7 keys to success, team is high performing, risks are being mitigated, delivery organization benefits are realized.
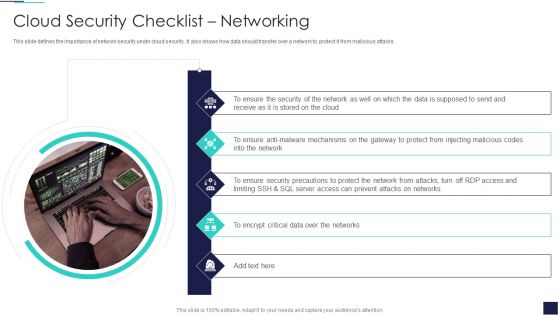
Cloud Information Security Cloud Security Checklist Networking Ppt Infographics Deck PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. This is a Cloud Information Security Cloud Security Checklist Networking Ppt Infographics Deck PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ensure Security, Data Supposed, Encrypt Critical. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

International Organization Standardization 270001 Our Objectives And Goals To Grow Business Sample PDF
Following slide illustrates different objectives and goals of the organization to grow its business. Objectives covered are information assets security, best customer service, revenue generation and employee competency. Deliver an awe inspiring pitch with this creative international organization standardization 270001 our objectives and goals to grow business sample pdf bundle. Topics like business objectives, business goals, customer service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
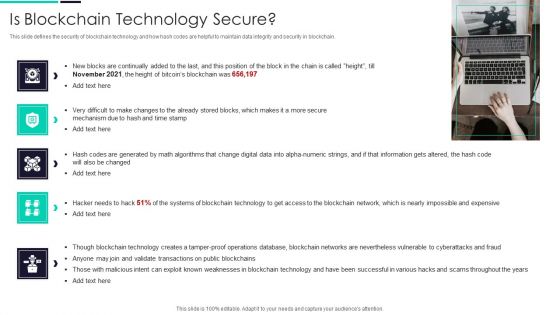
Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Time Stamp, Blockchain Technology, Weaknesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Communicate Your Csr Values To Team Ppt PowerPoint Presentation Good
This is a communicate your csr values to team ppt powerpoint presentation good. This is a six stage process. The stages in this process are passion, agility, innovation, diversity, security, promotion.
IT Security IT Prepare And Deploy Strong IT Policies Ppt Icon Design Ideas PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security it prepare and deploy strong it policies ppt icon design ideas pdf bundle. Topics like it policies, management, access, policies, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
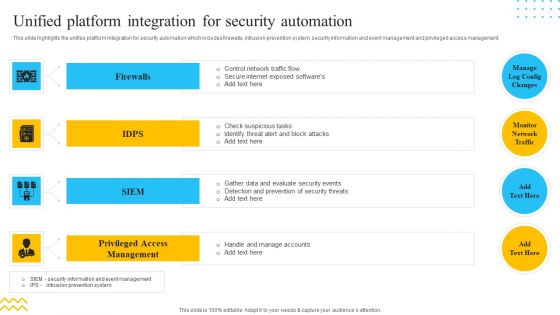
IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. This is a IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, IDPS, SIEM, Privileged Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Face Scanning Smart Phone Security Technique Icon Brochure PDF
Persuade your audience using this Face Scanning Smart Phone Security Technique Icon Brochure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Face Scanning, Smart Phone, Security Technique Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Payment Service Managed Services On Premises For Digital Payment Solutions Mockup PDF
Securely integrated on premise data storage and applications architecture. This is a online payment service managed services on premises for digital payment solutions mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, platform, servers, networking, storage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Yearly Virtual Team Building Timeline For Workforce Management Download PDF
Following slide highlights remote team development roadmap for organizations to facilitate communication, streamline work processes and foster company culture. This slide includes information about tasks such as evaluating company viability, utilizing tools, preparing leadership teams, etc. Showcasing this set of slides titled Yearly Virtual Team Building Timeline For Workforce Management Download PDF. The topics addressed in these templates are Communication, Security Policy, Management, Cloud Based Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Information Security Measures And Controls In Cloud Security Ppt Slides Graphic Images PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. This is a Cloud Information Security Measures And Controls In Cloud Security Ppt Slides Graphic Images PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Detective Control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
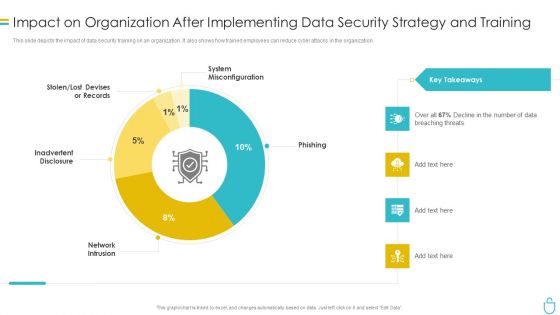
Information Security Impact On Organization After Implementing Data Security Strategy And Training Ppt Ideas Images PDF
This slide depicts the impact of data security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this information security impact on organization after implementing data security strategy and training ppt ideas images pdf. Use them to share invaluable insights on organization, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Marketing Concepts 4 One To Many Stages Organizational Diagram Business Unit Strategy
We present our modern marketing concepts 4 one to many stages organizational diagram business unit strategy.Present our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team. Download our Shapes PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Download our Process and Flows PowerPoint Templates because It will get your audience in sync. Download and present our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team.Use these PowerPoint slides for presentations relating to Development, Web, Design, Building, Plan, Hand, Success, Successful, Internet, Visitor, Site, Website, Network, White, Innovation, Formula, Media, Business, Server, Concept, Characteristic, Organizing, Diagram, Drawing, Marketing, Word, Starting, Technology, Security, Blogging, Strategy, Technique, Young, Writing, Domain, Text, Quality, Organization, Brainstorming, Information, Background, Hosting, Blog, Database, Software, Component, White Board, Entrepreneur, Communication. The prominent colors used in the PowerPoint template are Green, Gray, Black.

Table Of Contents For Mobile Device Security Management In Organization Tips Inspiration PDF
Presenting Table Of Contents For Mobile Device Security Management In Organization Tips Inspiration PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Current Scenario, Determine Current, Determine Various. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Example PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security prepare and deploy strong it policies ppt icon graphics example pdf bundle. Topics like management, it policies, network access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Automated Government Procedures E Governance Workstream Strategies Introduction PDF
Here we are covering the e-governance strategies which is enable everyone to use effective government services, in a secure, integrated and easy way through multiple electronic channels. Deliver an awe-inspiring pitch with this creative automated government procedures e governance workstream strategies introduction pdf bundle. Topics like infrastructure, institutional framework, change management, human capital, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
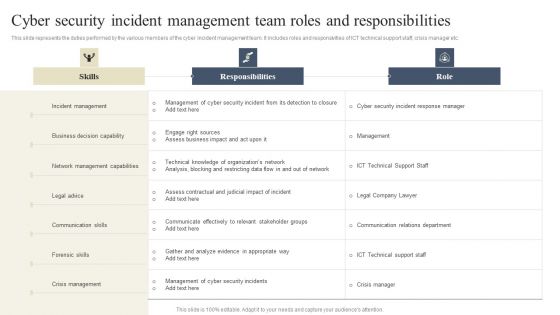
CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
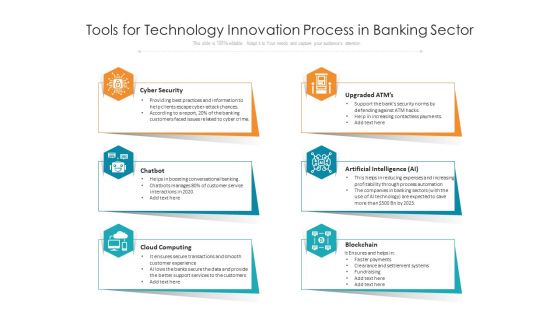
Tools For Technology Innovation Process In Banking Sector Ppt PowerPoint Presentation Show Inspiration PDF
Persuade your audience using this tools for technology innovation process in banking sector ppt powerpoint presentation show inspiration pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security, upgraded atms, artificial intelligence ai, chatbot, cloud computing, blockchain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Guidelines IT Internet Usage Policy Password Guidelines Download PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cybersecurity Guidelines IT Internet Usage Policy Password Guidelines Download PDF from Slidegeeks and deliver a wonderful presentation.
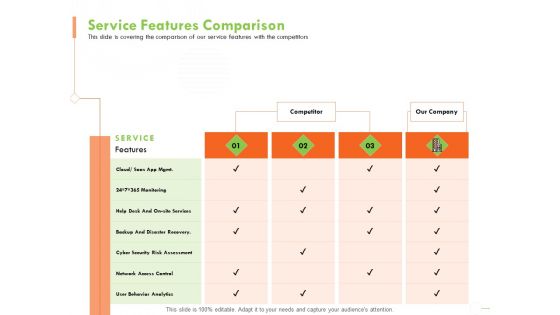
Welfare Work Value Service Features Comparison Ppt Outline Themes PDF
Presenting this set of slides with name welfare work value service features comparison ppt outline themes pdf. The topics discussed in these slides are monitoring, services, cyber security, analytics, network access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
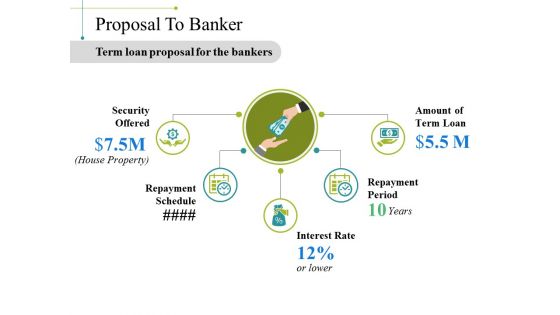
Proposal To Banker Ppt PowerPoint Presentation Outline Grid
This is a proposal to banker ppt powerpoint presentation outline grid. This is a five stage process. The stages in this process are security offered, repayment schedule, interest rate, repayment period, amount of term loan.

Security And Surveillance Company Profile Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fouty two slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

Security Functioning Centre Role Of Security Operations Centre In Security Operations Sample PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting security functioning centre role of security operations centre in security operations sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational system, security, operations team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
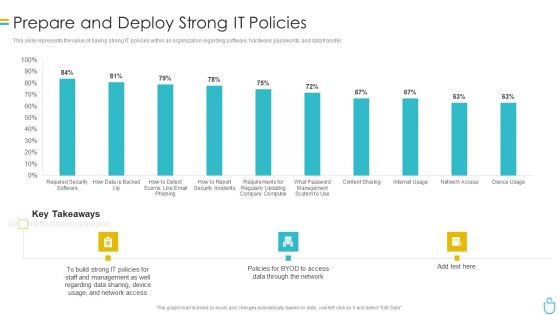
Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Prepare And Deploy Strong It Policies Template PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this desktop security management prepare and deploy strong it policies template pdf. Use them to share invaluable insights on management, data, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Information Technology Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Design PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this information technology security prepare and deploy strong it policies ppt icon graphics design pdf. Use them to share invaluable insights on v and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Insider Threat In Cyber Security Detection And Prevention Framework Information PDF
This slide shows insider threat prevention and detection framework. It contains information user characteristics, attack status, vulnerability, personality, past record, motivation behind attack, etc. Presenting Insider Threat In Cyber Security Detection And Prevention Framework Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Actor Characteristic, Attack Characteristic, Organisation Characteristic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
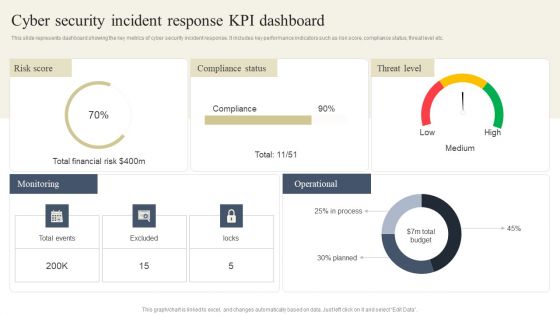
CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
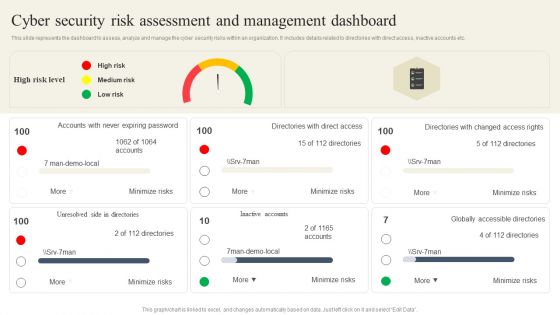
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. This CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Table Of Contents For IT Data Services Certification Programs Rules PDF
Presenting Table Of Contents For IT Data Services Certification Programs Rules PDF to provide visual cues and insights. Share and navigate important information on fifteen stages that need your due attention. This template can be used to pitch topics like Certified Data Professional, Systems Security Professional, Cisco Certified Internetwork Expert. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Collateral Security Document Vector Icon Ppt PowerPoint Presentation Outline Information
Presenting this set of slides with name collateral security document vector icon ppt powerpoint presentation outline information. This is a one stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Amount Spent On Cyber Fraud Settlements Ppt Outline Visual Aids PDF
Presenting this set of slides with name strategies to mitigate cyber security risks amount spent on cyber fraud settlements ppt outline visual aids pdf. This is a one stage process. The stages in this process are settlements, amount, average per settlement, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
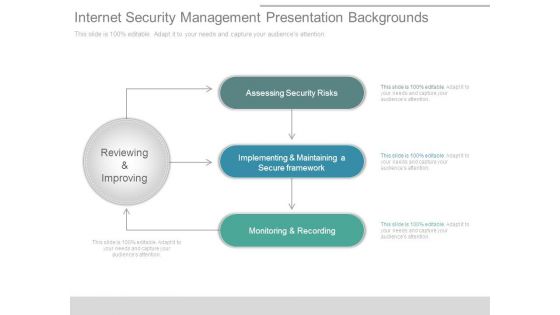
Internet Security Management Presentation Backgrounds
This is a internet security management presentation backgrounds. This is a three stage process. The stages in this process are assessing security risks, implementing and maintaining a secure framework, monitoring and recording, reviewing and improving.
Stock Photo Business Growth Strategy Help Yourself And Others Image
Our stock photo business growth strategy help yourself and others image Abhor Any Flaws. Give Your Expression A Beautiful Background. Honor Your Forefathers With Our puzzles or jigsaws. They Also Descend From An Esteemed Ancestry.

CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Explore a selection of the finest CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

 Home
Home