Security

Implementing Mobile Device Security Framework Roadmap Business Mobile Device Security Sample PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. There are so many reasons you need a Implementing Mobile Device Security Framework Roadmap Business Mobile Device Security Sample PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cloud Information Security Roadmap Of Cloud Security Implementation Ppt Styles PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Cloud Information Security Roadmap Of Cloud Security Implementation Ppt Styles PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Network Security, Configuration Management, Cloud Services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
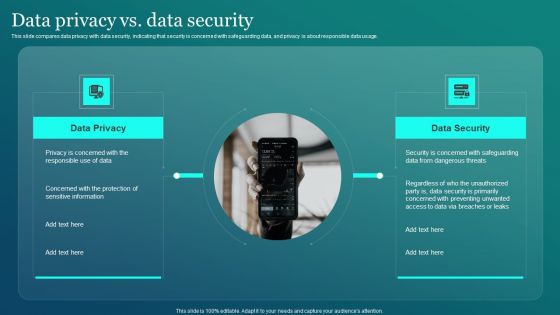
Information Security Data Privacy Vs Data Security Ppt PowerPoint Presentation File Infographic Template PDF
This slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Security Data Privacy Vs Data Security Ppt PowerPoint Presentation File Infographic Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
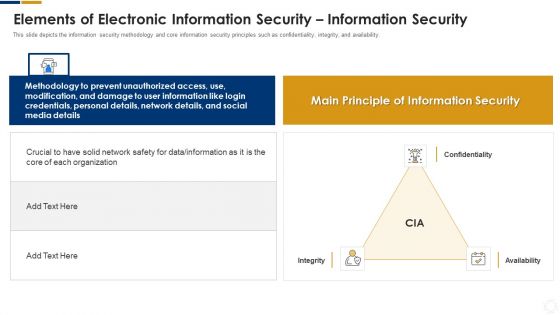
Cybersecurity Elements Of Electronic Information Security Information Security Ppt Pictures Slide PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a cybersecurity elements of electronic information security information security ppt pictures slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, network, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Security Information And Event Management Services Information PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting real time assessment of security threats security information and event management services information pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
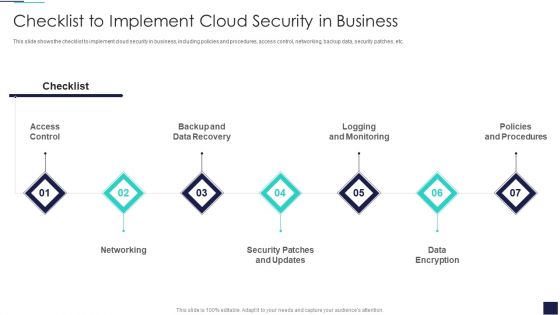
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
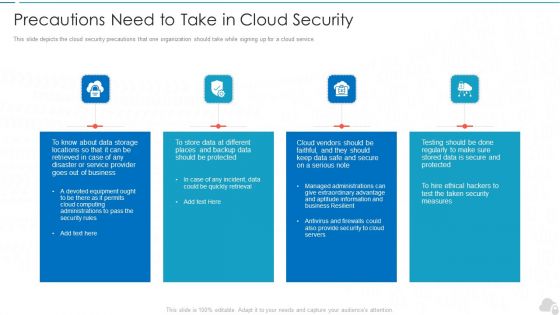
Precautions Need To Take In Cloud Security Cloud Computing Security IT Ppt Inspiration Templates PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service. Presenting precautions need to take in cloud security cloud computing security it ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, service, security measures, computing administrations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Best Practices For Cloud Security Ppt Icon Pictures PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting it security best practices for cloud security ppt icon pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like operations management, security and compliance monitoring, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
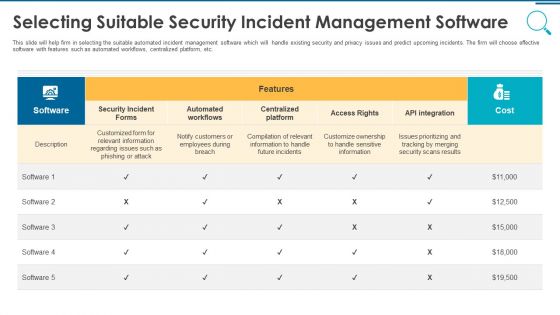
Information And Technology Security Operations Selecting Suitable Security Incident Management Software Diagrams PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative information and technology security operations selecting suitable security incident management software diagrams pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions Selecting Suitable Security Incident Management Software Pictures PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative organizational security solutions selecting suitable security incident management software pictures pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
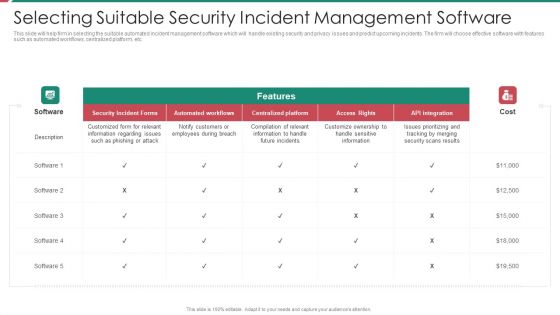
Security And Process Integration Selecting Suitable Security Incident Management Software Brochure PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative security and process integration selecting suitable security incident management software brochure pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
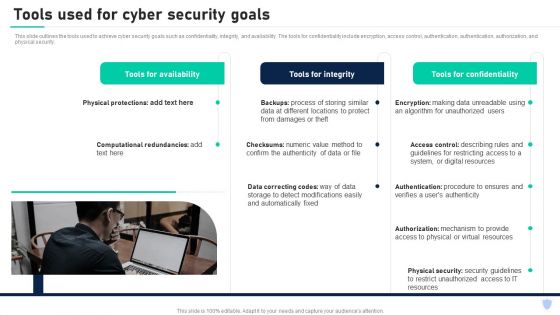
Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Presenting Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Implement Policies, Protect Data, Security Procedures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ensuring Checklist For Mobile Security Deployment Business Mobile Device Security Management Sample PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Ensuring Checklist For Mobile Security Deployment Business Mobile Device Security Management Sample PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF
The given slide provides the key activities to be done to alleviate the effects of cyber threats. It includes managing social media profiles, backing up the data, crosschecking privacy and security settings etc. Showcasing this set of slides titled Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF. The topics addressed in these templates are Concerned Areas, Social Media Profiles, Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
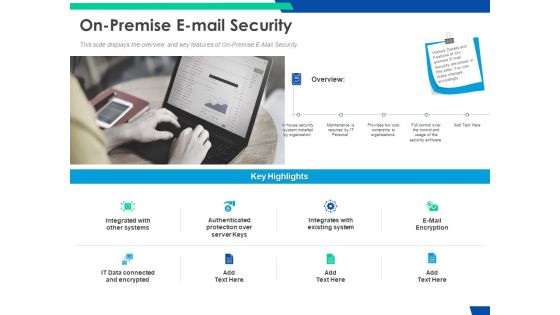
Cloud Based Email Security Market Report On Premise E Mail Security Ppt Ideas Design Inspiration PDF
This slide displays the overview and key features of On Premise E Mail Security. This is a cloud based email security market report on premise e mail security ppt ideas design inspiration pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like on premise e mail security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
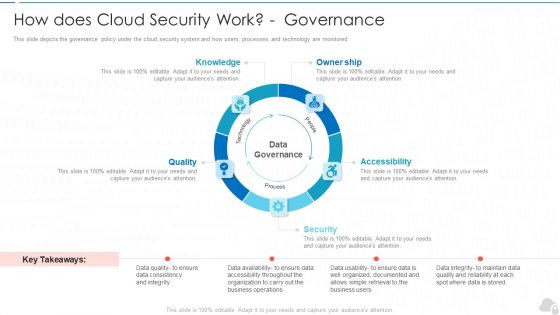
How Does Cloud Security Work Governance Cloud Computing Security IT Ppt Layouts Structure PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a how does cloud security work governance cloud computing security it ppt layouts structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like knowledge, owner ship, quality, security, accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
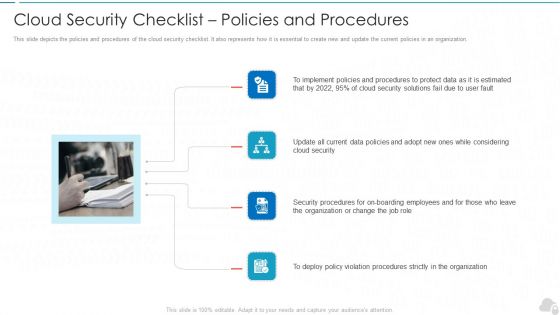
Cloud Security Checklist Policies And Procedures Cloud Computing Security IT Ppt Layouts Show PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. This is a cloud security checklist policies and procedures cloud computing security it ppt layouts show pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implement policies, cloud security, organization, policy violation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Elements Of IT Security IT Application Security Ppt Layouts Ideas PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. This is a elements of it security it application security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, encryption, authorization, techniques, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Role Of Management In Effective Corporate Security Governance Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an awe inspiring pitch with this creative developing firm security strategy plan role of management in effective corporate security governance slides pdf bundle. Topics like strategic alignment, risk management, measuring performance, value delivery, managing resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Addressing Physical Security At Workplace Ideas PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Presenting developing firm security strategy plan addressing physical security at workplace ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like workplace surveillance, employee monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
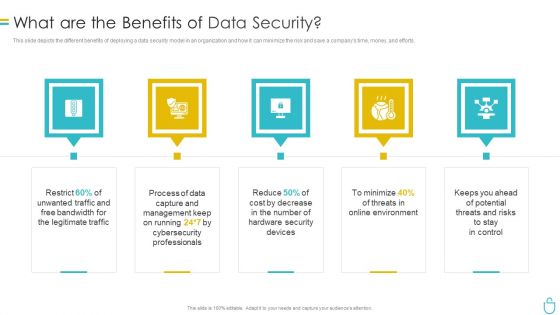
Information Security What Are The Benefits Of Data Security Ppt Infographics Example Topics PDF
This slide depicts the different benefits of deploying a data security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting information security what are the benefits of data security ppt infographics example topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, hardware security, devices, environment, risks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
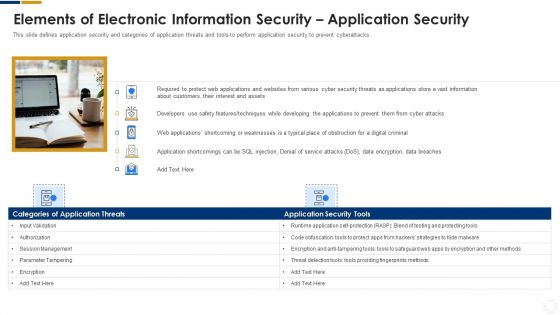
Cybersecurity Elements Of Electronic Information Security Application Security Ppt Styles Graphics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. This is a cybersecurity elements of electronic information security application security ppt styles graphics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, developers, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Suggested Coverage For Security Management Plan Information PDF
This slide provides information about the areas that are covered under the security management plan.This is a techniques and strategies to reduce security management risks suggested coverage for security management plan information pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like governance arrangement, information including, personnel security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
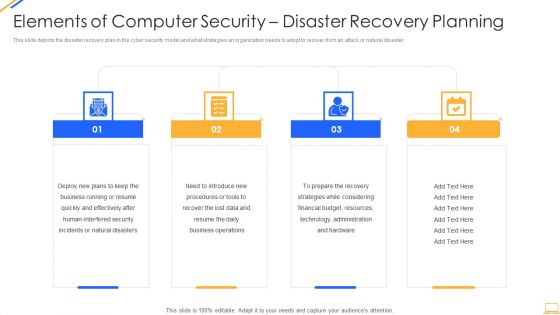
Desktop Security Management Elements Of Computer Security Disaster Recovery Planning Guidelines PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting desktop security management elements of computer security disaster recovery planning guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, resources, financial budget, strategies, plans. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
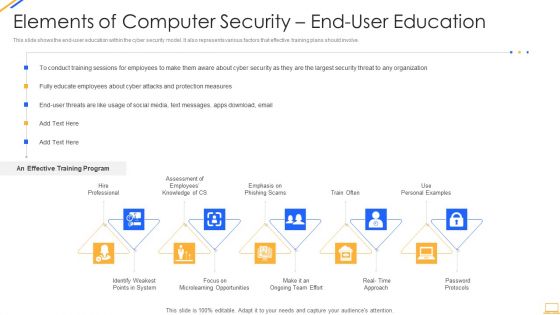
Desktop Security Management Elements Of Computer Security End User Education Background PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a desktop security management elements of computer security end user education background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, opportunities, security, organization, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Desktop Security Management What Are The Benefits Of Computer Security Icons PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting desktop security management what are the benefits of computer security icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, environment, potential, devices, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elements Of Information Technology Security Application Security Ppt Portfolio Inspiration PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Presenting elements of information technology security application security ppt portfolio inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like required, information, customers, interest, assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
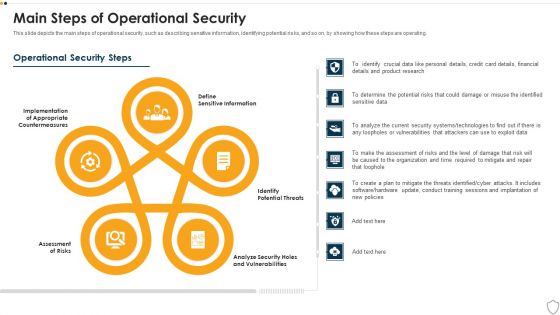
IT Security Main Steps Of Operational Security Ppt Show Design Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting it security main steps of operational security ppt show design inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like assessment of risks, potential threats, sensitive information, analyze security holes and vulnerabilities, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
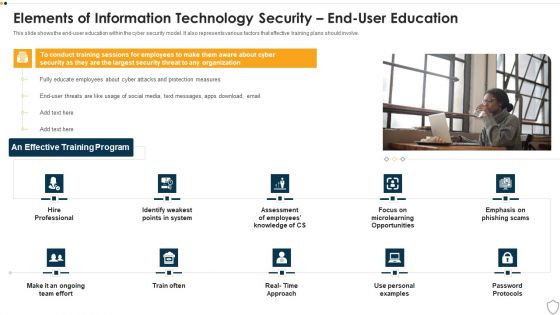
IT Security Elements Of Information Technology Security End User Education Ppt Show Maker PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a it security elements of information technology security end user education ppt show maker pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elements of information technology security end user education. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
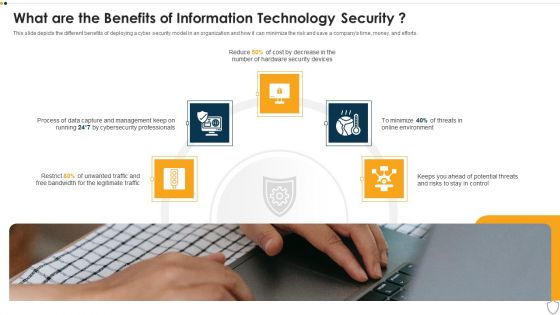
IT Security What Are The Benefits Of Information Technology Security Ppt Layouts Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a it security what are the benefits of information technology security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, process, potential threats, security devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Elements Of Information Security Disaster Recovery Planning Ppt PowerPoint Presentation Gallery Designs PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a info security elements of information security disaster recovery planning ppt powerpoint presentation gallery designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deploy new plans, quickly and effectively, security incidents, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
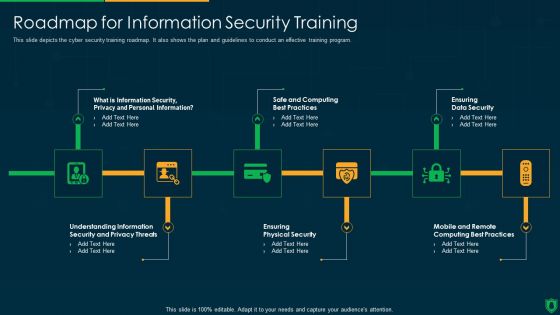
Info Security Roadmap For Information Security Training Ppt PowerPoint Presentation File Inspiration PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a info security roadmap for information security training ppt powerpoint presentation file inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, personal information, safe and computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smart Home Security Solutions Company Profile Security Company Organization Chart Diagrams PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Smart Home Security Solutions Company Profile Security Company Organization Chart Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Executive Vice President, EVP Home Security, Chief Marketing Officer, Chief Administrative Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. This is a Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Control Identity, Security Breaches, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
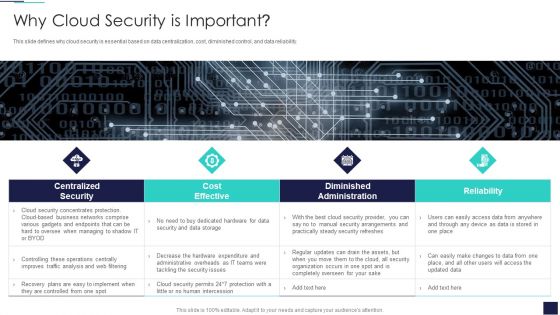
Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. This is a Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cost Effective, Diminished Administration, Centralized Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. This is a Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Threat Prevention, Threat Detection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
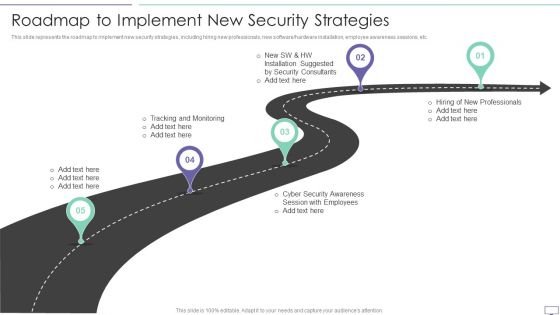
IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software hardware installation, employee awareness sessions, etc.This is a IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking And Monitoring, Security Awareness, Installation Suggested. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets.This is a Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identifying Internal, Allocating Vulnerability, Assessing Level. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Security Orchestration Automation And Response Layer Structure PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. This is a IT Security Automation Tools Integration Security Orchestration Automation And Response Layer Structure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Investigation, Findings, Remediation, Visualization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
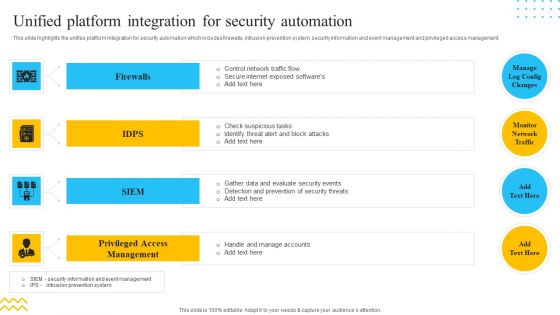
IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. This is a IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, IDPS, SIEM, Privileged Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
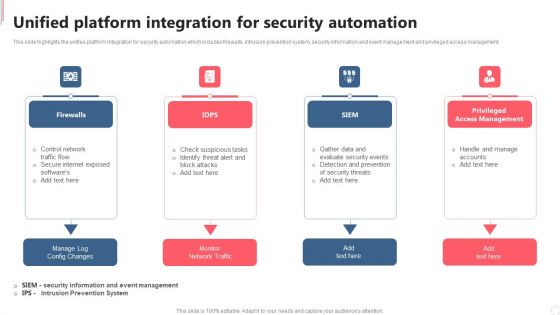
Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present like a pro with Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
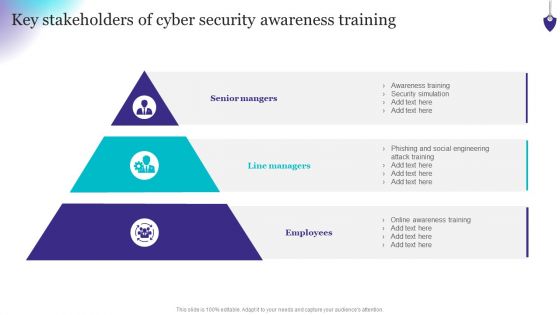
Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF.
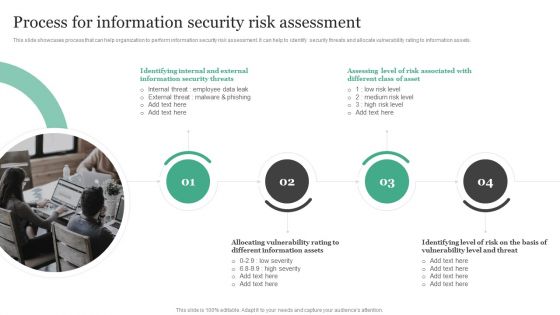
Process For Information Security Risk Assessment Information Security Risk Administration Demonstration PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help to identify security threats and allocate vulnerability rating to information assets.Take your projects to the next level with our ultimate collection of Process For Information Security Risk Assessment Information Security Risk Administration Demonstration PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.

Security Automation Integrates Security Automation To Analyze And Mitigate Cyberthreats Slides PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures.Present like a pro with Security Automation Integrates Security Automation To Analyze And Mitigate Cyberthreats Slides PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Security Automation To Analyze And Mitigate Cyberthreats Security Orchestration Automation Ideas PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Welcome to our selection of the Security Automation To Analyze And Mitigate Cyberthreats Security Orchestration Automation Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
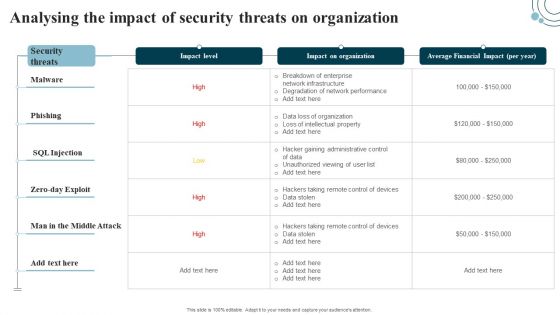
Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
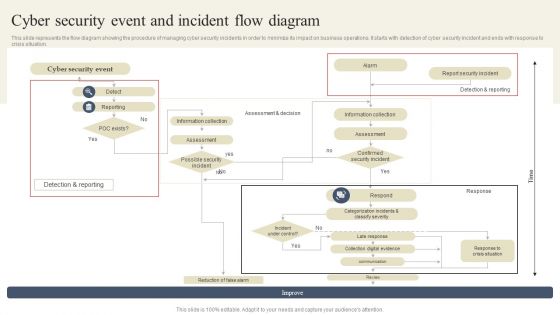
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist During An Incident Sample PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist During An Incident Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

 Home
Home