Security

Our Process For Migrating Firewall Network Security Cloud Security Firewall Proposal
This slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc.Take your presentations to the next level with our Our Process For Migrating Firewall Network Security Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights.
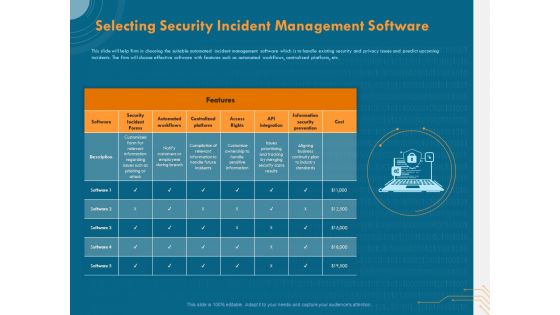
Cyber Security Implementation Framework Selecting Security Incident Management Software Microsoft PDF
Presenting this set of slides with name cyber security implementation framework selecting security incident management software microsoft pdf. The topics discussed in these slides are security incident forms, automated workflows, centralized platform, access rights, api integration, cost, information security prevention. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Impact Analysis Effective Security Management Ppt Show Design Inspiration PDF
Presenting this set of slides with name cyber security implementation framework impact analysis effective security management ppt show design inspiration pdf. This is a five stage process. The stages in this process are focus areas, security requirement, actual access violations, security incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Based Email Security Market Report Cyber Security Market Overview Ppt Infographics Format PDF
This slide shows a brief overview of the entire Cyber security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report cyber security market overview ppt infographics format pdf bundle. Topics like cyber security market overview can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Guards Of Bank Standing Outside For Security Ppt PowerPoint Presentation File Visual Aids PDF
Showcasing this set of slides titled security guards of bank standing outside for security ppt powerpoint presentation file visual aids pdf. The topics addressed in these templates are security guards of bank standing outside for security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
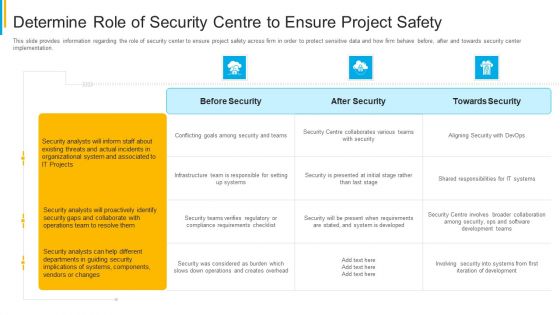
Project Security Administration IT Determine Role Of Security Centre To Ensure Project Safety Microsoft PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this project security administration it determine role of security centre to ensure project safety microsoft pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
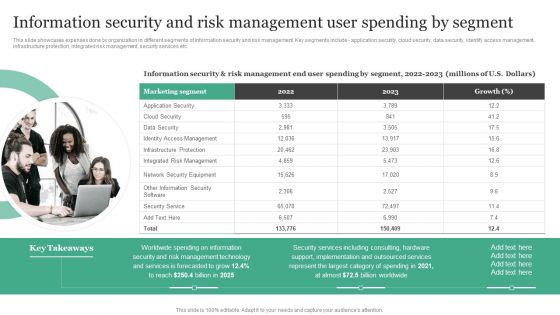
Information Security And Risk Management User Spending By Segment Information Security Risk Administration Slides PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc.Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security And Risk Management User Spending By Segment Information Security Risk Administration Slides PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Elements Of Information Technology Security Cloud Security Ppt Icon Gridlines PDF
This slide defines the cloud security element of network security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a elements of information technology security cloud security ppt icon gridlines pdf show pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elements of information technology security cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Introducing Security At Workplace To Ensure Assets Safety Introduction PDF
This slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Presenting developing firm security strategy plan introducing security at workplace to ensure assets safety introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security policy, organizational strategy, security mission statement, strategic security objectives. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
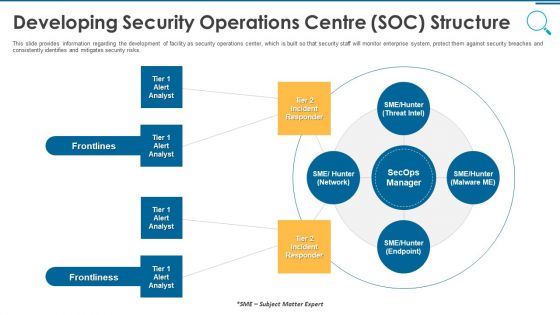
Information And Technology Security Operations Developing Security Operations Centre SOC Structure Slides PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting information and technology security operations developing security operations centre soc structure slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
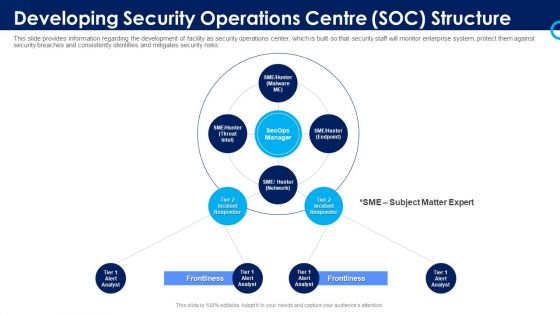
Organizational Security Solutions Developing Security Operations Centre SOC Structure Introduction PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting organizational security solutions developing security operations centre soc structure introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
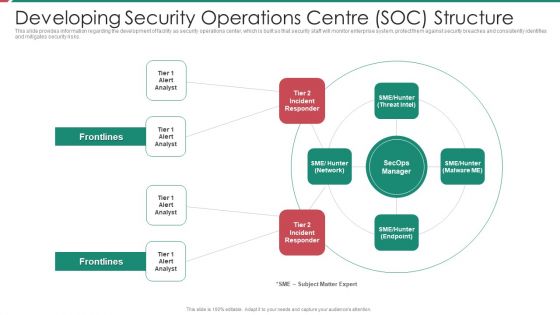
Security And Process Integration Developing Security Operations Centre SOC Structure Inspiration PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting security and process integration developing security operations centre soc structure inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
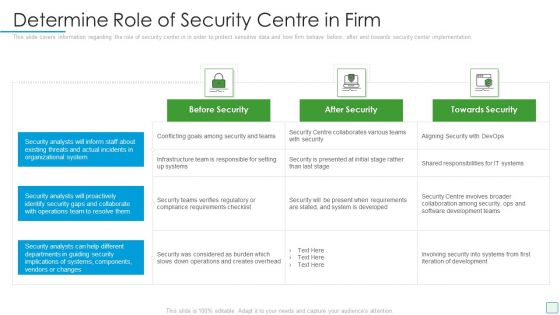
Developing Firm Security Strategy Plan Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan determine role of security centre in firm graphics pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
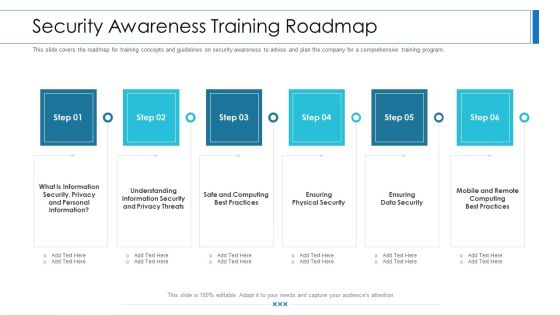
Workforce Security Realization Coaching Plan Security Awareness Training Roadmap Ppt Slides Visual Aids PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a workforce security realization coaching plan security awareness training roadmap ppt slides visual aids pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, privacy threats, physical security, data security, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
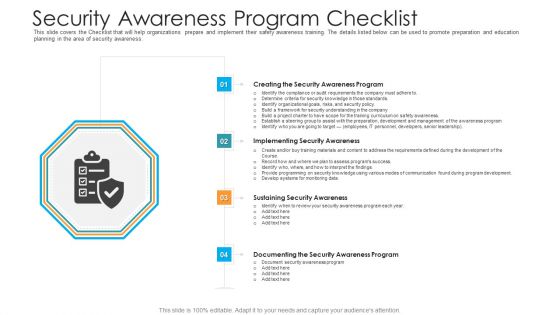
Security Awareness Program Checklist Hacking Prevention Awareness Training For IT Security Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting security awareness program checklist hacking prevention awareness training for it security background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating the security awareness program, implementing security awareness, sustaining security awareness, documenting the security awareness program. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
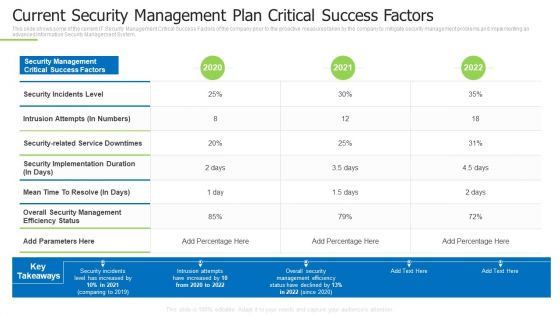
Techniques And Strategies To Reduce Security Management Risks Current Security Management Plan Ideas PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks current security management plan ideas pdf bundle. Topics like intrusion attempts, overall security management, security incidents level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cloud Information Security Types Of Cloud Security Solutions Ppt Icon Format Ideas PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. Presenting Cloud Information Security Types Of Cloud Security Solutions Ppt Icon Format Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Hybrid Cloud, Security Solutions, SMB Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
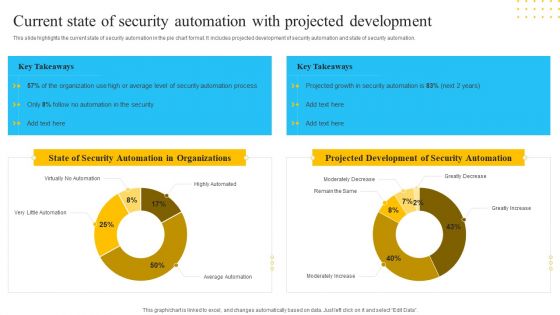
IT Security Automation Tools Integration Current State Of Security Automation With Projected Introduction PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Current State Of Security Automation With Projected Introduction PDF. Use them to share invaluable insights on State Security, Automation Organizations, Projected Development, Security Automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
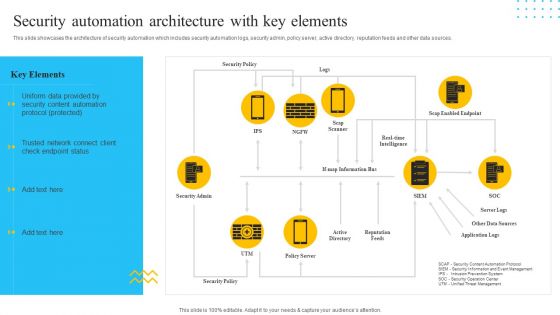
IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Presenting IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Policy, Security Admin, Reputation Feeds. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Building Trust With IoT Security Emerging Technologies Enhancing IoT Security And Privacy IoT SS V
This slide includes key technologies integrated with IoT ecosystem that helps to tackle cyberattacks and resolve any other issues. It includes technologies such as blockchain technology, artificial intelligence and machine learning and quantum computing. Make sure to capture your audiences attention in your business displays with our gratis customizable Building Trust With IoT Security Emerging Technologies Enhancing IoT Security And Privacy IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
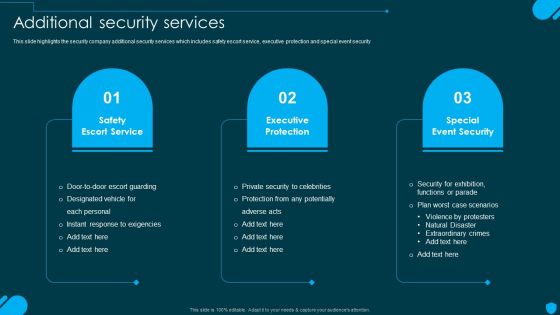
Security And Human Resource Services Business Profile Additional Security Services Rules PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Find a pre-designed and impeccable Security And Human Resource Services Business Profile Additional Security Services Rules PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Security Agency Business Profile Retail And Shopping Complex Security Services Background PDF
This is a Security Agency Business Profile Retail And Shopping Complex Security Services Background PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Retail Security, Shopping Complex Security, Theatre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
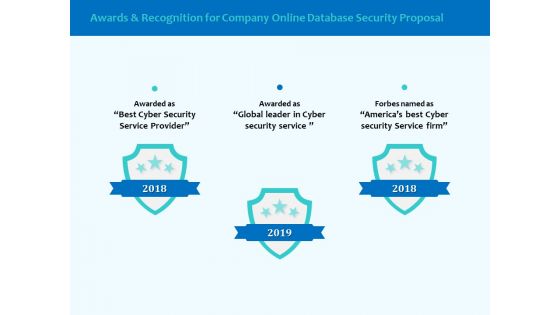
Best Data Security Software Awards And Recognition For Company Online Database Security Proposal Clipart PDF
Presenting this set of slides with name best data security software awards and recognition for company online database security proposal clipart pdf. This is a three stage process. The stages in this process are awarded as best cyber security service provider, awarded as global leader in cyber security service, forbes named as americas best cyber security service firm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
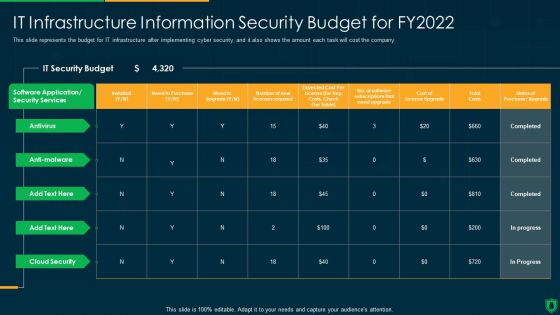
Info Security IT Infrastructure Information Security Budget For FY2022 Ppt PowerPoint Presentation File Pictures PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative info security it infrastructure information security budget for fy2022 ppt powerpoint presentation file pictures pdf bundle. Topics like it security budget, security services, cost license upgrade can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Security Company Strategic Partnerships Summary PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Security Company Strategic Partnerships Summary PDF. Use them to share invaluable insights on Security Application, Technology Partner, Google Assistant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
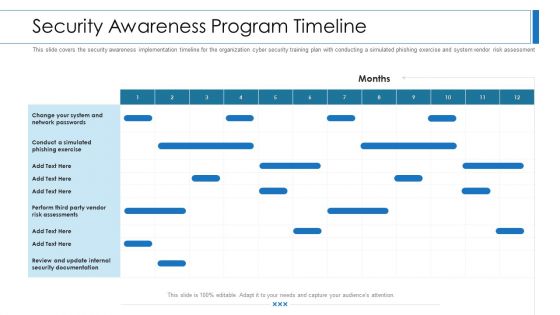
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Awareness Tracking Kpis Hacking Prevention Awareness Training For IT Security Background PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. Deliver an awe inspiring pitch with this creative security awareness tracking kpis hacking prevention awareness training for it security background pdf bundle. Topics like compliance, security culture, incident reduction can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
What Makes Cloud Security Different Cloud Computing Security IT Ppt Summary Icons PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi-tenant storage system. Deliver an awe inspiring pitch with this creative what makes cloud security different cloud computing security it ppt summary icons pdf bundle. Topics like convenience over security, centralization and multi tenant storage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Current Security Management Professional PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks current security management professional pdf Use them to share invaluable insights on potential insider threats, external security breaches, centric breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
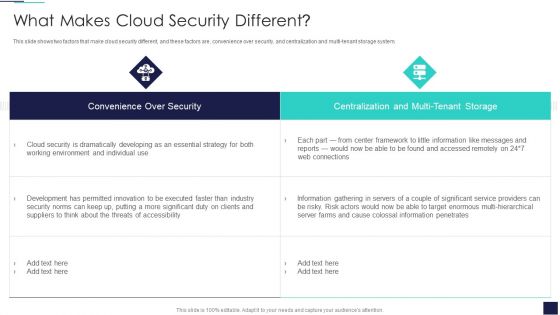
Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi-tenant storage system. Deliver an awe inspiring pitch with this creative Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF bundle. Topics like Cloud Security, Threats Accessibility, Risk Actors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
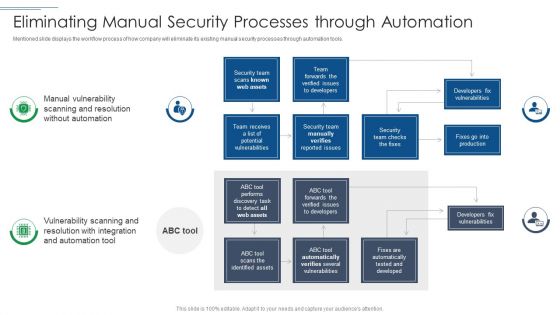
IT Security Risk Management Approach Introduction Eliminating Manual Security Processes Through Automation Guidelines PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Eliminating Manual Security Processes Through Automation Guidelines PDF bundle. Topics like Security Team, Developers Fix Vulnerabilities, Security Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
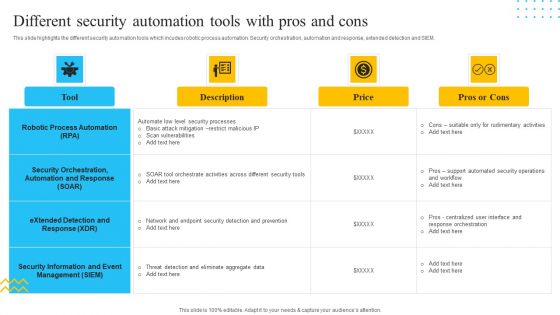
IT Security Automation Tools Integration Different Security Automation Tools With Pros And Cons Summary PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Different Security Automation Tools With Pros And Cons Summary PDF. Use them to share invaluable insights on Robotic Process Automation, Security Orchestration, Price and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Automation Tools Integration Security Automation Stages With Maturity Level Icons PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Stages With Maturity Level Icons PDF bundle. Topics like Security Automation, Maturity Level, Security Automation, Stages Opportunistic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
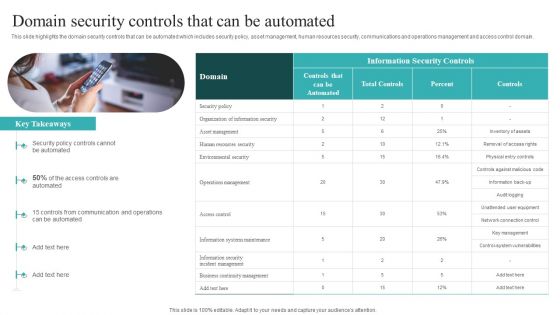
IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. There are so many reasons you need a IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
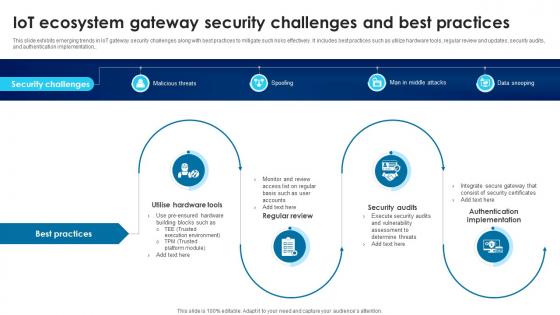
Building Trust With IoT Security IoT Ecosystem Gateway Security Challenges And Best Practices IoT SS V
This slide exhibits emerging trends in IoT gateway security challenges along with best practices to mitigate such risks effectively. It includes best practices such as utilize hardware tools, regular review and updates, security audits, and authentication implementation. Slidegeeks has constructed Building Trust With IoT Security IoT Ecosystem Gateway Security Challenges And Best Practices IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
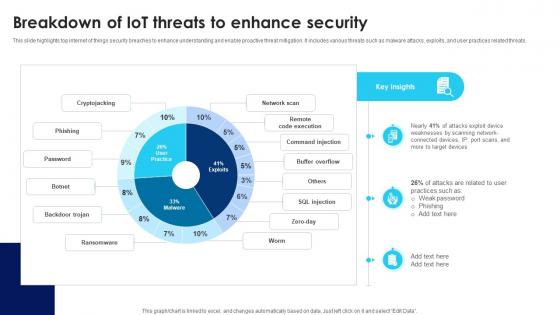
Building Trust With IoT Security Breakdown Of IoT Threats To Enhance Security IoT SS V
This slide highlights top internet of things security breaches to enhance understanding and enable proactive threat mitigation. It includes various threats such as malware attacks, exploits, and user practices related threats. Present like a pro with Building Trust With IoT Security Breakdown Of IoT Threats To Enhance Security IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cloud Security Checklist Networking Cloud Computing Security IT Ppt Show Samples PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting cloud security checklist networking cloud computing security it ppt show samples pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, mechanisms, security, critical data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
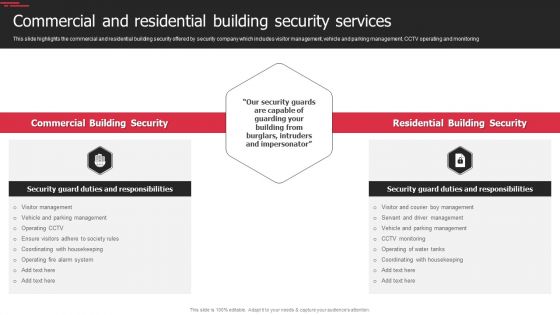
Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Automation To Analyze And Mitigate Cyberthreats Enterprise Network It Security Inspiration PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Security Automation To Analyze And Mitigate Cyberthreats Enterprise Network It Security Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
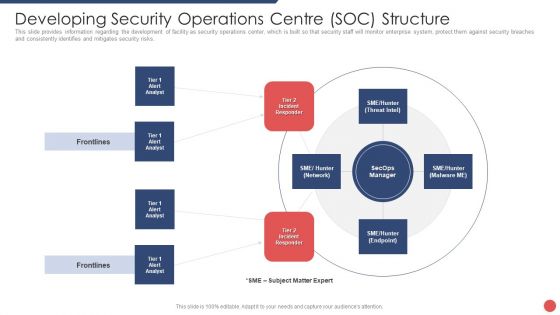
Security Functioning Centre Developing Security Operations Centre SOC Structure Guidelines PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Deliver and pitch your topic in the best possible manner with this security functioning centre developing security operations centre soc structure guidelines pdf. Use them to share invaluable insights on incident responder, analyst, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
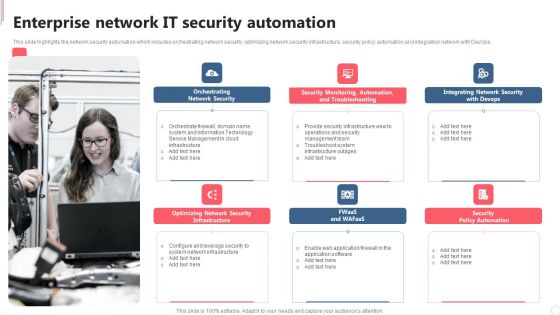
Cyber Security Automation Framework Enterprise Network IT Security Automation Background PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Boost your pitch with our creative Cyber Security Automation Framework Enterprise Network IT Security Automation Background PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Developing Firm Security Strategy Plan Addressing Different Security Priorities At Organization Background PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of fraud or threat protection, physical security and business continuity. This is a developing firm security strategy plan addressing different security priorities at organization background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fraud or threat protection, physical security, business continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workforce Security Realization Coaching Plan Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting workforce security realization coaching plan security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementing security awareness, sustaining security awareness, security awareness program. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Information And Technology Security Operations Assessment Of Security Maturity Spectrum Template PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative information and technology security operations assessment of security maturity spectrum template pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
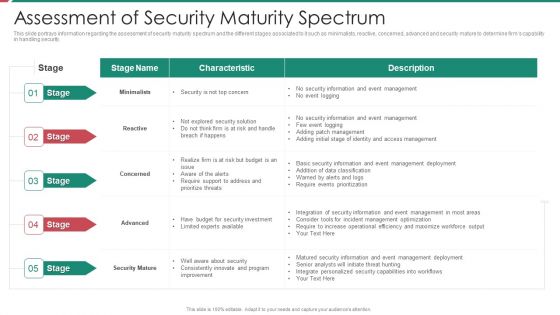
Security And Process Integration Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security and process integration assessment of security maturity spectrum slides pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
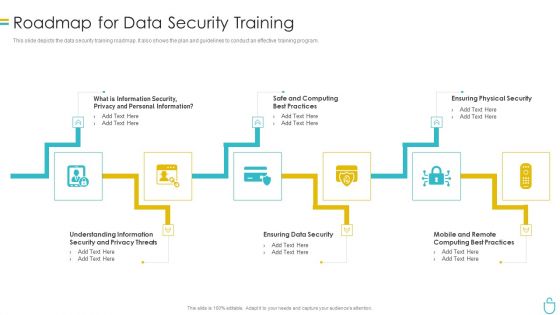
Information Security Roadmap For Data Security Training Ppt Model Show PDF
This slide depicts the data security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a information security roadmap for data security training ppt model show pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, ensuring data security, ensuring physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
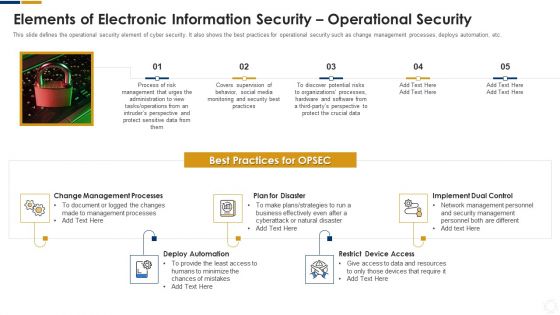
Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
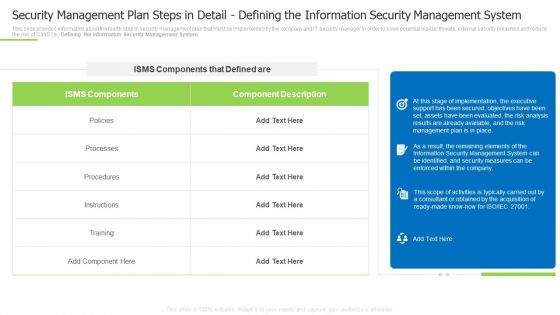
Security Management Plan Steps In Detail Defining The Information Security Management System Summary PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system summary pdf Use them to share invaluable insights on instructions, processes, implementation, the executive and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
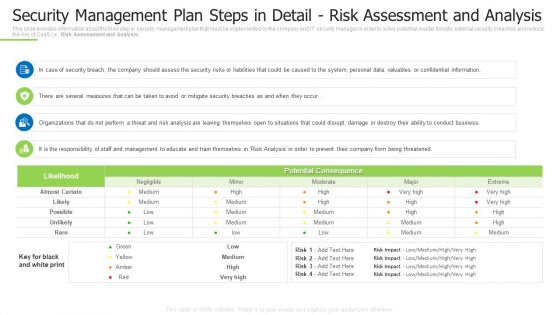
Techniques And Strategies To Reduce Security Management Risks Security Detail Risk Assessment And Analysis Template PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks security detail risk assessment and analysis template pdf Use them to share invaluable insights on security breach, perform a threat, several measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Risk Management Assessment Checklist Demonstration PDF
This slide shows a security risk management assessment checklist with multiple categories.Presenting techniques and strategies to reduce security management risks security risk management assessment checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, responding to security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
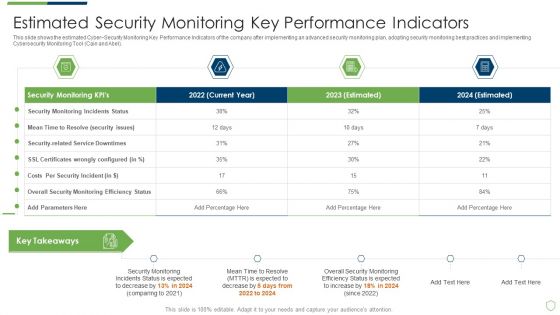
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
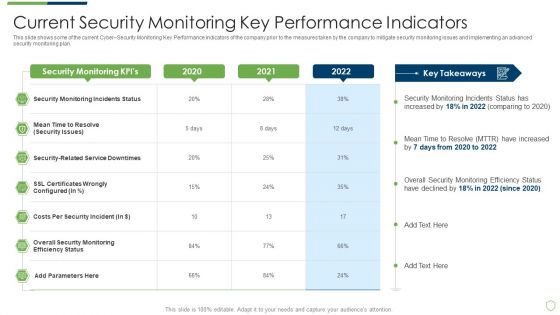
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Impacts Of Ineffective Information Technology Security Elements PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Presenting IT Security Automation Tools Integration Impacts Of Ineffective Information Technology Security Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cost Security, Data Breach, Security And Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Get a simple yet stunning designed Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
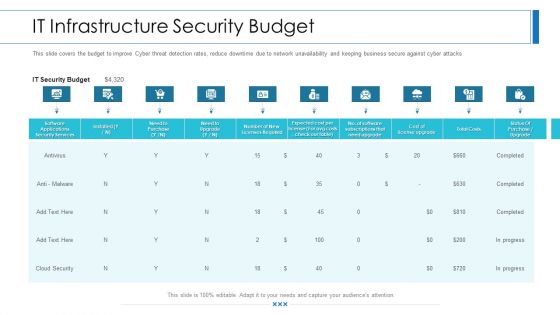
Workforce Security Realization Coaching Plan IT Infrastructure Security Budget Background PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan it infrastructure security budget background pdf bundle. Topics like software applications security services, business, it security budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Infrastructure Security Budget Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe inspiring pitch with this creative it infrastructure security budget hacking prevention awareness training for it security graphics pdf bundle. Topics like security, services, costs, cloud security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home