Safety Plan
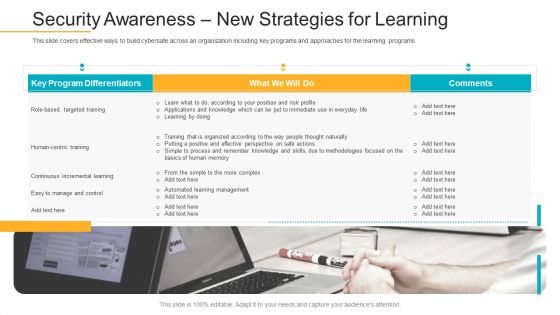
Data Breach Prevention Recognition Security Awareness New Strategies For Learning Download PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
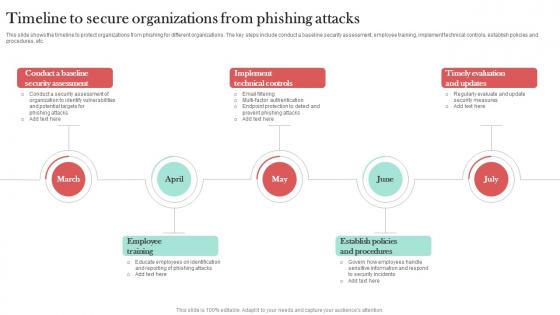
Timeline To Secure Organizations From Man In The Middle Phishing IT
This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. This Timeline To Secure Organizations From Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Timeline To Secure Organizations From Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
PowerPoint Backgrounds Diagram Chains Flowchart Ppt Process
PowerPoint Backgrounds Diagram Chains Flowchart PPT Process--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!

PowerPoint Design Slides Leadership Chains Flowchart Ppt Slidelayout
PowerPoint Design Slides Leadership Chains Flowchart PPT Slidelayout--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!
PowerPoint Presentation Graphic Chains Flowchart Ppt Slide
PowerPoint Presentation Graphic Chains Flowchart PPT Slide--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!
PowerPoint Presentation Success Chains Flowchart Ppt Layout
PowerPoint Presentation Success Chains Flowchart PPT Layout--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!
PowerPoint Slide Designs Growth Chains Flowchart Ppt Design
PowerPoint Slide Designs Growth Chains Flowchart PPT Design--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!
PowerPoint Slidelayout Graphic Chains Flowchart Ppt Slide
PowerPoint Slidelayout Graphic Chains Flowchart PPT Slide--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!
PowerPoint Templates Education Chains Flowchart Ppt Theme
PowerPoint Templates Education Chains Flowchart PPT Theme--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!
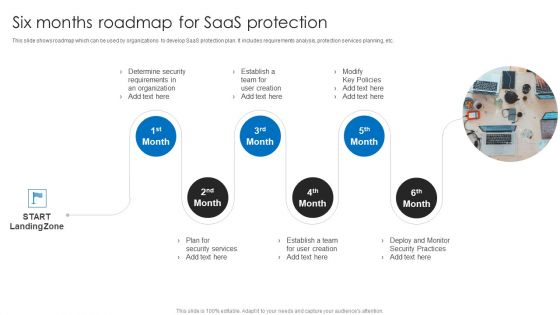
Six Months Roadmap For Saas Protection Brochure PDF
This slide shows roadmap which can be used by organizations to develop SaaS protection plan. It includes requirements analysis, protection services planning, etc. Persuade your audience using this Six Months Roadmap For Saas Protection Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Determine Security, Requirements, Organization. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

How Does Cloud Security Work Cloud Computing Security IT Ppt Show Graphics Design PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting how does cloud security work cloud computing security it ppt show graphics design pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data security, access management, governance, business continuity planning, legal compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
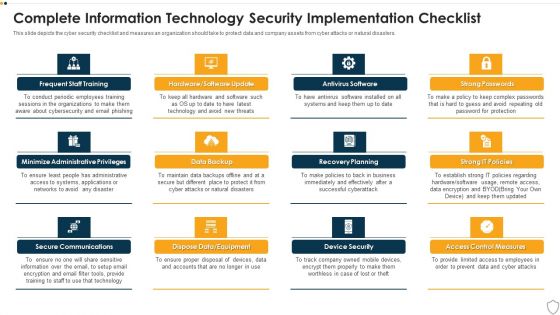
IT Security Complete Information Technology Security Implementation Checklist Ppt Inspiration Templates PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting it security complete information technology security implementation checklist ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like frequent staff training, secure communications, data backup, recovery planning, device security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
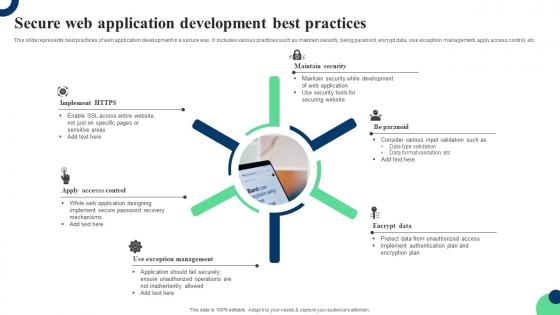
Secure Web Application Development Best Practices Ppt Inspiration Outline Pdf
This slide represents best practices of web application development in a secure way. It includes various practices such as maintain security, being paranoid, encrypt data, use exception management, apply access control, etc. Showcasing this set of slides titled Secure Web Application Development Best Practices Ppt Inspiration Outline Pdf. The topics addressed in these templates are Being Paranoid, Encrypt Data, Use Exception Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Info Security Elements Of Information Security Information Security Ppt PowerPoint Presentation Gallery Smartart PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a info security elements of information security information security ppt powerpoint presentation gallery smartart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, availability, integrity, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
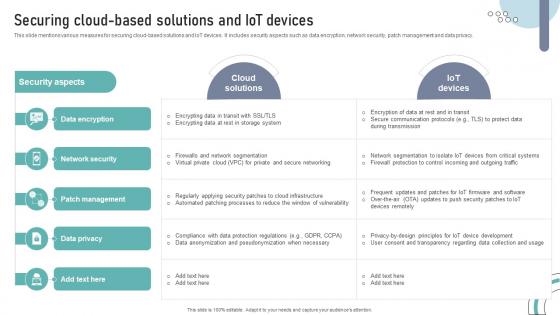
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Information Technology Functions Management Table Of Content Ppt Model Files PDF
This is a information technology functions management table of content ppt model files pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to infrastructure, asset management process, inventory and condition assessment, deterioration modeling, optimization and decision making, performance and cost functions, interdependence, resiliency and security, contract and workflow management, commissioning new facilities, capital budgeting, metrics and dashboard. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Mission Vision And Core Values Professional PDF
This slide highlights the security company long term and short term objectives which includes trust, collaboration, service, and innovation as base of core values. Presenting Manpower Corporate Security Business Profile Mission Vision And Core Values Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Mission, Vision, Core Values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
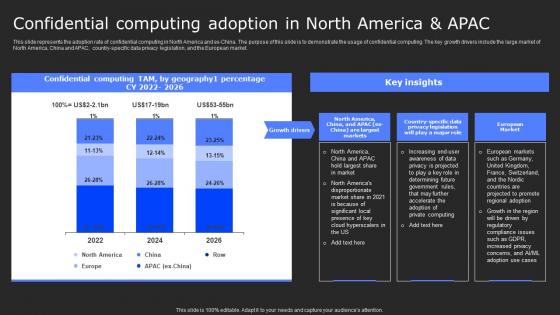
Confidential Computing Adoption In North Secure Computing Framework Template Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In North Secure Computing Framework Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In North Secure Computing Framework Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Security Threats Revenue Losses Cloud Computing Security IT Ppt Ideas Rules PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. This is a cloud security threats revenue losses cloud computing security it ppt ideas rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, cyber threats, revenue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness New Strategies For Learning Ppt Infographic Template Graphic Images PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver and pitch your topic in the best possible manner with this Security Awareness New Strategies For Learning Ppt Infographic Template Graphic Images Pdf. Use them to share invaluable insights on key program, targeted training, management, methodologies, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
5G Network Security Technologies To Overcome Threats Icons Pdf
This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks. Showcasing this set of slides titled 5G Network Security Technologies To Overcome Threats Icons Pdf. The topics addressed in these templates are Security Threat, Impact, Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
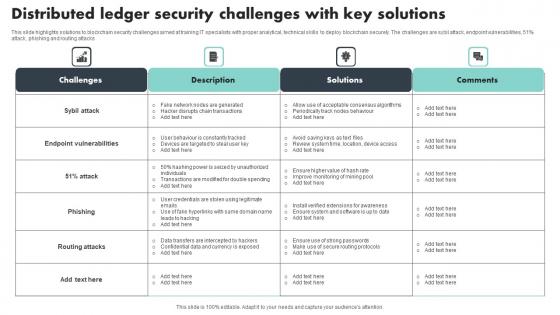
Distributed Ledger Security Challenges With Key Solutions Introduction Pdf
This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51percent attack, phishing and routing attacks Showcasing this set of slides titled Distributed Ledger Security Challenges With Key Solutions Introduction Pdf The topics addressed in these templates are Endpoint Vulnerabilities, Routing Attacks, Phishing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. This is a New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Applicable, Enforcement, Develop Good. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stock Photo Fighter Aircrafts On White Background PowerPoint Slide
This image is designed with fighter aircraft on white background. Download this image to display concepts like defence services, jet fighter, army planes etc. This image will help to express your views in your presentations.

Stock Photo Illustration Of Military Aircraft PowerPoint Slide
This image is designed with military aircraft on white background. Download this image to display concepts like defence services, jet fighter, army planes etc. This image will help to express your views in your presentations.

Stock Photo Jet Fighters High On Speed PowerPoint Slide
This image is designed with jet fighters on white background. Download this image to display concepts like defence services, jet fighter, army planes etc. This image will help to express your views in your presentations.

Strategies To Mitigate Cyber Security Risks Table Of Contents Ppt Inspiration Professional PDF
Presenting this set of slides with name strategies to mitigate cyber security risks table of contents ppt inspiration professional pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role personnel, cost associated to firm, impact analysis dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Challenges And Solutions To Big Data Monitoring Security Slides pdf
This slide highlights the various challenges faced while safeguarding big data analytics. This slide aims to help business analysts in determining issues with the security of big data analytics and overcome them through the solutions provided. Showcasing this set of slides titled Challenges And Solutions To Big Data Monitoring Security Slides pdf. The topics addressed in these templates are Challenges, Solutions, Difficulty Storing Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Global 5G Network Security Market Dynamics Designs Pdf
This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc. Showcasing this set of slides titled Global 5G Network Security Market Dynamics Designs Pdf. The topics addressed in these templates are Market Dynamics, Description. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
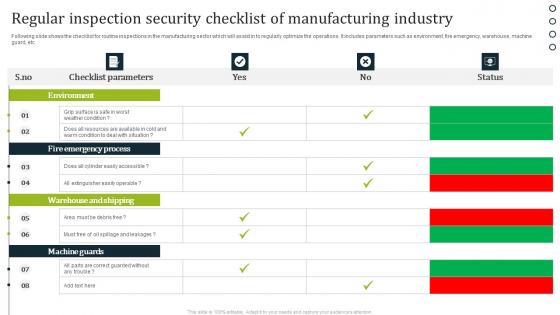
Regular Inspection Security Checklist Of Manufacturing Industry Demonstration Pdf
Following slide shows the checklist for routine inspections in the manufacturing sector which will assist in to regularly optimize the operations. It includes parameters such as environment, fire emergency, warehouse, machine guard, etc. Pitch your topic with ease and precision using this Regular Inspection Security Checklist Of Manufacturing Industry Demonstration Pdf. This layout presents information on Checklist Parameters, Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Confidential Computing Total Addressable Secure Computing Framework Themes Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Confidential Computing Total Addressable Secure Computing Framework Themes Pdf from Slidegeeks and deliver a wonderful presentation.
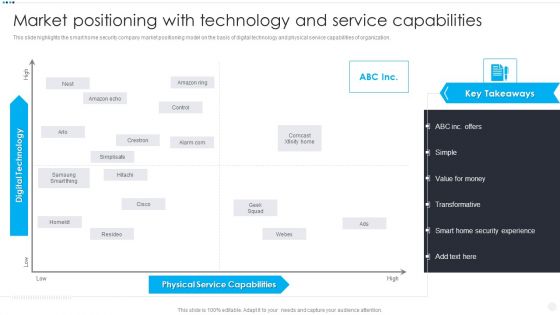
Smart Home Security Solutions Company Profile Market Positioning With Technology Information PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. This is a Smart Home Security Solutions Company Profile Market Positioning With Technology Information PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Physical Service Capabilities, Digital Technology High. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Savings And Keys Of House Real Estate PowerPoint Templates And PowerPoint Themes 1112
We present our Savings And Keys Of House Real Estate PowerPoint Templates And PowerPoint Themes 1112.Use our Money PowerPoint Templates because,Demonstrate how you think out of the box. Use our Security PowerPoint Templates because, To achieve sureshot success they need to come together at the right time, place and manner. Use our Success PowerPoint Templates because, Get your listeners to put on their thinking caps. Use our Business PowerPoint Templates because, Draw on its universal impact to highlight the similarities with your organizational structure and plans. Use our Future PowerPoint Templates because, Our template will help pinpoint their viability.Use these PowerPoint slides for presentations relating to Piggy bank and key of house, money, business, success, security, future. The prominent colors used in the PowerPoint template are Brown, Yellow, Black
Omnichannel Banking Services Platform Introduction To Secure Self Service Bill Payment Kiosks Icons PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Omnichannel Banking Services Platform Introduction To Secure Self Service Bill Payment Kiosks Icons PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Omnichannel Banking Services Platform Introduction To Secure Self Service Bill Payment Kiosks Icons PDF today and make your presentation stand out from the rest.

Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum safe cryptography, secure multi party computation, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf.

Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Slidegeeks is here to make your presentations a breeze with Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Checklist To Conduct Tokenization In Data Security PPT Presentation
This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Boost your pitch with our creative Checklist To Conduct Tokenization In Data Security PPT Presentation. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
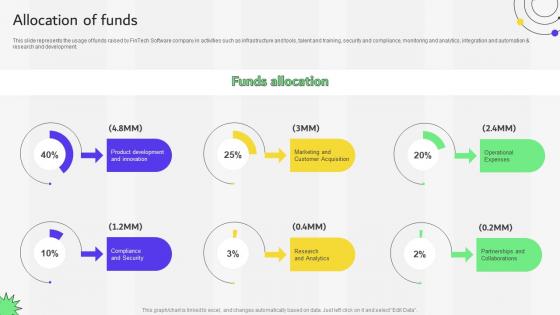
Allocation Of Funds Financial Services Provider Investor Funding Elevator Pitch Deck
This slide represents the usage of funds raised by FinTech Software company in activities such as infrastructure and tools, talent and training, security and compliance, monitoring and analytics, integration and automation and research and development. Find a pre-designed and impeccable Allocation Of Funds Financial Services Provider Investor Funding Elevator Pitch Deck. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Guide For Software Developers Service Agreement For Securing More Clients Mockup PDF
Purpose of this slide is to show service agreement that will assist service managers in gaining the attention on new clients. Sections covered in the agreement are parties, invoices, list of service and signature. Deliver an awe inspiring pitch with this creative guide for software developers service agreement for securing more clients mockup pdf bundle. Topics like service agreement, securing more clients can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CASB 2 0 IT Cloud Access Security Broker Use Cases
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Organizational Network Staff Learning Security Awareness New Strategies For Learning Rules PDF
This slide cover effective way to build cybersafe across on organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness new strategies for learning rules pdf bundle. Topics like human centric training, manage and control, targeted training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CASB 2 0 IT Cloud Access Security Broker Architectural Components
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. This modern and well-arranged CASB 2 0 IT Cloud Access Security Broker Architectural Components provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
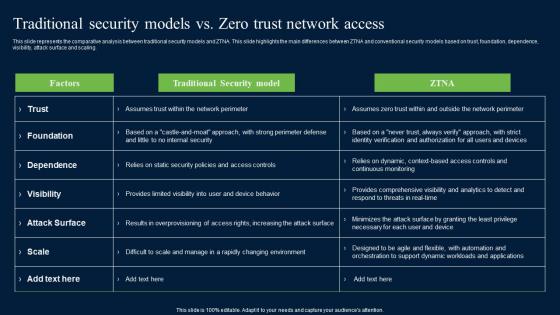
Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
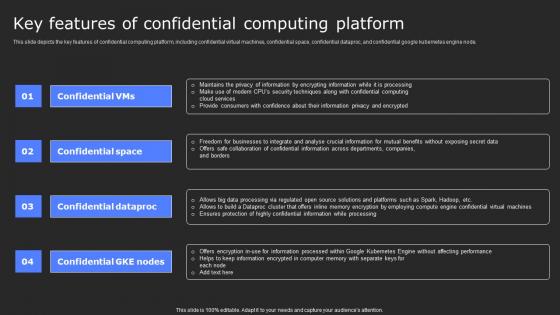
Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential google kubernetes engine node. Create an editable Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
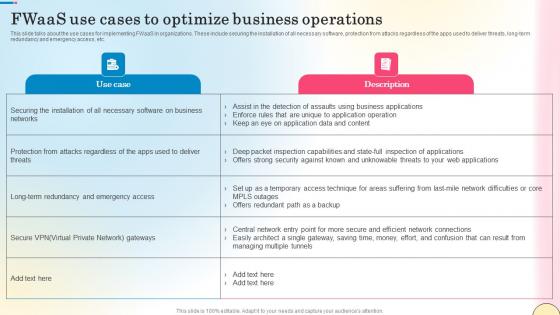
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Cyber Security Implementation Framework Table Of Contents Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting this set of slides with name cyber security implementation framework table of contents ppt powerpoint presentation icon portfolio pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role of personnel, cost associated to firm, impact analysis, dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security System In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security System In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security System that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
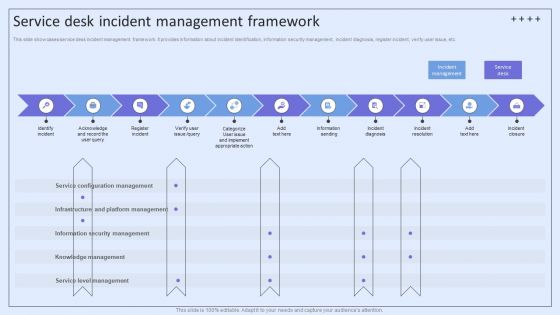
Integrating ITSM To Enhance Service Service Desk Incident Management Framework Download PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. Boost your pitch with our creative Integrating ITSM To Enhance Service Service Desk Incident Management Framework Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.
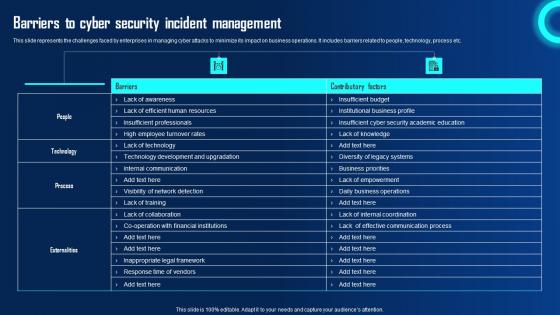
Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Checklist To Implement Effective Application Security Application Security Testing
This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. If you are looking for a format to display your unique thoughts, then the professionally designed Checklist To Implement Effective Application Security Application Security Testing is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Checklist To Implement Effective Application Security Application Security Testing and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF
The following slide showcases comparison of different cloud infrastructure securities which provides continuous monitoring and support for improvement and better management of security. It presents information related to Microsoft defender, identity manager, etc. Showcasing this set of slides titled Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF. The topics addressed in these templates are Software, Services, Security Layer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
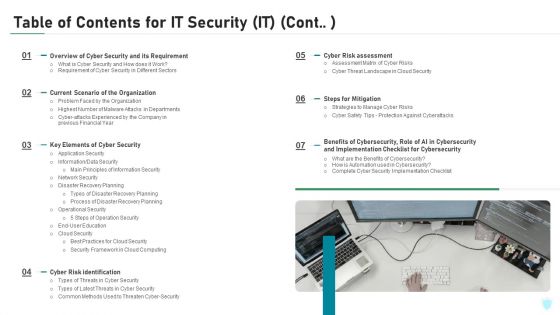
Table Of Contents For IT Security IT Cont Cyber Ppt Slides Graphics Tutorials PDF
This is a table of contents for it security it cont cyber ppt slides graphics tutorials pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, cyber security, implementation, financial, strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Serverless Computing Security Role Serverless Computing Modern Technology Ideas Pdf
The purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc. This modern and well arranged Serverless Computing Security Role Serverless Computing Modern Technology Ideas Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Stock Photo Business Strategy Execution Keys Of Success And Growth Clipart
Delight Them With Our Stock Photo Business Strategy Execution Keys Of Success And Growth Clipart Powerpoint Templates. Your Audience Will Be Ecstatic. Our Security Powerpoint Templates Are Created Cost Effective. They Understand The Need For Economy.

 Home
Home