Safety Plan

Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
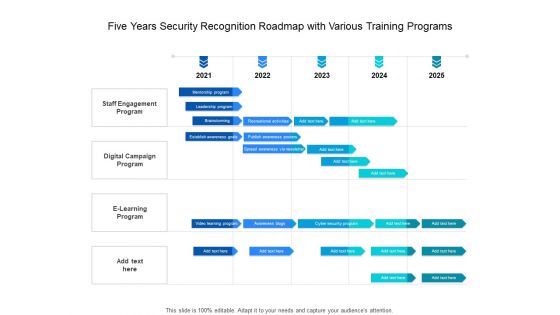
Five Years Security Recognition Roadmap With Various Training Programs Slides
Presenting the five years security recognition roadmap with various training programs slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
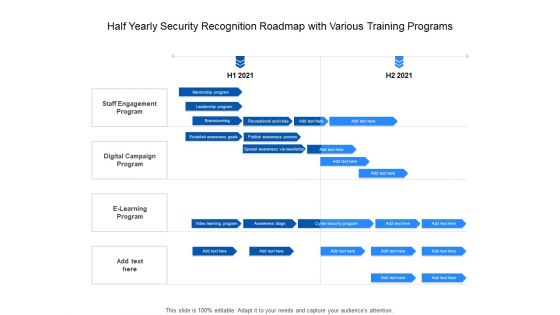
Half Yearly Security Recognition Roadmap With Various Training Programs Themes
Presenting the half yearly security recognition roadmap with various training programs themes. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
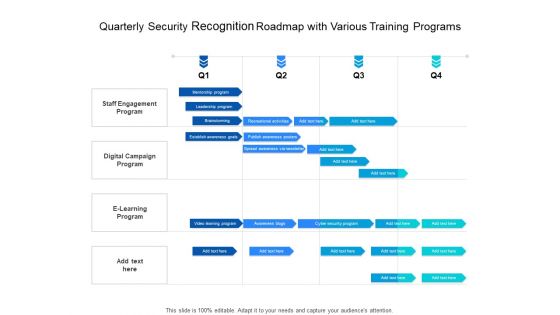
Quarterly Security Recognition Roadmap With Various Training Programs Download
Presenting the quarterly security recognition roadmap with various training programs download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
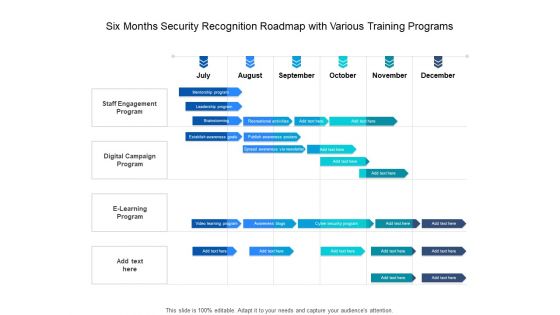
Six Months Security Recognition Roadmap With Various Training Programs Summary
Presenting the six months security recognition roadmap with various training programs summary. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
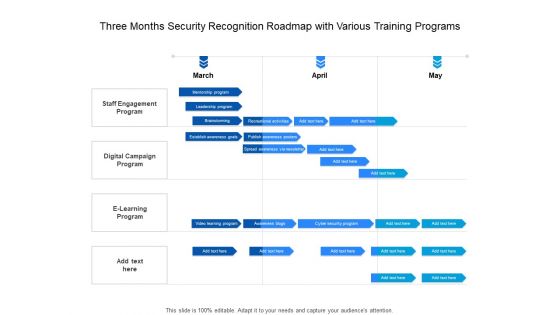
Three Months Security Recognition Roadmap With Various Training Programs Elements
Presenting the three months security recognition roadmap with various training programs elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Strategies To Mitigate Cyber Security Risks Agenda For Cyber Security Risks Ppt Infographics Graphics Design PDF
Presenting this set of slides with name strategies to mitigate cyber security risks agenda for cyber security risks ppt infographics graphics design pdf. This is a one stage process. The stages in this process are determining roles and responsibilities, senior management, executives responsible, risk management, presenting optimize cybersecurity, risk framework. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Under Construction Real Estate PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with contemporary style house under construction on blueprints with energy ratings

Under Construction Real Estate PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with contemporary style house under construction on blueprints with energy ratings
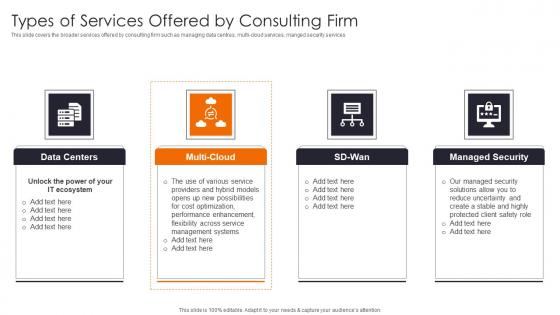
Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf
This slide covers the broader services offered by consulting firm such as managing data centres, multi cloud services, manged security services If you are looking for a format to display your unique thoughts, then the professionally designed Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
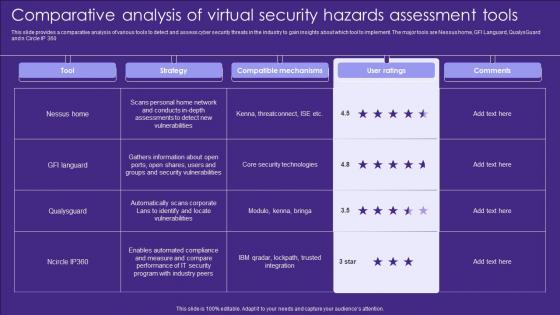
Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf
This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Pitch your topic with ease and precision using this Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf. This layout presents information on Strategy, Compatible Mechanisms, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Agenda For Cloud Computing Security IT Ppt Infographic Template Inspiration PDF
Presenting agenda for cloud computing security it ppt infographic template inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cloud security, service, architecture, organizations, responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Application Services Company Outline Information Technology Services Ideas PDF
The slide showcases range of information technology services offered by company for customers. It depicts managed services, intelligent business services, digital experience, solution engineering, innovation services and technology and security advisory. Presenting IT Application Services Company Outline Information Technology Services Ideas PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security Advisory, Managed Services, Intelligent Business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Model Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Traditional Security Models Vs Zero Trust Network Access and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
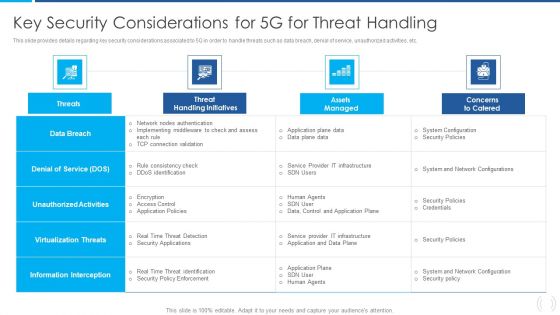
Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF bundle. Topics like Virtualization Threats, Information Interception, Unauthorized Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
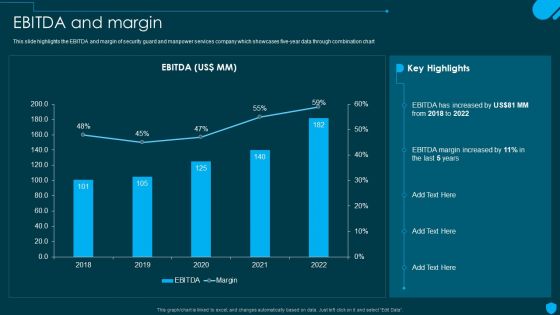
Security And Human Resource Services Business Profile EBITDA And Margin Ideas PDF
This slide highlights the EBITDA and margin of security guard and manpower services company which showcases five-year data through combination chart. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security And Human Resource Services Business Profile EBITDA And Margin Ideas PDF can be your best option for delivering a presentation. Represent everything in detail using Security And Human Resource Services Business Profile EBITDA And Margin Ideas PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
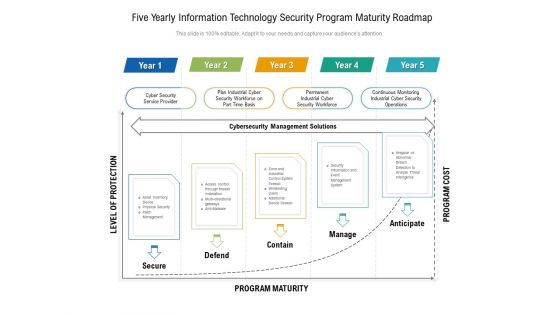
Five Yearly Information Technology Security Program Maturity Roadmap Information
Presenting the five yearly information technology security program maturity roadmap information. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
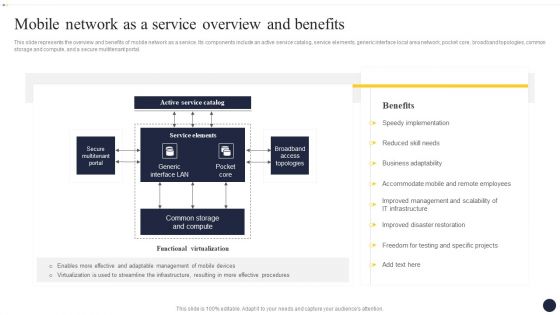
Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. If you are looking for a format to display your unique thoughts, then the professionally designed Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
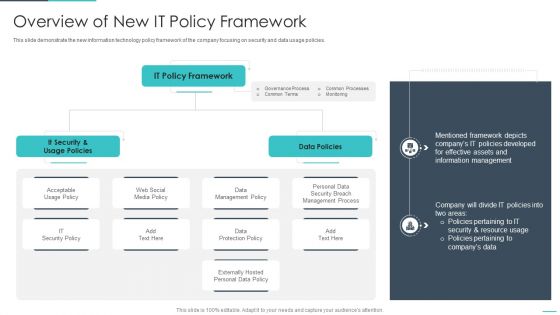
Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Technologies Used To Protect Data In Use Secure Multi Party Template Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Technologies Used To Protect Data In Use Secure Multi Party Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Technologies Used To Protect Data In Use Secure Multi Party Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Risk Assessment Dashboard For Securing Supply Chain System Graphics PDF
This slide demonstrates risk assessment matrix for improving the efficiency of industrial supply chain system. It includes supplier risks, service type and service health etc.Showcasing this set of slides titled Risk Assessment Dashboard For Securing Supply Chain System Graphics PDF The topics addressed in these templates are Operation Compliance, Privacy Compilation, External Score All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V
This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making. The Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF
The following slide highlights components of managed security service along with the expected cost. Software, antivirus and security monitoring are some of the components which will assist the organization in improving its IT security. Showcasing this set of slides titled Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF. The topics addressed in these templates are Security Monitoring, Antivirus, Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
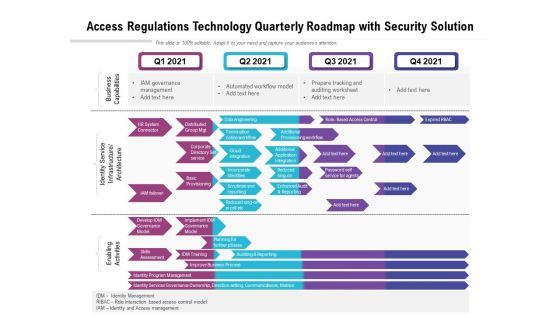
Access Regulations Technology Quarterly Roadmap With Security Solution Graphics
We present our access regulations technology quarterly roadmap with security solution graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched access regulations technology quarterly roadmap with security solution graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Four Quarter Data Encryption For Security Career Roadmap Sample
We present our four quarter data encryption for security career roadmap sample. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched four quarter data encryption for security career roadmap sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
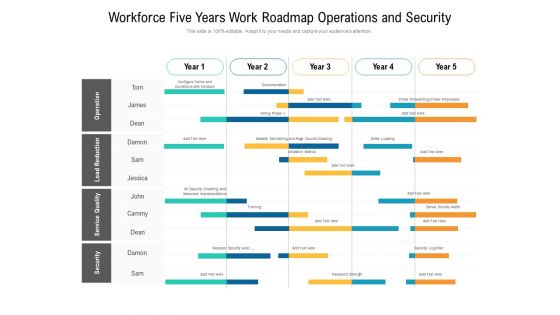
Workforce Five Years Work Roadmap Operations And Security Pictures
We present our workforce five years work roadmap operations and security pictures. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched workforce five years work roadmap operations and security pictures in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Enterprise Information Technology Security Roadmap Through Identification Summary
We present our half yearly enterprise information technology security roadmap through identification summary. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly enterprise information technology security roadmap through identification summary in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
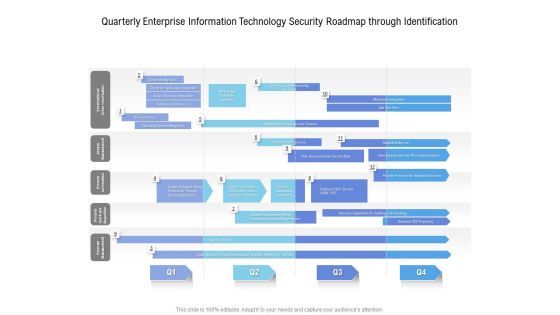
Quarterly Enterprise Information Technology Security Roadmap Through Identification Topics
We present our quarterly enterprise information technology security roadmap through identification topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly enterprise information technology security roadmap through identification topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Enterprise Information Technology Security Roadmap Through Identification Infographics
We present our six months enterprise information technology security roadmap through identification infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise information technology security roadmap through identification infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
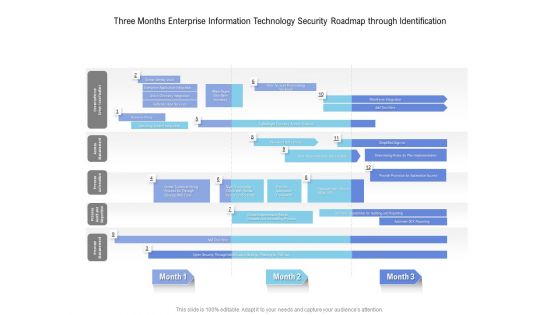
Three Months Enterprise Information Technology Security Roadmap Through Identification Introduction
We present our three months enterprise information technology security roadmap through identification introduction. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months enterprise information technology security roadmap through identification introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
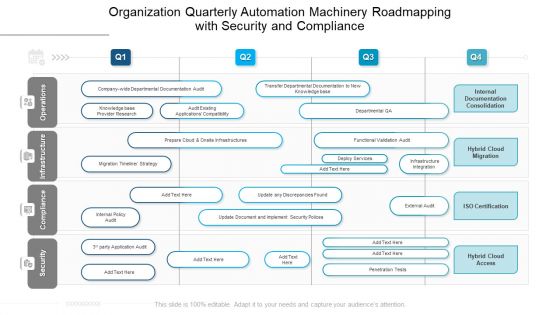
Organization Quarterly Automation Machinery Roadmapping With Security And Compliance Brochure
We present our organization quarterly automation machinery roadmapping with security and compliance brochure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched organization quarterly automation machinery roadmapping with security and compliance brochure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
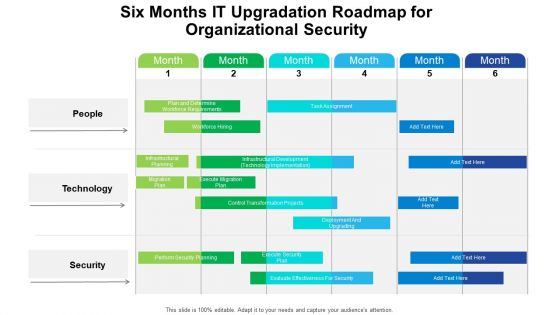
Six Months IT Upgradation Roadmap For Organizational Security Structure
We present our six months it upgradation roadmap for organizational security structure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months it upgradation roadmap for organizational security structure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cybersecurity Cyber Threat Landscape In Cloud Security Ppt Inspiration Microsoft PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this cybersecurity cyber threat landscape in cloud security ppt inspiration microsoft pdf. Use them to share invaluable insights on business disruption, strategic plans, reputation damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample
This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Boost your pitch with our creative Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document
Presenting you an exemplary Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.
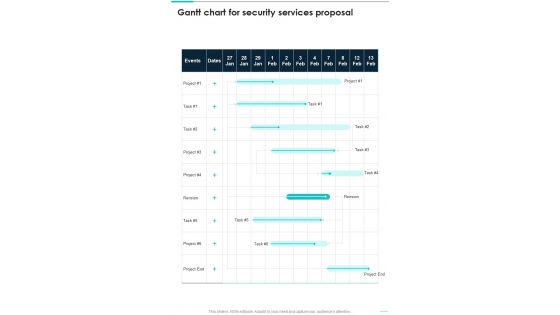
Gantt Chart For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart For Security Services Proposal One Pager Sample Example Document brilliant piece now.

Secured Digital Currency Transaction Five Year Roadmap Themes
We present our secured digital currency transaction five year roadmap themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched secured digital currency transaction five year roadmap themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Five Year Cyber Data Security Career Growth Roadmap Formats
We present our five year cyber data security career growth roadmap formats. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five year cyber data security career growth roadmap formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
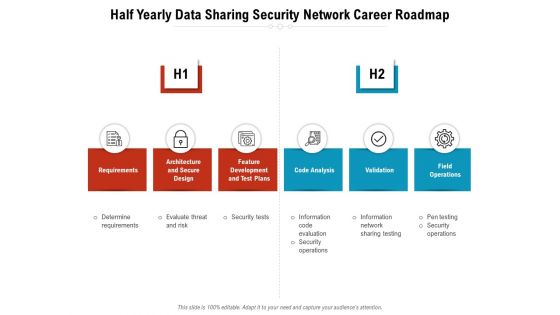
Half Yearly Data Sharing Security Network Career Roadmap Rules
We present our half yearly data sharing security network career roadmap rules. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly data sharing security network career roadmap rules in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
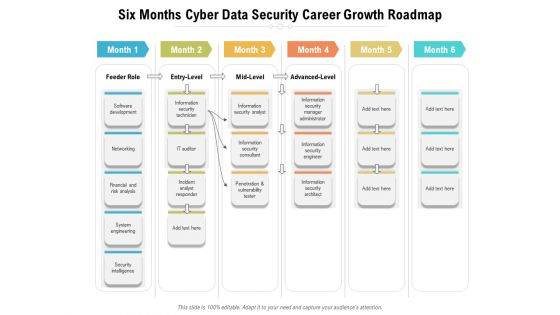
Six Months Cyber Data Security Career Growth Roadmap Diagrams
We present our six months cyber data security career growth roadmap diagrams. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months cyber data security career growth roadmap diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
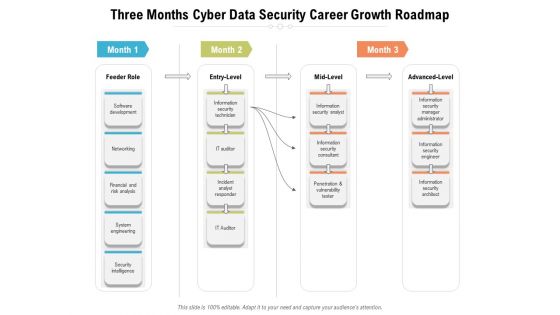
Three Months Cyber Data Security Career Growth Roadmap Diagrams
We present our three months cyber data security career growth roadmap diagrams. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched three months cyber data security career growth roadmap diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Five Year Organization Product Development Roadmap With Advanced Security Sample
We present our five year organization product development roadmap with advanced security sample. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five year organization product development roadmap with advanced security sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Five Years Engineering Roadmap With Security And Compliance Clipart
We present our five years engineering roadmap with security and compliance clipart. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five years engineering roadmap with security and compliance clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
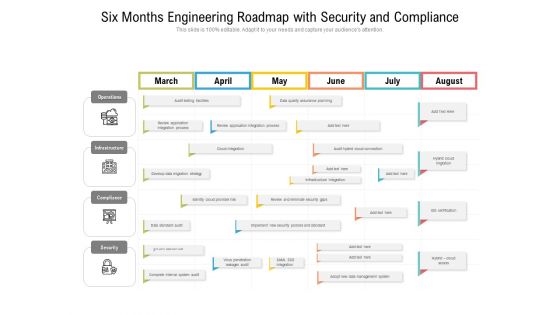
Six Months Engineering Roadmap With Security And Compliance Clipart
We present our six months engineering roadmap with security and compliance clipart. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months engineering roadmap with security and compliance clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
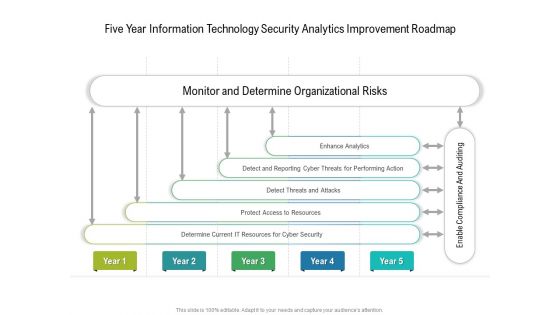
Five Year Information Technology Security Analytics Improvement Roadmap Infographics
We present our five year information technology security analytics improvement roadmap infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year information technology security analytics improvement roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Security Strategic Process Management Four Quarter Timeline Diagrams
We present our cyber security strategic process management four quarter timeline diagrams. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security strategic process management four quarter timeline diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Effective Digital Security Five Year Strategic Timeline Formats
We present our effective digital security five year strategic timeline formats. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched effective digital security five year strategic timeline formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Smart Home Security Solutions Company Profile Structure PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Smart Home Security Solutions Company Profile Structure PDF. Use them to share invaluable insights on Key Solutions Services, Intelligent Smart Devices, Operating System Integration, Service Delivery Model and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Effective Digital Security Metrics And Metrics Categories Microsoft Pdf
Pitch your topic with ease and precision using this Effective Digital Security Metrics And Metrics Categories Microsoft Pdf This layout presents information on Security Program Maturity, Metric Category, Sensitive Data Scanning It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
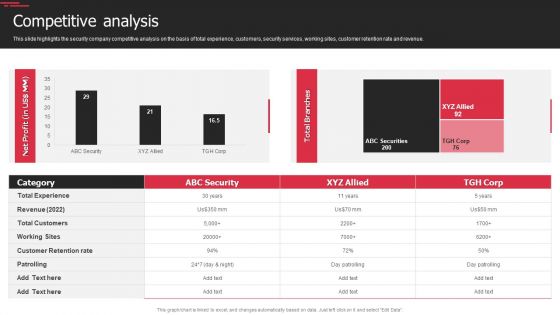
Security Agency Business Profile Competitive Analysis Designs PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Competitive Analysis Designs PDF bundle. Topics like Revenue, Customer Retention Rate, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Policies And Procedures Security Awareness And Training Policy Overview Guidelines PDF
This slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Take your projects to the next level with our ultimate collection of IT Policies And Procedures Security Awareness And Training Policy Overview Guidelines PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
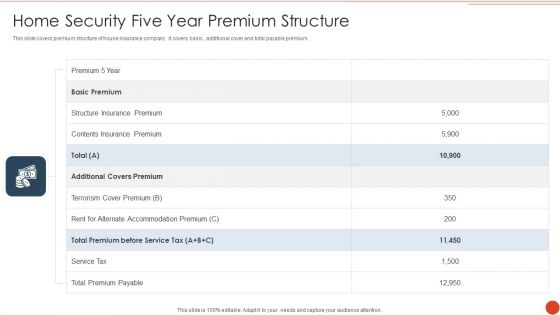
Home Security Five Year Premium Structure Graphics PDF
This slide covers premium structure of house insurance company . it covers basic , additional cover and total payable premium. Showcasing this set of slides titled Home Security Five Year Premium Structure Graphics PDF. The topics addressed in these templates are Additional Covers Premium, Service Tax, Total Premium Payable. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
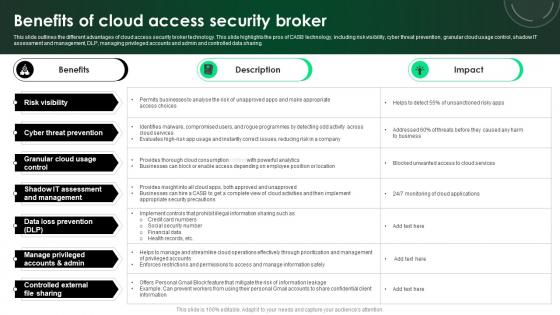
CASB 2 0 IT Benefits Of Cloud Access Security Broker
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. There are so many reasons you need a CASB 2 0 IT Benefits Of Cloud Access Security Broker. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
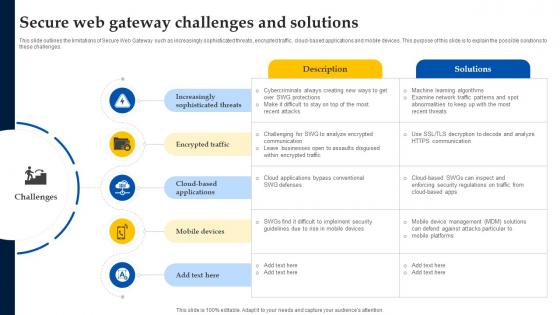
Web Access Control Solution Secure Web Gateway Challenges And Solutions
This slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges. Want to ace your presentation in front of a live audience Our Web Access Control Solution Secure Web Gateway Challenges And Solutions can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

 Home
Home