Safety Improvement Plan

Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS
Following slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Showcasing this set of slides titled Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS. The topics addressed in these templates are Data Security Tools Evaluation, Data Security Tools Used, Budget Allocated For Tools, Data Security Software Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
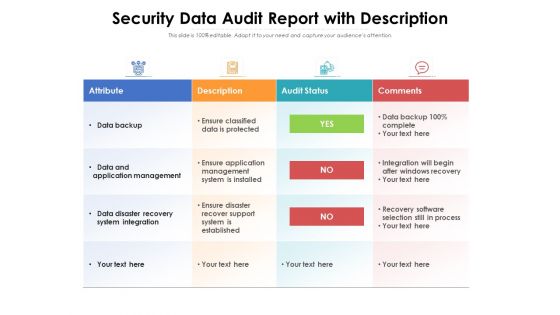
Security Data Audit Report With Description Ppt PowerPoint Presentation Inspiration Example PDF
Showcasing this set of slides titled security data audit report with description ppt powerpoint presentation inspiration example pdf. The topics addressed in these templates are attribute, description, audit status, comments, data backup, data and application management, data disaster recovery system integration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Emerging Technology Trends For Business Growth Diagrams PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Emerging Technology Trends For Business Growth Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Emerging Technology Trends For Business Growth Diagrams PDF.
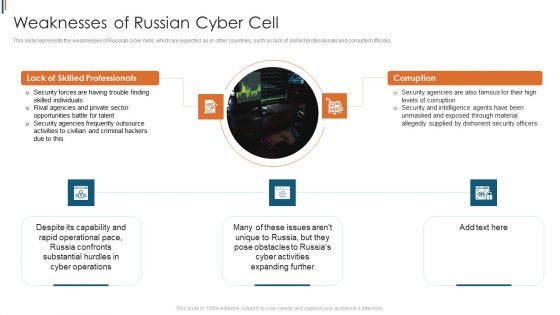
Ukraine Cyberwarfare Weaknesses Of Russian Cyber Cell Brochure Pdf
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials. Presenting ukraine cyberwarfare weaknesses of russian cyber cell brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security forces are having trouble finding skilled individuals, rival agencies and private sector opportunities battle for talent, security agencies frequently outsource activities to civilian and criminal hackers due to this. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
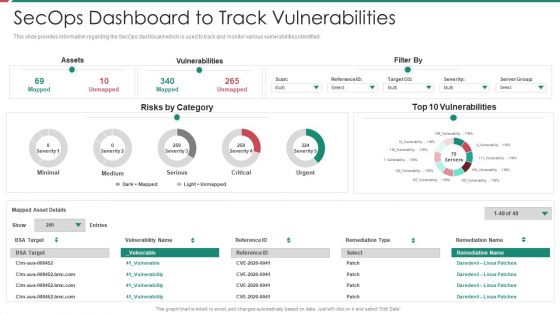
Security And Process Integration Secops Dashboard To Track Vulnerabilities Mockup PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this security and process integration secops dashboard to track vulnerabilities mockup pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Deploying AI To Enhance Global Spending On Industrial Internet Of Things Technologies Clipart PDF
This slide depicts the global spending on the industrial internet of things technologies from 2019 to 2027. The market is segmented as IoT security, IoT hardware, IoT services, IoT software and total. This modern and well-arranged Deploying AI To Enhance Global Spending On Industrial Internet Of Things Technologies Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Digital Transformation Strategy Roadmap Customer Experience Mapping Ppt PowerPoint Presentation Inspiration Maker PDF
Presenting this set of slides with name digital transformation strategy roadmap customer experience mapping ppt powerpoint presentation inspiration maker pdf. This is a seven stage process. The stages in this process are blood glucose levels, securely transmitted, progress reports, consultation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Stages Of SRE Pipeline Ppt PowerPoint Presentation File Objects PDF
The following slide showcases the various phases involved in SRE to develop secured IT systems. It includes elements such as continuous integration, deployment, auto canary analysis, operate and optimize etc. Persuade your audience using this Stages Of SRE Pipeline Ppt PowerPoint Presentation File Objects PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Deploy To Prod, Operate And Optimize, Continuous Deployment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Reverse Proxy Server IT What Is A Proxy Server Ppt Infographics Infographics PDF
This slide depicts the meaning of proxy servers, where it is used, and how it manages traffic based on pre-defined policies and blocks the unknown traffic. This is a reverse proxy server it what is a proxy server ppt infographics infographics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, unfamiliar traffic, enforce security protocols, controls traffic based. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
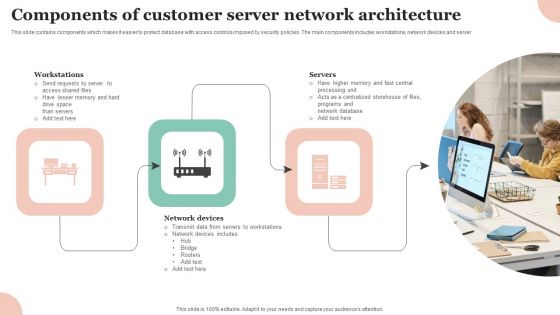
Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
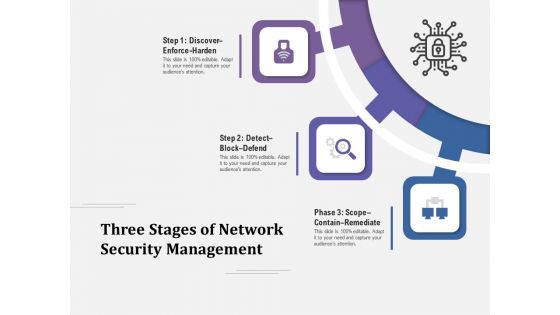
Three Stages Of Network Security Management Ppt PowerPoint Presentation Layouts Influencers PDF
Presenting three stages of network security management ppt powerpoint presentation layouts influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Three Phases Of Network Security Issues Ppt PowerPoint Presentation Icon Portrait PDF
Presenting three phases of network security issues ppt powerpoint presentation icon portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
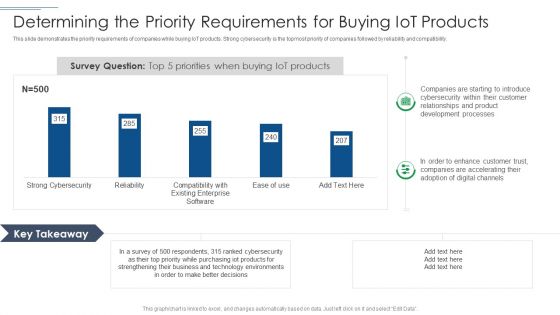
IT Security Risk Management Approach Introduction Determining The Priority Requirements Diagrams PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Determining The Priority Requirements Diagrams PDF bundle. Topics like Development Processes, Technology Environments, Purchasing Iot Products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
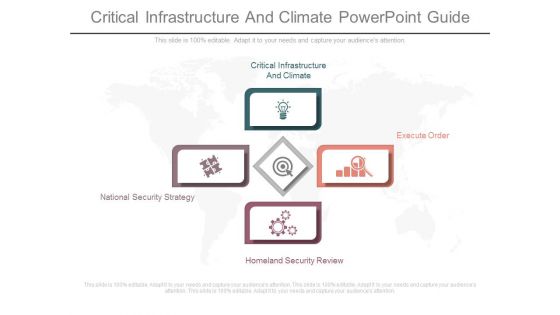
Critical Infrastructure And Climate Powerpoint Guide
This is a critical infrastructure and climate powerpoint guide. This is a four stage process. The stages in this process are critical infrastructure and climate, national security strategy, execute order, homeland security review.

Major Stream Processing Challenges And Solutions To Overcome Themes PDF
The following slide outlines various data ingestion challenges faced by the company. The key challenges are manual data ingestion process, high budget, and security issue. It also covers information about multiple solutions which can be used to overcome the challenges. Presenting Major Stream Processing Challenges And Solutions To Overcome Themes PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Challenges, Solutions, Manual Data, Ingestion Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Detailed Requirements Collection Chart Of IT Companies Ppt Summary Show PDF
This slide shows information technology IT company requirements collection form. It provides information such as application usage, networking issues, operating system, capabilities, features, etc. Presenting Detailed Requirements Collection Chart Of IT Companies Ppt Summary Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Each Problem, Problem Security, Market. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
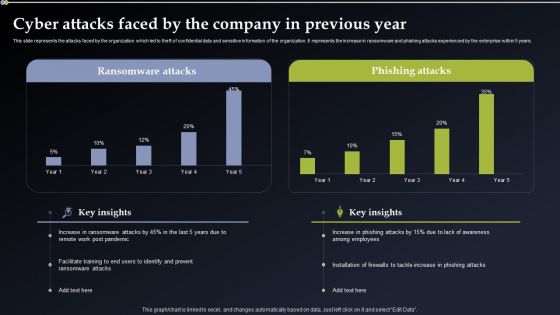
Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Scm Process With Procurement Warehouse And Security Ppt PowerPoint Presentation Infographic Template Structure PDF
Pitch your topic with ease and precision using this SCR process with procurement warehouse and security ppt powerpoint presentation infographic template structure pdf. This layout presents information on procurement, warehouse, evaluation for correct products in shipment, inbound shipping schedule update, procuring and notifying for shipping. It is also available for immediate download and adjustment. So, changes can be made in the colour, design, graphics or any other component to create a unique layout.
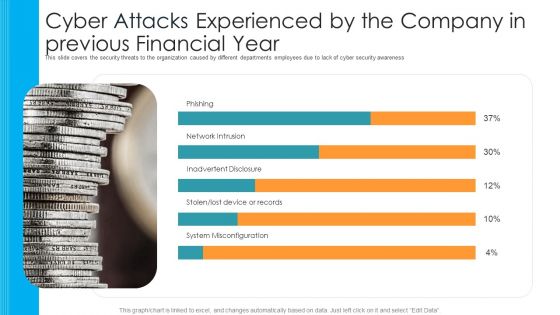
Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Employee Benefits Perks And Bonuses Ppt PowerPoint Presentation Outline Graphic Tips
This is a employee benefits perks and bonuses ppt powerpoint presentation outline graphic tips. This is a six stage process. The stages in this process are employees allowance, meal breaks, social security.

Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. If you are looking for a format to display your unique thoughts, then the professionally designed Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
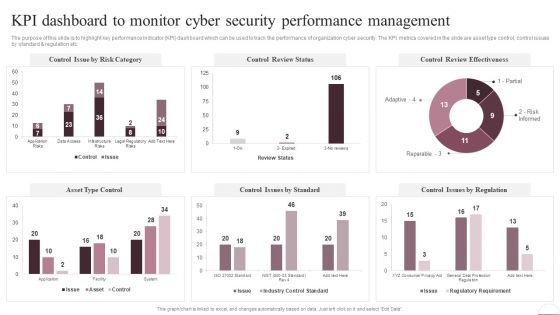
Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard AND regulation etc. This Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
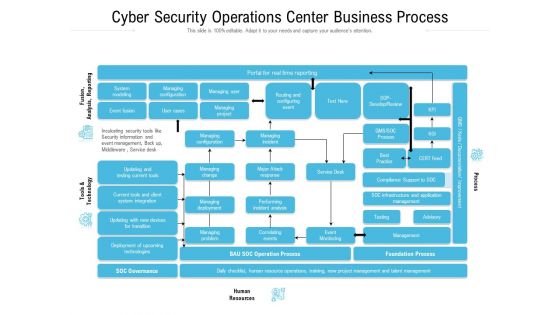
Cyber Security Operations Center Business Process Ppt Slides Graphic Images PDF
Showcasing this set of slides titled cyber security operations center business process ppt slides graphic images pdf. The topics addressed in these templates are infrastructure, management, business, process, resources. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
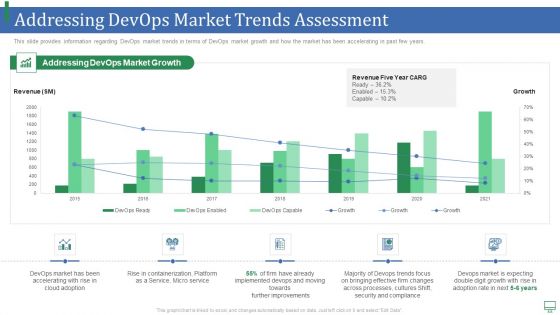
Addressing Devops Market Trends Assessment Portrait PDF
This slide provides information regarding DevOps market trends in terms of DevOps market growth and how the market has been accelerating in past few years. Deliver an awe inspiring pitch with this creative addressing devops market trends assessment portrait pdf bundle. Topics like service, implemented, processes, security, growth can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

MDM Strategies At Office Mobile Device Management For Android Platform Introduction PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Presenting MDM Strategies At Office Mobile Device Management For Android Platform Introduction PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Application Control, Mandatary Installed, Theft Protection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Computer Security Incident Handling Dashboard Incident Tracking Ppt Gallery Infographics PDF
Presenting this set of slides with name computer security incident handling dashboard incident tracking ppt gallery infographics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, user application hardening, daily backup of important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
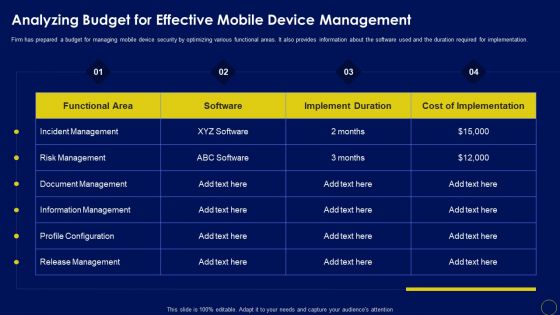
Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Explore a selection of the finest Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
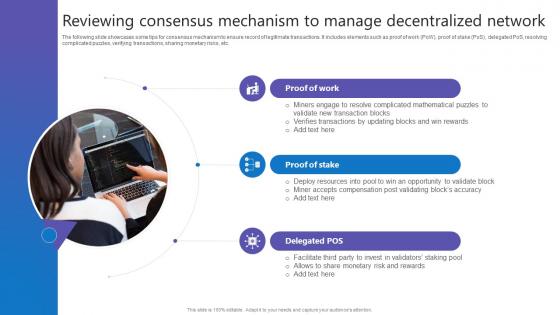
Reviewing Consensus Mechanism Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases some tips for consensus mechanism to ensure record of legitimate transactions. It includes elements such as proof of work PoW, proof of stake PoS, delegated PoS, resolving complicated puzzles, verifying transactions, sharing monetary risks, etc. Find a pre designed and impeccable Reviewing Consensus Mechanism Comprehensive Guide To Blockchain Digital Security Summary Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
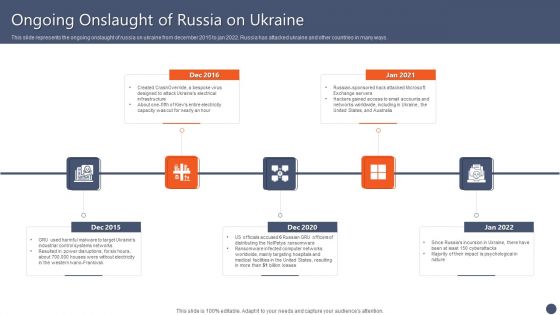
Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF
This slide represents the ongoing onslaught of russia on ukraine from december 2015 to jan 2022. Russia has attacked ukraine and other countries in many ways. If you are looking for a format to display your unique thoughts, then the professionally designed Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Strengths Weaknesses Opportunities And Threats Analysis Of Electronic Gadgets Business Microsoft PDF
This slide covers the SWOT analysis of the electronics computer systems business which will be needed to know how the competitors are growing and what are the opportunities that we could grab to make our business grow.Presenting Strengths Weaknesses Opportunities And Threats Analysis Of Electronic Gadgets Business Microsoft PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Standards, High Investment, Organization Culture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Decentralized Applications IT Why Choose Dapp Development Over Conventional App Development Brochure PDF
This slide highlights the reasons for which dApp development should be chosen over conventional app development methods, such as it provides a high degree of security, payment processing is comparatively faster, and so on. This is a Decentralized Applications IT Why Choose Dapp Development Over Conventional App Development Brochure PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Decentralization, Security, Payments. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
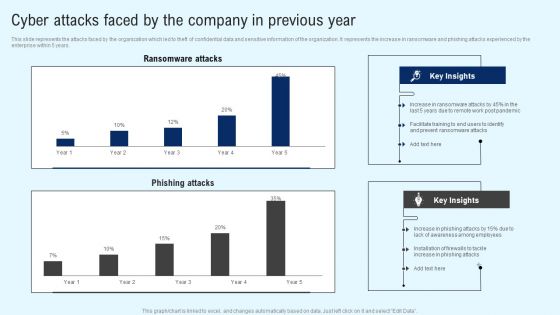
Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Digital Terrorism International Statistical Trends Brochure PDF
This slide shows International Statistical Trends of cyber terrorism at global level for building cyber security systems. It include statistics such as Global business attacks, International BYOD registrations etc. Showcasing this set of slides titled Digital Terrorism International Statistical Trends Brochure PDF. The topics addressed in these templates are International Businesses, Cyber Security Statistical Trends, Business Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
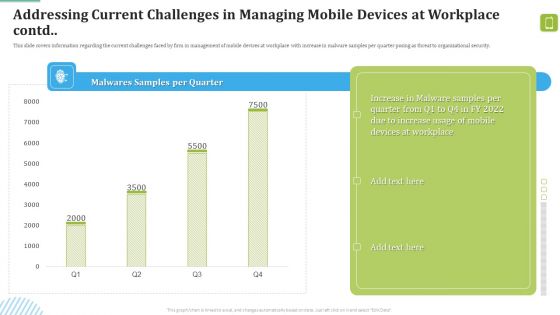
MDM Strategies At Office Addressing Current Challenges In Managing Mobile Devices At Workplace Contd Formats PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with increase in malware samples per quarter posing as threat to organizational security.Deliver and pitch your topic in the best possible manner with this MDM Strategies At Office Addressing Current Challenges In Managing Mobile Devices At Workplace Contd Formats PDF. Use them to share invaluable insights on Malware Samples, Increase Usage, Devices Workplace and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
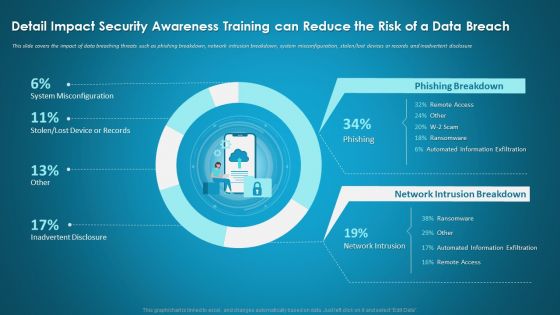
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
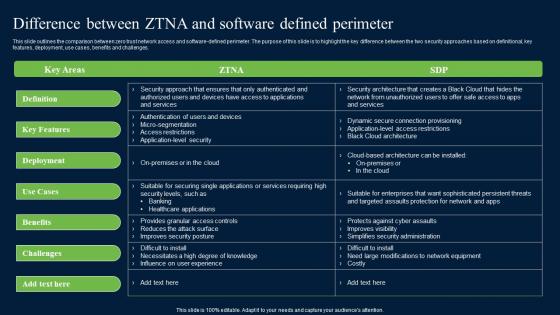
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Alert On Computer Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Computer PowerPoint Templates because they pinpoint the core values of your organisation. Use our Technology PowerPoint Templates because these ideas abound in the strong branches of your brain. Download our Signs PowerPoint Templates because health of the determines the quality of our lives. Present our Business PowerPoint Templates because your fledgling career is in the chrysallis stage. Nurture it and watch it grow into a beautiful butterfly. Download and present our Triangles PowerPoint Templates because it unravels each one for your audience while setting key timelines as you go along.Use these PowerPoint slides for presentations relating to Alert button on a black computer keyboard, computer, technology, signs, business, triangles. The prominent colors used in the PowerPoint template are Red, Black, Yellow. We assure you our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. Customers tell us our keyboard PowerPoint templates and PPT Slides are Classic. You can be sure our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Beautiful. People tell us our a PowerPoint templates and PPT Slides are Splendid. Presenters tell us our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Adorable. People tell us our technology PowerPoint templates and PPT Slides are Efficient.

Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF
This slide depicts different points leading to failures to set up an effective security system. It includes the cost borne by company due to failures in log management, communication over unauthorized ports, asset inventory, failures of anti-malware software, etc.Showcasing this set of slides titled Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF. The topics addressed in these templates are Management Failures, Irregular Penetration, Expense Borne. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
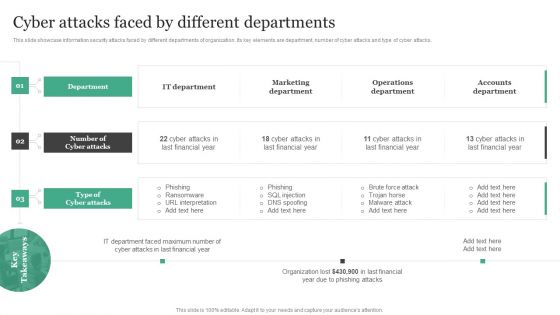
Cyber Attacks Faced By Different Departments Information Security Risk Administration Clipart PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks.Boost your pitch with our creative Cyber Attacks Faced By Different Departments Information Security Risk Administration Clipart PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
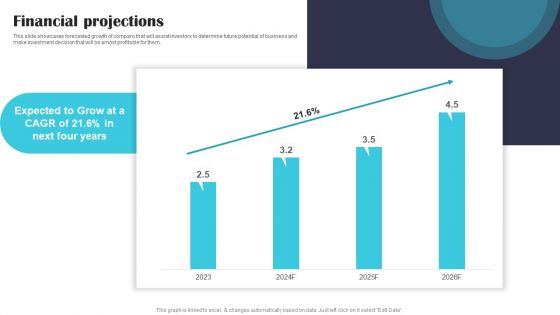
Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF
This slide showcases forecasted growth of company that will assist investors to determine future potential of business and make investment decision that will be amost profitable for them. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
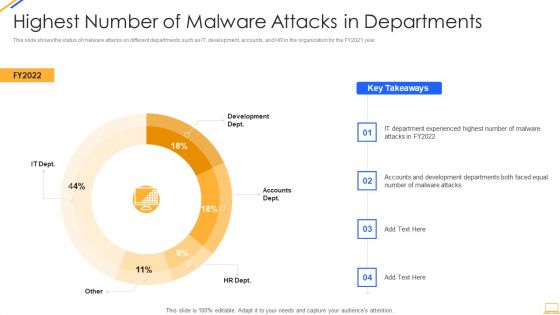
Desktop Security Management Highest Number Of Malware Attacks In Departments Inspiration PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Deliver an awe inspiring pitch with this creative desktop security management highest number of malware attacks in departments inspiration pdf bundle. Topics like highest number of malware attacks in departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
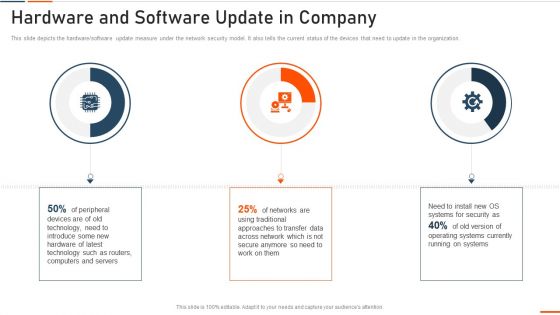
Information Technology Security Hardware And Software Update In Company Ppt Infographic Template Outfit PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022 year. Deliver an awe inspiring pitch with this creative information technology security hardware and software update in company ppt infographic template outfit pdf bundle. Topics like highest number of malware attacks in departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

API Administration Solution API Management Market Size By Region World Map Representation Ppt Outline Graphics Download PDF
Presenting api administration solution api management market size by region world map representation ppt outline graphics download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, growth, technical, development, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
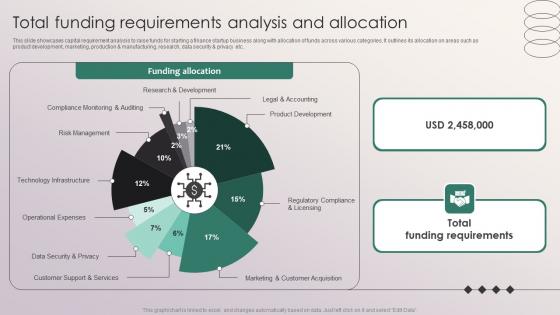
Total Funding Requirements Analysis And Allocation Penetrating Markets With Financial Strategy SS V
This slide showcases capital requirement analysis to raise funds for starting a finance startup business along with allocation of funds across various categories. It outlines its allocation on areas such as product development, marketing, production and manufacturing, research, data security and privacy etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Total Funding Requirements Analysis And Allocation Penetrating Markets With Financial Strategy SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Developing Business Analytics Framework Addressing Business Intelligence Rules PDF
This slide provides information regarding the various business intelligence solution by analyzing on various parameters such as hybrid cloud, data value maximization, secure infrastructure, etc. with cost. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Addressing Business Intelligence Rules PDF bundle. Topics like Effective Secure, Employees Customers, Connectivity Transformation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Multiplayer Gameplay System Venture Capitalist PPT What Video Game Experience Challenges Are Faced By Prospect Structure PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances.This is a multiplayer gameplay system venture capitalist ppt what video game experience challenges are faced by prospect structure pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security threats, everchanging government, systems information breach You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
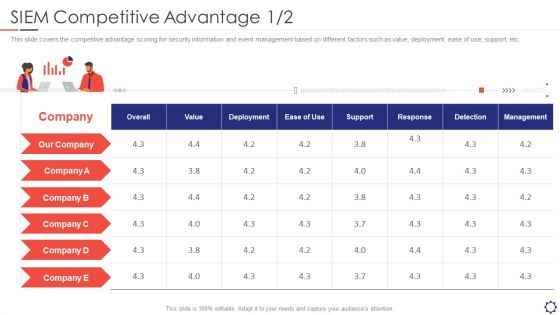
SIEM Competitive Advantage Detection Ppt Layouts Outline PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver and pitch your topic in the best possible manner with this siem competitive advantage detection ppt layouts outline pdf. Use them to share invaluable insights on value, deployment, response, detection, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
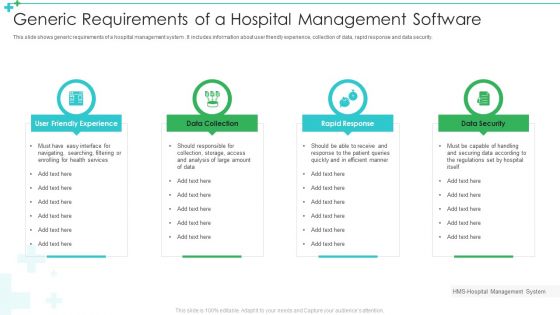
Generic Requirements Of A Hospital Management Software Ppt File Show PDF
This slide shows generic requirements of a hospital management system . It includes information about user friendly experience, collection of data, rapid response and data security. Presenting Generic Requirements Of A Hospital Management Software Ppt File Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including User Friendly Experience, Data Collection, Rapid Response, Data Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Find highly impressive Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.

Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre-designed and impeccable Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
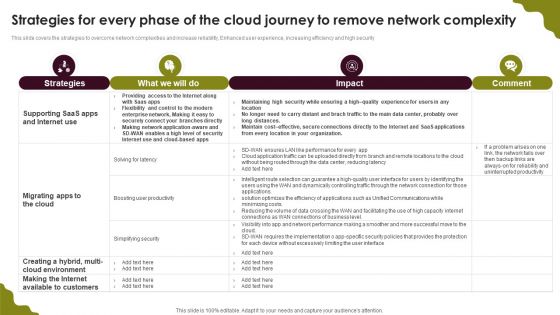
Cloud Computing Scalability Strategies For Every Phase Of The Cloud Journey Diagrams PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security. Do you know about Slidesgeeks Cloud Computing Scalability Strategies For Every Phase Of The Cloud Journey Diagrams PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF
This slide explains the working of a reverse proxy server in two ways proxying for load balancing and proxy as a stand-in for a server which is further divided into three parts such as secure client to proxy, secure proxy to content server and secure client to proxy and secure proxy to content server. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF.
Three Seps Of Enterprise Network Security With Icons Ppt PowerPoint Presentation Icon Slide Portrait PDF
Presenting three seps of enterprise network security with icons ppt powerpoint presentation icon slide portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, scope contain remediate, detect block defend. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Research Study Providing Statistics On Employee Engagement Project Success Brochure PDF
Mentioned slide outlines research study showing key statistics on employee engagement program success. Relation with colleagues and manager, meaningfulness of the job, work life balance are some of the parameters on which this study was conducted. Showcasing this set of slides titled research study providing statistics on employee engagement project success brochure pdf. The topics addressed in these templates are team, social, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Introduction To Modern Billing System Software Ppt PowerPoint Presentation File Ideas PDF
Following slide provide overview of modern billing software that helps to increase business operations efficiency. It include benefits such as high data security, flexibility, resource optimization etc.Retrieve professionally designed Introduction To Modern Billing System Software Ppt PowerPoint Presentation File Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Phishing Scams And Attacks Assessment And Cyber Security Training Inspiration PDF
Mentioned slide showcases phishing awareness training program used to prevent cyber attacks. It provides detailed information about deploying phishing program within the organization, analyzing and preparing reports, developing training and education etc. Persuade your audience using this phishing scams and attacks assessment and cyber security training inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including analyze, develop, measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF
This slide represents the technical analysis of ddos attacks against ukrainian websites by showing the internet traffic to the oschad bank website on 15 16 february 2022. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Steps For Devops Implementation IT Determine Devops Market Scenario Assessment Clipart PDF
This slide provides information regarding DevOps market scenario in terms of DevOps market growth and how the market has been accelerating in past few years. Deliver and pitch your topic in the best possible manner with this steps for devops implementation it determine devops market scenario assessment clipart pdf. Use them to share invaluable insights on market, service, security, growth and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home