Safety Improvement Plan
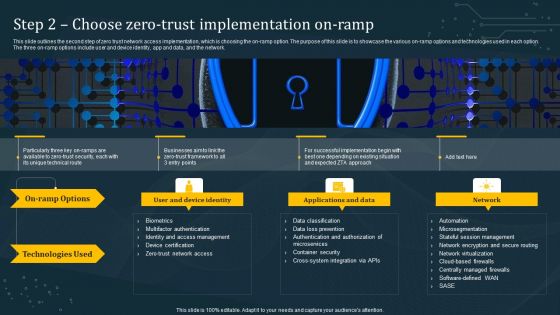
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Cyber Security Strategic Process Management Five Year Timeline Inspiration
Presenting our jaw dropping cyber security strategic process management five year timeline inspiration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. If you are looking for a format to display your unique thoughts, then the professionally designed Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Project Management Outline For Schedule Performance Index Using Optimized Tools For Continuous Monitoring Pictures PDF
This slide provides the glimpse about the tools which can be used by the company for regular monitoring and optimization within the company. Deliver and pitch your topic in the best possible manner with this project management outline for schedule performance index using optimized tools for continuous monitoring pictures pdf. Use them to share invaluable insights on monitoring, management, it security, cost, database and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides
This presentation deck enables you to communicate the message, idea, and proposal to your audience in a clear and effective manner. The slides of this PowerPoint Bundle are professional and visually appealing, engaging your audience and gaining their heartful interest in your content. In addition to its spectacular design, this PPT deck is easy to use and altered to fit the specific needs of the user. All fifty one slides in this set are compatible with multiple data handling and presentation platforms like Google Slides, MS Excel, Tableau, etc., so you can present your information hassle free. Begin your journey to tremendous success using our Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides in many settings, including meetings, pitches, and conference presentations In fact, customer testimonials.

Developing Client Engagement Techniques Common Challenges Faced By The Marketeers Clipart PDF
This slide focuses on common challenges faced by the marketeers which includes generation of traffic and leads, providing ROI for marketing activities, managing website, securing budget, delivering marketing strategy, etc. Deliver an awe inspiring pitch with this creative Developing Client Engagement Techniques Common Challenges Faced By The Marketeers Clipart PDF bundle. Topics like Securing Budget, Managing Website, Delivering Marketing Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Find highly impressive Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
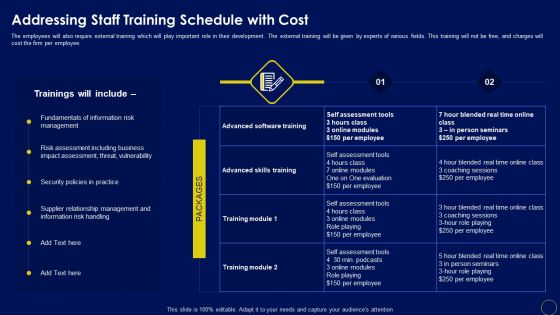
Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF
This slide showcases assessing impact on major operations and workflows. It provides information about customer understanding, knowledge, data management, financial risk management, customer relationship management, client onboarding, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF.
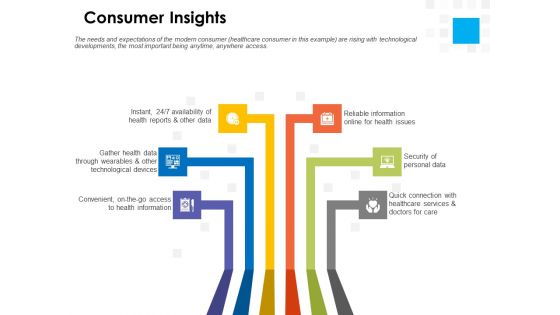
Digital Transformation Strategy Roadmap Consumer Insights Ppt PowerPoint Presentation Layouts Design Inspiration PDF
Presenting this set of slides with name digital transformation strategy roadmap consumer insights ppt powerpoint presentation layouts design inspiration pdf. This is a six stage process. The stages in this process are convenient access, health information, quick connection, healthcare services, security personal data, reliable information online health issues, health reports, gather health data through wearables, technological devices. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
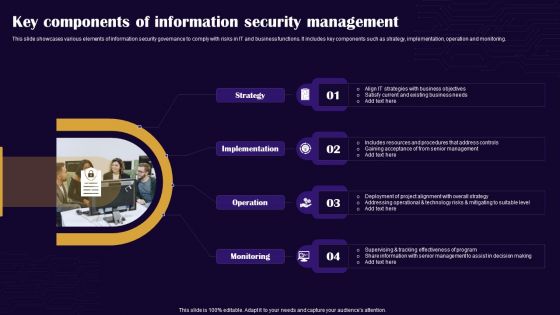
Key Components Of Information Security Management Graphics PDF
This slide showcases various elements of information security governance to comply with risks in IT and business functions. It includes key components such as strategy, implementation, operation and monitoring. Persuade your audience using this Key Components Of Information Security Management Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Implementation, Operation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Stages To Develop Security Analysis Approach Documentation Ppt PowerPoint Presentation File Graphics PDF
Showcasing this set of slides titled stages to develop security analysis approach documentation ppt powerpoint presentation file graphics pdf. The topics addressed in these templates are relevant frameworks, stages to develop security, analysis approach documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Activity Schedule For Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Activity Schedule For Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Activity Schedule For Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.

Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security. Deliver an awe inspiring pitch with this creative Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF bundle. Topics like Productivity, Simplifying Security, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
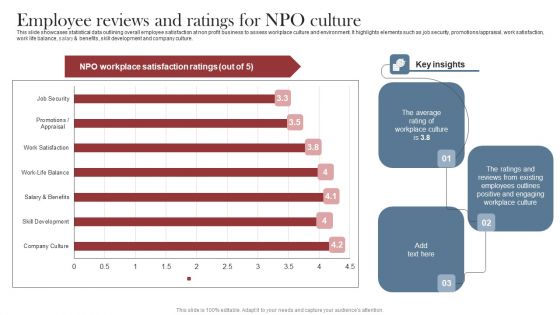
Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF
This slide showcases statistical data outlining overall employee satisfaction at non profit business to assess workplace culture and environment. It highlights elements such as job security, promotions appraisal, work satisfaction, work life balance, salary and benefits, skill development and company culture. This Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF
This slide talks about the various advantages of SOC-as-a-Service for organizations. The purpose of this slide is to highlight the main pros of security operations centers, including lowering the risk of data breaches, quick detection and remediation, ability to scale, resource optimization, enhanced maturity, and lowering costs. Find highly impressive Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policy, Organization Information, Human Resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
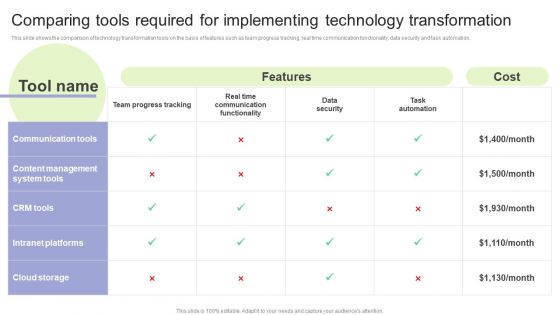
Implementing Change Management Strategy To Transform Business Processes Comparing Tools Required Elements PDF
This slide shows the comparison of technology transformation tools on the basis of features such as team progress tracking, real time communication functionality, data security and task automation. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Change Management Strategy To Transform Business Processes Comparing Tools Required Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Online PR Techniques To Boost Brands Online Visibility Budget Securing Tips For Public Relations Introduction PDF
This slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Make sure to capture your audiences attention in your business displays with our gratis customizable Online PR Techniques To Boost Brands Online Visibility Budget Securing Tips For Public Relations Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Key Approaches For Successful Implementation Of Smart Production Ppt Icon Portrait PDF
This slide signifies the key strategies for successfully executing smart production. It covers information about approaches like cybersecurity, augmented reality, big data, stimulation, system integration and cloud computing. Presenting Key Approaches For Successful Implementation Of Smart Production Ppt Icon Portrait PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Cyber Security, Augmented Reality, Big Data, Autonomous Robots. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
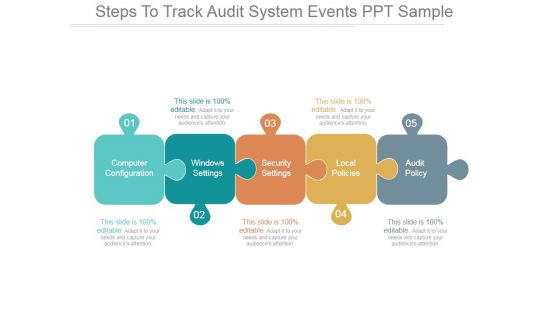
Steps To Track Audit System Events Ppt PowerPoint Presentation Summary
This is a steps to track audit system events ppt powerpoint presentation summary. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.

Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Multi Stages System For Contractor Security Management With Key Tasks Ppt PowerPoint Presentation Styles Tips PDF
Presenting this set of slides with name multi stages system for contractor security management with key tasks ppt powerpoint presentation styles tips pdf. This is a five stage process. The stages in this process are contract definition and award, pre commencement, contract execution and control, hand over and acceptance, close out and review. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
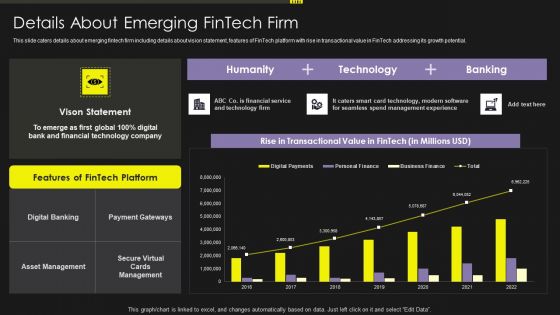
Investment Service Provider Capital Raising Elevator Details About Emerging Fintech Firm Topics PDF
This slide caters details about emerging fintech firm including details about vision statement, features of FinTech platform with rise in transactional value in FinTech addressing its growth potential. Deliver and pitch your topic in the best possible manner with this investment service provider capital raising elevator details about emerging fintech firm topics pdf. Use them to share invaluable insights on payment gateways, digital banking, asset management, secure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
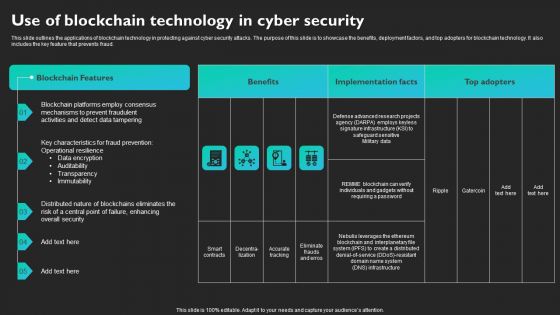
Use Of Blockchain Technology In Cyber Security Slides PDF
This slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Find a pre-designed and impeccable Use Of Blockchain Technology In Cyber Security Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Techniques To Monitor Transactions Key Members Of Financial Security Department Themes PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Techniques To Monitor Transactions Key Members Of Financial Security Department Themes PDF from Slidegeeks and deliver a wonderful presentation.

International Organization Standardization 270001 Dashboard For Information Security Risk Management Pictures PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, parcent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative international organization standardization 270001 dashboard for information security risk management pictures pdf bundle. Topics like dashboard for information security risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Revenue And Net Profit Inspiration PDF
This slide highlights the revenue and net profit of security guard company through bar graph and tabular format. It covers three years data of revenue, and net profit. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Revenue And Net Profit Inspiration PDF. Use them to share invaluable insights on Revenue, Profit, Growth Rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Application Development Startup Problems Faced By Companies Pictures PDF
This slide provides the glimpse about the problem faced by the companies such as network security, professional and qualified experience, backup issues, hardware and software concerns, etc. Presenting application development startup problems faced by companies pictures pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like poor network security, backup issues, lack professional and qualified experience, hardware and software concerns. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Objectives Of IBM Watson IoT Platform Exploring Google Cloud IoT Platform
This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Objectives Of IBM Watson IoT Platform Exploring Google Cloud IoT Platform for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
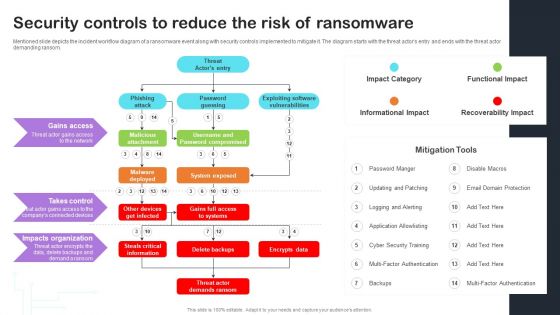
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

Proposal For Corporate Meeting Scope One Pager Sample Example Document
The slide presents the scope of services for the proposal project in terms of catering, internet and audio visual equipment , logistics, security and decor. Presenting you an exemplary Proposal For Corporate Meeting Scope One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Corporate Meeting Scope One Pager Sample Example Document brilliant piece now.

Scope For Scientific Conference One Pager Sample Example Document
The slide presents the scope of services for the proposal project in terms of catering, internet and audio-visual equipment, logistics, security and decor. Presenting you an exemplary Scope For Scientific Conference One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Scope For Scientific Conference One Pager Sample Example Document brilliant piece now.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Manpower Corporate Security Business Profile Executive Leadership And Management Team Template PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Manpower Corporate Security Business Profile Executive Leadership And Management Team Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Business, Security Operations, Resource Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
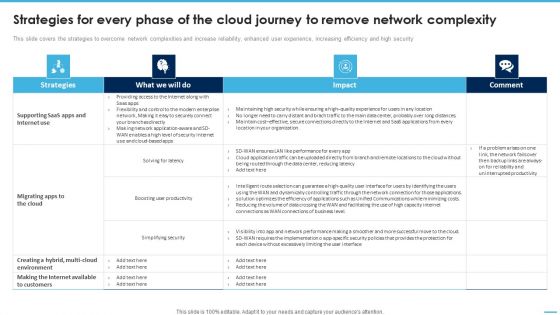
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF
This slide covers the strategies to overcome network complexities and increase reliability, enhanced user experience, increasing efficiency and high security.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF.
Security Patch Management Best Practices Ppt PowerPoint Presentation Pictures Infographics
This is a security patch management best practices ppt powerpoint presentation pictures infographics. This is a three stage process. The stages in this process are patch management process, patch management procedure, patch management approach.
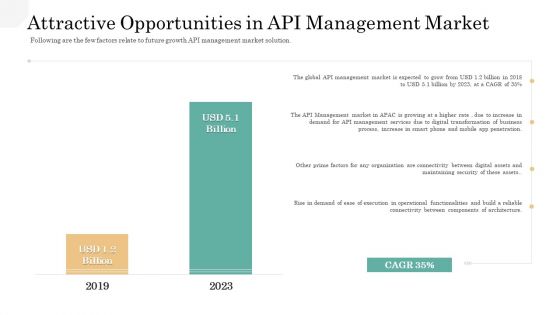
API Management Market Attractive Opportunities In API Management Market Portrait PDF
Following are the few factors relate to future growth API management market solution. Deliver an awe inspiring pitch with this creative api management market attractive opportunities in api management market portrait pdf bundle. Topics like api management market, business process, maintaining security of these assets, operational functionalities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Organization Cyber Security Dashboard Ppt Icon Sample PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard ppt icon sample pdf. Use them to share invaluable insights on makes and models, application health, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organization Cyber Security Dashboard Ppt Show Outfit PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe inspiring pitch with this creative organization cyber security dashboard ppt show outfit pdf bundle. Topics like operating systems, license consumption, makes and models, other employees can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data And Customer Analysis Company Outline ESG Highlights Structure PDF

Computer Security Incident Handling Determining Roles And Responsibilities For Risk Handling Mockup PDF
Presenting this set of slides with name computer security incident handling determining roles and responsibilities for risk handling mockup pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Challenges Faced By The Firm While Managing Policies In Multi Cloud Environment Template PDF
This slide covers the challenges faced by the firm in managing multi cloud policies such as access, security, quota, budget, regulations, utilizations and many more.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Challenges Faced By The Firm While Managing Policies In Multi Cloud Environment Template PDF from Slidegeeks and deliver a wonderful presentation.
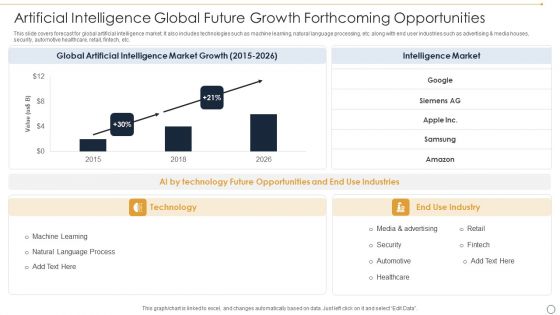
Artificial Intelligence Global Future Growth Forthcoming Opportunities Ppt Show Clipart PDF
This slide covers forecast for global artificial intelligence market. It also includes technologies such as machine learning, natural language processing, etc. along with end user industries such as advertising and media houses, security, automotive healthcare, retail, fintech, etc. Showcasing this set of slides titled Artificial Intelligence Global Future Growth Forthcoming Opportunities Ppt Show Clipart PDF. The topics addressed in these templates are Global Artificial, Intelligence Market, Growth. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Analysis And Valuation Of Equity Securities Ppt PowerPoint Presentation Icon Slide Portrait
This is a analysis and valuation of equity securities ppt powerpoint presentation icon slide portrait. This is a one stage process. The stages in this process are business, management, marketing, agenda.
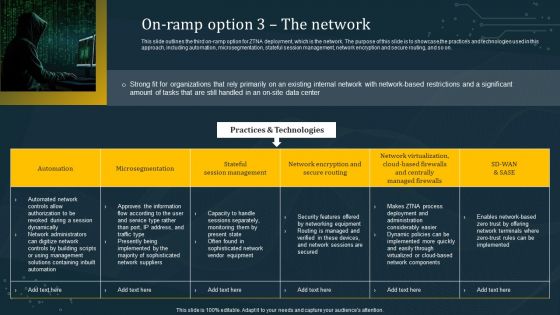
On Ramp Option 3 The Network Structure PDF
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you know about Slidesgeeks On Ramp Option 3 The Network Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Project Context For Partnership Proposal Ppt PowerPoint Presentation Professional Slide
Presenting this set of slides with name project context for partnership proposal ppt powerpoint presentation professional slide. This is a five stage process. The stages in this process are specialized, development, services, business, it infrastructure, security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
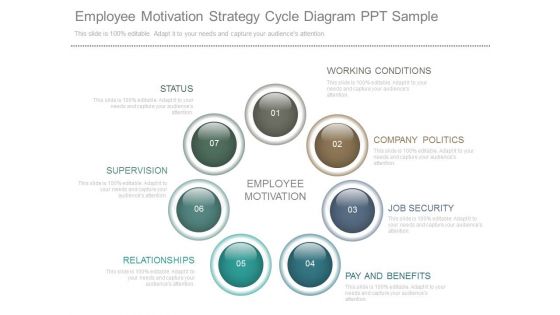
Employee Motivation Strategy Cycle Diagram Ppt Sample
This is a employee motivation strategy cycle diagram ppt sample. This is a four stage process. The stages in this process are working conditions, company politics, job security, pay and benefits, relationships, supervision, status.

Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of Multiple Mockup PDF
Following slide shows comparative analysis of multiple types of mobile wallet which can be leverages by business to go contactless. It includes key components such as features, transaction level, payment fees, transaction time, security and type of wallet. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of Multiple Mockup PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of Multiple Mockup PDF today and make your presentation stand out from the rest

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Summary Of Audit And Review Team Findings By Severity Download PDF
This slide summarizes inspection findings by severity of an organization by audit team. It includes findings like attack surface, account security, hardened system, patching etc.Showcasing this set of slides titled Summary Of Audit And Review Team Findings By Severity Download PDF. The topics addressed in these templates are System Hardening, Data Protection, Account Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
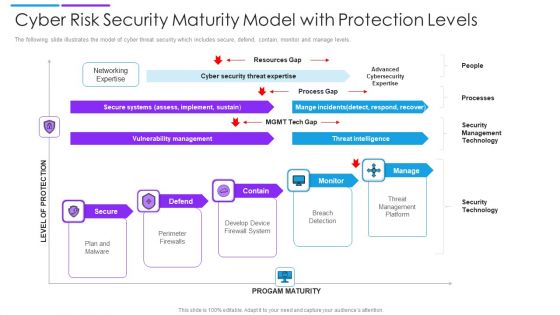
Cyber Risk Security Maturity Model With Protection Levels Mockup PDF
The following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Persuade your audience using this cyber risk security maturity model with protection levels mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including secure systems, vulnerability management, threat intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
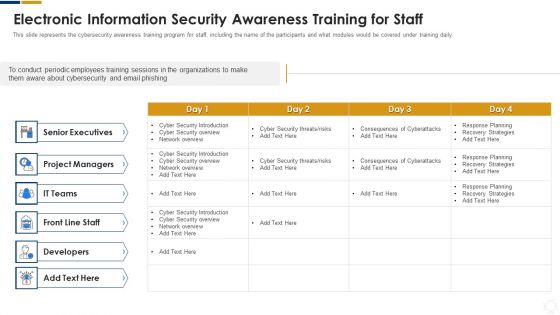
Cybersecurity Electronic Information Security Awareness Training For Staff Ppt Layouts Deck PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative cybersecurity electronic information security awareness training for staff ppt layouts deck pdf bundle. Topics like project managers, developers, senior executives, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Intelligence With Data Governance And Security Ppt PowerPoint Presentation Infographics Example PDF
Pitch your topic with ease and precision using this business intelligence with data governance and security ppt powerpoint presentation infographics example pdf. This layout presents information on data governance, data discovery, data quality management, connected clouds, security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Challenges And Opportunities For Online Money Transfer Service Provider Ppt Professional Files PDF
The following slide highlights some major challenges and opportunities fund transfer service providers to grab the advantage. It includes elements such as low profit margin, reliability, security etc. Showcasing this set of slides titled Challenges And Opportunities For Online Money Transfer Service Provider Ppt Professional Files PDF. The topics addressed in these templates are Challenges, Opportunities, Traditional Providers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with increase in malware samples per quarter posing as threat to organizational security. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF.

Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V
This slide provides an overview of the blockchain technology used for remote monotiling. It also includes the benefits that are it allows device communication, enhance security and provides authorization access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V today and make your presentation stand out from the rest

 Home
Home