Safety Improvement Plan

Deployment Of Cloud Project Management Model Digital Transformation In Project Management
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deployment Of Cloud Project Management Model Digital Transformation In Project Management. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deployment Of Cloud Project Management Model Digital Transformation In Project Management today and make your presentation stand out from the rest

Regulations Of Security Tokenization Strategies For Data Security PPT Template
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Comprehensive Look At Blockchain Challenges And Solutions Of Introducing BCT SS V
This slide mentions various challenges that can be faced by government in introducing blockchain technology and its corresponding solutions. Areas evaluated include regulatory challenges, security concerns, lack of standardization, integration with legacy systems and limited expertise. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comprehensive Look At Blockchain Challenges And Solutions Of Introducing BCT SS V can be your best option for delivering a presentation. Represent everything in detail using Comprehensive Look At Blockchain Challenges And Solutions Of Introducing BCT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

IT Business Alignment Framework Business And IT Alignment Governance And Transformation Themes PDF
This slide represents the business and IT alignment, governance, and transformation, including the strategic alignment model. The components of the SAM model include business strategy, IT strategy, organizational infrastructure and processes, information security infrastructure and processes, and business and IT domain.This IT Business Alignment Framework Business And IT Alignment Governance And Transformation Themes PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The IT Business Alignment Framework Business And IT Alignment Governance And Transformation Themes PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
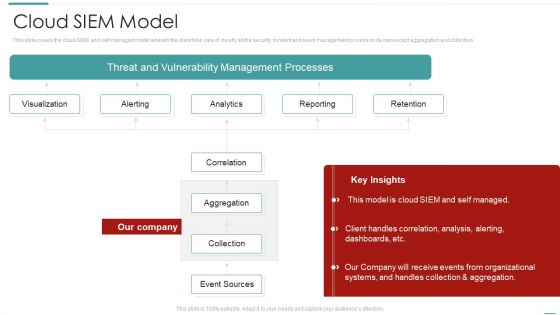
Risk Recognition Automation Cloud Siem Model Ppt Layouts Templates PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this risk recognition automation cloud siem model ppt layouts templates pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Recognition Automation Hybrid Managed Siem Model Ppt Show Themes PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this risk recognition automation hybrid managed siem model ppt show themes pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
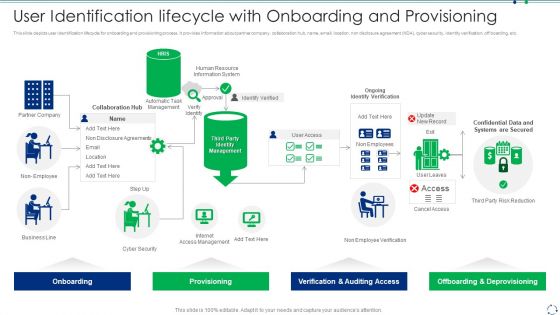
User Identification Lifecycle With Onboarding And Provisioning Introduction PDF
This slide depicts user identification lifecycle for onboarding and provisioning process. It provides information about partner company, collaboration hub, name, email, location, non disclosure agreement NDA cyber security, identity verification, off boarding, etc.Showcasing this set of slides titled user identification lifecycle with onboarding and provisioning introduction pdf The topics addressed in these templates are verification and auditing access, offboarding and deprovisioning, provisioning All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
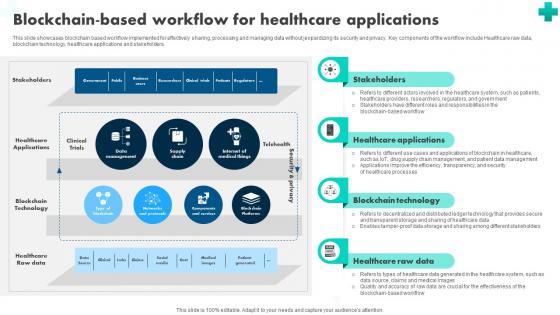
A56 How Blockchain Is Reshaping Blockchain Based Workflow For Healthcare BCT SS V
This slide showcases blockchain based workflow implemented for effectively sharing, processing and managing data without jeopardizing its security and privacy. Key components of the workflow include Healthcare raw data, blockchain technology, healthcare applications and stakeholders. Want to ace your presentation in front of a live audience Our A56 How Blockchain Is Reshaping Blockchain Based Workflow For Healthcare BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
Icons Slide For Secure Computing Framework Designs Pdf
Download our innovative and attention grabbing Icons Slide For Secure Computing Framework Designs Pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
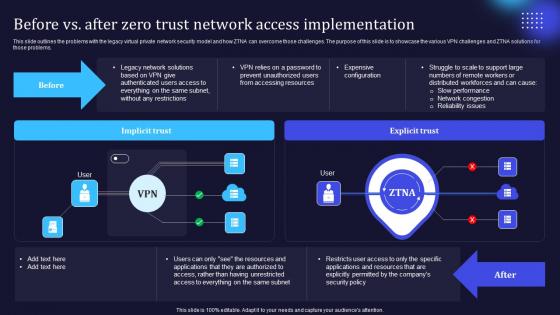
Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
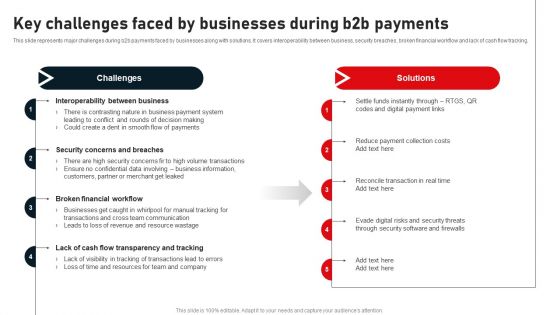
Key Challenges Faced By Businesses During B2B Payments Structure PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. Slidegeeks is here to make your presentations a breeze with Key Challenges Faced By Businesses During B2B Payments Structure PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
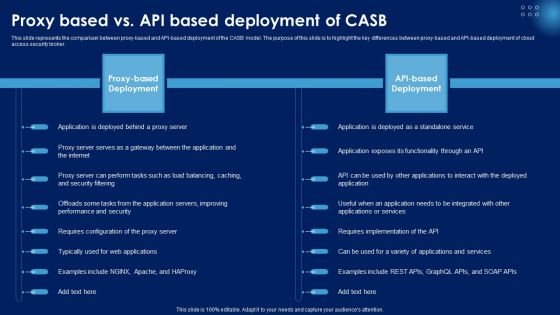
Proxy Based Vs API Based Deployment Of CASB Ppt PowerPoint Presentation File Pictures PDF
This slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker. Find highly impressive Proxy Based Vs API Based Deployment Of CASB Ppt PowerPoint Presentation File Pictures PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Proxy Based Vs API Based Deployment Of CASB Ppt PowerPoint Presentation File Pictures PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
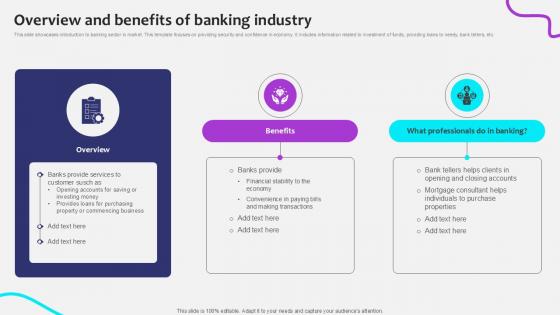
Overview And Benefits Of Banking Initiating Globalization Of Banking Ppt Powerpoint
This slide showcases introduction to banking sector in market. This template focuses on providing security and confidence in economy. It includes information related to investment of funds, providing loans to needy, bank tellers, etc. Explore a selection of the finest Overview And Benefits Of Banking Initiating Globalization Of Banking Ppt Powerpoint here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Overview And Benefits Of Banking Initiating Globalization Of Banking Ppt Powerpoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Tokenization Working Process For Data Security Securing Your Data Ppt Presentation
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Find highly impressive Tokenization Working Process For Data Security Securing Your Data Ppt Presentation on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Tokenization Working Process For Data Security Securing Your Data Ppt Presentation for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Business And IT Alignment Governance And Transformation Graphics PDF
This slide represents the business and IT alignment, governance, and transformation, including the strategic alignment model. The components of the SAM model include business strategy, IT strategy, organizational infrastructure and processes, information security infrastructure and processes, and business and IT domain. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Business And IT Alignment Governance And Transformation Graphics PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Business And IT Alignment Governance And Transformation Graphics PDF.
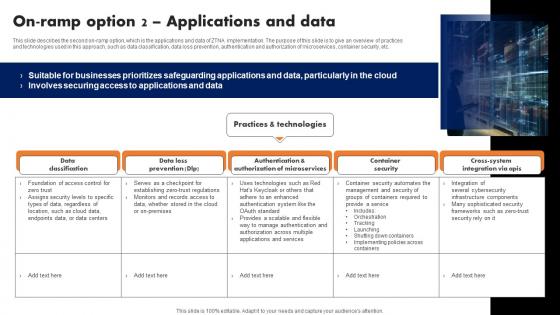
On Ramp Option 2 Applications And Data Software Defined Perimeter SDP
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
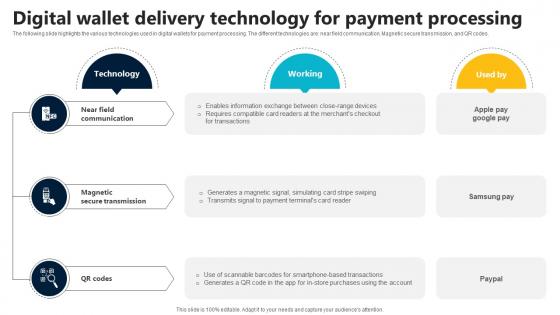
Digital Wallet Delivery Technology For Payment In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the various technologies used in digital wallets for payment processing. The different technologies are near field communication. Magnetic secure transmission, and QR codes. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Digital Wallet Delivery Technology For Payment In Depth Guide To Digital Wallets Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Digital Wallet Delivery Technology For Payment In Depth Guide To Digital Wallets Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
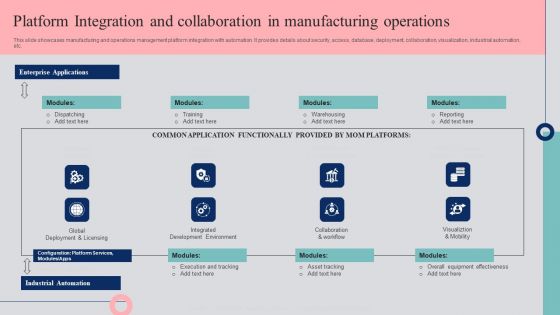
Platform Integration And Collaboration In Manufacturing Operations Template PDF
This slide showcases manufacturing and operations management platform integration with automation. It provides details about security, access, database, deployment, collaboration, visualization, industrial automation, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Platform Integration And Collaboration In Manufacturing Operations Template PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Platform Integration And Collaboration In Manufacturing Operations Template PDF today and make your presentation stand out from the rest
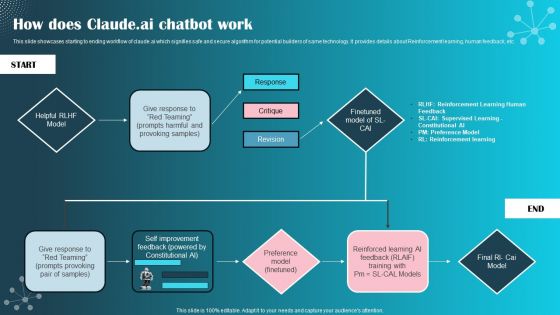
How Does Claude Ai Chatbot Work Ppt PowerPoint Presentation File Model PDF
This slide showcases starting to ending workflow of claude.ai which signifies safe and secure algorithm for potential builders of same technology. It provides details about Reinforcement learning, human feedback, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than How Does Claude Ai Chatbot Work Ppt PowerPoint Presentation File Model PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab How Does Claude Ai Chatbot Work Ppt PowerPoint Presentation File Model PDF today and make your presentation stand out from the rest.
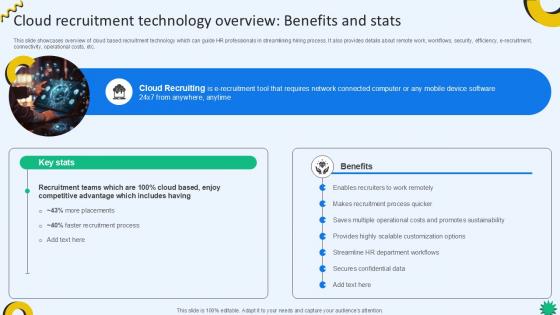
Cloud Recruitment Technology Overview Cloud Recruiting Technologies PPT Sample
This slide showcases overview of cloud based recruitment technology which can guide HR professionals in streamlining hiring process. It also provides details about remote work, workflows, security, efficiency, e-recruitment, connectivity, operational costs, etc. Get a simple yet stunning designed Cloud Recruitment Technology Overview Cloud Recruiting Technologies PPT Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Cloud Recruitment Technology Overview Cloud Recruiting Technologies PPT Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
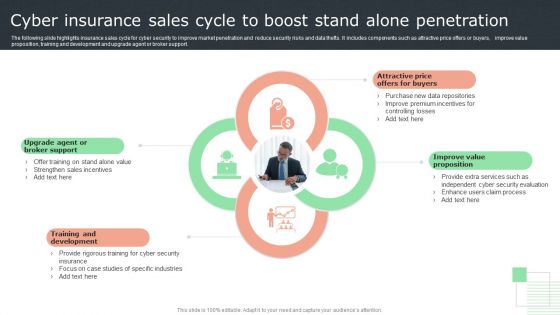
Cyber Insurance Sales Cycle To Boost Stand Alone Penetration Topics PDF
The following slide highlights insurance sales cycle for cyber security to improve market penetration and reduce security risks and data thefts. It includes components such as attractive price offers or buyers, improve value proposition, training and development and upgrade agent or broker support. Presenting Cyber Insurance Sales Cycle To Boost Stand Alone Penetration Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Broker Support, Development, Proposition. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Home Network Diagram In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Home Network Diagram In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Home Network Diagram that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Teamwork Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Teamwork Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Teamwork Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Flaw Cyber Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Tab Manager Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Tab Manager Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Tab Manager Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Agenda For Zero Trust Network Security Pictures Pdf
Find a pre-designed and impeccable Agenda For Zero Trust Network Security Pictures Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Tokenization Working Process For Data Security PPT Powerpoint
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Boost your pitch with our creative Tokenization Working Process For Data Security PPT Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Icons Slide For Zero Trust Security Template Pdf
Introducing our well designed Icons Slide For Zero Trust Security Template Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf
Introducing our well designed Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Securing Your Data With Tokenization Ppt Slide
Download our innovative and attention grabbing Icons Slide For Securing Your Data With Tokenization Ppt Slide template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
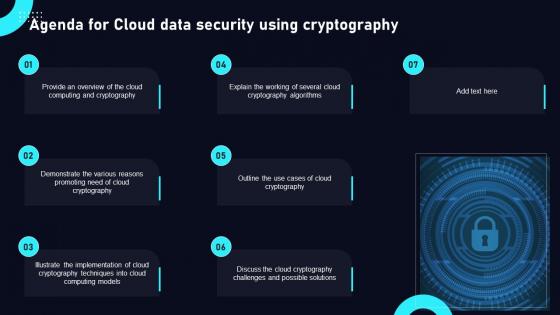
Agenda For Cloud Data Security Using Cryptography Structure Pdf
Find highly impressive Agenda For Cloud Data Security Using Cryptography Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Agenda For Cloud Data Security Using Cryptography Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Continuous Integration And Continuous Delivery Process Security Role Of Devsecops Ppt Slide
This slide discusses the continuous integration and continuous delivery process security for DevSecOps. The purpose of this slide is to highlight the process, including integrating container security scanners, automating security testing in CI, incorporating security tests in acceptance testing, and so on. Present like a pro with Continuous Integration And Continuous Delivery Process Security Role Of Devsecops Ppt Slide Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Architecture Of Security Harnessing The World Of Ethical Ppt Template
This slide highlights the architecture of security testing components such as user interface, controller, tester, controller, test report, test case, etc. There are so many reasons you need a Architecture Of Security Harnessing The World Of Ethical Ppt Template The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Icons Slide For Exploring Investment Opportunities With Security Token Offerings Infographics Pdf
Introducing our well designed Icons Slide For Exploring Investment Opportunities With Security Token Offerings Infographics Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf
Introducing our well designed Icons Slide For Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Global Security Industry Report PPT Slide IR SS V
Introducing our well designed Icons Slide For Global Security Industry Report PPT Slide IR SS V set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf
Slidegeeks has constructed Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
Best Security Management In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Best Security Management In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Best Security Management that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

CASB 2 0 IT Cloud Access Security Broker Pillar Visibility
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Slidegeeks has constructed CASB 2 0 IT Cloud Access Security Broker Pillar Visibility after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Zero Trust Model Traditional Perimeter Based Network Security Overview
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Traditional Perimeter Based Network Security Overview is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Traditional Perimeter Based Network Security Overview and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Agenda For Building Trust With IoT Security And Privacy Measures IoT SS V
Find a pre-designed and impeccable Agenda For Building Trust With IoT Security And Privacy Measures IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation
This slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. This Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Our Csr Values And Ethics Ppt PowerPoint Presentation Ideas
This is a our csr values and ethics ppt powerpoint presentation ideas. This is a nine stage process. The stages in this process are passion, agility, innovation, power, promotion, commitment, diversity, tradition, security.
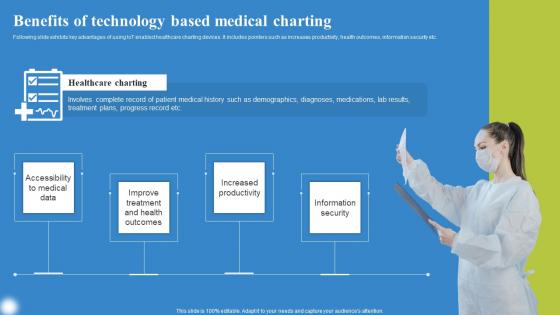
Benefits Of Technology Based Deploying IoT Solutions For Enhanced Healthcare Infographics Pdf
Following slide exhibits key advantages of using IoT enabled healthcare charting devices. It includes pointers such as increases productivity, health outcomes, information security etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Benefits Of Technology Based Deploying IoT Solutions For Enhanced Healthcare Infographics Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Benefits Of Technology Based Deploying IoT Solutions For Enhanced Healthcare Infographics Pdf
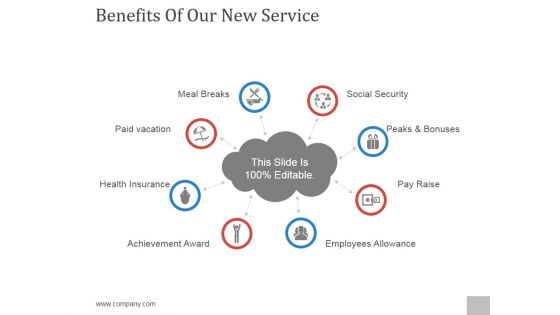
Benefits Of Our New Service Ppt PowerPoint Presentation Slide Download
This is a benefits of our new service ppt powerpoint presentation slide download. This is a eight stage process. The stages in this process are social security, peaks and bonuses, pay raise, employees allowance, achievement award, health insurance, paid vacation, meal breaks.
Predictive Modeling Process Flow In Logistics Icons PDF
This slide showcases Predictive modeling which enables production and distribution optimization through better throughput, quality and safety. It provides details about historical data, predictive analytics model, forecast visualization, integrated custom analytics, etc. Get a simple yet stunning designed Predictive Modeling Process Flow In Logistics Icons PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Predictive Modeling Process Flow In Logistics Icons PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Our Services Ppt PowerPoint Presentation Professional Ideas
This is a our services ppt powerpoint presentation professional ideas. This is a four stage process. The stages in this process are marketing and analytics, digital advertising, security maintenance, digital care package.

Our Services Ppt PowerPoint Presentation Inspiration Brochure
This is a our services ppt powerpoint presentation inspiration brochure. This is a four stage process. The stages in this process are digital advertising, marketing and analytics, digital care package, security and maintenance.

Table Of Contents Security Service Provider Business Model BMC SS V
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Security Service Provider Business Model BMC SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Security Service Provider Business Model BMC SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Our Services Template 1 Ppt PowerPoint Presentation Model Picture
This is a our services template 1 ppt powerpoint presentation model picture. This is a four stage process. The stages in this process are digital advertising, marketing and analytics, digital care package, security and maintenance.
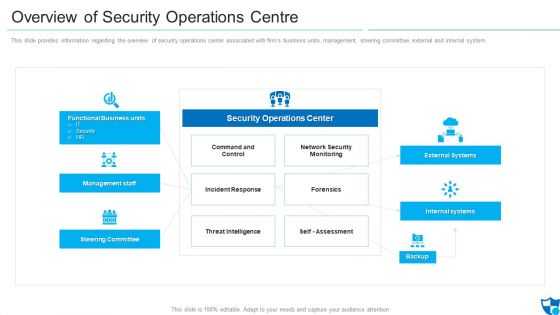
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
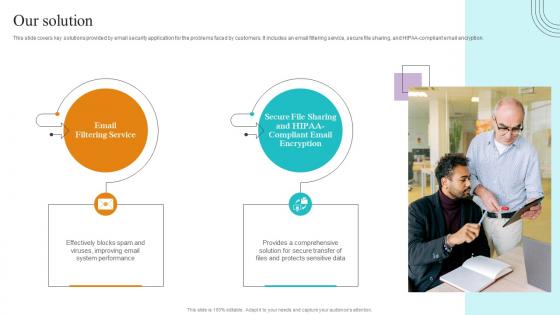
Our Solution Paubox Capital Funding Pitch Deck Summary Pdf
This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA compliant email encryption. Welcome to our selection of the Our Solution Paubox Capital Funding Pitch Deck Summary Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

Pricing Strategy Security Service Provider Business Model BMC SS V
slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Pricing Strategy Security Service Provider Business Model BMC SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Pricing Strategy Security Service Provider Business Model BMC SS V today and make your presentation stand out from the rest

 Home
Home