Safety Improvement Plan
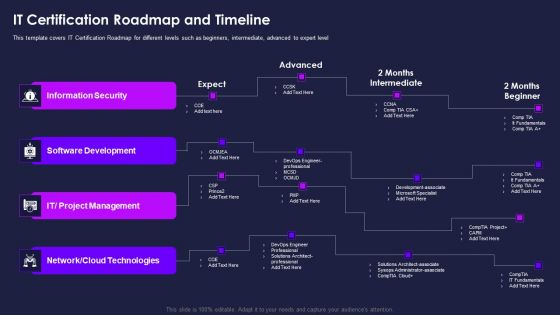
Certification Information Technology Professionals IT Certification Roadmap Elements PDF
This template covers IT Certification Roadmap for different levels such as beginners, intermediate, advanced to expert level Deliver an awe inspiring pitch with this creative certification information technology professionals it certification roadmap elements pdf bundle. Topics like information security, software development, project management, network cloud technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Deployment Of Omnichannel Banking Solutions Self Service Bill Payment Kiosks Process Clipart PDF
This slide covers process to be followed while paying bills using a secure self service kiosks. The purpose of this template is to provide customer a guide to follow for better experience. It includes steps starting from selecting payment option on kiosks, entering amount to be paid, scanning the QR code generated, etc. Want to ace your presentation in front of a live audience Our Deployment Of Omnichannel Banking Solutions Self Service Bill Payment Kiosks Process Clipart PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
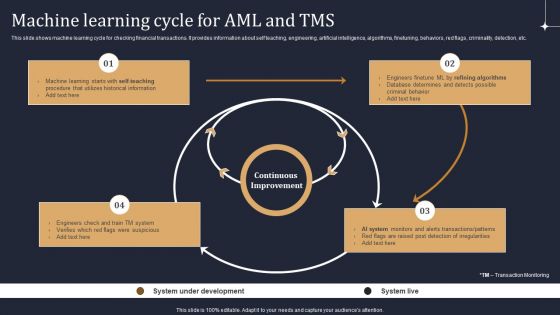
KYC Transaction Monitoring System Business Security Machine Learning Cycle For Aml And Tms Demonstration PDF
This slide shows machine learning cycle for checking financial transactions. It provides information about self teaching, engineering, artificial intelligence, algorithms, finetuning, behaviors, red flags, criminality, detection, etc. There are so many reasons you need a KYC Transaction Monitoring System Business Security Machine Learning Cycle For Aml And Tms Demonstration PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

KYC Transaction Monitoring System Business Security Effective Ways To Report Fraudulent Transactions Summary PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download KYC Transaction Monitoring System Business Security Effective Ways To Report Fraudulent Transactions Summary PDF from Slidegeeks and deliver a wonderful presentation.
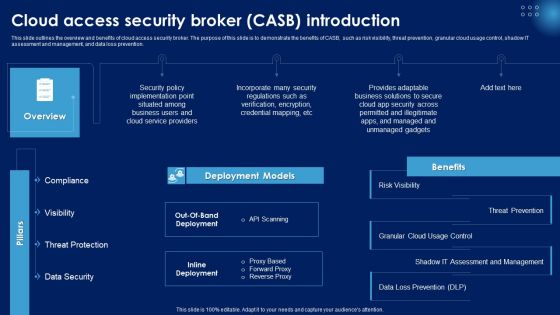
Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF.

Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf
This slide highlights the various limitations of traditional firewall systems. The purpose of this slide is to outline the different issues of traditional firewalls. These include unable to prevent transfer of infected files, do not protect already compromised systems, etc. Create an editable Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
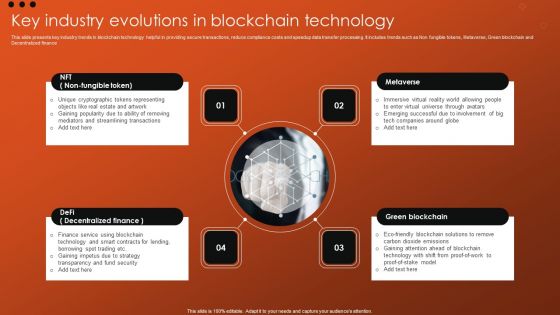
Key Industry Evolutions In Blockchain Technology Infographics PDF
This slide presents key industry trends in blockchain technology helpful in providing secure transactions, reduce compliance costs and speedup data transfer processing. It includes trends such as Non fungible tokens, Metaverse, Green blockchain and Decentralized finance. Pitch your topic with ease and precision using this Key Industry Evolutions In Blockchain Technology Infographics PDF. This layout presents information on Involvement, Security, Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Horizontal Scaling Technique For Information Team Structure For Data Management System Expansion Icons PDF
This slide represents the team structure for the data repository expansion project. It provides details regarding core and support team members in terms of job role and employee name.Deliver and pitch your topic in the best possible manner with this Horizontal Scaling Technique For Information Team Structure For Data Management System Expansion Icons PDF Use them to share invaluable insights on Documentation Information, Security Engineer, Information Security Engineer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Camera System Business In Powerpoint And Google Slides Cpb
Introducing our well-designed Security Camera System Business In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Camera System Business. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Optimization Of IoT Remote Monitoring Smart Home Alarm System To Prevent Unauthorized Entry IoT SS V
This slide provides an overview of the smart alarm system installed in homes to increase security. It further includes challenges faced and advantages that are easy installation, cost-effective, send real-time alerts, etc. Retrieve professionally designed Optimization Of IoT Remote Monitoring Smart Home Alarm System To Prevent Unauthorized Entry IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
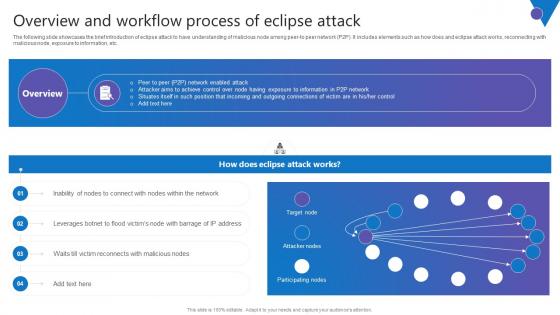
Overview And Workflow Process Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Overview And Workflow Process Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks and deliver a wonderful presentation.
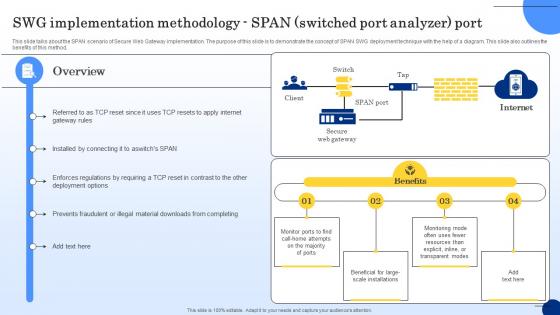
SWG Implementation Methodology Span Web Threat Protection System
This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than SWG Implementation Methodology Span Web Threat Protection System. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab SWG Implementation Methodology Span Web Threat Protection System today and make your presentation stand out from the rest

IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT Ss V
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
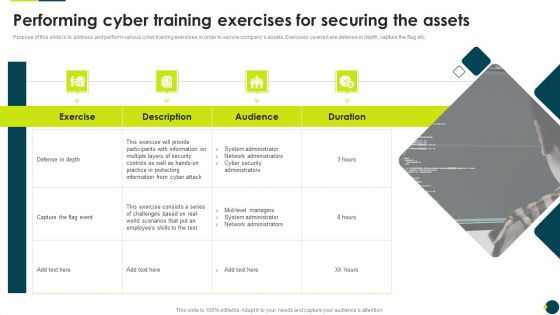
IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
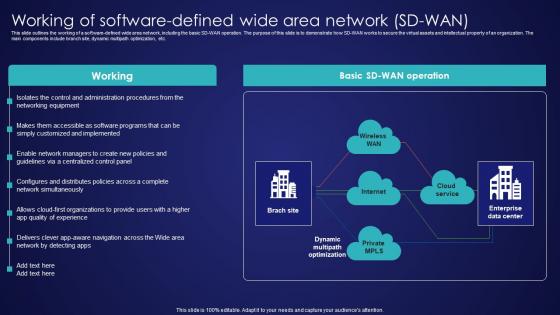
Working Of Software Defined Wide Area Network SD Wan Wide Area Network Services Diagrams Pdf
This slide outlines the working of a software-defined wide area network, including the basic SD-WAN operation. The purpose of this slide is to demonstrate how SD-WAN works to secure the virtual assets and intellectual property of an organization. The main components include branch site, dynamic multipath optimization, etc. Present like a pro with Working Of Software Defined Wide Area Network SD Wan Wide Area Network Services Diagrams Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Our Services Ppt PowerPoint Presentation Gallery Model
This is a our services ppt powerpoint presentation gallery model. This is a four stage process. The stages in this process are marketing and analytics, digital advertising, security maintenance, digital care package.
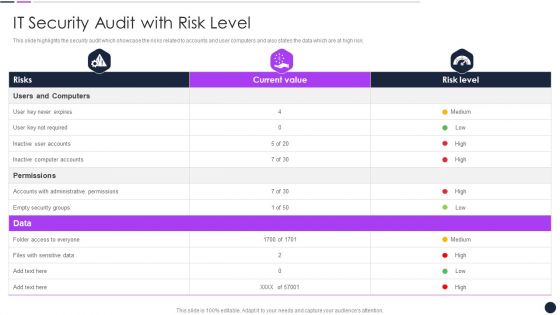
Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF
Deliver an awe inspiring pitch with this creative Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF bundle. Topics like Inactive Computer, Administrative Permissions, Security Groups can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
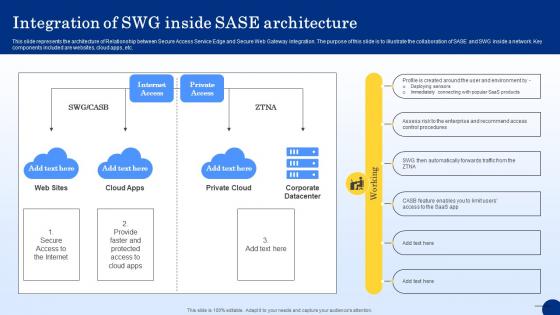
Integration Of SWG Inside SASE Architecture Web Threat Protection System
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of SWG Inside SASE Architecture Web Threat Protection System to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF
This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier. Find highly impressive Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Incorporation Of ISMS Framework Into Corporate Control Processes Inspiration PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Inspiration PDF. Use them to share invaluable insights on Risk Management, Management Information, Controlling Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
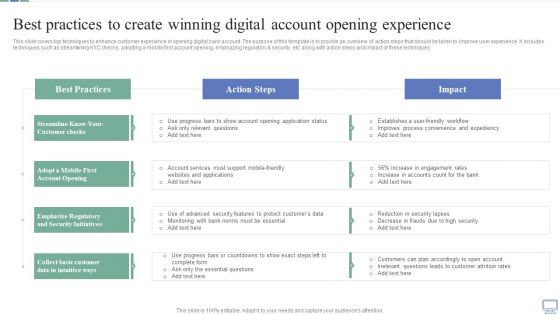
Best Practices To Create Winning Digital Account Opening Experience Mockup PDF
This slide covers top techniques to enhance customer experience in opening digital bank account. The purpose of this template is to provide an overview of action steps that should be taken to improve user experience. It includes techniques such as streamlining KYC checks, adopting a mobile first account opening, emphazing regulatory and security, etc along with action steps and impact of these techniques. Find a pre designed and impeccable Best Practices To Create Winning Digital Account Opening Experience Mockup PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF
This slide represents the introduction to software defined networking that helps network managers to manage network resources faster. It also includes its components such as applications, control plane, SDN controller, SDN datapath, data plane, switches, and so on. Presenting this PowerPoint presentation, titled SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
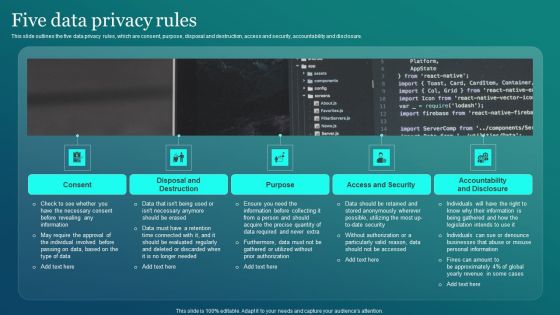
Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. Slidegeeks is here to make your presentations a breeze with Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
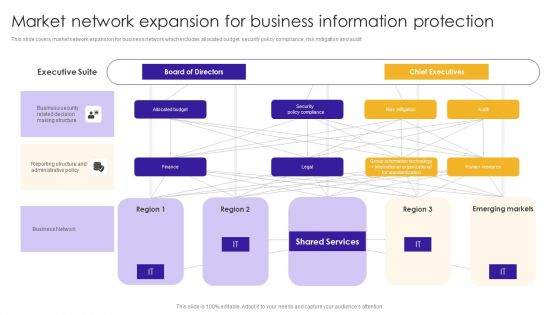
Market Network Expansion For Business Information Protection Sample PDF
This slide covers market network expansion for business network which includes allocated budget, security policy compliance, risk mitigation and audit. Showcasing this set of slides titled Market Network Expansion For Business Information Protection Sample PDF. The topics addressed in these templates are Business Security, Related Decision, Making Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.
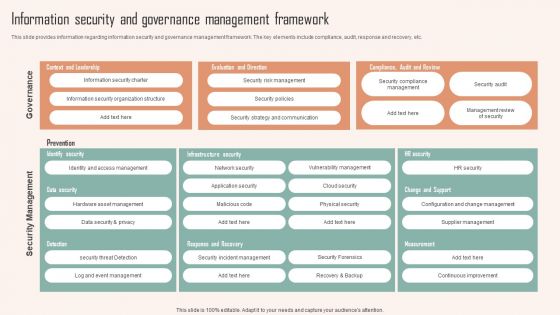
Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
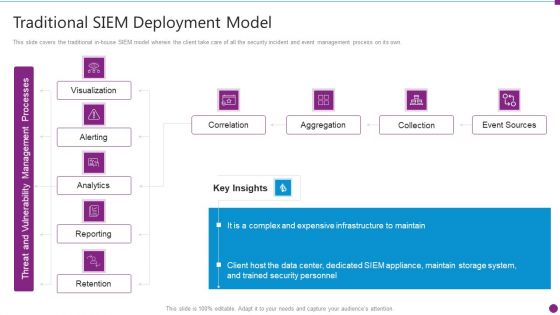
Security Information And Event Management Strategies For Financial Audit And Compliance Traditional SIEM Deployment Guidelines PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance traditional siem deployment guidelines pdf bundle. Topics like correlation, aggregation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF bundle. Topics like Corporate Data, Allowed Employees, Consumerization Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Overview Of Blockchain 51 Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Slidegeeks has constructed Overview Of Blockchain 51 Comprehensive Guide To Blockchain Digital Security Information Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Security Information And Event Management Strategies For Financial Audit And Compliance Cloud SIEM Model Diagrams PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance cloud siem model diagrams pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
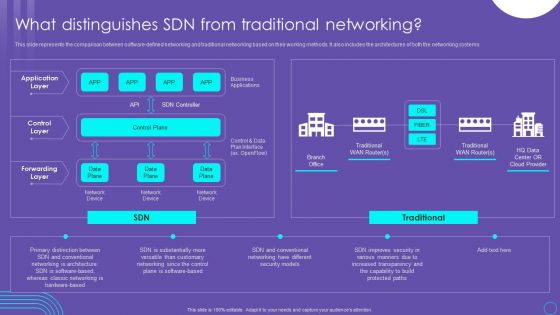
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Explore a selection of the finest Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Secure Web Gateway SWG Introduction And Features Ppt Portfolio Master Slide PDF
This slide describes the overview and features of the secure gateway. The purpose of this slide is to demonstrate the SWG and its benefits to businesses. The features include URL filtering, application control, data loss prevention, antivirus, and HTTPS inspection. Present like a pro with Secure Web Gateway SWG Introduction And Features Ppt Portfolio Master Slide PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
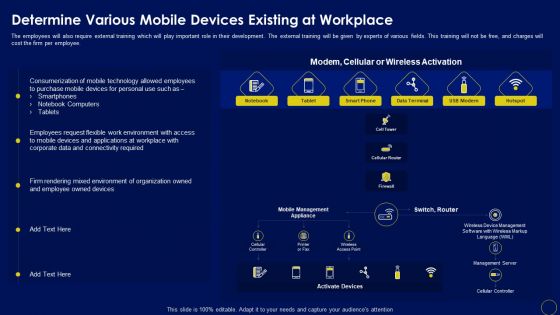
Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Do you know about Slidesgeeks Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Cognitive Visualizations Computing Strategy How Cognitive Technology Affects Functional Business Areas Slides PDF
This slide provides information regarding how cognitive technology affect core functional business areas such as front office, middle office and back office. Deliver an awe inspiring pitch with this creative Cognitive Visualizations Computing Strategy How Cognitive Technology Affects Functional Business Areas Slides PDF bundle. Topics like Customer Service, Product Development, Information Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
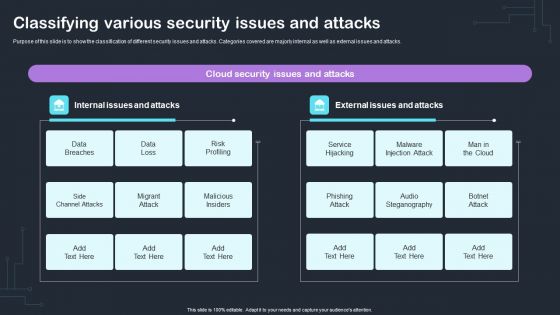
Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
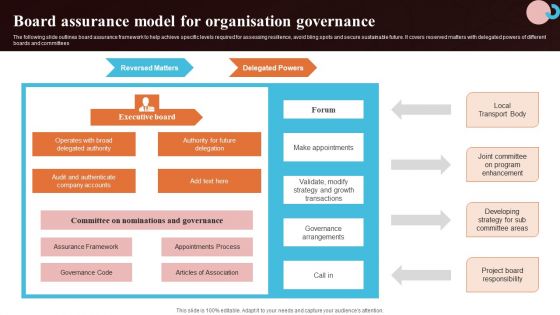
Board Assurance Model For Organisation Governance Diagrams PDF
The following slide outlines board assurance framework to help achieve specific levels required for assessing resilience, avoid bling spots and secure sustainable future. It covers reserved matters with delegated powers of different boards and committees. Showcasing this set of slides titled Board Assurance Model For Organisation Governance Diagrams PDF. The topics addressed in these templates are Assurance Framework, Appointments Process, Articles Of Association. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Key Issues Faced By Hospitality Sector Ppt PowerPoint Presentation Icon Example PDF
Showcasing this set of slides titled key issues faced by hospitality sector ppt powerpoint presentation icon example pdf. The topics addressed in these templates are management, data security, growth. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Presenting this PowerPoint presentation, titled Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF
The following slide will assist an IT company to show the investors or audience a complete view of its competitive landscape based on elements like leaders by category, company, their market capitalization and revenue. There are so many reasons you need a Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
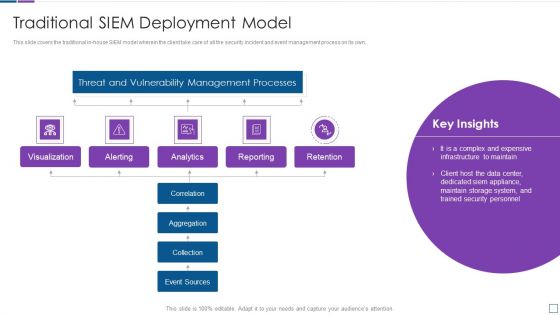
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
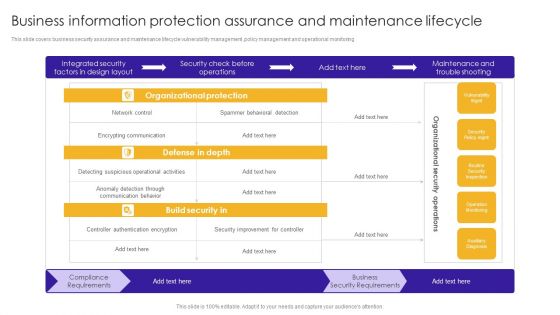
Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
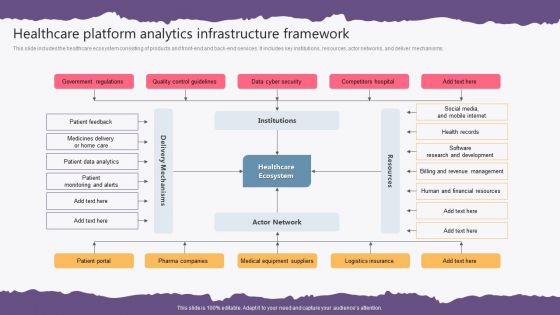
Healthcare Platform Analytics Infrastructure Framework Background PDF
This slide includes the healthcare ecosystem consisting of products and front-end and back-end services. It includes key institutions, resources, actor networks, and deliver mechanisms. Pitch your topic with ease and precision using this Healthcare Platform Analytics Infrastructure Framework Background PDF. This layout presents information on Government Regulations, Quality Control Guidelines, Data Cyber Security, Competitors Hospital. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Quantum Computing For Everyone IT How Will Quantum Computing Help Enterprises Download PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Deliver and pitch your topic in the best possible manner with this quantum computing for everyone it how will quantum computing help enterprises download pdf. Use them to share invaluable insights on development, optimization, accelerate autonomous, transform cybersecurity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
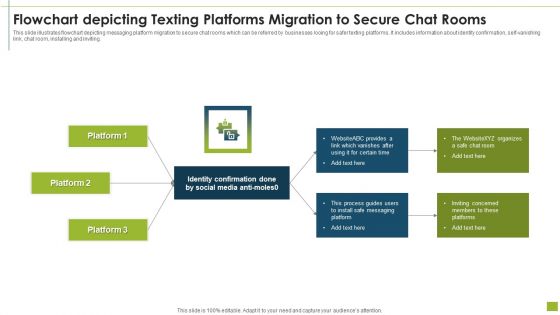
Flowchart Depicting Texting Platforms Migration To Secure Chat Rooms Inspiration PDF
This slide illustrates flowchart depicting messaging platform migration to secure chat rooms which can be referred by businesses looing for safer texting platforms. It includes information about identity confirmation, self-vanishing link, chat room, installing and inviting.Pitch your topic with ease and precision using this flowchart depicting texting platforms migration to secure chat rooms inspiration pdf This layout presents information on identity confirmation, process guides, install safe messaging It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
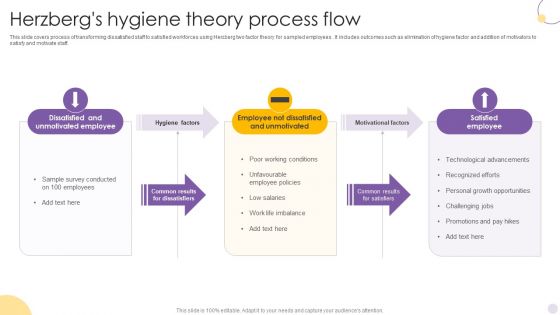
Herzbergs Hygiene Theory Process Flow Introduction PDF
This slide covers conditional hygiene and motivating factors to match motivation with job requirements. It includes extrinsic and intrinsic factors such as salary and pay hikes, secure working conditions , grow and career opportunities, recognition of efforts, etc. Showcasing this set of slides titled Herzbergs Hygiene Theory Process Flow Introduction PDF. The topics addressed in these templates are Hygiene Factors, Motivational Factors, Satisfied Employee. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
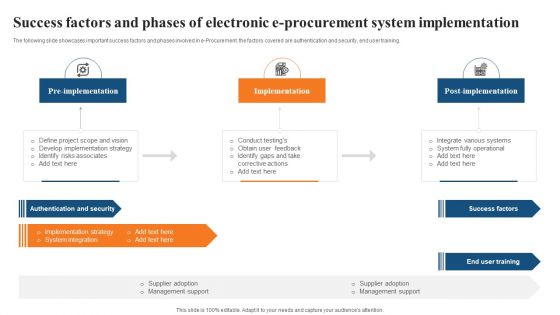
Success Factors And Phases Of Electronic E Procurement System Implementation Formats PDF

BI Implementation To Enhance Hiring Process Business Intelligence Hybrid Architecture Framework Structure PDF
This slide represents the hybrid architecture including both technologies of data mart and OLAP cubes. It includes key recommendations such as implementation of data marts as part of data security for data aggregation etc.Slidegeeks is here to make your presentations a breeze with BI Implementation To Enhance Hiring Process Business Intelligence Hybrid Architecture Framework Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Roadmap To Identify And Launch Devops Initiatives Ppt Professional Slide Download PDF
This template covers DevOps implementation roadmaps starting from organizing devOps initiative, then building, containerizing, integrating, test automation and monitoring etc. Deliver and pitch your topic in the best possible manner with this roadmap to identify and launch devops initiatives ppt professional slide download pdf. Use them to share invaluable insights on process, security, strategy, opportunities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
RUP Methodology Management And Control Change Software Icons PDF
This slide represents how management and control change software is easy in the rational unified process methodology RUP also determines work and security domains.Deliver an awe inspiring pitch with this creative RUP Methodology Management And Control Change Software Icons PDF bundle. Topics like Unforeseen Effects On Applications, Management Is Critical, Domains Assuring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Overview Of Centralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V
This slide covers brief summary of centralized crypto exchanges with steps to interact by users. It also includes benefits such as high liquidity, user friendly, diverse cryptocurrencies, advanced trading features, fiat support, security measures, customer support, market insights and additional services, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Centralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Centralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
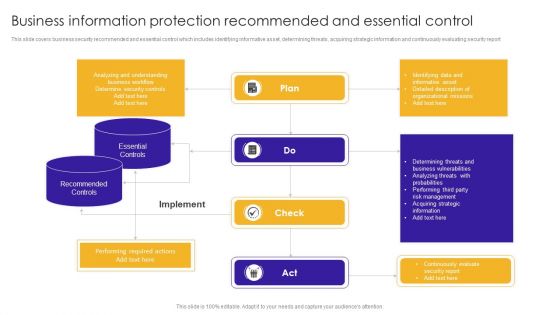
Business Information Protection Recommended And Essential Control Background PDF
This slide covers business security recommended and essential control which includes identifying informative asset, determining threats, acquiring strategic information and continuously evaluating security report. Showcasing this set of slides titled Business Information Protection Recommended And Essential Control Background PDF. The topics addressed in these templates are Determining Threats, Business Vulnerabilities, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

 Home
Home