Safety Improvement Plan
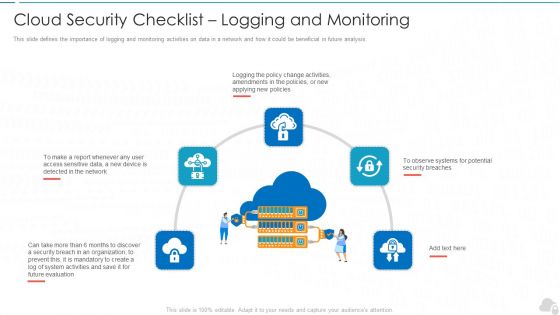
Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
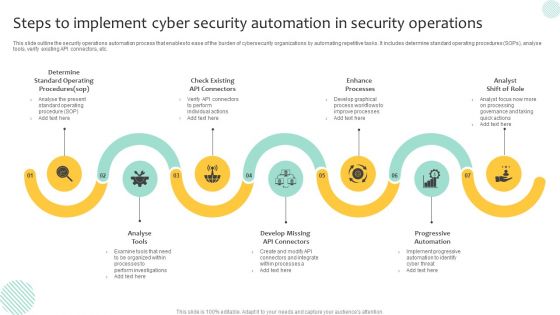
Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF
This slide outline the security operations automation process that enables to ease of the burden of cybersecurity organizations by automating repetitive tasks. It includes determine standard operating procedures SOPs, analyse tools, verify existing API connectors, etc. Presenting Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Progressive Automation, Enhance Processes, Analyse Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
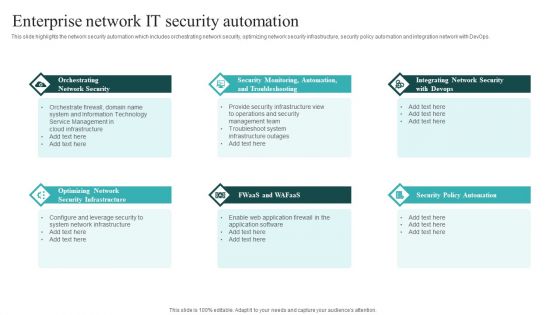
IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Security Framework In Cloud Computing IT Security IT Ppt Portfolio Pictures PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a security framework in cloud computing it security it ppt portfolio pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, respond, protect, identify, detect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Security Framework In Cloud Computing Ppt Summary Designs PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Presenting information security security framework in cloud computing ppt summary designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identify, protect, detect, respond, recover. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Security Framework In Cloud Computing Ppt Model Sample PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a it security security framework in cloud computing ppt model sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, respond, identify, protect, detect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Development And Operations Pipeline IT Major Steps To Be Considered While Building Devops Pipeline Architecture Designs PDF
Following slide provides information about the steps to be considered like CI framework installation, enabling the use of automation tools while developing DevOps pipeline architecture. Presenting development and operations pipeline it major steps to be considered while building devops pipeline architecture designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, environments, management, integration, framework. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Prevention Strategy Ppt PowerPoint Presentation Ideas Format Ideas Cpb
Presenting this set of slides with name cyber security prevention strategy ppt powerpoint presentation ideas format ideas cpb. This is an editable Powerpoint eight stages graphic that deals with topics like cyber security prevention strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.Presenting ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Asset Management, Operational Security, Physical And Environmental. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
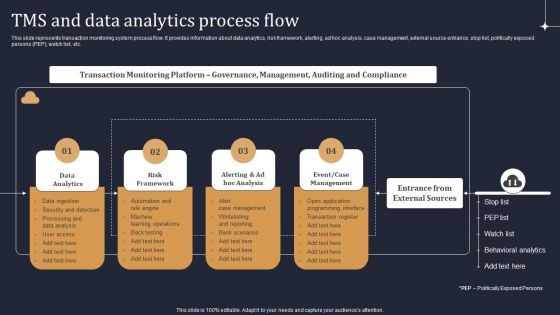
KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Icons Slide Inspiration PDF
Introducing our well designed Executing security management program to mitigate threats and safeguard confidential organizational data icons slide inspiration pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Integrations Ideas PDF
This is a security information and event management strategies for financial audit and compliance siem integrations ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF
This slide depicts cyber security principles, including work factor, compromising recording, the economy of mechanism, fail-safe defaults, complete mediation, open design, separation of privilege, least privilege, least common mechanism, and so on. Get a simple yet stunning designed Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Impact On Organization After Implementing Computer Security Strategy And Training Ideas PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. This is a impact on organization after implementing computer security strategy and training ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network intrusion, system misconfiguration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
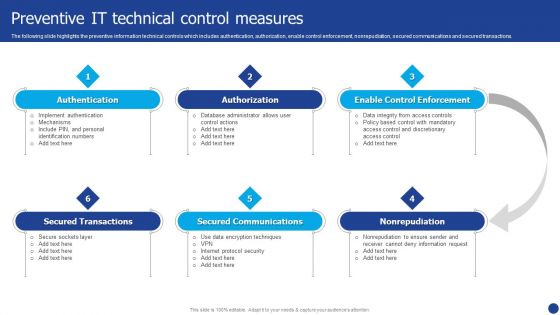
Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
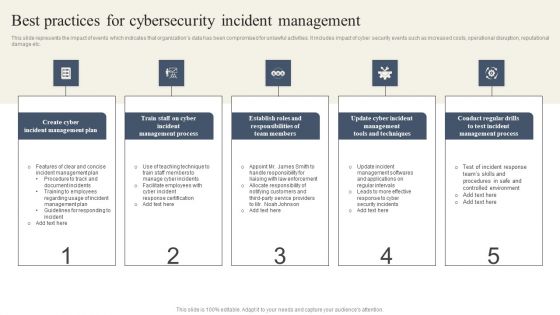
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Smart Phone Security Key Aspects For Growing Revenue Icons PDF
This slide shows every aspect of phone security model that should be considered while framing security policy for organization. It include aspects such as compliance security, product security and infrastructure security etc. Presenting Smart Phone Security Key Aspects For Growing Revenue Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Compliance Security, Product Security, Infrastructure Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF
The following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Presenting Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Responsibilities, Security Awareness, Data Support, Data Segregation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
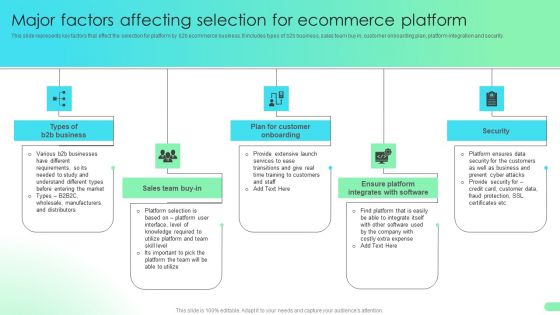
Major Factors Affecting Selection For Ecommerce Platform Comprehensive Guide For Developing Microsoft PDF
This slide represents key factors that effect the selection for platform by b2b ecommerce business. It includes types of b2b business, sales team buy in, customer onboarding plan, platform integration and security.The Major Factors Affecting Selection For Ecommerce Platform Comprehensive Guide For Developing Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Website Designing And Development Service Benefits Of Content Management Ideas PDF
This slide represents the benefits of using a Content Management System in the organization, and it provides features such as on page SEO, teams collaboration, template making, security, and analytics.Presenting Website Designing And Development Service Benefits Of Content Management Ideas PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Collaboration, Templates, Easily Collaborate In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud-Based Identify And Access Management Technique Best Practices Slides PDF
This slide shows ideal practices for IAM strategy. The purpose of this strategy is to highlight all effective practices along with concerned activities. It include practices such as defining IAM vision, building strong foundation , etc. Presenting Cloud-Based Identify And Access Management Technique Best Practices Slides PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Vision Clearly, Strong Foundation, Secure Generic Accounts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Technology Risks With Security Incident Management Ppt PowerPoint Presentation Gallery Graphics Template PDF
Presenting cloud technology risks with security incident management ppt powerpoint presentation gallery graphics template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification and allowance, management interface vulnerability, security incident management, application security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Infotech Solutions Research And Development Company Summary Information Technology Services Infographics PDF
The slide showcases range of information technology services offered by company for customers. It depicts managed services, intelligent business services, digital experience, solution engineering, innovation services and technology and security advisory. This is a Infotech Solutions Research And Development Company Summary Information Technology Services Infographics PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managed Services, Intelligent Business, Digital Experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Presenting this PowerPoint presentation, titled CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

IT Data Services Certification Programs Certified Data Professional Program CDP Structure PDF
This slide covers the CDP course details such as CDP Benefits, Who should become CDP, salary expectations, International Standards for CDP Program etc. This is a IT Data Services Certification Programs Certified Data Professional Program CDP Structure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like International Standards, Information Security, Data Protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Service Marketing Fundraising Future Of Services Managed By Firm Background PDF
This slide caters details about future of services managed by firm with details about firms overall future strategy. This is a service marketing fundraising future of services managed by firm background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data analytics, cloud computing technology, transforming security infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Awards And Accolades Structure PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year.This is a Security And Surveillance Company Profile Awards And Accolades Structure PDF template with various stages. Focus and dispense information on Four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Digital Trends, Consumer Technology, Technology Association. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Components Of Data Security Management Framework Pictures PDF
This slide showcases a framework highlighting key areas covered in data security governance to manage business information. It includes key components such as quality, knowledge, ownership, accessibility and security. Presenting Key Components Of Data Security Management Framework Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Ownership, Accessibility, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
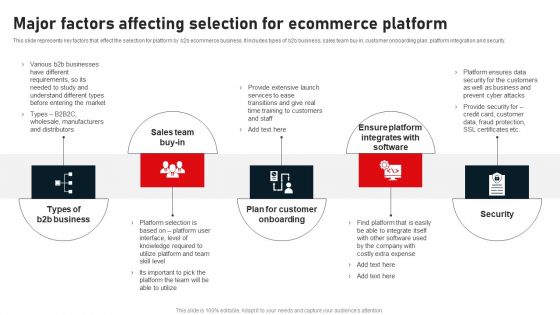
Major Factors Affecting Selection For Ecommerce Platform Brochure PDF
This slide represents key factors that effect the selection for platform by b2b ecommerce business. It includes types of b2b business, sales team buy in, customer onboarding plan, platform integration and security. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Major Factors Affecting Selection For Ecommerce Platform Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Major Factors Affecting Selection For Ecommerce Platform Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
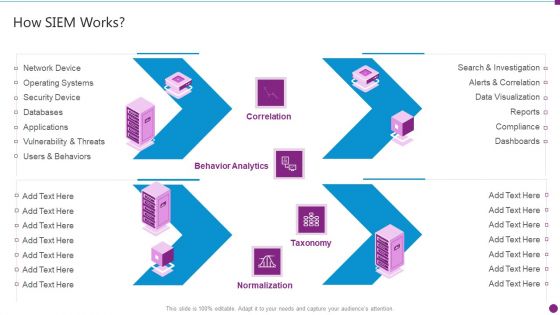
Security Information And Event Management Strategies For Financial Audit And Compliance How SIEM Works Clipart PDF
Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance how siem works clipart pdf bundle. Topics like behavior analytics, correlation, taxonomy, normalization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.This is a Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Categorization, Incident Resolution, Incident Prioritization You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF
This template covers account based marketing strategy such as create content that provide value to the customers. It also depicts that Different types of target accounts require additional content focuses.Presenting Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Competitors Customers, Strategic Importance, Different. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
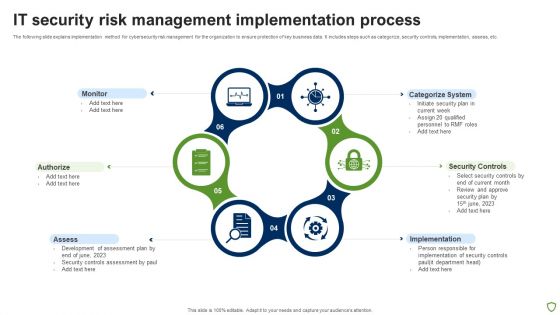
IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Supply Chain Security Management Model Infographics PDF
This slide represents the framework showing the management of supply chain security. It includes details related to supply chain security goals such as facility, cargo, human resource, information and ABC companys management system along with their respective security measures. Presenting Supply Chain Security Management Model Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Human Resources Management, Cargo Management, Facility Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Machine To Machine Communication IOT Security Challenges Pictures PDF
The slide highlights key Challenges in IoT security.Presenting machine to machine communication iot security challenges pictures pdf. to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like confidentiality, secure middleware, policy enforcement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
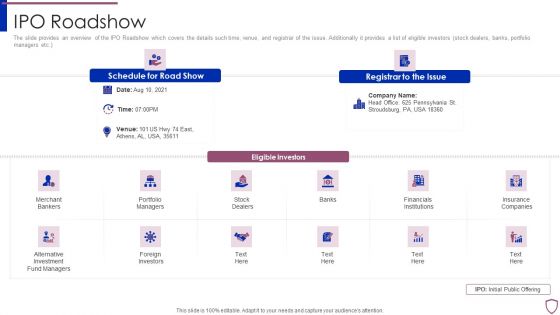
Financing Catalogue For Security Underwriting Agreement IPO Roadshow Topics PDF
The slide provides an overview of the IPO Roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc. This is a financing catalogue for security underwriting agreement ipo roadshow topics pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like merchant bankers, portfolio managers, financials institutions, foreign investors, insurance companies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Security Framework In Cloud Computing Ppt Portfolio Grid PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a cybersecurity security framework in cloud computing ppt portfolio grid pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, identify, protect, detect, respond. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
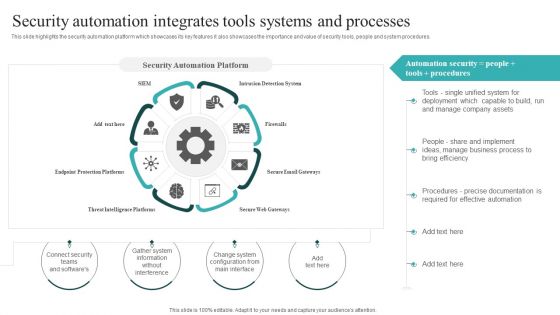
IT Security Automation Systems Guide Security Automation Integrates Tools Systems And Processes Graphics PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Slidegeeks is here to make your presentations a breeze with IT Security Automation Systems Guide Security Automation Integrates Tools Systems And Processes Graphics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Strategies To Rebuild CIBIL To Prevent Bankruptcy Information PDF
This slide showcases ways to rebuild credit information bureau India limited score to overcome bankruptcy . It includes reviewing CIBIL reports regularly , not closing the amounts , applying for a secure credit card , avoid visiting credit repair service etc. Persuade your audience using this Strategies To Rebuild CIBIL To Prevent Bankruptcy Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information, Payments, Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
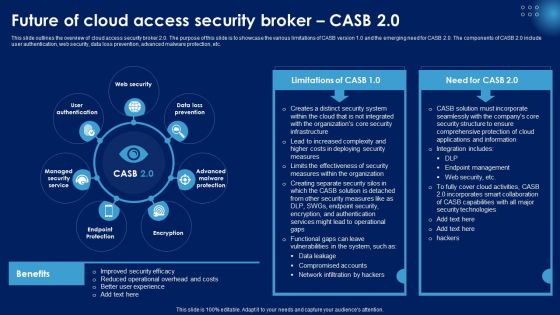
Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Explore a selection of the finest Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Security Management Tools Techniques Ppt PowerPoint Presentation Summary Cpb Pdf
Presenting this set of slides with name security management tools techniques ppt powerpoint presentation summary cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like security management tools techniques to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
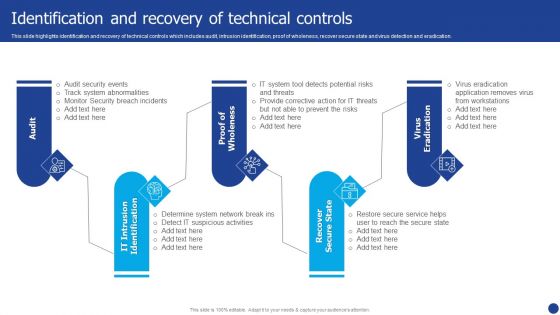
Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Impact Of Everything As A Service On Business Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Grid PDF
This slide depicts the benefits of XaaS, including cost savings, scalability, accessibility, faster implementation, quick modification, better security, and boosting innovation.This is a Impact Of Everything As A Service On Business Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Grid PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Faster Implementation, Quick Modification, Boost Innovation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF
This slide depicts the hybrid cloud storage service, its implementation method, and advantages such as Flexibility and security, cost effectiveness and excellence in risk management. If you are looking for a format to display your unique thoughts, then the professionally designed Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security Automation Integrates Security Automation To Analyze And Mitigate Cyberthreats Slides PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures.Present like a pro with Security Automation Integrates Security Automation To Analyze And Mitigate Cyberthreats Slides PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
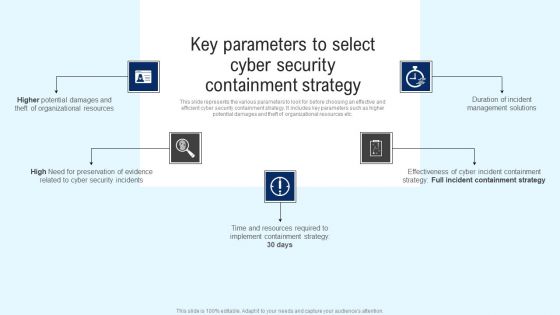
Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
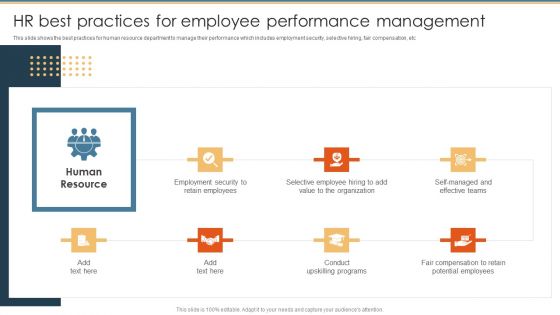
Methods To Optimize HR Operations HR Best Practices For Employee Performance Management Background PDF
This slide shows the best practices for human resource department to manage their performance which includes employment security, selective hiring, fair compensation, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Methods To Optimize HR Operations HR Best Practices For Employee Performance Management Background PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Human Rights Policies Of The Company Icons PDF
This slide shows the human rights policies that are followed by the company for the betterment of community and employees such as stakeholder engagement, diversity and inclusion, safe and healthy workplace, workplace security, work hours, wages and benefits etc. Presenting human rights policies of the company icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like community and stakeholder engagement, diversity and inclusion, safe and healthy workplace. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
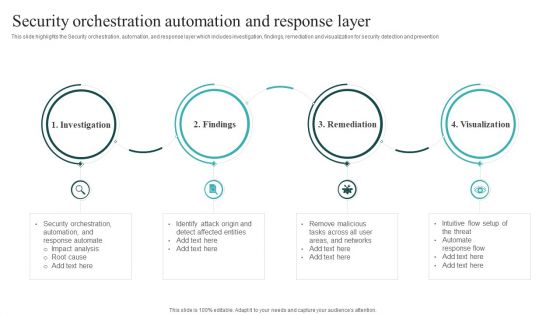
IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF can be your best option for delivering a presentation. Represent everything in detail using IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
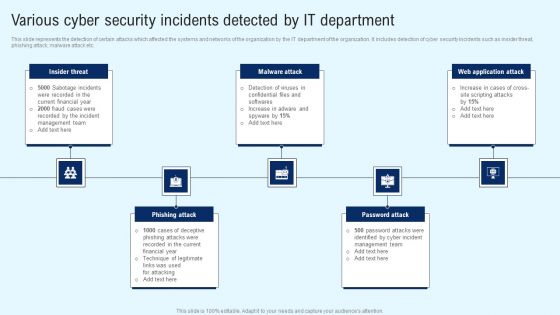
Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
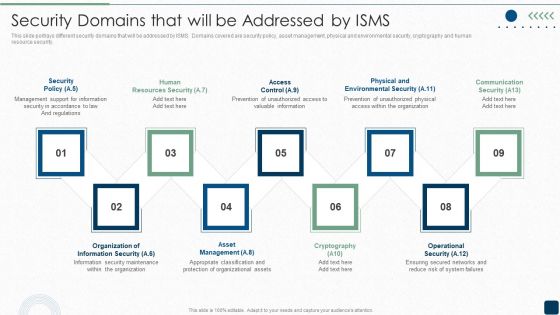
Security Domains That Will Be Addressed By ISMS Diagrams PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.This is a Security Domains That Will Be Addressed By ISMS Diagrams PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Support, Resources Security, Prevention Of Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Risk Analysis Model With Metrics Ppt PowerPoint Presentation Outline Designs PDF
Persuade your audience using this security risk analysis model with metrics ppt powerpoint presentation outline designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including automated discovery, define system relationships, automated asset classification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
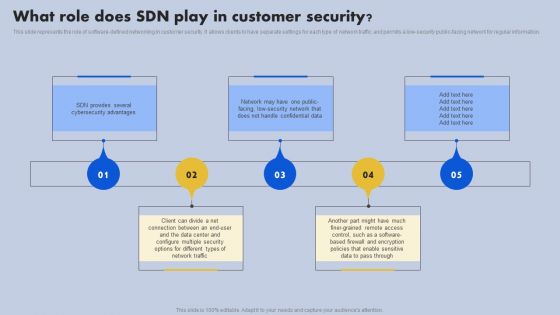
What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
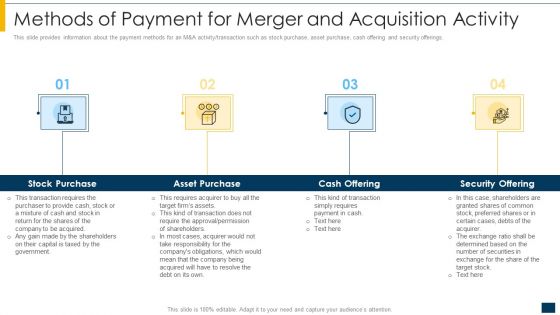
Methods Of Payment For Merger And Acquisition Activity Ppt Professional Vector PDF
This slide provides information about the payment methods for an M and A activity transaction such as stock purchase, asset purchase, cash offering and security offerings. Presenting methods of payment for merger and acquisition activity ppt professional vector pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like stock purchase, asset purchase, cash offering, security offering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
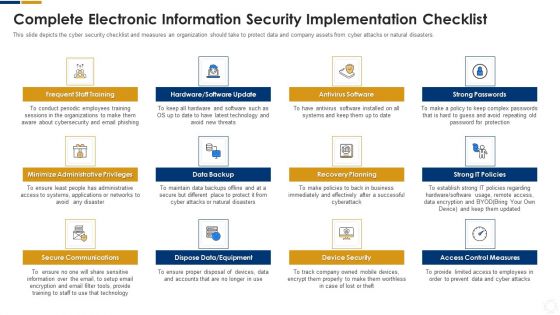
Cybersecurity Complete Electronic Information Security Implementation Checklist Ppt Inspiration Outline PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting cybersecurity complete electronic information security implementation checklist ppt inspiration outline pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, equipment, secure communications, data backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
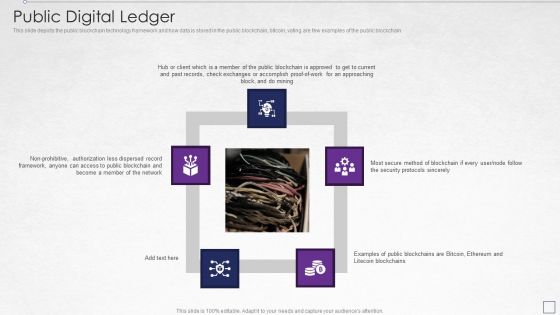
Digitized Record Book Technology Public Digital Ledger Download PDF
This slide depicts the public blockchain technology framework and how data is stored in the public blockchain, bitcoin, voting are few examples of the public blockchain. Presenting digitized record book technology public digital ledger download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like method, secure, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
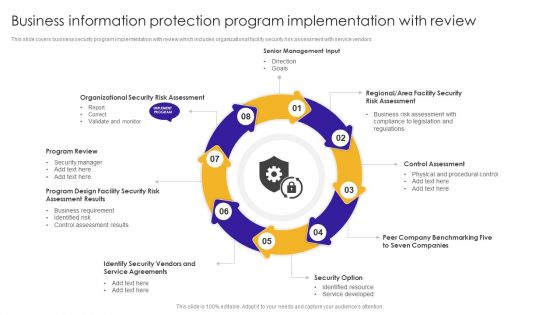
Business Information Protection Program Implementation With Review Information PDF
This slide covers business security program implementation with review which includes organizational facility security risk assessment with service vendors.Persuade your audience using this Business Information Protection Program Implementation With Review Information PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Program Review, Assessment Results, Business Requirement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home