Safety Improvement Plan

Information Security Main Principle Of Information Security Ppt Outline Guidelines PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. This is a information security main principle of information security ppt outline guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like integrity, confidentiality, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Everything As A Service Xaas For Cloud Computing IT Impact Of Everything As A Service On Business Template PDF
This slide depicts the benefits of XaaS, including cost savings, scalability, accessibility, faster implementation, quick modification, better security, and boosting innovation. Presenting everything as a service xaas for cloud computing it impact of everything as a service on business template pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like accessibility, scalability, cost savings, better security, quick modification. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Elements Of Electronic Information Security Cloud Security Ppt Outline Background Designs PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a cybersecurity elements of electronic information security cloud security ppt outline background designs pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, risks, resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Develop Secure Database Ppt PowerPoint Presentation Outline Graphic Tips Cpb
Presenting this set of slides with name develop secure database ppt powerpoint presentation outline graphic tips cpb. This is an editable Powerpoint four stages graphic that deals with topics like develop secure database to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Google Cloud Console IT Benefits Of Google Cloud To The Organization Ppt Styles Templates PDF
This slide describes the main benefits of the Google Cloud based on cost, performance, data migration, network type, and control and security. Presenting google cloud console it benefits of google cloud to the organization ppt styles templates pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like cost effective price plans, live migration, private network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
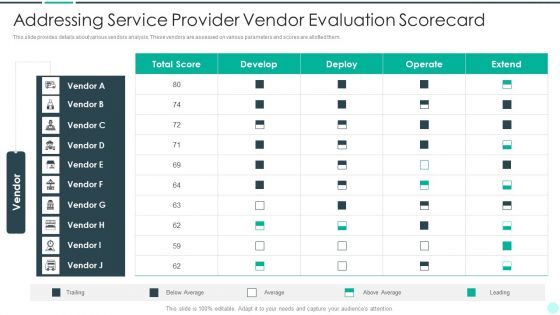
Executing Advance Data Analytics At Workspace Addressing Service Provider Vendor Formats PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing service provider vendor formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fault management, performance management, configuration management, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
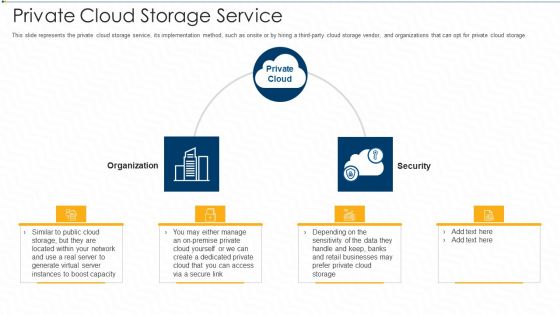
Private Cloud Storage Service Ppt Pictures Slide PDF
This slide represents the private cloud storage service, its implementation method, such as onsite or by hiring a third party cloud storage vendor, and organizations that can opt for private cloud storage. This is a private cloud storage service ppt pictures slide pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, secure, businesses, security, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Managing Cyber Security Risks Ppt PowerPoint Presentation Outline Slide Cpb
Presenting this set of slides with name managing cyber security risks ppt powerpoint presentation outline slide cpb. This is an editable Powerpoint four stages graphic that deals with topics like managing cyber security risks to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Operations Analytics Reporting Ppt PowerPoint Presentation Outline Templates Cpb
Presenting this set of slides with name security operations analytics reporting ppt powerpoint presentation outline templates cpb. This is an editable Powerpoint four stages graphic that deals with topics like security operations analytics reporting to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Corporate Security Tool Ppt PowerPoint Presentation Outline Sample Cpb Pdf
Presenting this set of slides with name corporate security tool ppt powerpoint presentation outline sample cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like corporate security tool to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Cloud Computing Security Management Ppt PowerPoint Presentation Outline Icons Cpb
Presenting this set of slides with name cloud computing security management ppt powerpoint presentation outline icons cpb. This is an editable Powerpoint four stages graphic that deals with topics like cloud computing security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF
This slide covers framework to ensure safe transactions on ecommerce platform. It includes regulatory strategies, financial and marketing operation strategies. Persuade your audience using this E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Transactions, Assurance Metrics, Document Intellectual. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
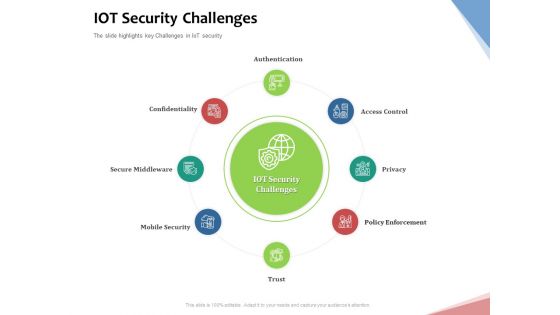
Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manual Vulnerability, Vulnerability Scanning, Automation Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
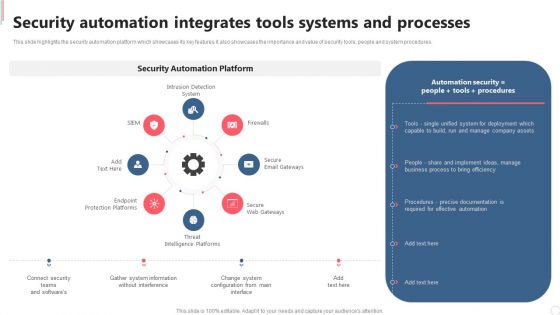
Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. There are so many reasons you need a Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Information Security What Is Data Security And How Does It Work Ppt Professional Infographics PDF
This slide defines the meaning of data security and how it helps to prevent data through different methods and techniques. Presenting information security what is data security and how does it work ppt professional infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like techniques, computer systems, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
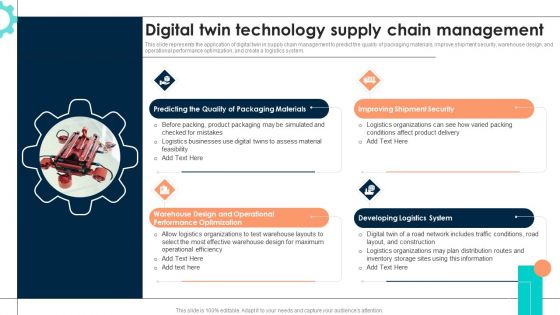
Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Best Practices To Create Winning Digital Account Opening Experience Infographics PDF
This slide covers top techniques to enhance customer experience in opening digital bank account. The purpose of this template is to provide an overview of action steps that should be taken to improve user experience. It includes techniques such as streamlining KYC checks, adopting a mobile first account opening, emphazing regulatory and security, etc along with action steps and impact of these techniques. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices To Create Winning Digital Account Opening Experience Infographics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Implement Electronic Health Records Techniques Brochure PDF
This slide showcases the strategies to implement electronic health records EHRs. It includes strategies such as integrate reliable EHR system, secure patient data, use data analytics and train staff. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implement Electronic Health Records Techniques Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implement Electronic Health Records Techniques Brochure PDF

Security Risk Management Assessment Checklist Structure PDF
Presenting security risk management assessment checklist structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, media handling security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
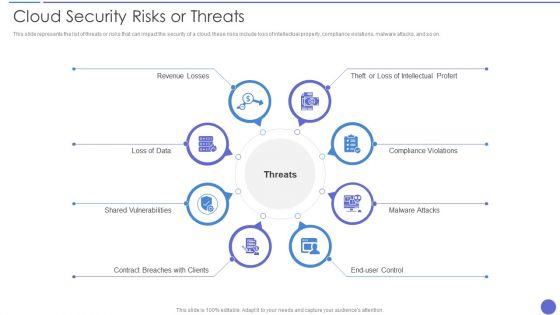
Cloud Security Risks Or Threats Brochure PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Security Risks Or Threats Brochure PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Malware Attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
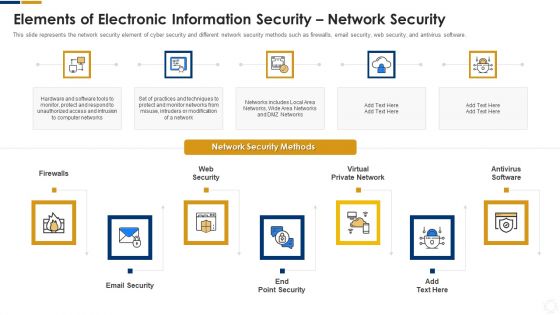
Cybersecurity Elements Of Electronic Information Security Network Security Ppt Ideas Skills PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a cybersecurity elements of electronic information security network security ppt ideas skills pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
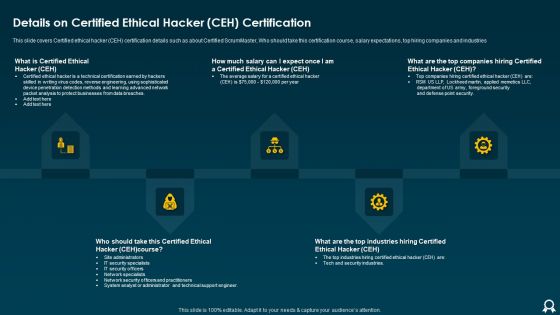
IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. This is a IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Average Salary, Point Security, Methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Service Desk Incident Management Framework Brochure PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Service Desk Incident Management Framework Brochure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Service Desk Incident Management Framework Brochure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Reverse Proxy CASB Deployment Model Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Reverse Proxy CASB Deployment Model Ppt PowerPoint Presentation Diagram Lists PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Reverse Proxy CASB Deployment Model Ppt PowerPoint Presentation Diagram Lists PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
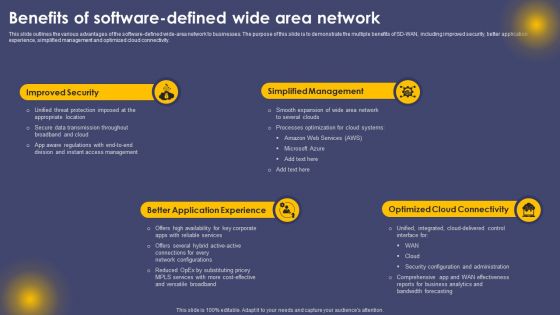
Benefits Of Software Defined Wide Area Network Ppt Professional Styles PDF
This slide outlines the various advantages of the software-defined wide-area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD-WAN, including improved security, better application experience, simplified management and optimized cloud connectivity. Take your projects to the next level with our ultimate collection of Benefits Of Software Defined Wide Area Network Ppt Professional Styles PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

11 Piece Wheel With New Product Launch Steps Ppt Diagram Lists PDF
Persuade your audience using this 11 Piece Wheel With New Product Launch Steps Ppt Diagram Lists PDF. This PPT design covers eleven stages, thus making it a great tool to use. It also caters to a variety of topics including Insure Security, Value And Market, Development Team. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Understanding The Kubernetes Concepts And Architecture Best Security Measures In Kubernetes Ppt Outline Templates PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture best security measures in kubernetes ppt outline templates pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
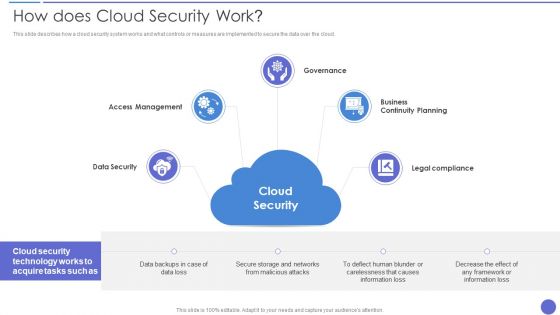
How Does Cloud Security Work Download PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a How Does Cloud Security Work Download PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organizations, Encryption Methods, Secure Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF
This slide describes the establishment of cyber policies by international laws, including the budapest convention on cybercrime and the united nations group of governmental experts. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Cyber Security Crisis Communication Process Framework Icons PDF
This slide showcases a model of crisis communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Presenting Cyber Security Crisis Communication Process Framework Icons PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Implement Strategy, Identify Community, Set Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
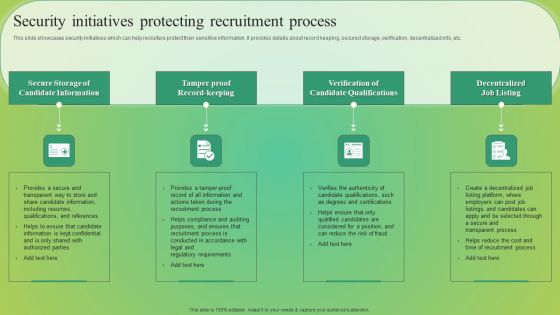
Security Initiatives Protecting Recruitment Process Elements PDF
This slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Slidegeeks is here to make your presentations a breeze with Security Initiatives Protecting Recruitment Process Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Insider Attacker Method And Behaviour Assessment Information PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver an awe inspiring pitch with this creative insider attacker method and behaviour assessment information pdf bundle. Topics like logging in at odd hours, first time accessing system, copying large amount of information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
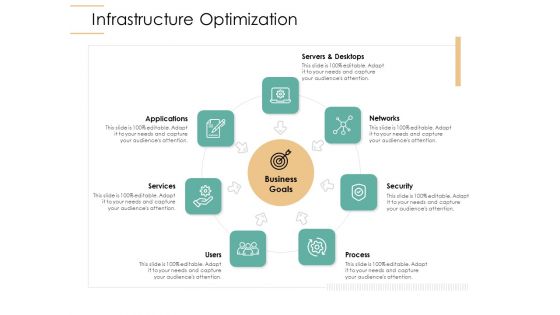
Infrastructure Strategies Infrastructure Optimization Ppt Layouts Slides PDF
Presenting infrastructure strategies infrastructure optimization ppt layouts slides pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like services, networks, servers and desktops, security, process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Security Risks Or Threats Cloud Computing Security IT Ppt Icon PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting cloud security risks or threats cloud computing security it ppt icon pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like revenue losses, loss of data, shared vulnerabilities, compliance violations, malware attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
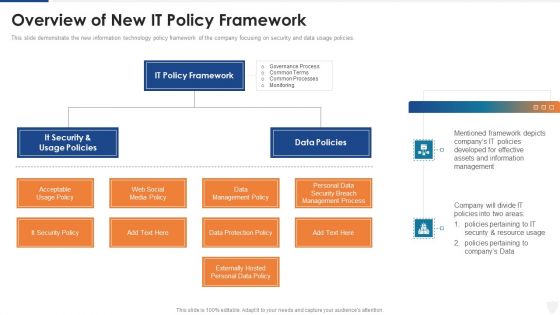
Overview Of New IT Policy Framework Ppt Summary Format Ideas PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting overview of new it policy framework ppt summary format ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like management policy, security breach, information, resource. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Be Adopted 1 Data Encryption Ppt Outline PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt outline pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Omnichannel Strategy Implementation For Banking Solutions Self Service Bill Payment Kiosks Process Brochure PDF
This slide covers process to be followed while paying bills using a secure self service kiosks. The purpose of this template is to provide customer a guide to follow for better experience. It includes steps starting from selecting payment option on kiosks, entering amount to be paid, scanning the QR code generated, etc. Find highly impressive Omnichannel Strategy Implementation For Banking Solutions Self Service Bill Payment Kiosks Process Brochure PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Omnichannel Strategy Implementation For Banking Solutions Self Service Bill Payment Kiosks Process Brochure PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
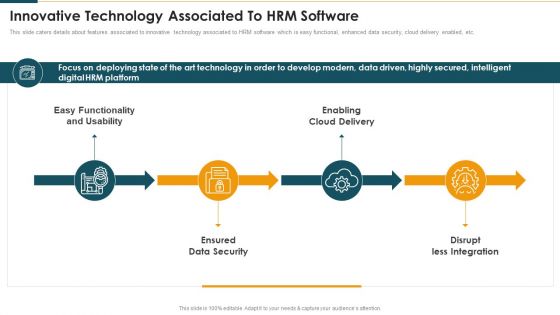
Innovative Technology Associated To Hrm Software Mockup PDF
This slide caters details about features associated to innovative technology associated to HRM software which is easy functional, enhanced data security, cloud delivery enabled, etc. This is a Innovative Technology Associated To Hrm Software Mockup PDF template with various stages. Focus and dispense information on fourstages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functionality And Usability, Enabling Cloud Delivery, Ensured Data Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ways For Integrating Security In Application Development Procedure Structure PDF
This slide shows the ways through which the vulnerabilities arising in the process of mobile application development could be eliminated. It includes three steps which are as follows knowledge of your code, prioritize your vulnerabilities and fixation of threats. Persuade your audience using this ways for integrating security in application development procedure structure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including prioritize your vulnerabilities, knowledge of your code, fix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategies For Successful Customer Base Development In B2b M Commerce Major Factors Affecting Selection For Ecommerce Microsoft PDF
This slide represents key factors that effect the selection for platform by b2b ecommerce business. It includes types of b2b business, sales team buy in, customer onboarding plan, platform integration and security. Find highly impressive Strategies For Successful Customer Base Development In B2b M Commerce Major Factors Affecting Selection For Ecommerce Microsoft PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Strategies For Successful Customer Base Development In B2b M Commerce Major Factors Affecting Selection For Ecommerce Microsoft PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
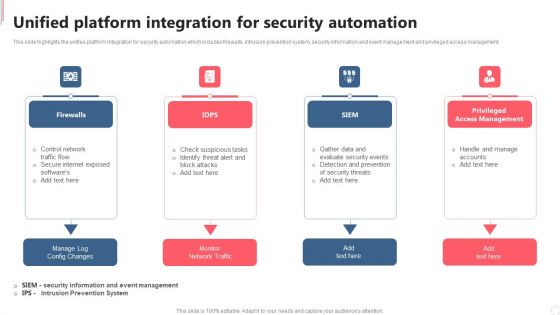
Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present like a pro with Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Agile Project Management Strategy 10 Agile Successful Strategies Portrait PDF
This slide provides the glimpse about the ten successful strategies for transitioning agile such as management commitment, team empowerment, collaborative culture, embrace agile methods, etc.This is a agile project management strategy 10 agile successful strategies portrait pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure management commitment, empowering the team, understand the collaborative culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Where Is The Gap In Security Programs Hacking Prevention Awareness Training For IT Security Diagrams PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a where is the gap in security programs hacking prevention awareness training for it security diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Steps Included In Data Retention Security Mechanism Introduction PDF
This slide depicts the steps covered in data retention policy. The steps included are determine applicable regulations, catalogue data, decision making, policy documentation and implementation.Persuade your audience using this Steps Included In Data Retention Security Mechanism Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Catalogue Data, Decision Making, Document Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

SME And Startups Financing Services Techniques Used In Finance Outsourcing Microsoft PDF
This slide shows the various techniques used by the outsourcing company such as FTP server-based technique, secure VPN based technique, etc. Presenting sme and startups financing services techniques used in finance outsourcing microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ftp server based, secure vpn based, online bookkeeping. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Get a simple yet stunning designed Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
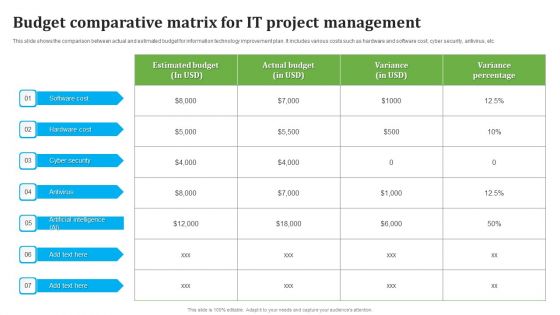
Budget Comparative Matrix For IT Project Management Information PDF
This slide shows the comparison between actual and estimated budget for information technology improvement plan. It includes various costs such as hardware and software cost, cyber security, antivirus, etc. Showcasing this set of slides titled Budget Comparative Matrix For IT Project Management Information PDF. The topics addressed in these templates are Budget Comparative Matrix, IT Project Management . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
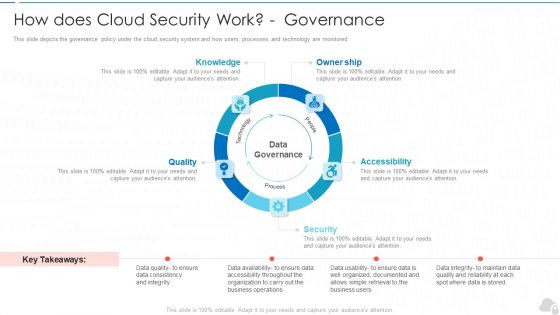
How Does Cloud Security Work Governance Cloud Computing Security IT Ppt Layouts Structure PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a how does cloud security work governance cloud computing security it ppt layouts structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like knowledge, owner ship, quality, security, accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
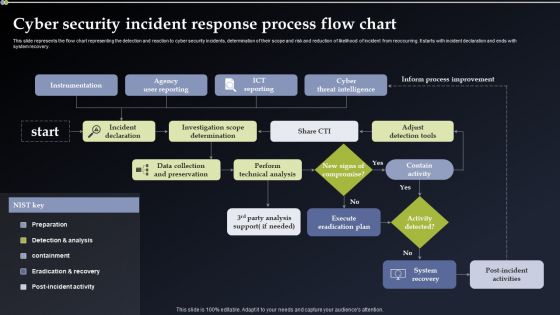
Cyber Security Incident Response Process Flow Chart Information PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Process Flow Chart Information PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Process Flow Chart Information PDF.

Steps To Develop Strategic IT Security Program Structure PDF
This slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc.Persuade your audience using this Steps To Develop Strategic IT Security Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Program Assessment, Emerging Threats, Organizational Culture Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digitized Record Book Technology Is Digital Ledger Technology Secure Sample PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Presenting digitized record book technology is digital ledger technology secure sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like information, data, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Presenting Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Accessibility, Knowledge, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. This Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
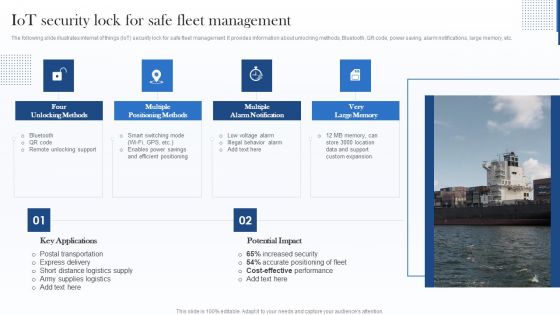
Iot Security Lock For Safe Fleet Management Sample PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
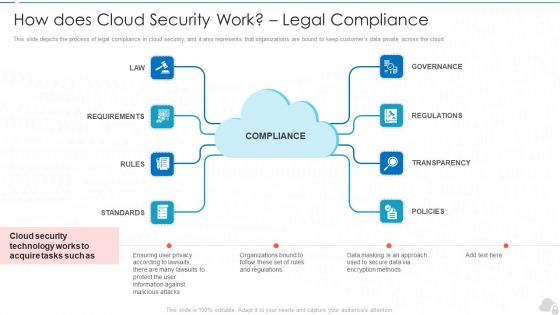
How Does Cloud Security Work Legal Compliance Cloud Computing Security IT Ppt Model Maker PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a how does cloud security work legal compliance cloud computing security it ppt model maker pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like governance, regulations, transparency, policies, rules. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home