Metrics Security

Access Regulations Technology Six Months Roadmap With Security Solution Brochure
Introducing our access regulations technology six months roadmap with security solution brochure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
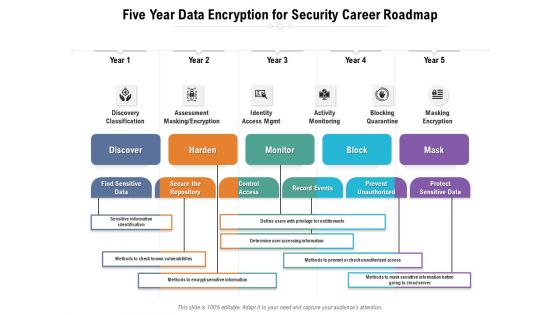
Five Year Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured five year data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Four Quarter Individual Data Security Career Roadmap Sample
Presenting our innovatively-structured four quarter individual data security career roadmap sample Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
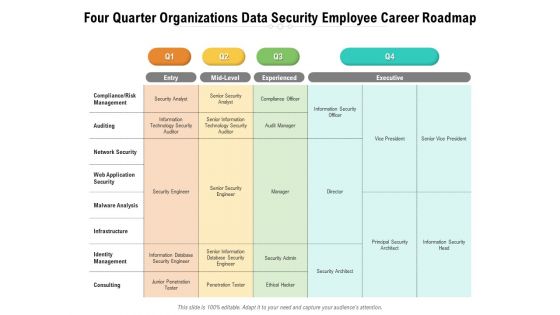
Four Quarter Organizations Data Security Employee Career Roadmap Download
Introducing our four quarter organizations data security employee career roadmap download. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Half Yearly Individual Data Security Career Roadmap Slides
Presenting our innovatively-structured half yearly individual data security career roadmap slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Half Yearly Organizations Data Security Employee Career Roadmap Introduction
Introducing our half yearly organizations data security employee career roadmap introduction. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
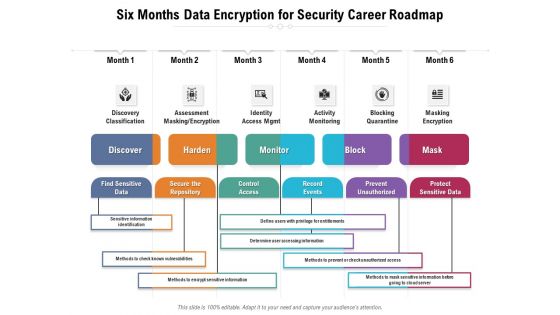
Six Months Data Encryption For Security Career Roadmap Structure
Presenting our innovatively-structured six months data encryption for security career roadmap structure Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Three Months Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured three months data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
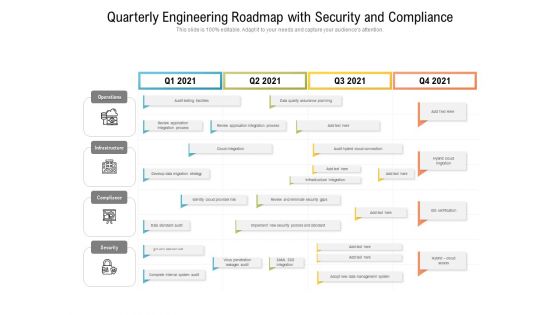
Quarterly Engineering Roadmap With Security And Compliance Template
Presenting our innovatively structured quarterly engineering roadmap with security and compliance template Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Workforce Half Yearly Work Roadmap Operations And Security Ideas
Presenting our innovatively structured workforce half yearly work roadmap operations and security ideas Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Workforce Quarterly Work Roadmap Operations And Security Demonstration
Introducing our workforce quarterly work roadmap operations and security demonstration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Cyber Security Disaster Recuperation Quarterly Roadmap To Eradicate Intrusion Icons
Introducing our cyber security disaster recuperation quarterly roadmap to eradicate intrusion icons. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cloud Computing Security Half Yearly Roadmap With Deployment Plan Guidelines
Presenting our innovatively structured cloud computing security half yearly roadmap with deployment plan guidelines Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
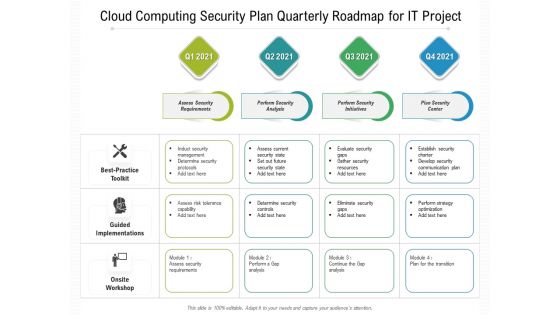
Cloud Computing Security Plan Quarterly Roadmap For IT Project Slides
Presenting our innovatively structured cloud computing security plan quarterly roadmap for it project slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cloud Computing Security Plan Quarterly Roadmap With Key Enablers Information
Introducing our cloud computing security plan quarterly roadmap with key enablers information. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
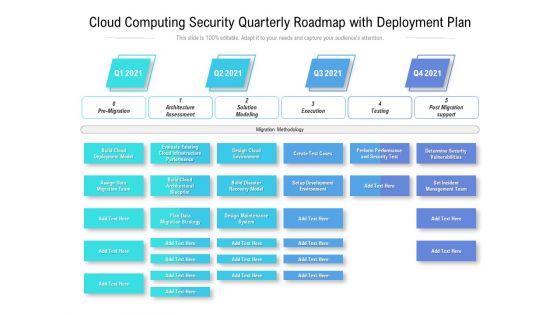
Cloud Computing Security Quarterly Roadmap With Deployment Plan Themes
Introducing our cloud computing security quarterly roadmap with deployment plan themes. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
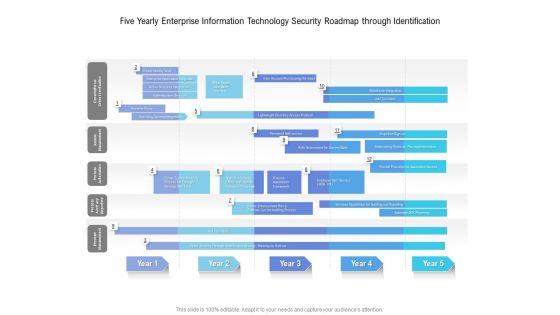
Five Yearly Enterprise Information Technology Security Roadmap Through Identification Sample
Introducing our five yearly enterprise information technology security roadmap through identification sample. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
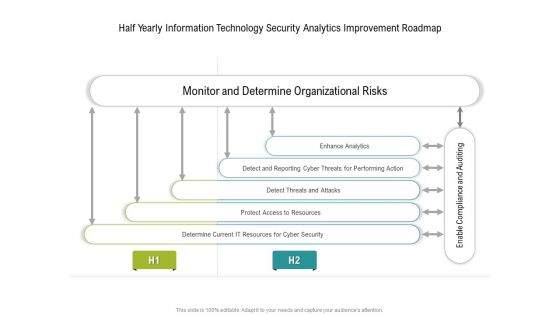
Half Yearly Information Technology Security Analytics Improvement Roadmap Slides
Presenting our innovatively structured half yearly information technology security analytics improvement roadmap slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Half Yearly Information Technology Security Program Maturity Roadmap Microsoft
Introducing our half yearly information technology security program maturity roadmap microsoft. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Quarterly Information Technology Security Analytics Improvement Roadmap Template
Presenting our innovatively structured quarterly information technology security analytics improvement roadmap template Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
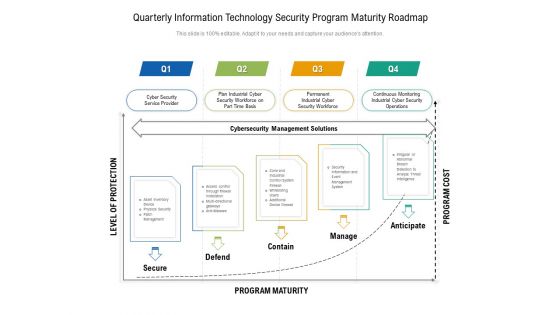
Quarterly Information Technology Security Program Maturity Roadmap Ideas
Introducing our quarterly information technology security program maturity roadmap ideas. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
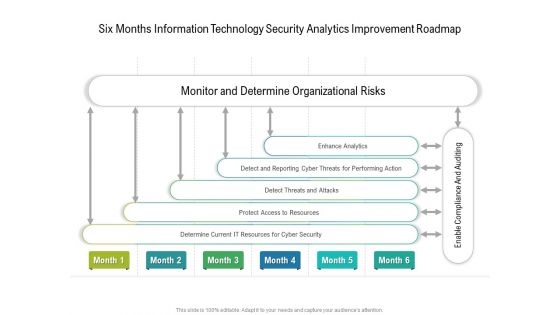
Six Months Information Technology Security Analytics Improvement Roadmap Background
Presenting our innovatively structured six months information technology security analytics improvement roadmap background Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
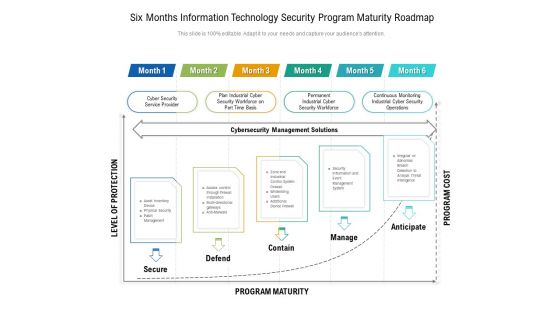
Six Months Information Technology Security Program Maturity Roadmap Infographics
Introducing our six months information technology security program maturity roadmap infographics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
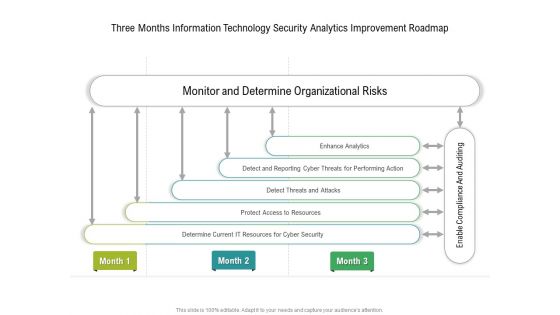
Three Months Information Technology Security Analytics Improvement Roadmap Inspiration
Presenting our innovatively structured three months information technology security analytics improvement roadmap inspiration Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Three Months Information Technology Security Program Maturity Roadmap Pictures
Introducing our three months information technology security program maturity roadmap pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Five Years IT Security Recognition Program Roadmap Introduction
Presenting our innovatively-structured five years it security recognition program roadmap introduction Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
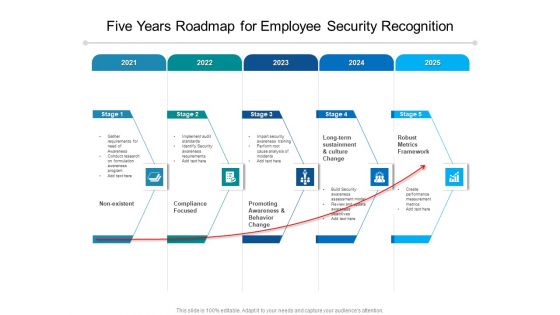
Five Years Roadmap For Employee Security Recognition Clipart
Introducing our five years roadmap for employee security recognition clipart. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
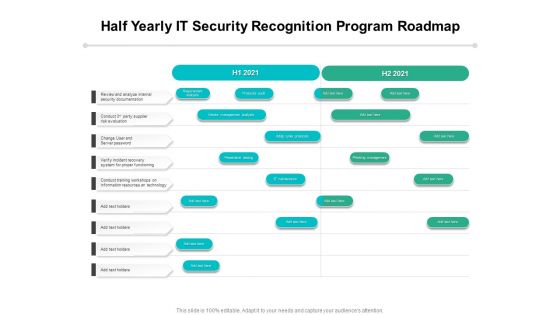
Half Yearly IT Security Recognition Program Roadmap Designs
Presenting our innovatively-structured half yearly it security recognition program roadmap designs Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Half Yearly Roadmap For Employee Security Recognition Formats
Introducing our half yearly roadmap for employee security recognition formats. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
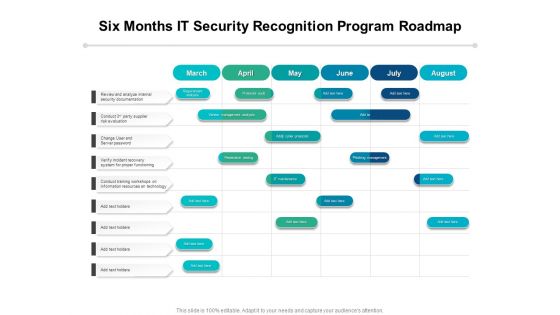
Six Months IT Security Recognition Program Roadmap Diagrams
Presenting our innovatively-structured six months it security recognition program roadmap diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Six Months Roadmap For Employee Security Recognition Inspiration
Introducing our six months roadmap for employee security recognition inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
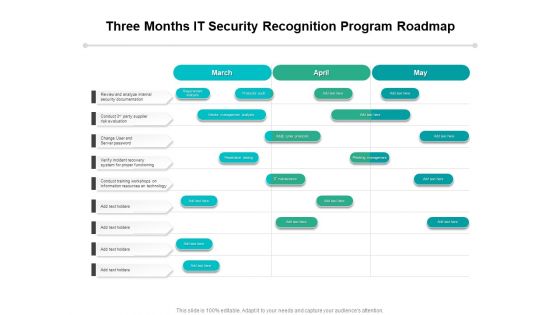
Three Months IT Security Recognition Program Roadmap Topics
Presenting our innovatively-structured three months it security recognition program roadmap topics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
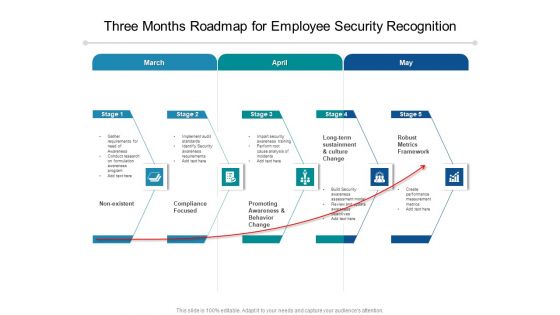
Three Months Roadmap For Employee Security Recognition Themes
Introducing our three months roadmap for employee security recognition themes. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
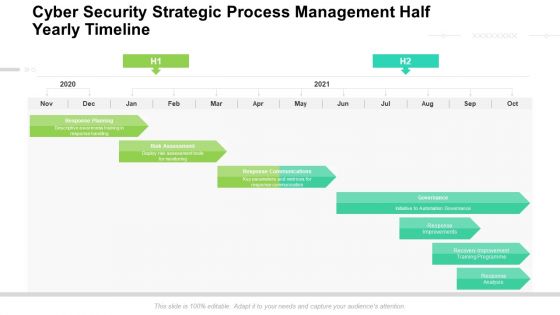
Cyber Security Strategic Process Management Half Yearly Timeline Rules
Presenting our innovatively structured cyber security strategic process management half yearly timeline rules Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Strategic Process Management Six Months Timeline Structure
Introducing our cyber security strategic process management six months timeline structure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
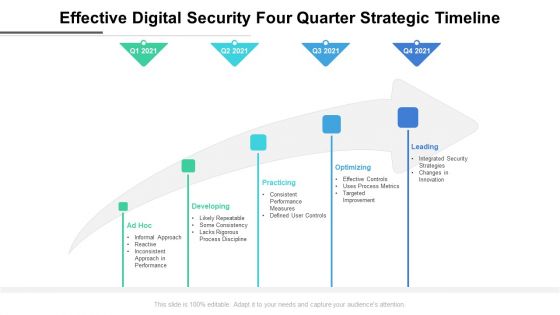
Effective Digital Security Four Quarter Strategic Timeline Elements
Presenting our innovatively structured effective digital security four quarter strategic timeline elements Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
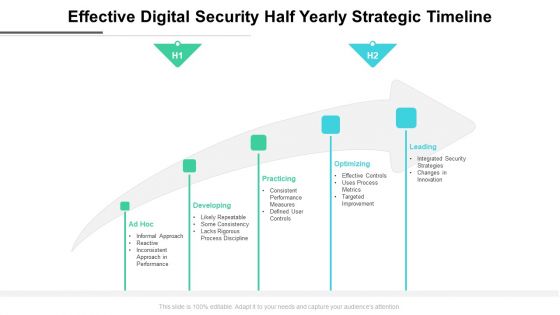
Effective Digital Security Half Yearly Strategic Timeline Download
Introducing our effective digital security half yearly strategic timeline download. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
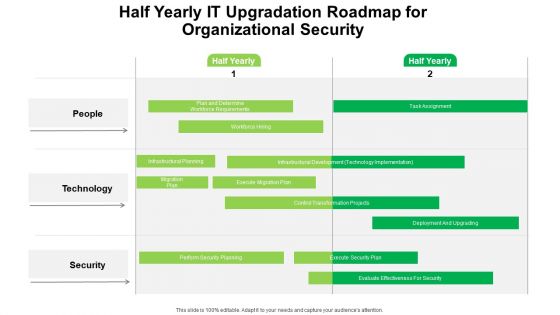
Half Yearly IT Upgradation Roadmap For Organizational Security Portrait
Introducing our half yearly it upgradation roadmap for organizational security portrait. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
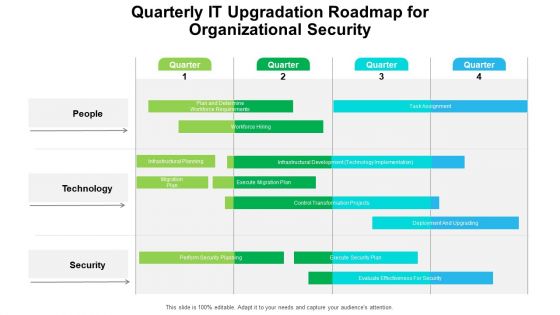
Quarterly IT Upgradation Roadmap For Organizational Security Professional
Presenting our innovatively structured quarterly it upgradation roadmap for organizational security professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

IT Security Protection Measures Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this it security protection measures ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
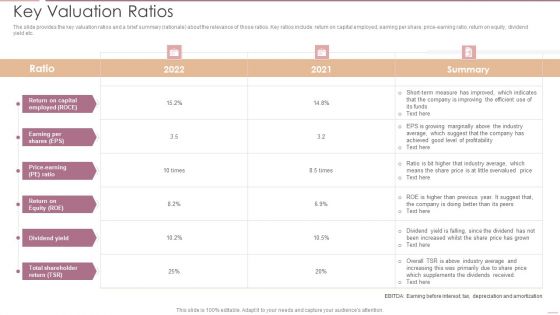
Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF
The slide provides the key valuation ratios and a brief summary rationale about the relevance of those ratios. Key ratios include return on capital employed, earning per share, price-earning ratio, return on equity, dividend yield etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF Use them to share invaluable insights on Measure Improved, Dividends Received, Total Shareholder and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
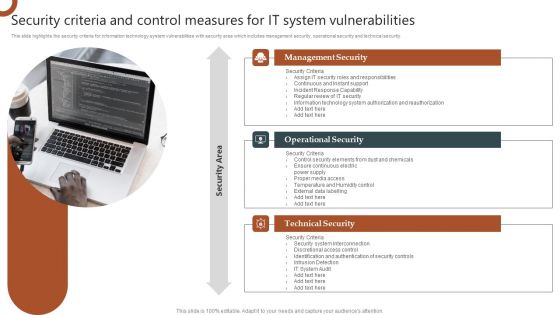
Organizations Risk Management And IT Security Security Criteria And Control Measures For IT System Vulnerabilities Diagrams PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizations Risk Management And IT Security Security Criteria And Control Measures For IT System Vulnerabilities Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using Organizations Risk Management And IT Security Security Criteria And Control Measures For IT System Vulnerabilities Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
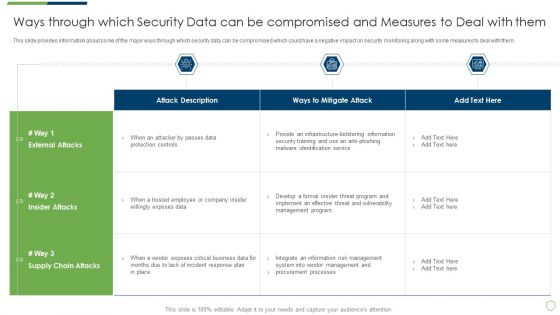
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ways Through Which Security Data Themes PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach ways through which security data themes pdf bundle. Topics like ways through which security data can be compromised and measures to deal with them can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategies To Mitigate Cyber Security Risks Role Of Management In Effective Information Security Governance Ppt Model File Formats PDF
Presenting this set of slides with name strategies to mitigate cyber security risks role of management in effective information security governance ppt model file formats pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
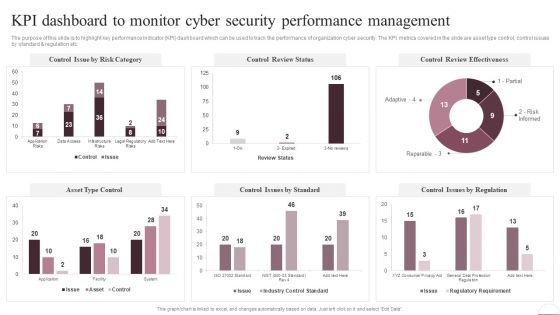
Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard AND regulation etc. This Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
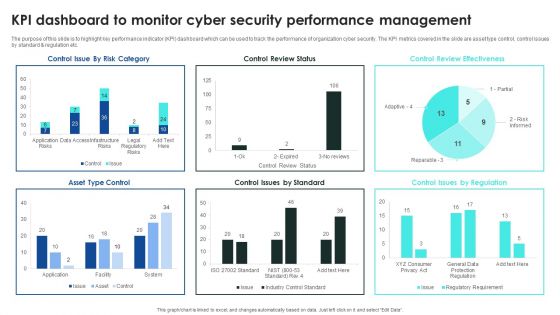
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
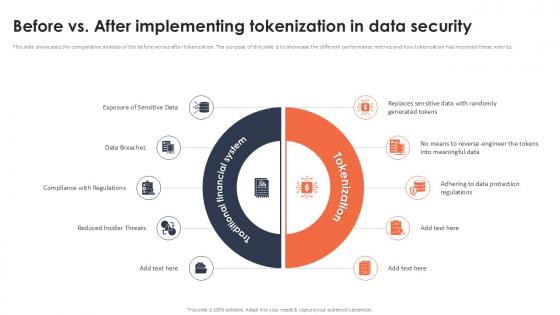
Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example
This slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Want to ace your presentation in front of a live audience Our Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
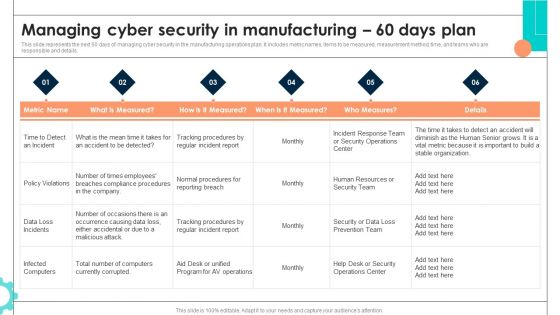
Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Are you searching for a CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF from Slidegeeks today.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF today and make your presentation stand out from the rest.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Get a simple yet stunning designed Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
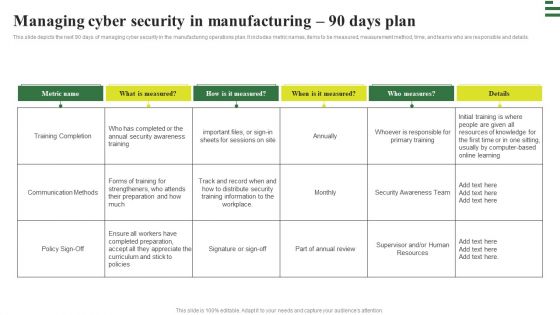
Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

 Home
Home