Metrics Security
Security Strategic Four Quarter Functional Timeline Icons
Presenting our innovatively structured security strategic four quarter functional timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
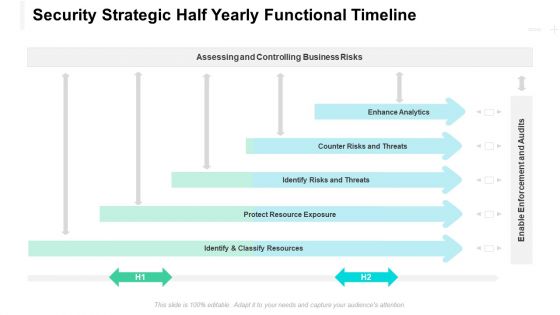
Security Strategic Half Yearly Functional Timeline Designs
Introducing our security strategic half yearly functional timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
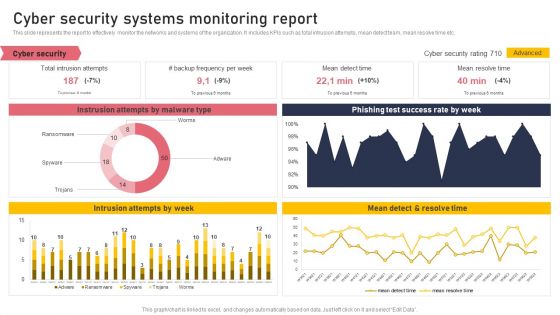
Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

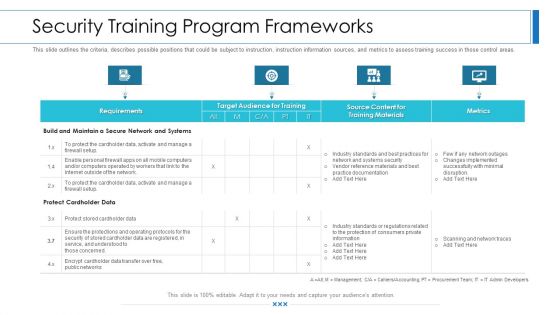
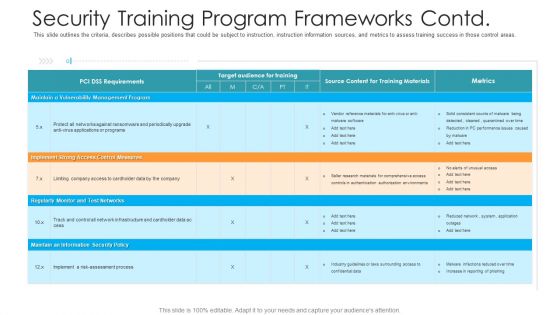
Workforce Security Realization Coaching Plan Security Training Program Frameworks Contd Rules PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks contd rules pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Workforce Security Realization Coaching Plan Security Training Program Frameworks Brochure PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks brochure pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Training Program Frameworks Contd Hacking Prevention Awareness Training For IT Security Background PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative security training program frameworks contd hacking prevention awareness training for it security background pdf bundle. Topics like management, implement, security policy, monitor can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
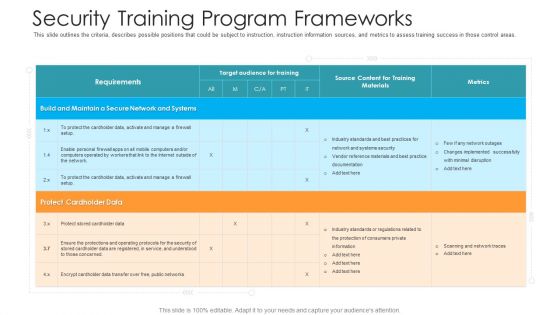
Security Training Program Frameworks Hacking Prevention Awareness Training For IT Security Themes PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this security training program frameworks hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on target, training, maintain, secure, implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
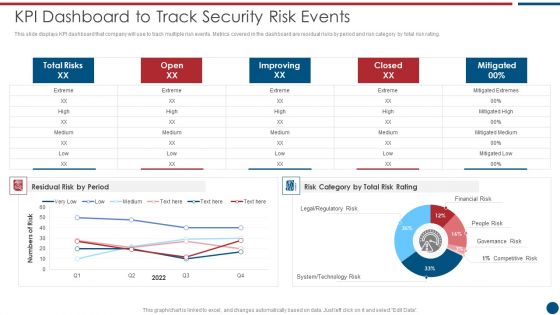
IT Security Risk Management Approach Introduction Kpi Dashboard To Track Security Risk Events Icons PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Kpi Dashboard To Track Security Risk Events Icons PDF. Use them to share invaluable insights on System Technology Risk, Governance Risk, Security Risk Events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Risk Based Procedures To IT Security KPI Dashboard To Track Security Risk Events Designs PDF

Information Security Managing Data Security 30 Days Plan Ppt Summary Slides PDF
This slide depicts how the data security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative information security managing data security 30 days plan ppt summary slides pdf bundle. Topics like risk, procedures, implement, metric can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Training Program Frameworks Ppt Infographics Show PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.This is a security training program frameworks ppt infographics show pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build and maintain a secure network and systems, protect cardholder data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Managing Electronic Information Security 30 Days Plan Ppt Layouts Design Ideas PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this cybersecurity managing electronic information security 30 days plan ppt layouts design ideas pdf. Use them to share invaluable insights on measured, metric, awareness, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF today and make your presentation stand out from the rest.
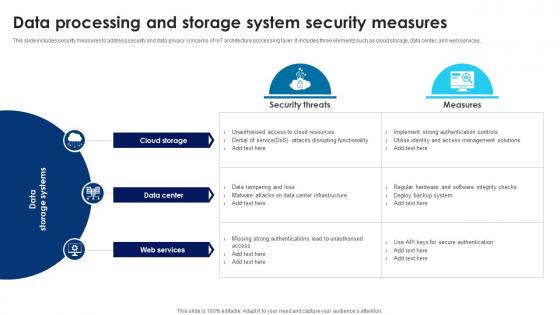
Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V
This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation.
Security Awareness Tracking Kpis Hacking Prevention Awareness Training For IT Security Background PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. Deliver an awe inspiring pitch with this creative security awareness tracking kpis hacking prevention awareness training for it security background pdf bundle. Topics like compliance, security culture, incident reduction can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Mockup PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system mockup pdf. Use them to share invaluable insights on implementation, management plan, security management, security measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Estimated Security Management Plan Information PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks estimated security management plan information pdf Use them to share invaluable insights on security incidents level, security implementation, overall security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
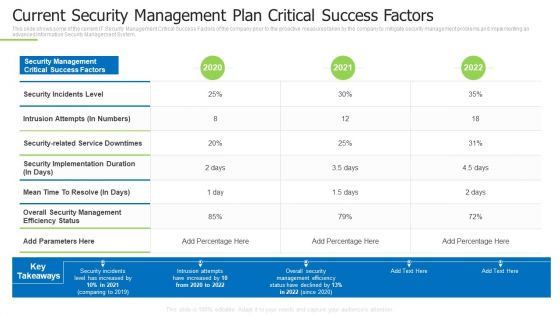
Techniques And Strategies To Reduce Security Management Risks Current Security Management Plan Ideas PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks current security management plan ideas pdf bundle. Topics like intrusion attempts, overall security management, security incidents level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Workforce Security Realization Coaching Plan Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a workforce security realization coaching plan security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
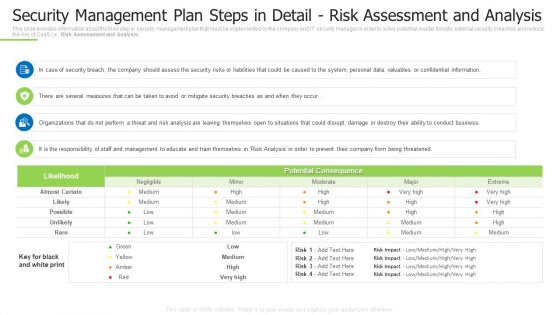
Techniques And Strategies To Reduce Security Management Risks Security Detail Risk Assessment And Analysis Template PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks security detail risk assessment and analysis template pdf Use them to share invaluable insights on security breach, perform a threat, several measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
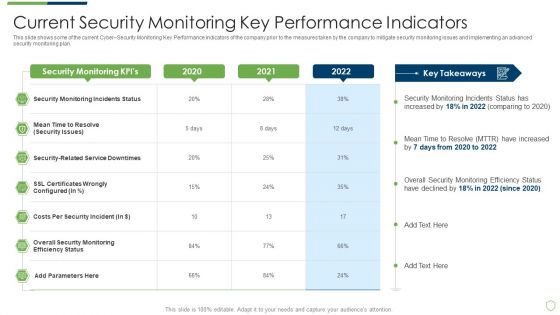
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
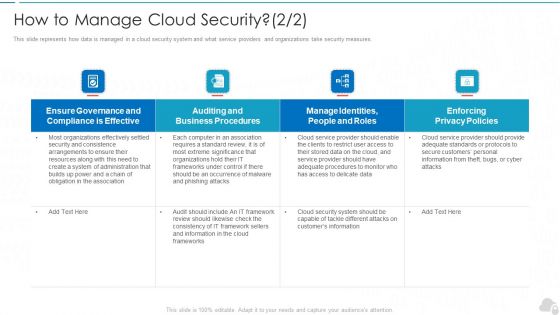
How To Manage Cloud Security Cloud Computing Security IT Ppt Infographic Template Inspiration PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. Deliver an awe inspiring pitch with this creative how to manage cloud security cloud computing security it ppt infographic template inspiration pdf bundle. Topics like effective, privacy policies, business procedures, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
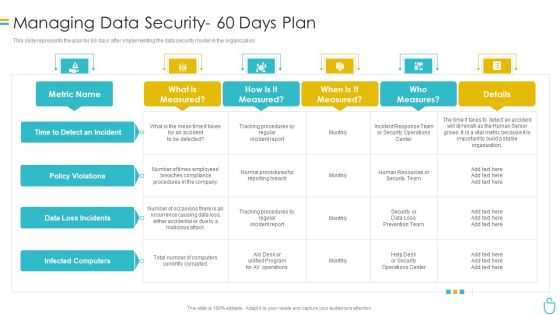
Information Security Managing Data Security 60 Days Plan Ppt Inspiration Slide Download PDF
This slide represents the plan for 60 days after implementing the data security model in the organization. Deliver and pitch your topic in the best possible manner with this information security managing data security 60 days plan ppt inspiration slide download pdf. Use them to share invaluable insights on measured, procedures, team, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
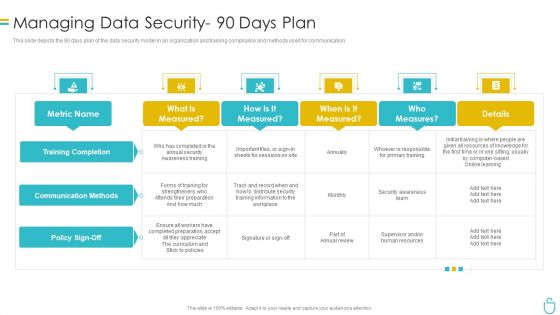
Information Security Managing Data Security 90 Days Plan Ppt Infographic Template Slides PDF
This slide depicts the 90 days plan of the data security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative information security managing data security 90 days plan ppt infographic template slides pdf bundle. Topics like security, measured can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Managing Computer Security 30 Days Plan Designs PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 30 days plan designs pdf bundle. Topics like awareness, measured, risk, security, team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Implementation Framework Role Of Management In Effective Information Security Governance Download PDF
Presenting this set of slides with name cyber security implementation framework role of management in effective information security governance download pdf. The topics discussed in these slides are board directors, senior executives, steering committees, chief information security officer, measuring performance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
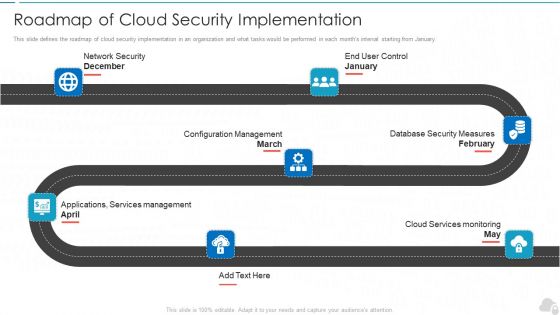
Roadmap Of Cloud Security Implementation Cloud Computing Security IT Ppt Outline Files PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. This is a roadmap of cloud security implementation cloud computing security it ppt outline files pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configuration management, database security measures, cloud services monitoring, applications, services management, network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
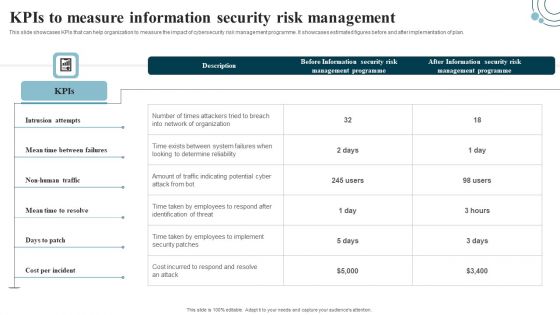
Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF today and make your presentation stand out from the rest.

Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF bundle. Topics like Between Failures, Times Attackers, Management Programme can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
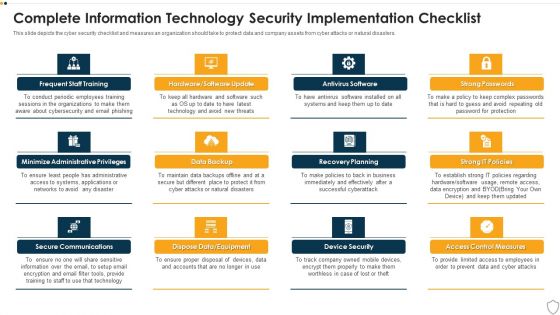
IT Security Complete Information Technology Security Implementation Checklist Ppt Inspiration Templates PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting it security complete information technology security implementation checklist ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like frequent staff training, secure communications, data backup, recovery planning, device security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

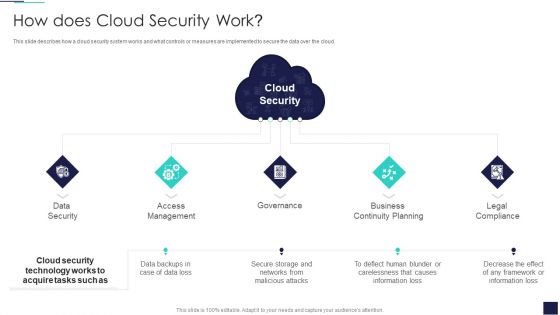
How Does Cloud Security Work Cloud Computing Security IT Ppt Show Graphics Design PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting how does cloud security work cloud computing security it ppt show graphics design pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data security, access management, governance, business continuity planning, legal compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. This is a Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
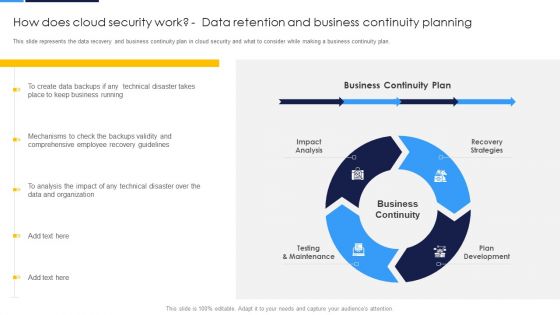
Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.This is a Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Business Continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
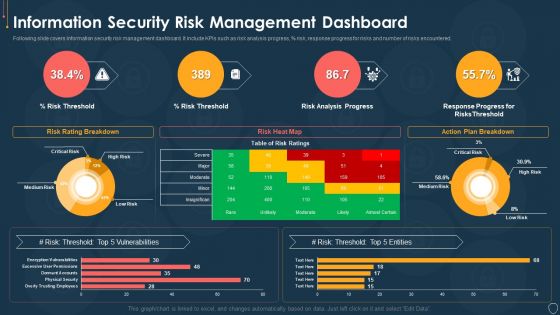
Cyber Security Risk Management Plan Information Security Risk Management Dashboard Sample PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk management dashboard sample pdf bundle. Topics like vulnerabilities, entities, action plan, risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
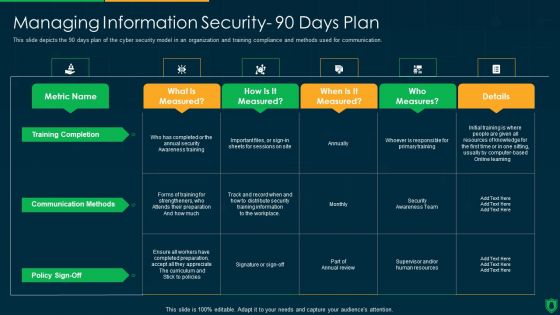
Info Security Managing Information Security 90 Days Plan Ppt PowerPoint Presentation Gallery Maker PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative info security managing information security 90 days plan ppt powerpoint presentation gallery maker pdf bundle. Topics like training completion, communication methods, policy sign off, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
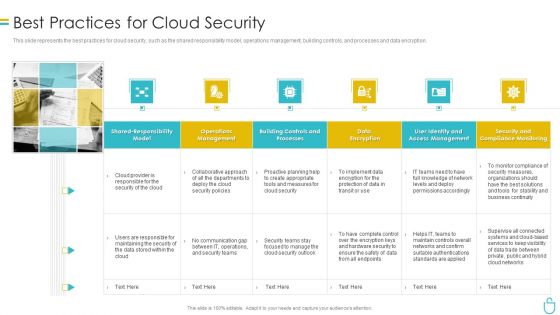
Information Security Best Practices For Cloud Security Ppt Ideas Deck PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting information security best practices for cloud security ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, measures, planning, teams, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
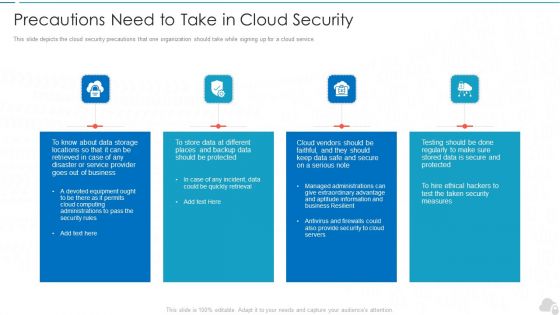
Precautions Need To Take In Cloud Security Cloud Computing Security IT Ppt Inspiration Templates PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service. Presenting precautions need to take in cloud security cloud computing security it ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, service, security measures, computing administrations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Role Of Management In Effective Corporate Security Governance Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an awe inspiring pitch with this creative developing firm security strategy plan role of management in effective corporate security governance slides pdf bundle. Topics like strategic alignment, risk management, measuring performance, value delivery, managing resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
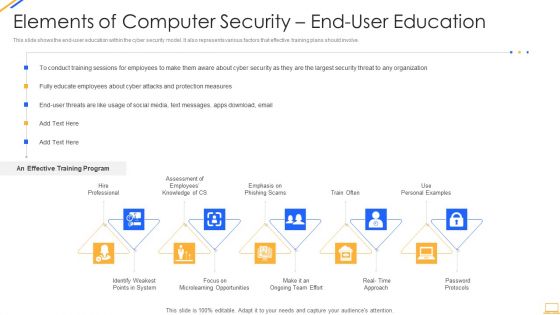
Desktop Security Management Elements Of Computer Security End User Education Background PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a desktop security management elements of computer security end user education background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, opportunities, security, organization, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Measures And Controls In Cloud Security Cloud Computing Security IT Ppt Styles Example File PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. Presenting measures and controls in cloud security cloud computing security it ppt styles example file pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like corrective control, preventive control, deterrent control, detective control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Measures And Controls In Cloud Security Ppt Slides Graphic Images PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. This is a Cloud Information Security Measures And Controls In Cloud Security Ppt Slides Graphic Images PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Detective Control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Measures And Controls In Cloud Security Demonstration PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls.This is a Cloud Security Assessment Measures And Controls In Cloud Security Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Detective Control You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
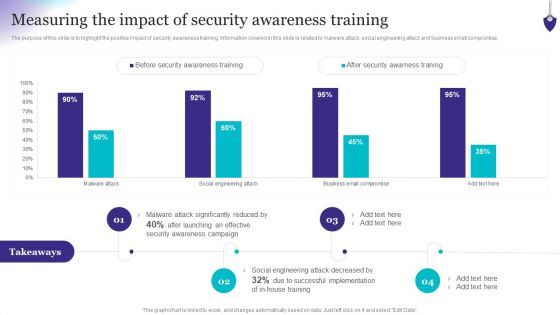
Organizing Security Awareness Measuring The Impact Of Security Awareness Training Background PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Organizing Security Awareness Measuring The Impact Of Security Awareness Training Background PDF from Slidegeeks and deliver a wonderful presentation.
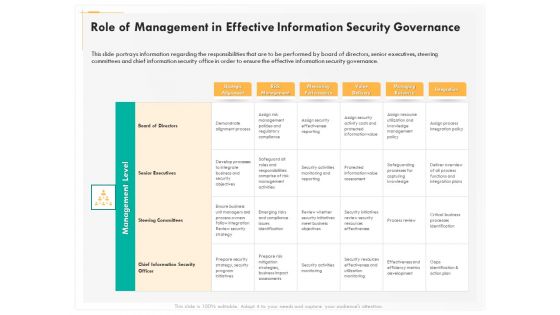
Computer Security Incident Handling Role Of Management In Effective Information Security Governance Portrait PDF
Presenting this set of slides with name computer security incident handling role of management in effective information security governance portrait pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
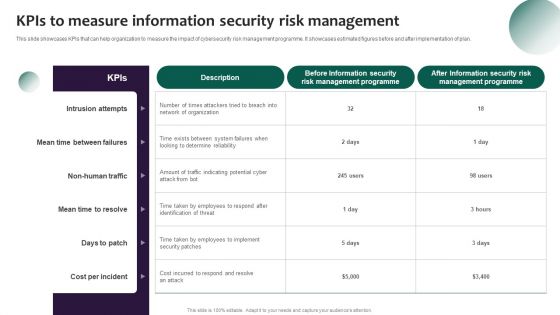
Information Systems Security And Risk Management Plan Kpis To Measure Information Security Risk Management Template PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Want to ace your presentation in front of a live audience Our Information Systems Security And Risk Management Plan Kpis To Measure Information Security Risk Management Template PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF.
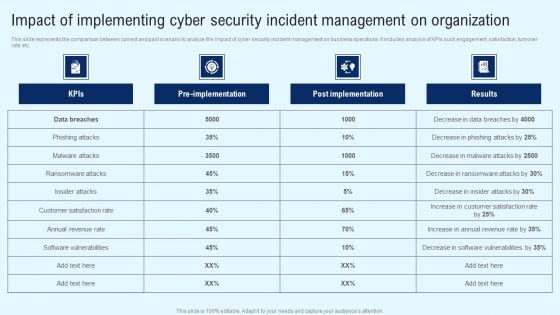
Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
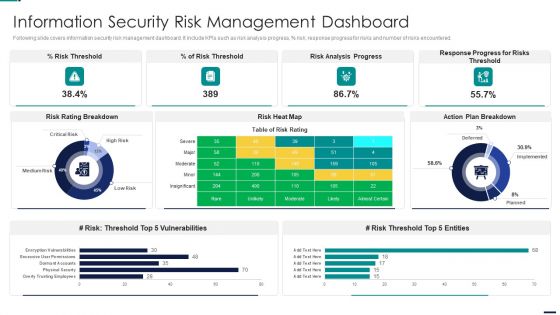
Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF bundle. Topics like Risk Threshold, Risk Analysis Progress, Response Progress For Risks Threshold, Action Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Introducing Information Security Risk Assessment Process Workflow Elements PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a cyber security risk management plan introducing information security risk assessment process workflow elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like characterize system, identify vulnerabilities, identify threats, recommend remediation measures, analyze risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Elements Of Data Security End User Education Ppt Ideas Professional PDF
This slide shows the end user education within the data security model. It also represents various factors that effective training plans should involve. Presenting information security elements of data security end user education ppt ideas professional pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like system, opportunities, employees, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

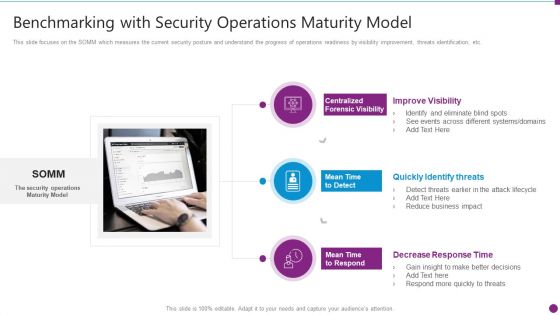
Real Time Assessment Of Security Threats Benchmarking With Security Operations Maturity Model Infographics PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting real time assessment of security threats benchmarking with security operations maturity model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like centralized forensic visibility, mean time to detect, mean time to respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Information And Event Management Strategies For Financial Audit And Compliance Benchmarking With Security Guidelines PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting security information and event management strategies for financial audit and compliance benchmarking with security guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improve visibility, quickly identify threats, decrease response time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Explore a selection of the finest CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cloud Information Security How To Manage Cloud Security Ppt Model Graphics PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. This is a four template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ensure Governance, Compliance Effective, Business Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.This modern and well-arranged Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present like a pro with Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

 Home
Home