Insider Threat

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
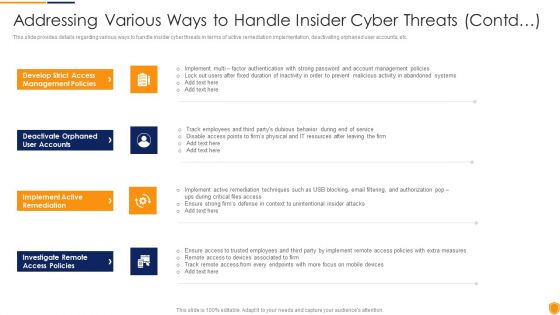
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
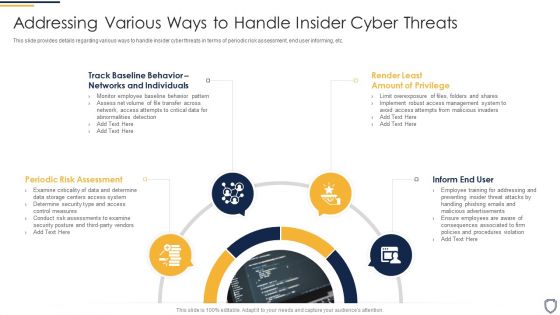
Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Infographics PDF
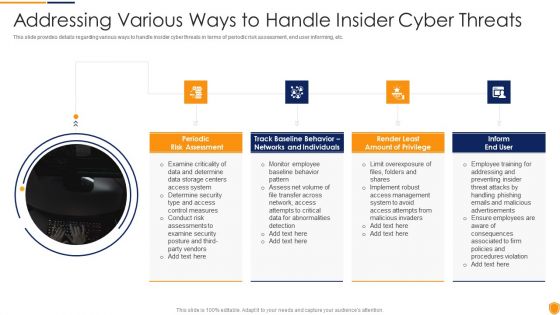
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a corporate security and risk management addressing various ways to handle insider cyber threats infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
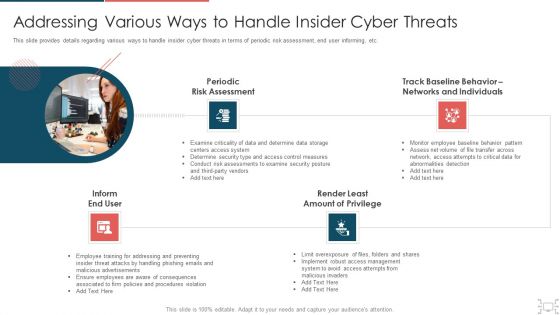
Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Various Ways To Handle Insider Cyber Threats Monitoring Digital Assets Slides Pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This Addressing Various Ways To Handle Insider Cyber Threats Monitoring Digital Assets Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
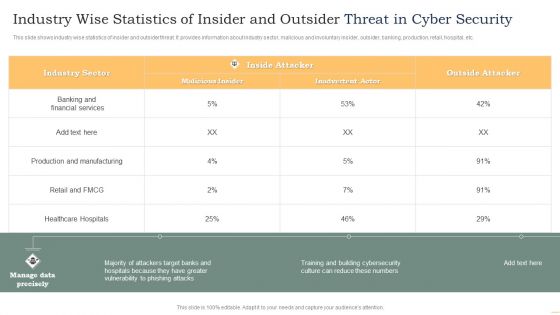
Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
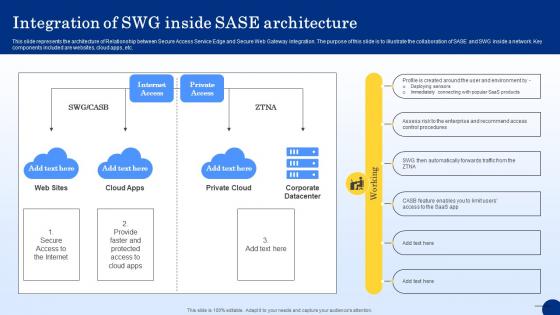
Integration Of SWG Inside SASE Architecture Web Threat Protection System
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of SWG Inside SASE Architecture Web Threat Protection System to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Mitigating Cybersecurity Threats And Vulnerabilities Different Kinds Of Insider Information PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a mitigating cybersecurity threats and vulnerabilities different kinds of insider information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like different kinds of insider digital threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
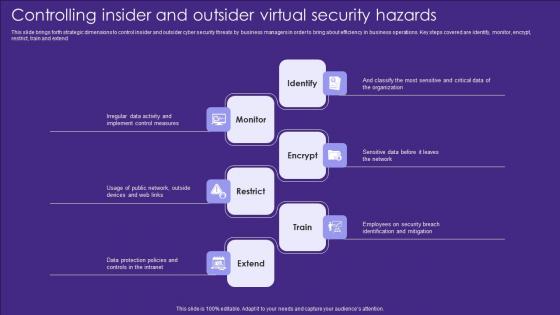
Controlling Insider And Outsider Virtual Security Hazards Designs Pdf
This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend Showcasing this set of slides titled Controlling Insider And Outsider Virtual Security Hazards Designs Pdf. The topics addressed in these templates are Identify, Monitor, Encrypt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Management For Organization Essential Assets Addressing Indicators Associated To Insider Portrait PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting risk management for organization essential assets addressing indicators associated to insider portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like traits, demeanor, goals. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management For Organization Essential Assets Addressing Various Ways To Handle Insider Graphics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a risk management for organization essential assets addressing various ways to handle insider graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, track baseline behavior networks and individuals, render least amount of privilege, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
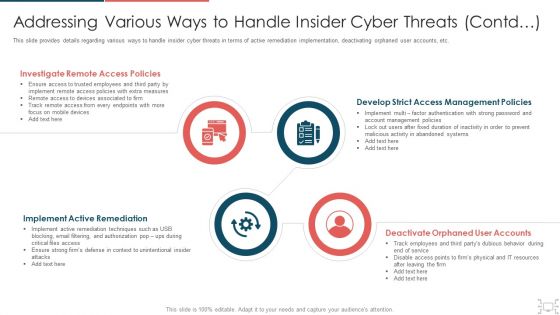
cyber security administration in organization addressing various ways to handle insider cyber active template pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting cyber security administration in organization addressing various ways to handle insider cyber active template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigate, access, policies, remediation, implement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
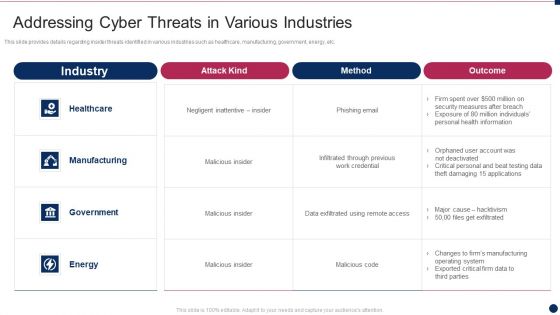
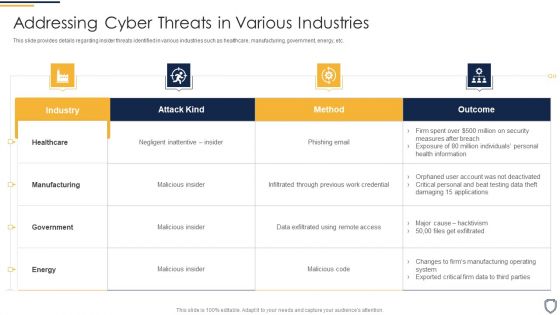
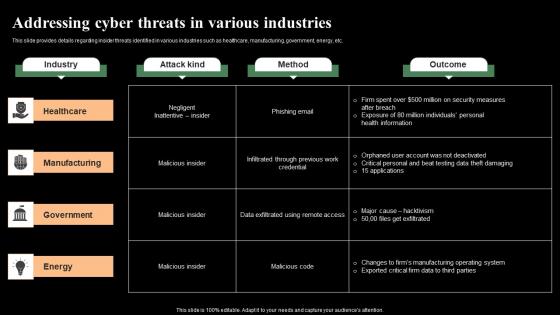
Threat Management At Workplace Addressing Cyber Threats In Various Industries Ideas Pdf
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace addressing cyber threats in various industries ideas pdf. Use them to share invaluable insights on healthcare, manufacturing, energy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
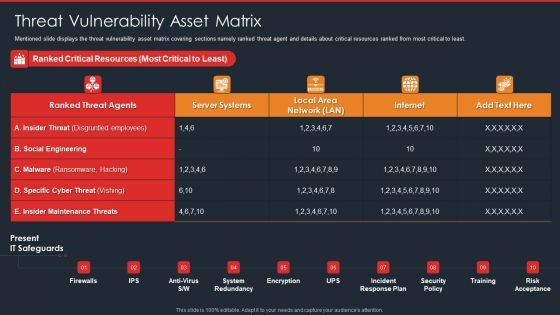
Data Safety Initiatives Threat Vulnerability Asset Matrix Themes PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this data safety initiatives threat vulnerability asset matrix themes pdf. Use them to share invaluable insights on ranked threat agents, insider threat, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Threat Mitigation Methods Information Technology Risks Form Human Threat Source Ideas PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Information Technology Risks Form Human Threat Source Ideas PDF bundle. Topics like Computer Criminal, Industrial Espionage, System Intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Cyber Threats Portrait PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. This is a mitigating cybersecurity threats and vulnerabilities addressing cyber threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like healthcare, manufacturing, government, energy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Risks Form Human Threat Source Summary PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. If you are looking for a format to display your unique thoughts, then the professionally designed Information Technology Risks Form Human Threat Source Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Technology Risks Form Human Threat Source Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
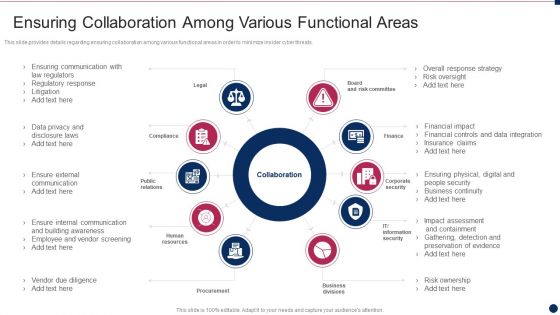
Threat Management At Workplace Ensuring Collaboration Among Various Functional Areas Elements Pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. This is a threat management at workplace ensuring collaboration among various functional areas elements pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vendor due diligence, ensure external communication, financial impact, insurance claims, risk oversight. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Managing Work Relations In Business Common Threats To Organization Ppt Styles Graphics Example PDF
Presenting this set of slides with name managing work relations in business common threats to organization ppt styles graphics example pdf. This is a five stage process. The stages in this process are data protection, insider threats, evolving cyber threats, strict compliance regulations, third party. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Comparative Assessment Of Various Background PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities comparative assessment of various background pdf bundle. Topics like social engineering, insider threat, maintenance threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
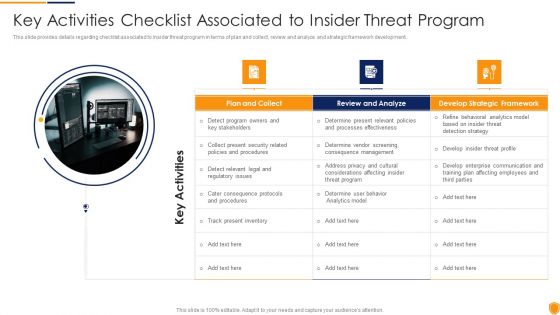
Mitigating Cybersecurity Threats And Vulnerabilities Key Activities Checklist Diagrams PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a mitigating cybersecurity threats and vulnerabilities key activities checklist diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collect, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cyber Security Administration In Organization Addressing Cyber Threats In Various Industries Diagrams PDF
s details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver an awe inspiring pitch with this creative cyber security administration in organization addressing cyber threats in various industries diagrams pdf bundle. Topics like addressing cyber threats in various industries can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
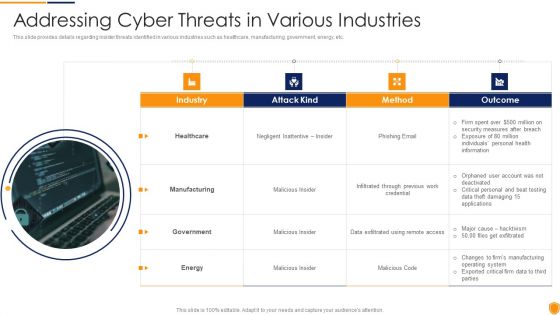
Corporate Security And Risk Management Addressing Cyber Threats In Various Industries Brochure PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management addressing cyber threats in various industries brochure pdf. Use them to share invaluable insights on healthcare, manufacturing, government, energy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Addressing Cyber Threats In Various Industries Monitoring Digital Assets Designs Pdf
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Slidegeeks has constructed Addressing Cyber Threats In Various Industries Monitoring Digital Assets Designs Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Risk Management For Organization Essential Assets Addressing Cyber Threats In Various Industries Structure PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. This is a risk management for organization essential assets addressing cyber threats in various industries structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like healthcare, manufacturing, government, energy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present like a pro with Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Value Based Data Threats Management Model Ppt Layouts Clipart Images PDF
This slide covers value-based data risk management model to balance risk with innovation, profits, and talent. It includes management of data risk such as data exfiltration, insider threat, compliance violation based on its impact on the organization. Presenting Value Based Data Threats Management Model Ppt Layouts Clipart Images PDF to dispense important information. This template comprises TWO stages. It also presents valuable insights into the topics including Profits Talent Innovation, Risk, Value Based, Data Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Stuck Inside Maze PowerPoint Templates Download
Stuck inside Maze PowerPoint templates Download-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! These PowerPoint presentation slides can be used to represent themes relating to -3d, abstract, background, business, challenge, choice, complicated, concept, confusing, confusion, decision, design, difficult, direction, discovery, entrance, exit, find, game, graphic, idea, illustration, labyrinth, lost, mystery, object, path, pattern, problem, puzzle, search, solution, solve, success, symbol, way-Stuck inside Maze PowerPoint templates Download

Men Running Inside The Gears PowerPoint Templates
This power point template has been designed with graphic of gears and 3d men. This 3d diagram contains the concept of problem solving techniques. Prescribe the process with this slide.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Various Ways Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a mitigating cybersecurity threats and vulnerabilities addressing various ways template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, networks and individuals, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
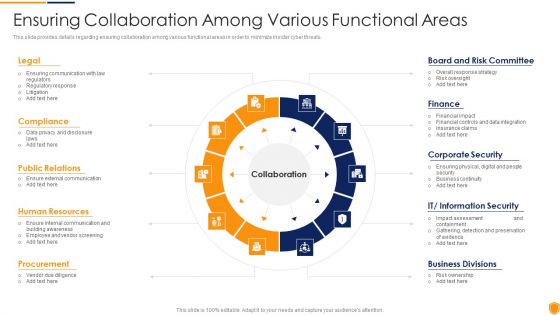
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Collaboration Among Elements PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting mitigating cybersecurity threats and vulnerabilities ensuring collaboration among elements pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like compliance, public relations, human resources, procurement, board and risk committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
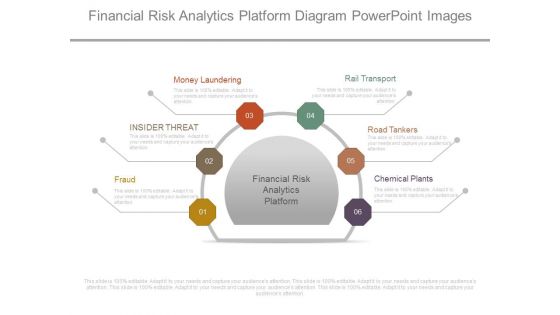
Financial Risk Analytics Platform Diagram Powerpoint Images
This is a financial risk analytics platform diagram powerpoint images. This is a six stage process. The stages in this process are money laundering, insider threat, fraud, rail transport, road tankers, chemical plants, financial risk analytics platform.

Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF
This slide covers annual awareness training program schedule for employees. It includes training for network security, cyber security fundamentals, insider threats, malicious code, etc.Showcasing this set of slides titled Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF. The topics addressed in these templates are Insider Threats, Network Security, Risk Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
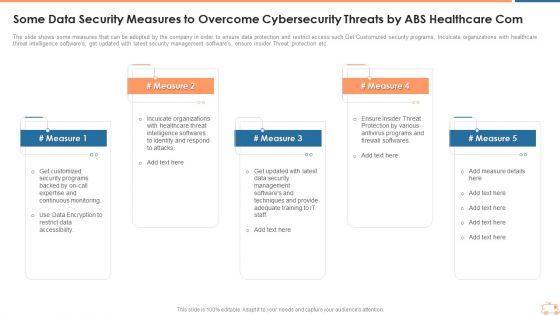
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
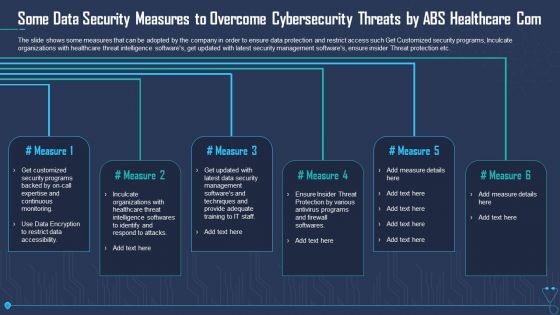
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF bundle. Topics like Safeguard Sensitive, Strong Passwords, Exchange Encrypted can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Addressing Various Ways To Handle Mitigating Cybersecurity Threats And Vulnerabilities Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a addressing various ways to handle mitigating cybersecurity threats and vulnerabilities template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user accounts, implement active remediation, management policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
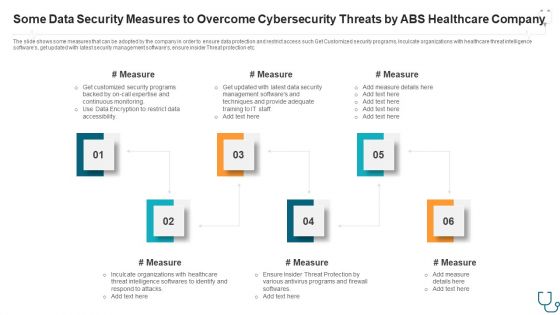
Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Inside Sales Problems Ppt PowerPoint Presentation File Smartart Cpb Pdf
Presenting this set of slides with name inside sales problems ppt powerpoint presentation file smartart cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like inside sales problems to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Puzzle And Icons Inside Magnifying Glass Powerpoint Template
This PowerPoint template has been designed with puzzle and icons inside magnifying glass. You may download this diagram to display puzzle strategy and problems solution. Chart the course you intend to take with this slide
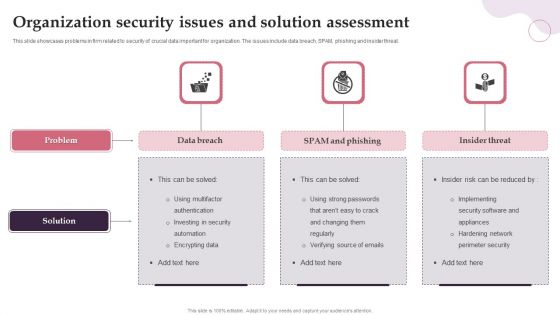
Organization Security Issues And Solution Assessment Ideas PDF
This slide showcases problems in firm related to security of crucial data important for organization. The issues include data breach, SPAM, phishing and insider threat. Persuade your audience using this Organization Security Issues And Solution Assessment Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breach, SPAM And Phishing, Insider Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Saas Cloud Security Challenges For IT Department Ppt PowerPoint Presentation Gallery Design Templates PDF
The following slide highlights some SaaS security challenges faced by IT team to plan mitigation actions. It mainly includes file security, insider threat, privilege access etc. Presenting Major Saas Cloud Security Challenges For It Department Ppt PowerPoint Presentation Gallery Design Templates PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including File Security, Insider Threat, Imposing Minimum, Privilege Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Measures And Ways To Mitigate Security Management Challenges Formats PDF
Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges formats pdf bundle. Topics like potential insider threats, external security breaches, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Risk Management For Organization Essential Assets Key Activities Checklist Associated Mockup PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver and pitch your topic in the best possible manner with this risk management for organization essential assets key activities checklist associated mockup pdf. Use them to share invaluable insights on plan and collect, review and analyze, strategic framework development and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Components To Enhance Processes Types Of Cyber Attackers Professional PDF
This slide represents the types of cyber attackers, including cyber criminals, hacktivists, state sponsored attackers, and insider threats. Insider threats can be occurred from within the organization and can be malicious, accidental or negligent. Present like a pro with Cyber Security Components To Enhance Processes Types Of Cyber Attackers Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Techniques And Strategies To Reduce Security Management Risks Current Security Management Professional PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks current security management professional pdf Use them to share invaluable insights on potential insider threats, external security breaches, centric breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Measures And Ways To Mitigate Security Management Challenges Background PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges background pdf bundle. Topics like potential insider threats, external security breaches, weak links in the supply chain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
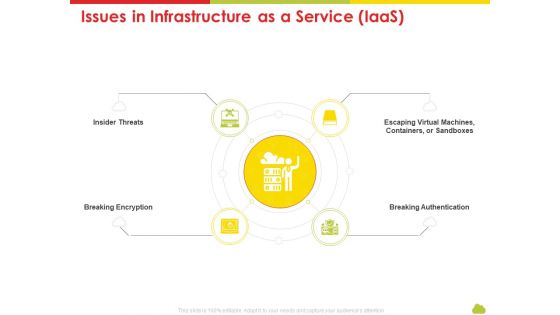
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Issues In Infrastructure As A Service Iaas Ideas PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan issues in infrastructure as a service iaas ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insider threats, breaking encryption, escaping virtual machines, containers, or sandboxes, breaking authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
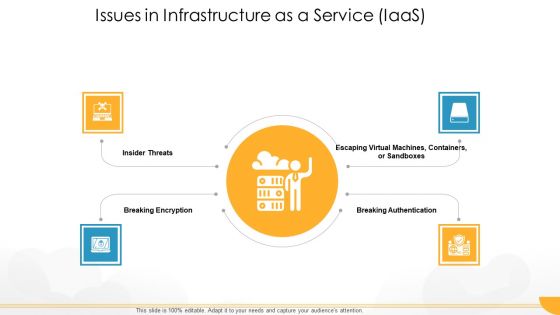
Technology Guide For Serverless Computing Issues In Infrastructure As A Service Iaas Diagrams PDF
This is a technology guide for serverless computing issues in infrastructure as a service iaas diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insider threats, breaking encryption, breaking authentication, virtual machines. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Current Security Management Challenges The Company Is Facing Download PDF
Presenting current security management challenges the company is facing download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like potential insider threats, external security breaches, rise of caas. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Current Security Management Challenges The Company Is Facing Demonstration PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers. Deliver an awe inspiring pitch with this creative current security management challenges the company is facing demonstration pdf bundle. Topics like potential insider threats, external security breaches, employee management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparing Different Types Of Calling Inside Vs Outside Sales PPT PowerPoint Strategy SS V
This slide showcases comparative assessment of different calling methods for generating new leads and converting sales prospects. It showcases comparison on the basis of overview, types of call, stage of sales funnel, rejection risk etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparing Different Types Of Calling Inside Vs Outside Sales PPT PowerPoint Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparing Different Types Of Calling Inside Vs Outside Sales PPT PowerPoint Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Risk Identification And Remediation In Information Technology Template PDF
The purpose of this slide is to outline the IT related risks and various measures to review and control those threats. This includes internal or external threats, system failure, IT policy, and performance. Persuade your audience using this Risk Identification And Remediation In Information Technology Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Insider Threats, General Threats, Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home