Insider Threat

Information Privacy IT Challenges Businesses Face To Protect Consumers Data Privacy Infographics PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. This is a information privacy it challenges businesses face to protect consumers data privacy infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, data breaches, inside threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Ensuring Collaboration Among Various Functional Areas Brochure PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a corporate security and risk management ensuring collaboration among various functional areas brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collet, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
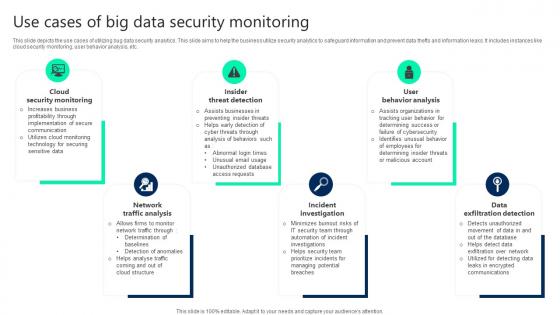
Use Cases Of Big Data Security Monitoring Clipart pdf
This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc. Pitch your topic with ease and precision using this Use Cases Of Big Data Security Monitoring Clipart pdf. This layout presents information on Cloud Security Monitoring, Insider Threat Detection, User Behavior Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Challenges To Medical Industry Cybersecurity Performance Background Pdf
This slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness Showcasing this set of slides titled Key Challenges To Medical Industry Cybersecurity Performance Background Pdf. The topics addressed in these templates are Data Breaches, Service, Cloud Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
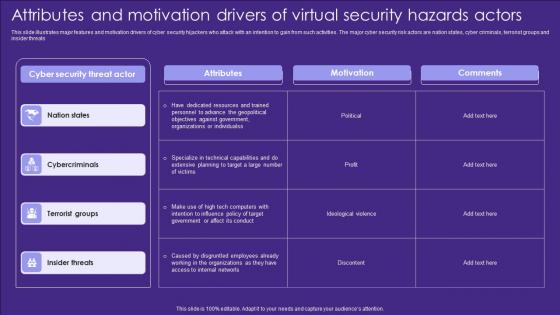
Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf
This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats Showcasing this set of slides titled Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf. The topics addressed in these templates are Attributes, Motivation, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Executing Advance Data Analytics At Workspace How Firm Handle Variou Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. Presenting executing advance data analytics at workspace how firm handle variou elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like employee training, coordination, implement, behavioral. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solutions To Overcome Various It Protection Challenges Summary PDF
This slide shows solutions to various challenges faced by organizations to provide information technology protection. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Persuade your audience using this Solutions To Overcome Various It Protection Challenges Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breaches, Cloud Security, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF
This slide shows solutions to various challenges faced by organizations to provide cloud security. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Showcasing this set of slides titled Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF. The topics addressed in these templates are Solutions To Overcome, Various Security For Cloud, Based Systems Challenges . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
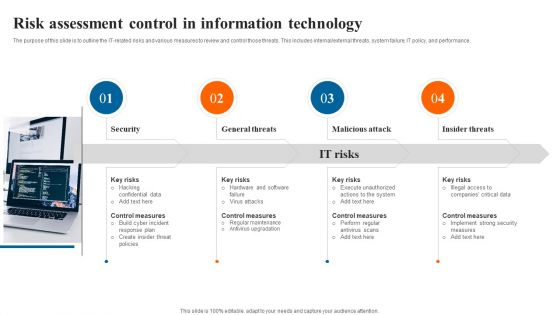
Risk Assessment Control In Information Technology Download PDF
The purpose of this slide is to outline the IT related risks and various measures to review and control those threats. This includes internal or external threats, system failure, IT policy, and performance. Presenting Risk Assessment Control In Information Technology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including General Threats, Malicious Attack, Insider Threats, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
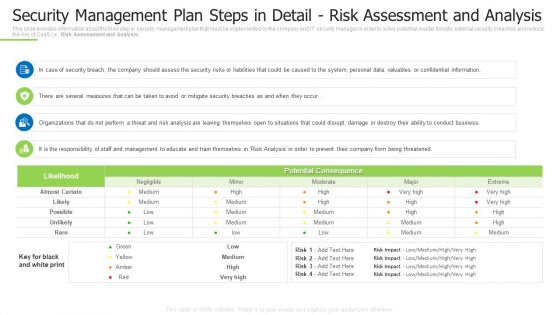
Techniques And Strategies To Reduce Security Management Risks Security Detail Risk Assessment And Analysis Template PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks security detail risk assessment and analysis template pdf Use them to share invaluable insights on security breach, perform a threat, several measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Measures And Ways To Mitigate Clipart PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks measures and ways to mitigate clipart pdf Use them to share invaluable insights on potential insider threats, external security breaches, centric breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Risk Assessment And Analysis Summary PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis summary pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Risk Assessment And Analysis Introduction PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver an awe inspiring pitch with this creative security management plan steps in detail risk assessment and analysis introduction pdf bundle. Topics like information, system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Remote Summary PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management plan steps in detail remote summary pdf bundle. Topics like requirement for additional, remote access control, control security status can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Measures And Ways To Mitigate Security Management Challenges Structure PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.This is a Measures and ways to mitigate security management challenges structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential insider threats, external security breaches, weak links in the supply chain. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
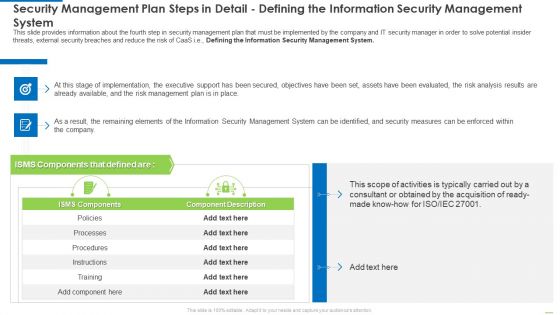
Security Management Plan Steps In Detail Defining The Information Security Management System Diagrams PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system diagrams pdf bundle. Topics like security management plan steps in detail - defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Sample PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system sample pdf bundle. Topics like security management plan steps in detail defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

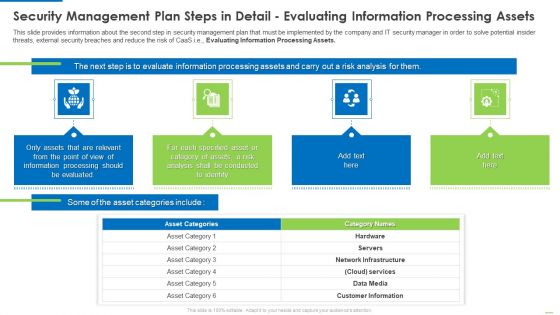
Security Management Plan Steps In Detail Evaluating Information Processing Assets Graphics PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail evaluating information processing assets graphics pdf. Use them to share invaluable insights on security management plan steps in detail evaluating information processing assets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Mockup PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system mockup pdf. Use them to share invaluable insights on implementation, management plan, security management, security measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
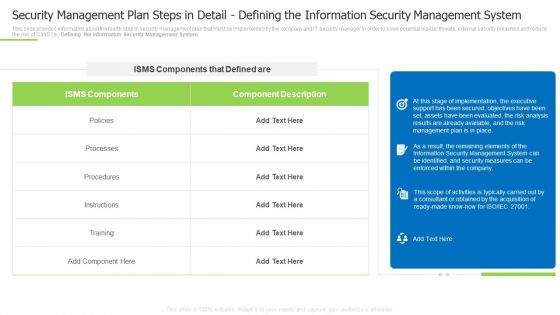
Security Management Plan Steps In Detail Defining The Information Security Management System Summary PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system summary pdf Use them to share invaluable insights on instructions, processes, implementation, the executive and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Security Management Challenges The Company Is Facing Elements PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers.This is a Current security management challenges the company is facing elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential insider threats, external security breaches, employee management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workplace Employee Cyber Safety Awareness Program Ppt Layouts Slide Portrait PDF
This slide covers plan related to workplace security awareness training program. It includes elements such as training providers, target employees and training topics related to BYOD, phishing, social engineering, data handling, privacy, security engineering, insider threat, etc. Pitch your topic with ease and precision using this Workplace Employee Cyber Safety Awareness Program Ppt Layouts Slide Portrait PDF. This layout presents information on Employee, Target, Developer. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
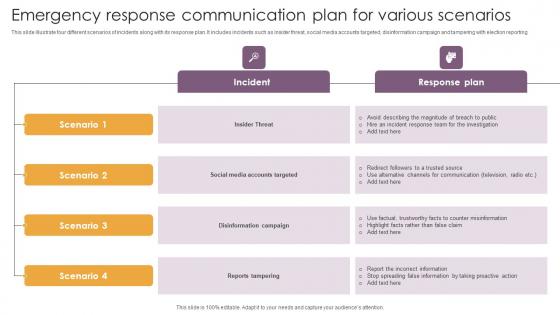
Emergency Response Communication Plan For Various Scenarios Information Pdf
This slide illustrate four different scenarios of incidents along with its response plan. It includes incidents such as insider threat, social media accounts targeted, disinformation campaign and tampering with election reporting Pitch your topic with ease and precision using this Emergency Response Communication Plan For Various Scenarios Information Pdf This layout presents information on Social Media Accounts Targeted, Disinformation Campaign It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
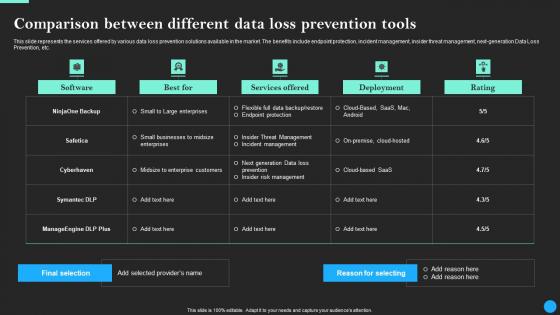
Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf
This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf today and make your presentation stand out from the rest

Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses
This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses today and make your presentation stand out from the rest

Implementing Safety Administration Initiative For Risk Mitigation Way To Overcome Security Demonstration PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. This is a implementing safety administration initiative for risk mitigation way to overcome security demonstration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like goals, information, risk, analysis, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps Portrait PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Adopting Access Controls. This is a techniques and strategies to reduce security management risks security management plan steps portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like suggested coverage, security risk management, estimated security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Detail System Maintenance And Monitoring Mockup PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. This is a techniques and strategies to reduce security management risks security detail system maintenance and monitoring mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perfective maintenance, corrective maintenance, perfective maintenance You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Inspiration PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a techniques and strategies to reduce security management risks security management plan steps in detail inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like effective implementation, consistent with the organizational, represent the business You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

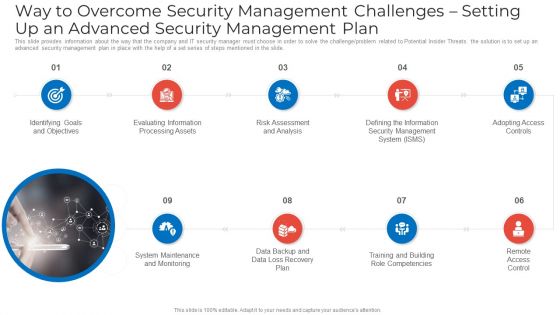
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Introduction PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment and analysis, adopting access controls, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Microsoft PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. Presenting way to overcome security management challenges setting up an advanced security management plan microsoft pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, evaluating information processing assets, risk assessment and analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Rules PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan rules pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Demonstration PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Data Backup and Data Loss Recovery Plan. Presenting Security management plan steps in detail data backup and data loss recovery plan demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security management plan steps in detail - data backup and data loss recovery plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Management Plan Steps In Detail Evaluating Information Processing Assets Summary PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e.Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processing should be evaluated, conducted to identify, category of assets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Summary PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. Presenting security management plan steps in detail system maintenance and monitoring summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like types of system maintenance, installation costs, types of system monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Management Plan Steps In Detail Training And Building Role Competencies Topics PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
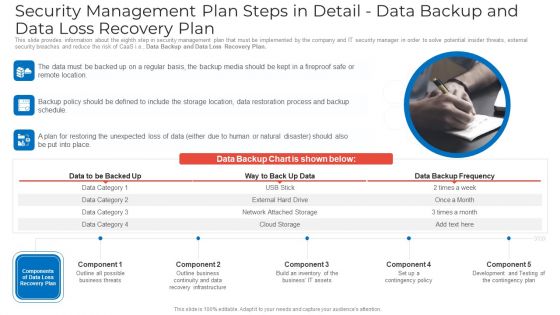
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Ideas PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Data Backup and Data Loss Recovery Plan. This is a security management plan steps in detail data backup and data loss recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail data backup and data loss recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

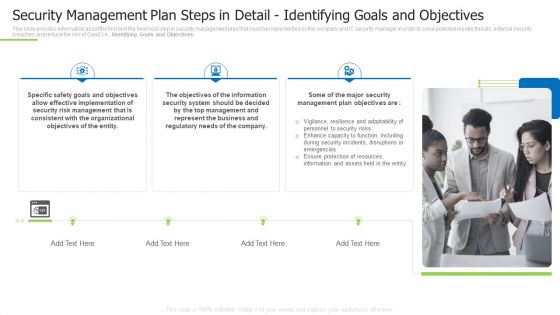
Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

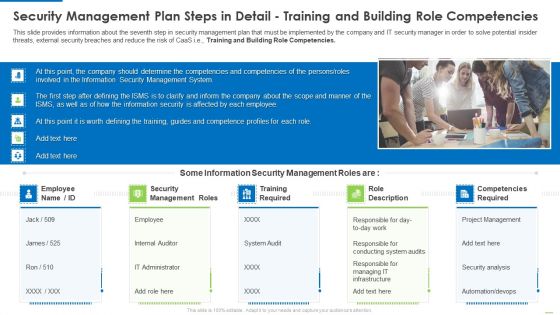
Security Management Plan Steps In Detail Training And Building Role Competencies Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, competencies required. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
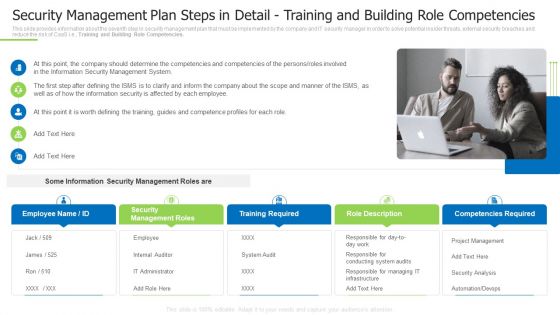
Security Management Plan Steps In Detail Training And Building Role Competencies Slides PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies slides pdf to provide visual cues and insights. Share and navigate important information on five tages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

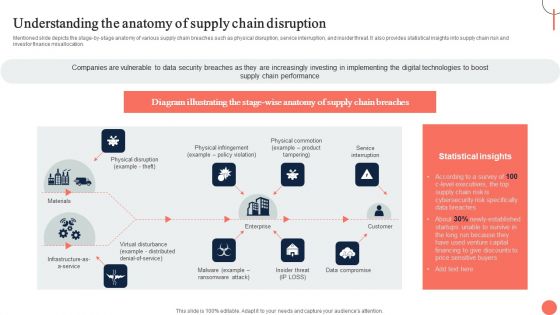
Understanding The Anatomy Of Supply Chain Disruption Stand Out Digital Supply Chain Tactics Enhancing Background PDF
Mentioned slide depicts the stage-by-stage anatomy of various supply chain breaches such as physical disruption, service interruption, and insider threat. It also provides statistical insights into supply chain risk and investor finance misallocation.Slidegeeks has constructed Understanding The Anatomy Of Supply Chain Disruption Stand Out Digital Supply Chain Tactics Enhancing Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Strategies For Dynamic Supply Chain Agility Understanding The Anatomy Of Supply Chain Disruption Elements PDF
Mentioned slide depicts the stage-by-stage anatomy of various supply chain breaches such as physical disruption, service interruption, and insider threat. It also provides statistical insights into supply chain risk and investor finance misallocation. Slidegeeks is here to make your presentations a breeze with Strategies For Dynamic Supply Chain Agility Understanding The Anatomy Of Supply Chain Disruption Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
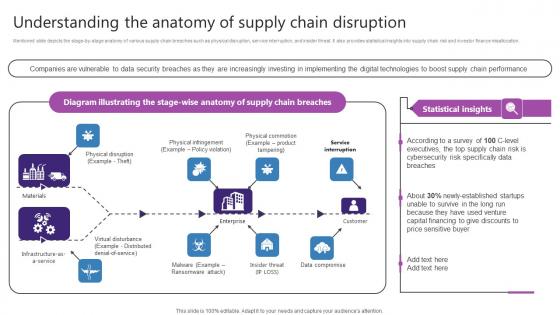
Understanding The Anatomy Of Supply Chain Disruption Strategic Plan For Enhancing Guidelines Pdf
Mentioned slide depicts the stage-by-stage anatomy of various supply chain breaches such as physical disruption, service interruption, and insider threat. It also provides statistical insights into supply chain risk and investor finance misallocation. Welcome to our selection of the Understanding The Anatomy Of Supply Chain Disruption Strategic Plan For Enhancing Guidelines Pdf These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
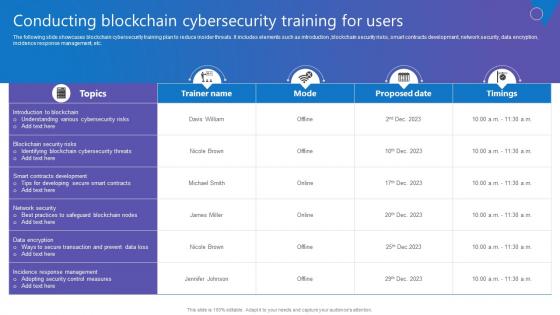
Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc. Create an editable Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Are you searching for a Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF from Slidegeeks today.

Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you searching for a Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF from Slidegeeks today.

Incident Response Techniques Deployement Various Cyber Security Incidents Detected By IT Department Clipart PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Various Cyber Security Incidents Detected By IT Department Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Various Cyber Security Incidents Detected By IT Department Clipart PDF today and make your presentation stand out from the rest.
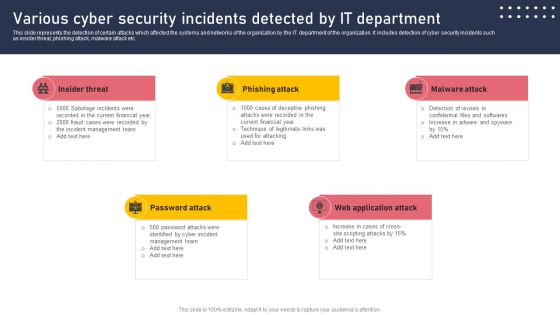
Various Cyber Security Incidents Detected By It Department Sample PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Various Cyber Security Incidents Detected By It Department Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

 Home
Home