Data Security
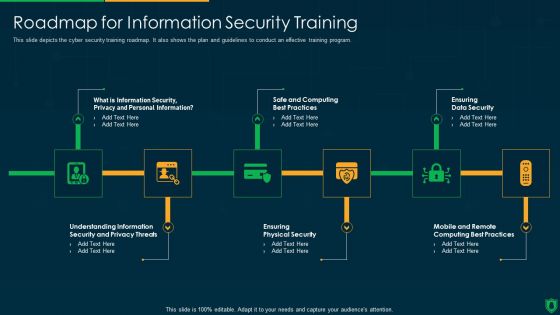
Info Security Roadmap For Information Security Training Ppt PowerPoint Presentation File Inspiration PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a info security roadmap for information security training ppt powerpoint presentation file inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, personal information, safe and computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Elements Of Information Security Disaster Recovery Planning Ppt PowerPoint Presentation Gallery Designs PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a info security elements of information security disaster recovery planning ppt powerpoint presentation gallery designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deploy new plans, quickly and effectively, security incidents, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Find highly impressive Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Cybersecurity Elements Of Electronic Information Security Cloud Security Ppt Outline Background Designs PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a cybersecurity elements of electronic information security cloud security ppt outline background designs pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, risks, resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
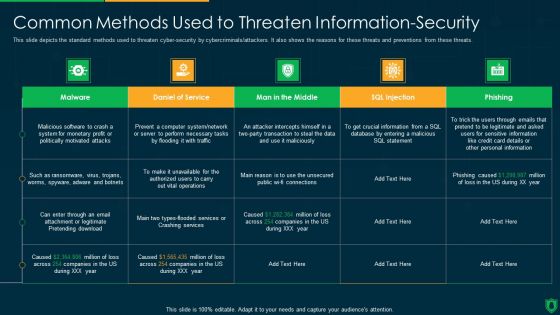
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
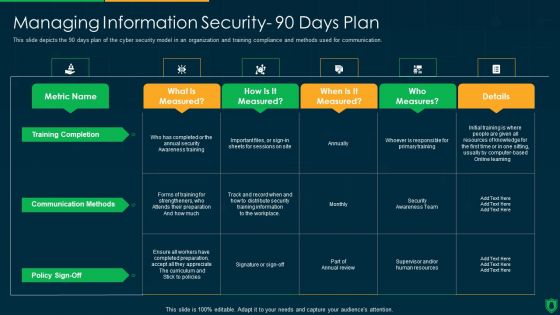
Info Security Managing Information Security 90 Days Plan Ppt PowerPoint Presentation Gallery Maker PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative info security managing information security 90 days plan ppt powerpoint presentation gallery maker pdf bundle. Topics like training completion, communication methods, policy sign off, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Latest Threats In Information Technology Security Ppt Slides Visuals PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting it security latest threats in information technology security ppt slides visuals pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dried malware, romance scams, emoted malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
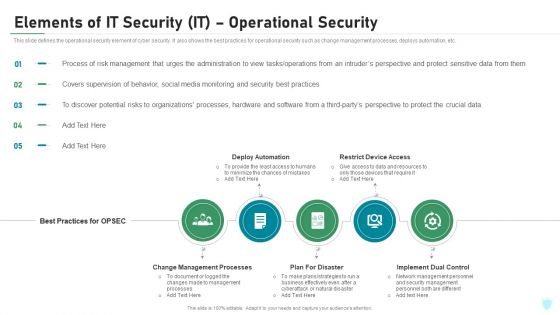
Elements Of IT Security IT Operational Security Ppt Outline Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting elements of it security it operational security ppt outline ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like change management processes, deploy automation, restrict device access, plan for disaster, implement dual control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Awareness Program Timeline Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This is a security awareness program timeline hacking prevention awareness training for it security professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perform, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
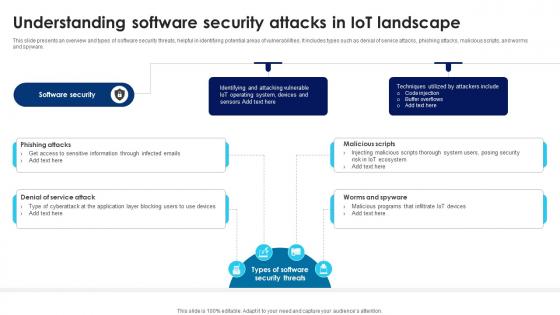
Building Trust With IoT Security Understanding Software Security Attacks In IoT Landscape IoT SS V
This slide presents an overview and types of software security threats, helpful in identifying potential areas of vulnerabilities. It includes types such as denial of service attacks, phishing attacks, malicious scripts, and worms and spyware. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Understanding Software Security Attacks In IoT Landscape IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
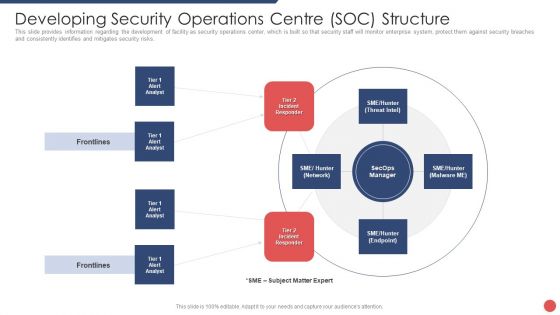
Security Functioning Centre Developing Security Operations Centre SOC Structure Guidelines PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Deliver and pitch your topic in the best possible manner with this security functioning centre developing security operations centre soc structure guidelines pdf. Use them to share invaluable insights on incident responder, analyst, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
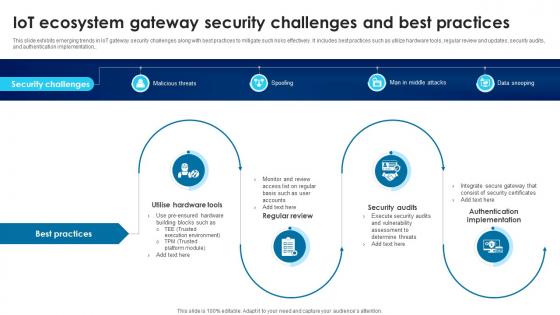
Building Trust With IoT Security IoT Ecosystem Gateway Security Challenges And Best Practices IoT SS V
This slide exhibits emerging trends in IoT gateway security challenges along with best practices to mitigate such risks effectively. It includes best practices such as utilize hardware tools, regular review and updates, security audits, and authentication implementation. Slidegeeks has constructed Building Trust With IoT Security IoT Ecosystem Gateway Security Challenges And Best Practices IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
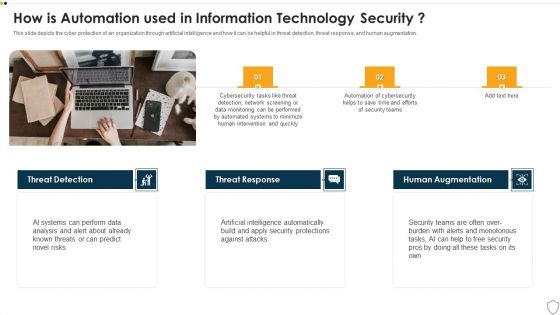
IT Security How Is Automation Used In Information Technology Security Ppt Diagram Lists PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting it security how is automation used in information technology security ppt diagram lists pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Information Technology Security Awareness Training For Staff Ppt Slide PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Presenting it security information technology security awareness training for staff ppt slide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like senior executives, developers, front line staff, it teams, project managers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
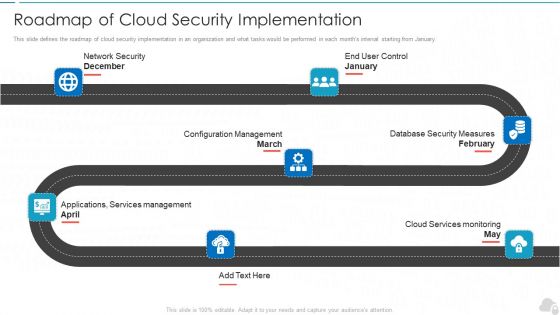
Roadmap Of Cloud Security Implementation Cloud Computing Security IT Ppt Outline Files PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. This is a roadmap of cloud security implementation cloud computing security it ppt outline files pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configuration management, database security measures, cloud services monitoring, applications, services management, network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
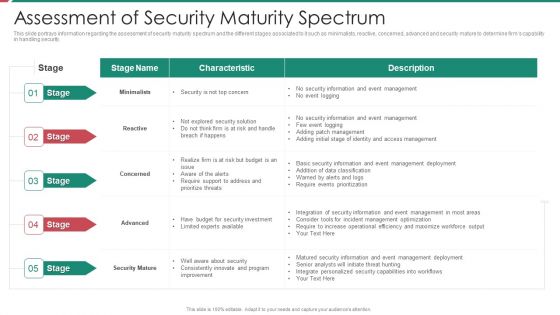
Security And Process Integration Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security and process integration assessment of security maturity spectrum slides pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
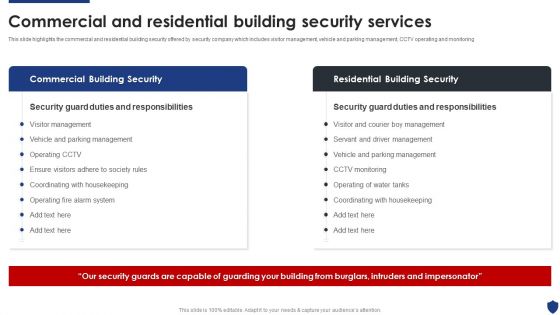
Security Officer Service Company Profile Commercial And Residential Building Security Services Clipart PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Commercial And Residential Building Security Services Clipart PDF bundle. Topics like Commercial Building Security, Residential Building Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
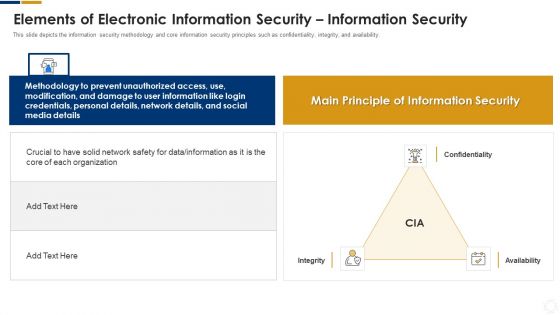
Cybersecurity Elements Of Electronic Information Security Information Security Ppt Pictures Slide PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a cybersecurity elements of electronic information security information security ppt pictures slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, network, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Systems Security And Risk Management Plan Steps For Information Security Risk Management Clipart PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Slidegeeks is here to make your presentations a breeze with Information Systems Security And Risk Management Plan Steps For Information Security Risk Management Clipart PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Security Guards Of Bank Standing Outside For Security Ppt PowerPoint Presentation File Visual Aids PDF
Showcasing this set of slides titled security guards of bank standing outside for security ppt powerpoint presentation file visual aids pdf. The topics addressed in these templates are security guards of bank standing outside for security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
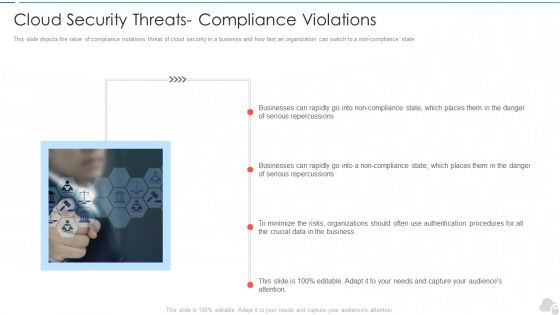
Cloud Security Threats Compliance Violations Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a cloud security threats compliance violations cloud computing security it ppt layouts slide portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like businesses, organizations, serious repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Mobile Device Security Framework Roadmap Mobile Device Security Management Infographics PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver and pitch your topic in the best possible manner with this Implementing Mobile Device Security Framework Roadmap Mobile Device Security Management Infographics PDF. Use them to share invaluable insights on Implement Enterprise, Security Program, Implement Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
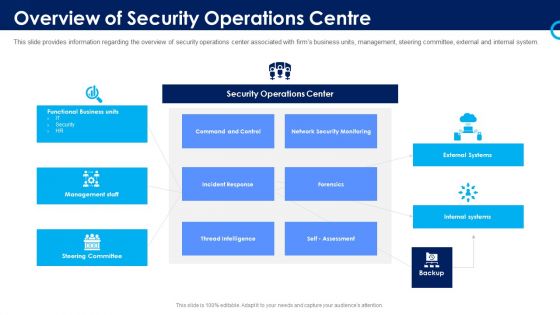
Organizational Security Solutions Overview Of Security Operations Centre Ppt Styles Graphics Pictures PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this organizational security solutions overview of security operations centre ppt styles graphics pictures pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
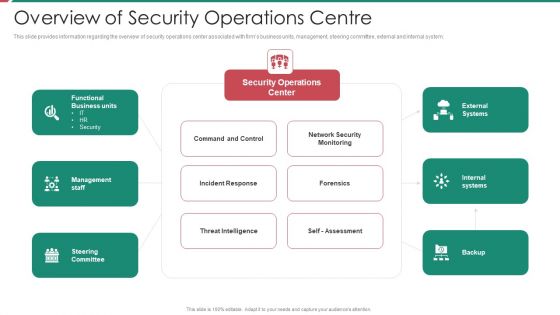
Security And Process Integration Overview Of Security Operations Centre Portrait PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security and process integration overview of security operations centre portrait pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
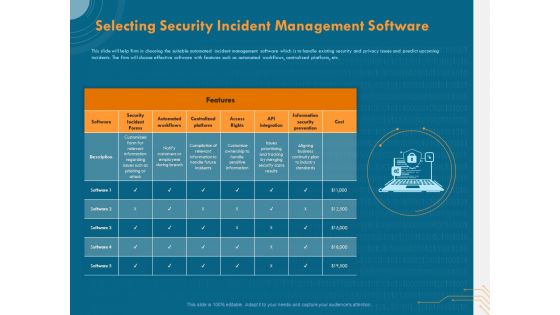
Cyber Security Implementation Framework Selecting Security Incident Management Software Microsoft PDF
Presenting this set of slides with name cyber security implementation framework selecting security incident management software microsoft pdf. The topics discussed in these slides are security incident forms, automated workflows, centralized platform, access rights, api integration, cost, information security prevention. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
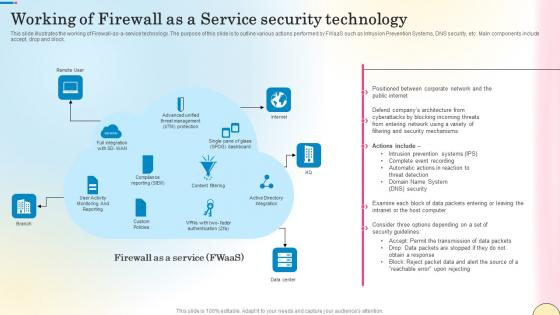
Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf
This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Find highly impressive Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
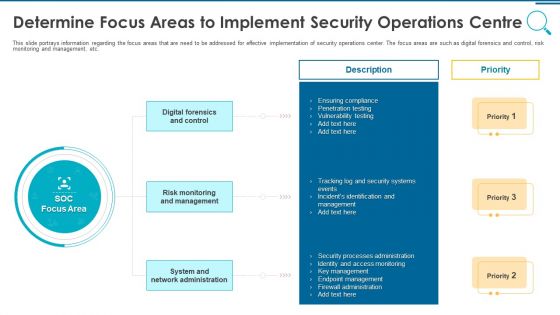
Information And Technology Security Operations Determine Focus Areas To Implement Security Operations Centre Download PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a information and technology security operations determine focus areas to implement security operations centre download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
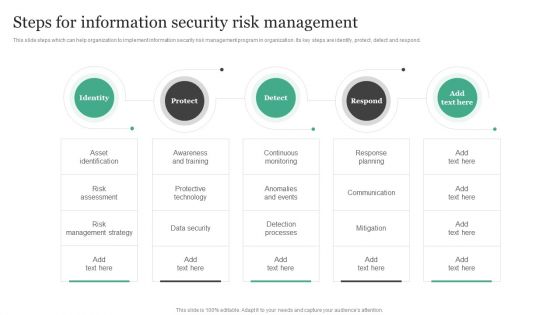
Steps For Information Security Risk Management Information Security Risk Administration Template PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.There are so many reasons you need a Steps For Information Security Risk Management Information Security Risk Administration Template PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Information Security Risk Evaluation Timeline For Information Security Risk Management Training Background PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Timeline For Information Security Risk Management Training Background PDF bundle. Topics like Cybersecurity Awareness, Malware Detection, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Introducing Security At Workplace To Ensure Assets Safety Introduction PDF
This slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Presenting developing firm security strategy plan introducing security at workplace to ensure assets safety introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security policy, organizational strategy, security mission statement, strategic security objectives. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
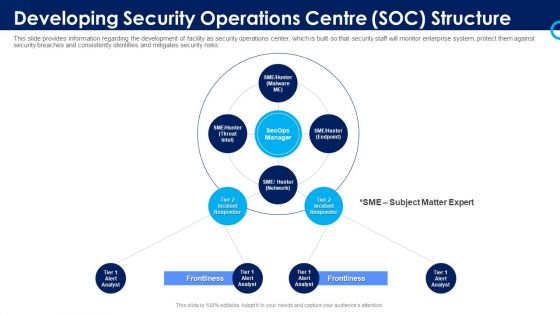
Organizational Security Solutions Developing Security Operations Centre SOC Structure Introduction PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting organizational security solutions developing security operations centre soc structure introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
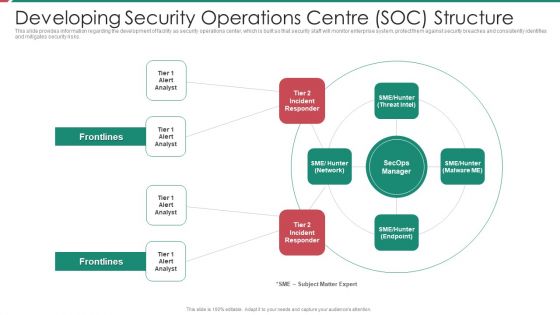
Security And Process Integration Developing Security Operations Centre SOC Structure Inspiration PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting security and process integration developing security operations centre soc structure inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
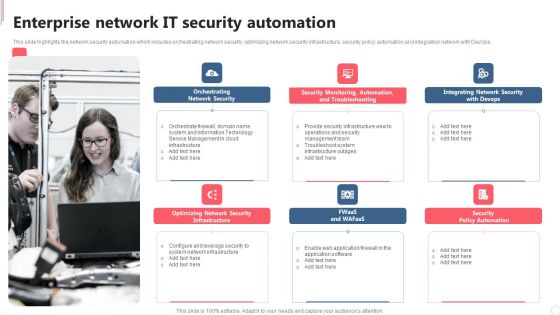
Cyber Security Automation Framework Enterprise Network IT Security Automation Background PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Boost your pitch with our creative Cyber Security Automation Framework Enterprise Network IT Security Automation Background PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Ensuring Checklist For Mobile Security Deployment Mobile Device Security Management Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this Ensuring Checklist For Mobile Security Deployment Mobile Device Security Management Pictures PDF. Use them to share invaluable insights on Remotely Locking, Protection Against, Malicious Codes and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
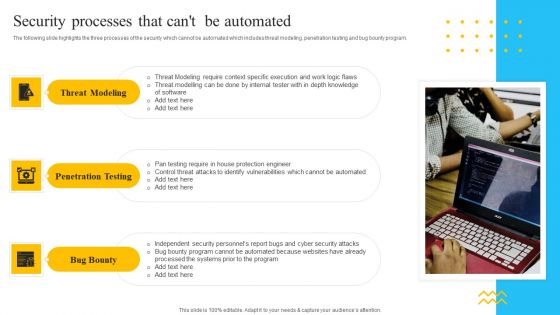
IT Security Automation Tools Integration Security Processes That Cant Be Automated Background PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Presenting IT Security Automation Tools Integration Security Processes That Cant Be Automated Background PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Threat Modeling, Penetration Testing, Bug Bounty. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
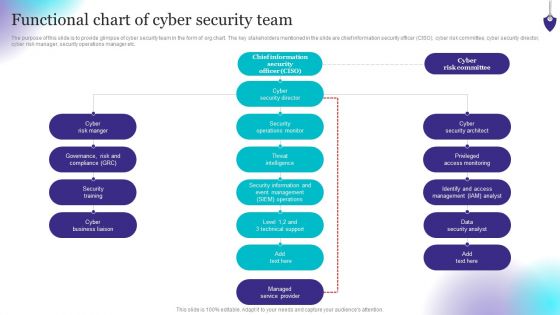
Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF today and make your presentation stand out from the rest.

Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets.This is a Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identifying Internal, Allocating Vulnerability, Assessing Level. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Security Automation To Analyze And Mitigate Cyberthreats Enterprise Network It Security Inspiration PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Security Automation To Analyze And Mitigate Cyberthreats Enterprise Network It Security Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
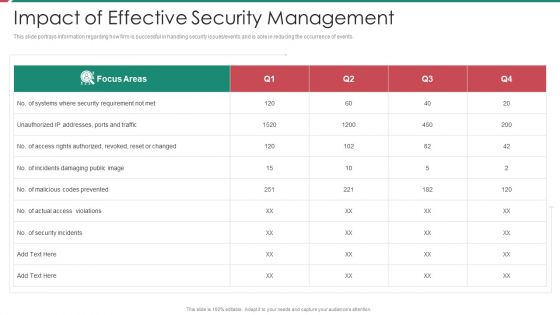
Security And Process Integration Impact Of Effective Security Management Topics PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative security and process integration impact of effective security management topics pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Effective Security Management At Workplace Structure PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan effective security management at workplace structure pdf. Use them to share invaluable insights on effective security management at workplace and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Managing Computer Security 90 Days Plan Professional PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 90 days plan professional pdf bundle. Topics like awareness, security, information, resources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective Mobile Device Security Management Mobile Device Security Management Professional PDF
This slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events associated to mobile device. Deliver an awe inspiring pitch with this creative Effective Mobile Device Security Management Mobile Device Security Management Professional PDF bundle. Topics like Security Requirement, Authorized Revoked, Access Violations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Security Company Strategic Partnerships Summary PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Security Company Strategic Partnerships Summary PDF. Use them to share invaluable insights on Security Application, Technology Partner, Google Assistant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
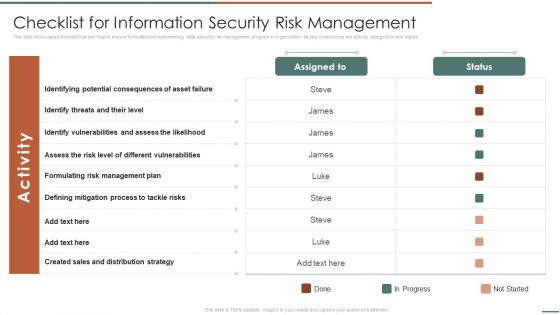
Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF bundle. Topics like Identifying Potential, Defining Mitigation, Created Sales can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF bundle. Topics like Business Disruption, Cost By Consequence, Malware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like, frequent malware attacks and lack of awareness among employees.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF bundle. Topics like Frequent Malware, Phishing Attacks, Ransomware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
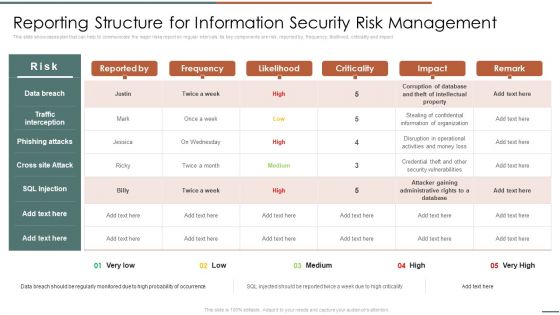
Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF bundle. Topics like Phishing Attacks, Cross Attack, Security Vulnerabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations How Security Concerns Affect Firm In Present Times Rules PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative information and technology security operations how security concerns affect firm in present times rules pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
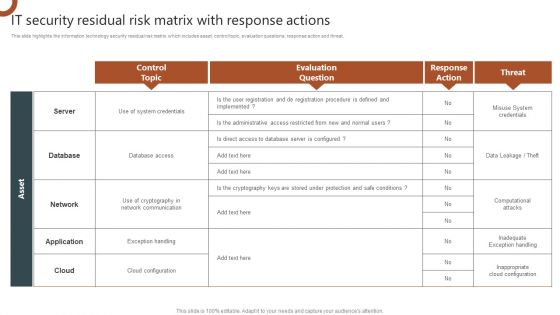
IT Security Residual Risk Matrix With Response Actions Organizations Risk Management And IT Security Professional PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Residual Risk Matrix With Response Actions Organizations Risk Management And IT Security Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
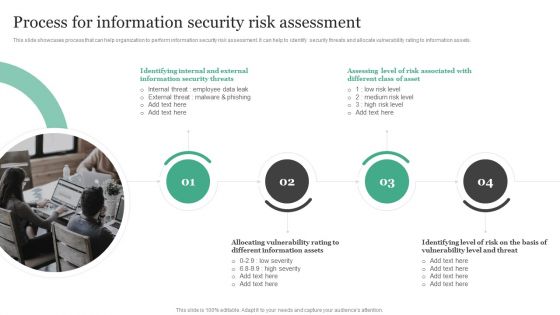
Process For Information Security Risk Assessment Information Security Risk Administration Demonstration PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help to identify security threats and allocate vulnerability rating to information assets.Take your projects to the next level with our ultimate collection of Process For Information Security Risk Assessment Information Security Risk Administration Demonstration PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.
Security And Surveillance Company Profile Our Security Services And Solutions Icons PDF
This slide highlights the security company services which includes CCTV, mobile app software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera.This is a Security And Surveillance Company Profile Our Security Services And Solutions Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Networking Solution, Display Solutions, Occupancy Sensor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Workforce Security Realization Coaching Plan Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a workforce security realization coaching plan security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.This is a Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Rival Organizations, Cybercriminals, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
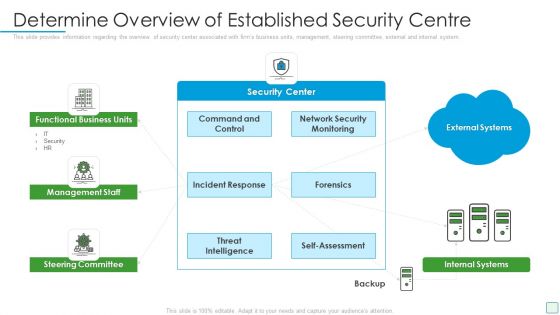
Developing Firm Security Strategy Plan Determine Overview Of Established Security Centre Download PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a developing firm security strategy plan determine overview of established security centre download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like functional business units, management staff, steering committee, internal systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
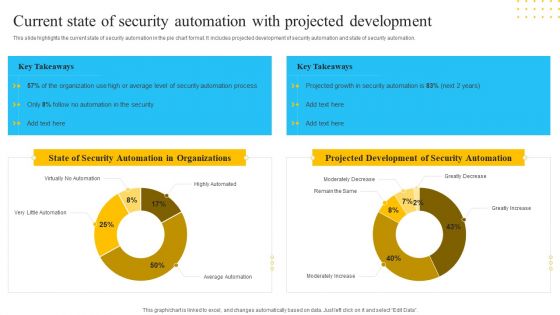
IT Security Automation Tools Integration Current State Of Security Automation With Projected Introduction PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Current State Of Security Automation With Projected Introduction PDF. Use them to share invaluable insights on State Security, Automation Organizations, Projected Development, Security Automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. This is a IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection System, Firewalls, Secure Email Gateways. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Top Advanced Cloud Security Challenges Cont Information PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Top Advanced Cloud Security Challenges Cont Information PDF. Use them to share invaluable insights on Dynamic Environments, Resources Are Provisioned, Access Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
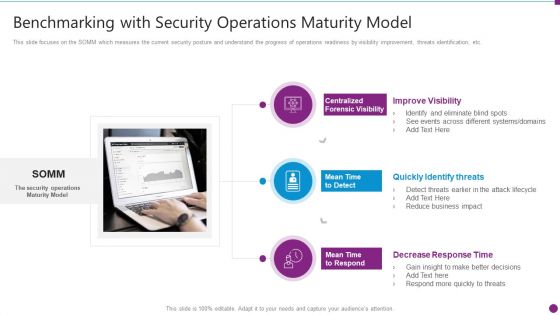
Security Information And Event Management Strategies For Financial Audit And Compliance Benchmarking With Security Guidelines PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting security information and event management strategies for financial audit and compliance benchmarking with security guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improve visibility, quickly identify threats, decrease response time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home