Data Security

Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
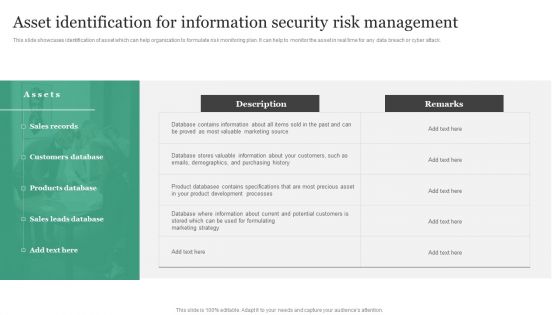
Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Slidegeeks has constructed Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. Take your projects to the next level with our ultimate collection of Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
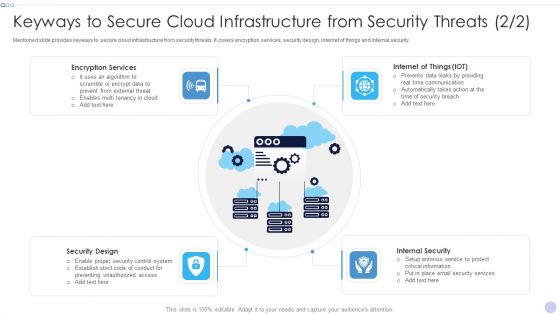
Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
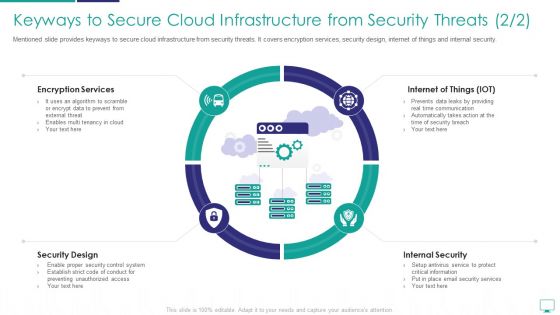
Keyways To Secure Cloud Infrastructure From Security Threats Formats PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a keyways to secure cloud infrastructure from security threats formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encryption services, internet of things, security design. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Elements Of Information Technology Security Information Technology Security Ppt Inspiration Icons PDF
This slide represents the network security element of network security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting elements of information technology security information technology security ppt inspiration icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network security methods, tools, techniques, respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Elements Of Information Technology Security Cloud Security Ppt Icon Gridlines PDF
This slide defines the cloud security element of network security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a elements of information technology security cloud security ppt icon gridlines pdf show pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elements of information technology security cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Defense Security Statistics By Global Security Industry PPT Sample IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates.Defense Security Statistics By Global Security Industry PPT Sample IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Organizational Security Solutions Prerequisites For Effective Secops Implementation Summary PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a organizational security solutions prerequisites for effective secops implementation summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
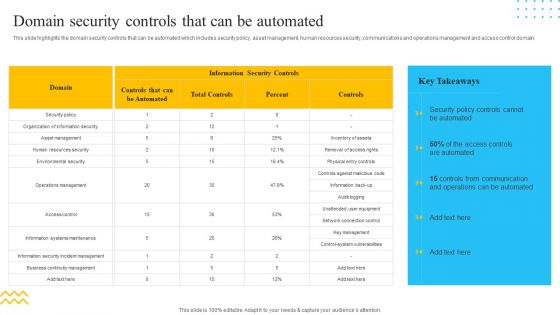
IT Security Automation Tools Integration Domain Security Controls That Can Be Automated Information PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Domain Security Controls That Can Be Automated Information PDF bundle. Topics like Information Security Controls, Controls, Security Policy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
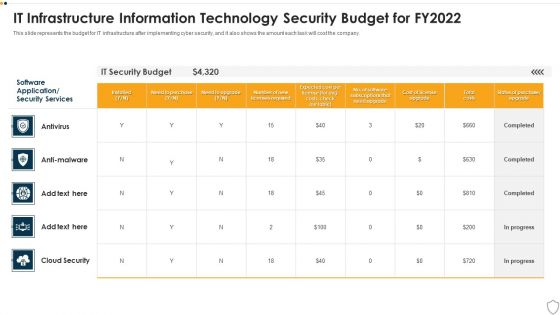
IT Security It Infrastructure Information Technology Security Budget For FY2022 Brochure PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative it security it infrastructure information technology security budget for fy2022 brochure pdf bundle. Topics like it infrastructure information technology security budget for fy2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
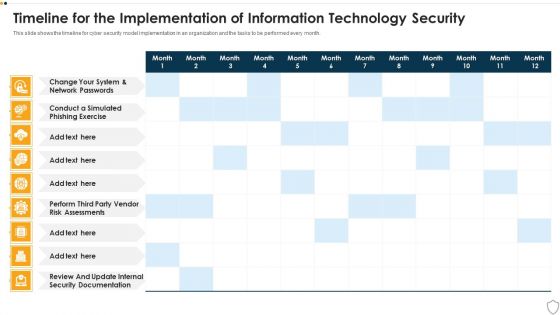
IT Security Timeline For The Implementation Of Information Technology Security Structure PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative it security timeline for the implementation of information technology security structure pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
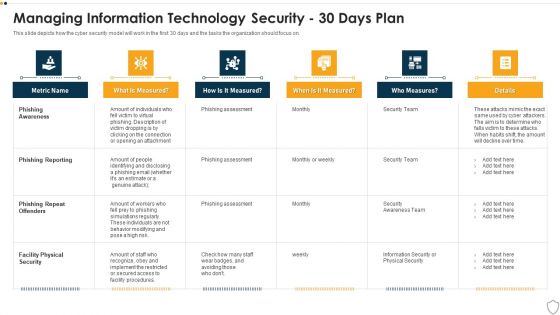
IT Security Managing Information Technology Security 30 Days Plan Themes PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 30 days plan themes pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information And Technology Security Operations Assessment Of Security Maturity Spectrum Template PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative information and technology security operations assessment of security maturity spectrum template pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Key Elements Of Information Security Ppt PowerPoint Presentation Gallery Slide Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. Presenting info security key elements of information security ppt powerpoint presentation gallery slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like application security, end user education, operational security, information security, network security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
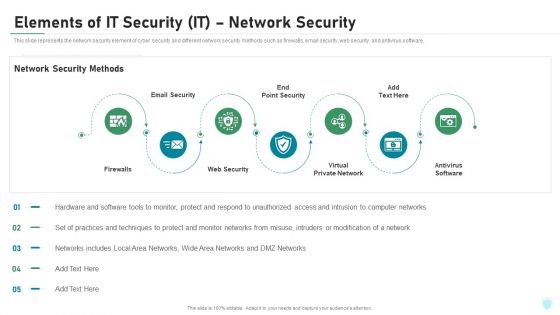
Elements Of IT Security IT Network Security Ppt Pictures Ideas PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a elements of it security it network security ppt pictures ideas pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like firewalls, email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
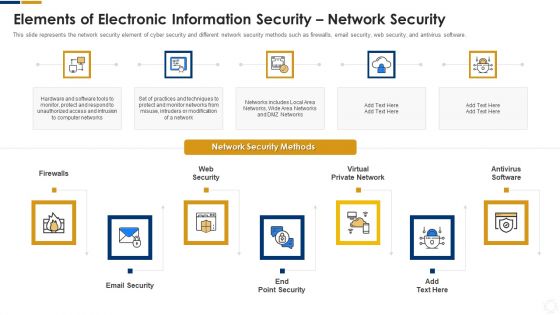
Cybersecurity Elements Of Electronic Information Security Network Security Ppt Ideas Skills PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a cybersecurity elements of electronic information security network security ppt ideas skills pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Overview Of Security Operations Centre Portrait PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this information and technology security operations overview of security operations centre portrait pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
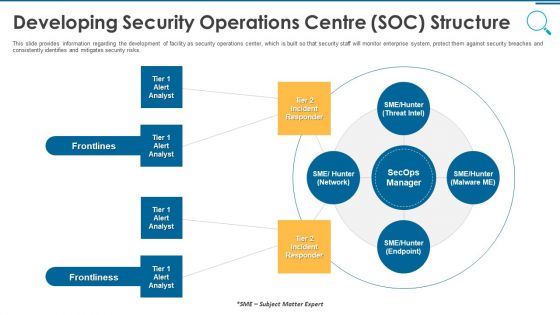
Information And Technology Security Operations Developing Security Operations Centre SOC Structure Slides PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting information and technology security operations developing security operations centre soc structure slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
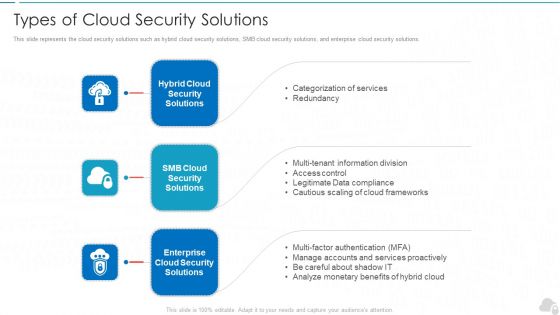
Types Of Cloud Security Solutions Cloud Computing Security IT Ppt Layouts Example PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. This is a types of cloud security solutions cloud computing security it ppt layouts example pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hybrid cloud security solutions, smb cloud security solutions, enterprise cloud security solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information And Technology Security Operations Impact Of Effective Security Management Icons PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative information and technology security operations impact of effective security management icons pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
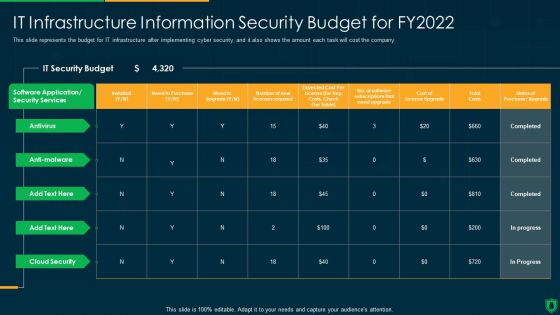
Info Security IT Infrastructure Information Security Budget For FY2022 Ppt PowerPoint Presentation File Pictures PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative info security it infrastructure information security budget for fy2022 ppt powerpoint presentation file pictures pdf bundle. Topics like it security budget, security services, cost license upgrade can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Elements Of Information Technology Security Operational Security Ppt Icon Guidelines PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a elements of information technology security operational security ppt icon guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process, sensitive, management, administration, operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Essential Pillars Of Cloud Security Cloud Computing Security IT Ppt Design Ideas PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. Presenting essential pillars of cloud security cloud computing security it ppt design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like visibility and consistency, process based security, network security, identity security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security What Is Cloud Security Ppt Inspiration Mockup PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. This is a Cloud Information Security What Is Cloud Security Ppt Inspiration Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Business Coherence, Small Organizations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
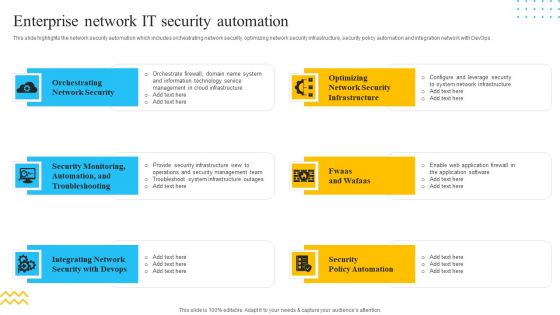
IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. This is a IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Orchestrating Network Security, Integrating Network, Security Policy Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
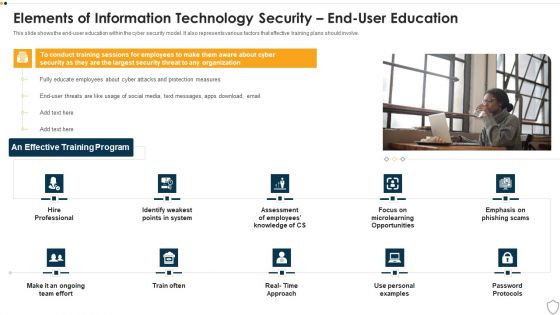
IT Security Elements Of Information Technology Security End User Education Ppt Show Maker PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a it security elements of information technology security end user education ppt show maker pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elements of information technology security end user education. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
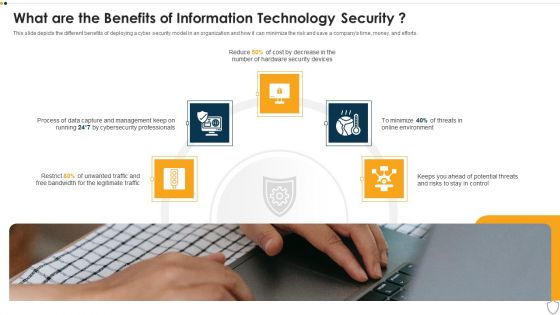
IT Security What Are The Benefits Of Information Technology Security Ppt Layouts Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a it security what are the benefits of information technology security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, process, potential threats, security devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Identity Security, Visibility Consistency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Corporate And Industrial Security Services Information PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Corporate And Industrial Security Services Information PDF. Use them to share invaluable insights on Corporate Security, Industrial Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
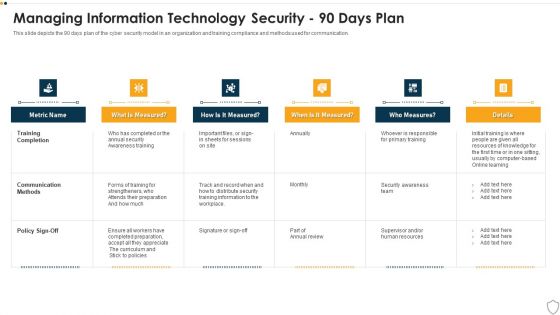
IT Security Managing Information Technology Security 90 Days Plan Sample PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 90 days plan sample pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Requirement Of Information Technology Security In Different Sectors Ppt File Display PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative it security requirement of information technology security in different sectors ppt file display pdf bundle. Topics like business transactions, organizations, financial, process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
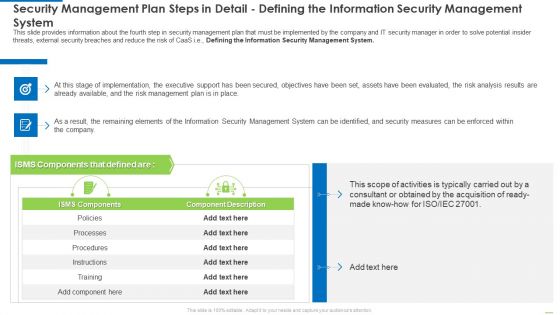
Security Management Plan Steps In Detail Defining The Information Security Management System Diagrams PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system diagrams pdf bundle. Topics like security management plan steps in detail - defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Sample PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system sample pdf bundle. Topics like security management plan steps in detail defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Mockup PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system mockup pdf. Use them to share invaluable insights on implementation, management plan, security management, security measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Estimated Security Management Plan Information PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks estimated security management plan information pdf Use them to share invaluable insights on security incidents level, security implementation, overall security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Manpower Corporate Security Business Profile Retail And Shopping Complex Security Services Icons PDF
This slide highlights the security company services for retail outlets, mall and shopping complex and theatre security which includes the key role and responsibility of security guard. Presenting Manpower Corporate Security Business Profile Retail And Shopping Complex Security Services Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Retail Security, Shopping Complex Security, Theatre Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
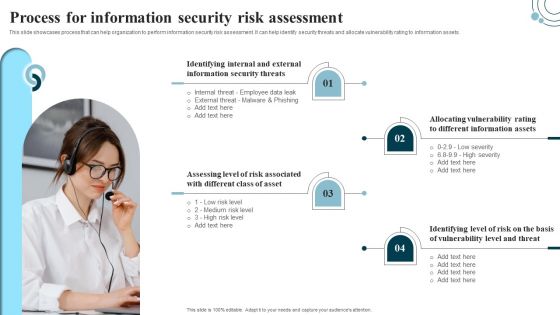
Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF.
Security Of Employees Devices IT Security IT Ppt Summary Background PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. This is a security of employees devices it security it ppt summary background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of employees devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
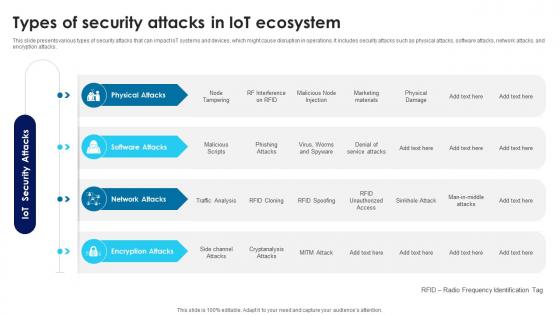
Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V
This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF
This slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF bundle. Topics like Awareness And Training, Protective Technology, Risk Assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
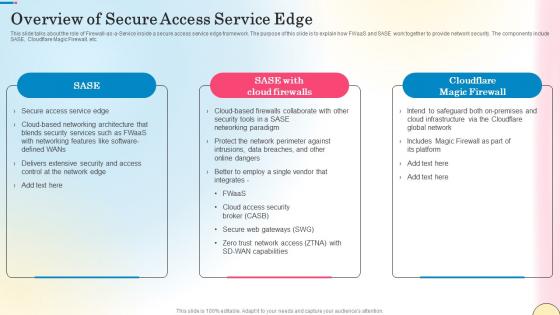
Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Elements Of IT Security IT Cloud Security Ppt Infographics Ideas PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting elements of it security it cloud security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, service, vulnerabilities, implemented, digital resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. This is a IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Failed Human Insights, Right Time Automation, High Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
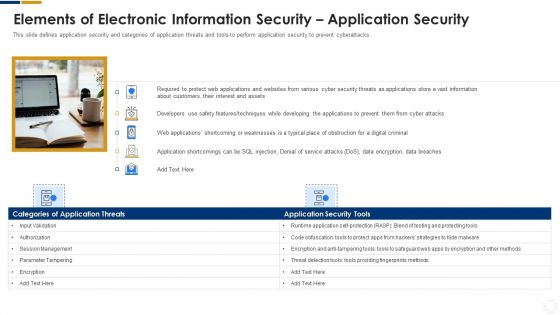
Cybersecurity Elements Of Electronic Information Security Application Security Ppt Styles Graphics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. This is a cybersecurity elements of electronic information security application security ppt styles graphics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, developers, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this information and technology security operations security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information And Technology Security Operations Security Operations Implementation Timeline Activity Professional PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative information and technology security operations security operations implementation timeline activity professional pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Security Operations Implementation Timeline Staff Template PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this information and technology security operations security operations implementation timeline staff template pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
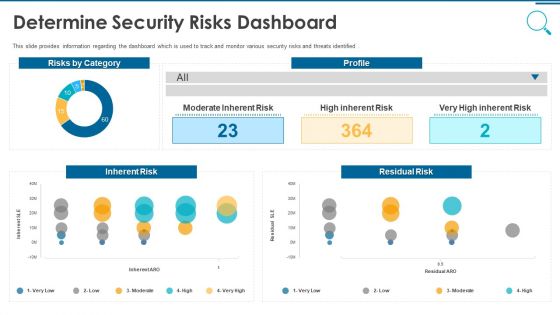
Information And Technology Security Operations Determine Security Risks Dashboard Themes PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations determine security risks dashboard themes pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Based Email Security Market Report Hosted E Mail Security Ppt Ideas Rules PDF
This slide displays the overview and key features of hosted E Mail Security. This is a cloud based email security market report hosted e mail security ppt ideas rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintenance, security, miscellaneous, protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Retail And Shopping Complex Security Services Summary PDF
This slide highlights the security company services for retail outlets, mall and shopping complex and theatre security which includes the key role and responsibility of security guard. This is a Security Officer Service Company Profile Retail And Shopping Complex Security Services Summary PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Retail Security, Shopping Complex Security, Theatre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
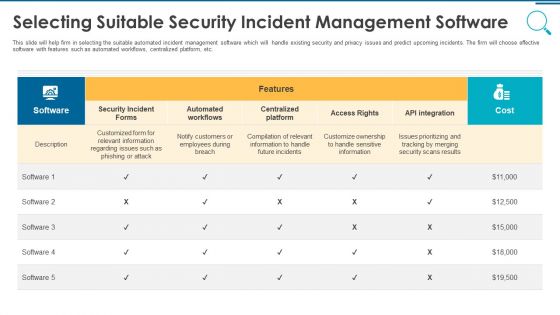
Information And Technology Security Operations Selecting Suitable Security Incident Management Software Diagrams PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative information and technology security operations selecting suitable security incident management software diagrams pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
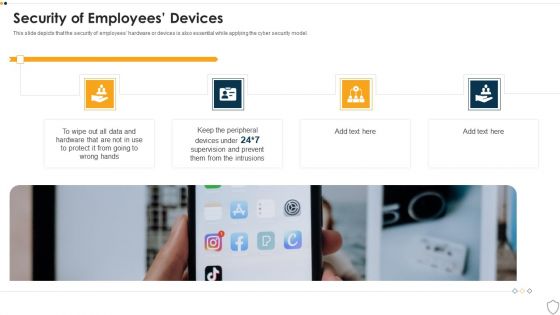
IT Security Security Of Employees Devices Ppt Summary Layout Ideas PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting it security security of employees devices ppt summary layout ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
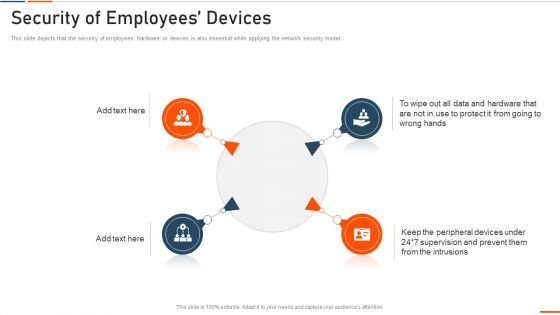
Information Technology Security Security Of Employees Devices Ppt File Portrait PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the network security model. Presenting information technology security security of employees devices ppt file portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Growth Guidelines PDF
This slide portrays information regarding the dashboard that firm will track various security incidents detected. These incidents will be managed in order to avoid security risks. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan security incidents tracking dashboard growth guidelines pdf. Use them to share invaluable insights on number of open security incidents, open security incidents by age, average age of open security incidents, security incident backlog growth and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
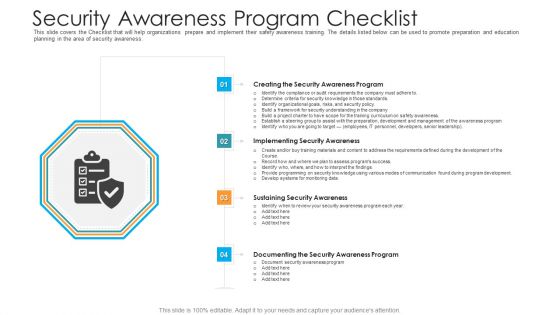
Security Awareness Program Checklist Hacking Prevention Awareness Training For IT Security Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting security awareness program checklist hacking prevention awareness training for it security background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating the security awareness program, implementing security awareness, sustaining security awareness, documenting the security awareness program. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

IT Security Common Methods Used To Threaten Information Technology Security Ppt Layouts Graphics PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a it security common methods used to threaten information technology security ppt layouts graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
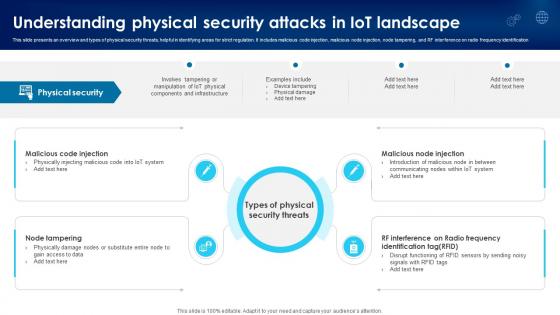
Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V
This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification. Find highly impressive Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
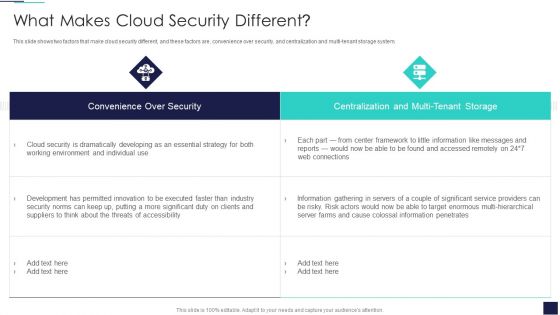
Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi-tenant storage system. Deliver an awe inspiring pitch with this creative Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF bundle. Topics like Cloud Security, Threats Accessibility, Risk Actors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home