Cybersecurity
Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. If you are looking for a format to display your unique thoughts, then the professionally designed Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Integrating Naas Service Model To Enhance Network As A Service Cloud Connections Rules PDF
This slide represents the naas cloud connections, covering metro ethernet, layer 2 virtual private networks, layer 3 virtual private networks, internet protocol secure ipsec MPLS vpns, SD-WAN, firewall, VCPE, remote access gateways, and so on. Explore a selection of the finest Integrating Naas Service Model To Enhance Network As A Service Cloud Connections Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Naas Service Model To Enhance Network As A Service Cloud Connections Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

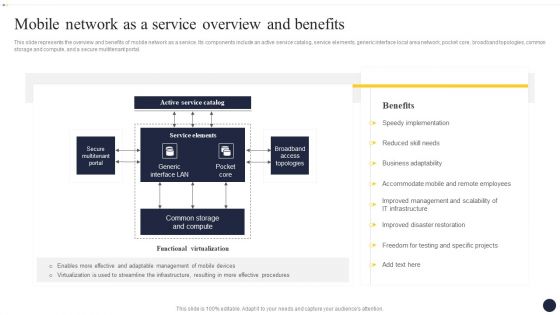
Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. Explore a selection of the finest Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Naas Architectural Framework Mobile Network As A Service Overview And Benefits Demonstration PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Naas Architectural Framework Mobile Network As A Service Overview And Benefits Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Naas Architectural Framework Mobile Network As A Service Overview And Benefits Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

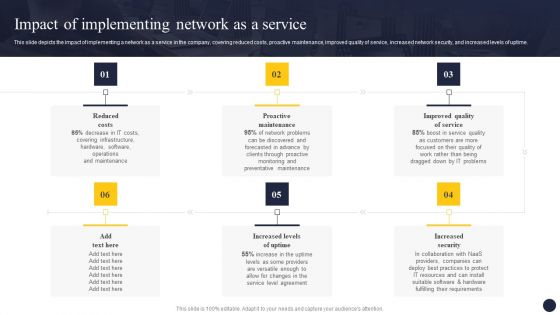
Naas Architectural Framework Impact Of Implementing Network As A Service Structure PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Naas Architectural Framework Impact Of Implementing Network As A Service Structure PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Naas Architectural Framework Impact Of Implementing Network As A Service Structure PDF today and make your presentation stand out from the rest.

Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Presenting this PowerPoint presentation, titled Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Welcome to our selection of the 1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
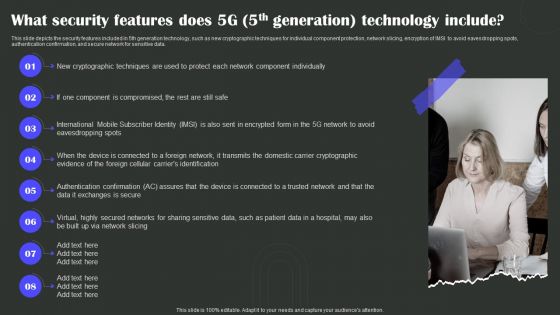
What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Present like a pro with What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
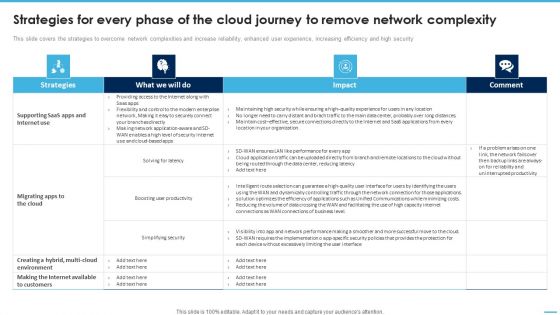
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF
This slide covers the strategies to overcome network complexities and increase reliability, enhanced user experience, increasing efficiency and high security.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF.
Integrating Naas Service Model To Enhance Impact Of Implementing Network As A Service Portrait PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. This Integrating Naas Service Model To Enhance Impact Of Implementing Network As A Service Portrait PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
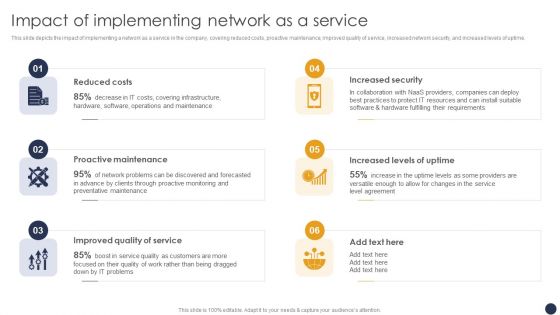
Integrating Naas Service Model Impact Of Implementing Network As A Service Ppt Slides Ideas PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integrating Naas Service Model Impact Of Implementing Network As A Service Ppt Slides Ideas PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Integrating Naas Service Model Network As A Service Cloud Connections Ppt Pictures Styles PDF
This slide represents the NaaS cloud connections, covering metro ethernet, layer 2 virtual private networks, layer 3 virtual private networks, internet protocol secure IPsec MPLS VPNs, SD-WAN, firewall, VCPE, remote access gateways, and so on. Take your projects to the next level with our ultimate collection of Integrating Naas Service Model Network As A Service Cloud Connections Ppt Pictures Styles PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
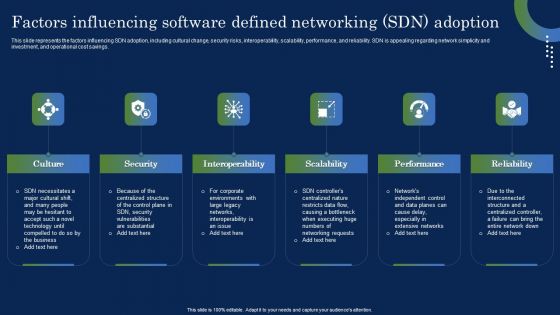
Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Naas Architectural Framework Network As A Service Cloud Connections Introduction PDF
This slide represents the NaaS cloud connections, covering metro ethernet, layer 2 virtual private networks, layer 3 virtual private networks, internet protocol secure IPsec MPLS VPNs, SD-WAN, firewall, VCPE, remote access gateways, and so on. The Naas Architectural Framework Network As A Service Cloud Connections Introduction PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
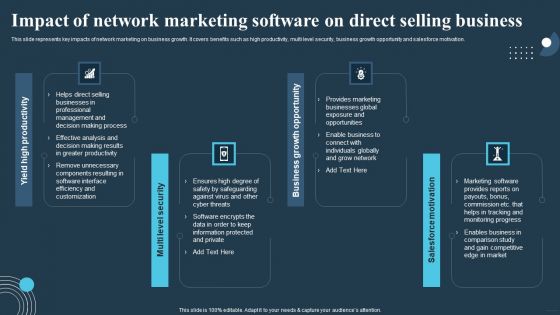
Comprehensive Guide For Multi Level Impact Of Network Marketing Software On Direct Rules PDF
This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation. Create an editable Comprehensive Guide For Multi Level Impact Of Network Marketing Software On Direct Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Comprehensive Guide For Multi Level Impact Of Network Marketing Software On Direct Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
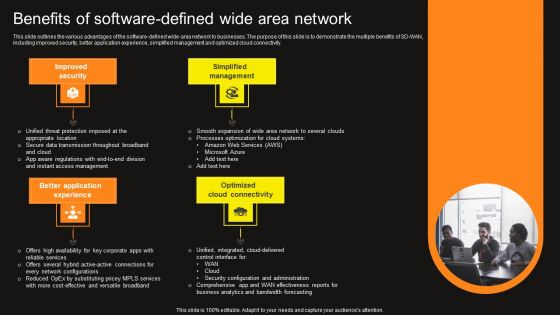
Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF
This slide outlines the various advantages of the software-defined wide-area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD-WAN, including improved security, better application experience, simplified management and optimized cloud connectivity. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
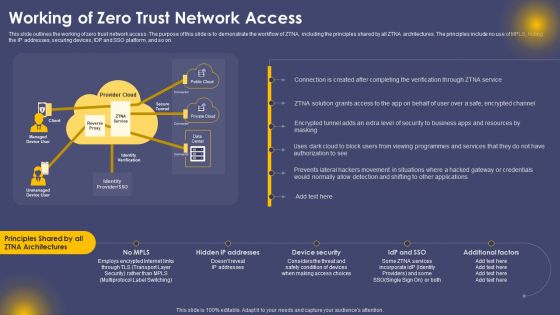
Working Of Zero Trust Network Access Ppt Professional File Formats PDF
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Are you searching for a Working Of Zero Trust Network Access Ppt Professional File Formats PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Working Of Zero Trust Network Access Ppt Professional File Formats PDF from Slidegeeks today.
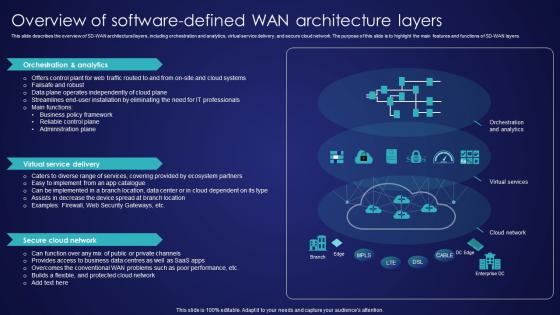
Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf
This slide describes the overview of SD-WAN architectural layers, including orchestration and analytics, virtual service delivery, and secure cloud network. The purpose of this slide is to highlight the main features and functions of SD-WAN layers. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf
Key Ways Of Incident Response Planning With Human Observations Ppt PowerPoint Presentation File Sample PDF
Persuade your audience using this key ways of incident response planning with human observations ppt powerpoint presentation file sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including physical alarm, cyber attack, human observations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
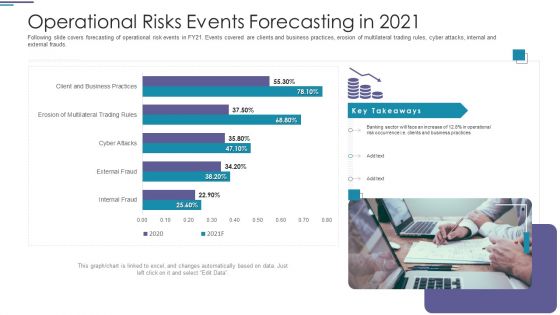
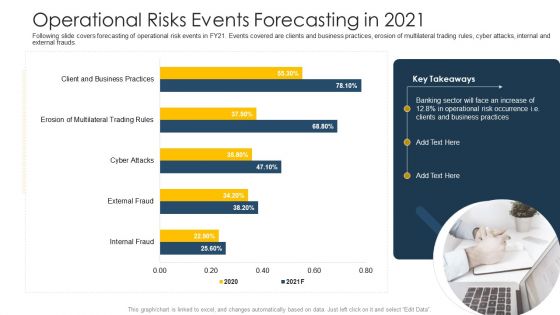
Operational Risks Events Forecasting In 2021 Ppt PowerPoint Presentation Ideas Picture PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds.Deliver an awe-inspiring pitch with this creative operational risks events forecasting in 2021 ppt powerpoint presentation ideas picture pdf. bundle. Topics like operational risks events forecasting in 2021 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
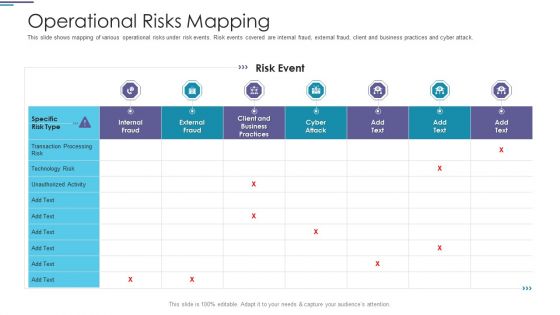
Operational Risks Mapping Ppt PowerPoint Presentation Ideas Graphics Example PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack.Deliver and pitch your topic in the best possible manner with this operational risks mapping ppt powerpoint presentation ideas graphics example pdf. Use them to share invaluable insights on transaction processing, technology risk, client and business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
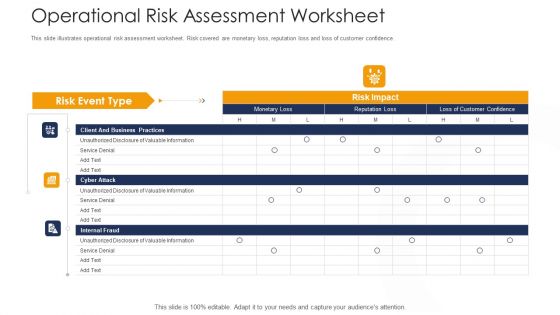
Strategies To Tackle Operational Risk In Banking Institutions Operational Risk Assessment Worksheet Elements PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative strategies to tackle operational risk in banking institutions operational risk assessment worksheet elements pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
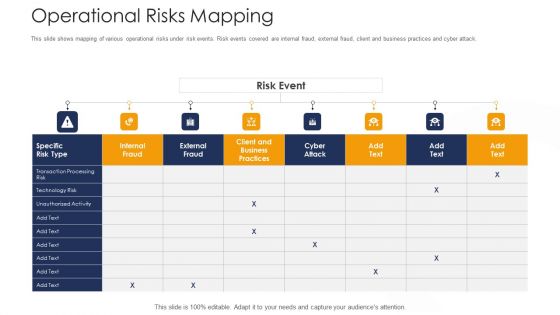
Strategies To Tackle Operational Risk In Banking Institutions Operational Risks Mapping Graphics PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe inspiring pitch with this creative strategies to tackle operational risk in banking institutions operational risks mapping graphics pdf bundle. Topics like technology risk, transaction processing risk, client and business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

OP Risk Management Operational Risk Assessment Worksheet Microsoft PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative op risk management operational risk assessment worksheet microsoft pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Initiating Hazard Managing Structure Firm Operational Risk Assessment Worksheet Rules PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe-inspiring pitch with this creative initiating hazard managing structure firm operational risk assessment worksheet rules pdf bundle. Topics like business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Establishing Operational Risk Framework Banking Operational Risks Events Forecasting In 2021 Portrait PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this establishing operational risk framework banking operational risks events forecasting in 2021 portrait pdf. Use them to share invaluable insights on business practices, operational risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Establishing Operational Risk Framework Banking Operational Risks Mapping Ppt File Icon PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe-inspiring pitch with this creative establishing operational risk framework banking operational risks mapping ppt file icon pdf bundle. Topics like client and business practices, technology risk, transaction processing risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Redundant Array Of Independent Disks Storage IT Checklist To Implement RAID In Business Formats PDF
This slide depicts the checklist to implement RAID in business describing guidelines to follow while implementing RAID. Deliver an awe inspiring pitch with this creative redundant array of independent disks storage it checklist to implement raid in business formats pdf bundle. Topics like organization, implement, cyber attacks, budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Risk Management Structure In Financial Companies Operational Risk Assessment Worksheet Introduction PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risk assessment worksheet introduction pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Risk Management Structure In Financial Companies Operational Risks Mapping Summary PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risks mapping summary pdf bundle. Topics like transaction processing risk, technology risk, unauthorized activity, business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
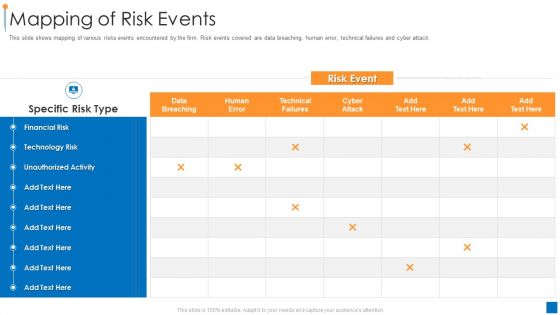
International Organization Standardization 270001 Mapping Of Risk Events Slides PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative international organization standardization 270001 mapping of risk events slides pdf bundle. Topics like financial risk, technology risk, unauthorized activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Statistics Associated To Workplace Threats Summary PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver an awe inspiring pitch with this creative threat management at workplace statistics associated to workplace threats summary pdf bundle. Topics like cyber attacks costs, organization, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
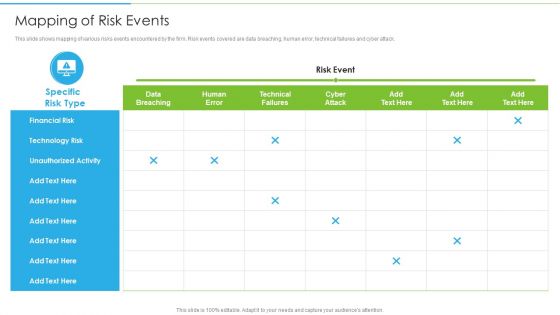
Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF bundle. Topics like Financial Risk, Technology Risk, Unauthorized Activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
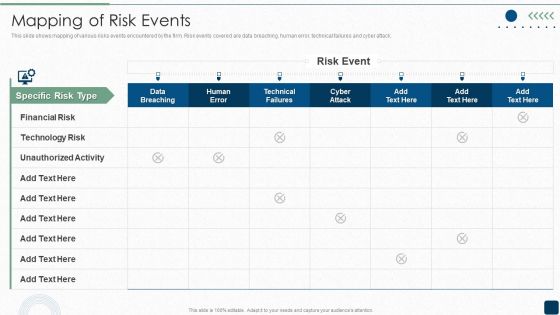
Mapping Of Risk Events Infographics PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative Mapping Of Risk Events Infographics PDF bundle. Topics like Financial Risk, Unauthorized Activity, Technology Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF bundle. Topics like Unauthorized Activity, Technology Risk, Financial Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
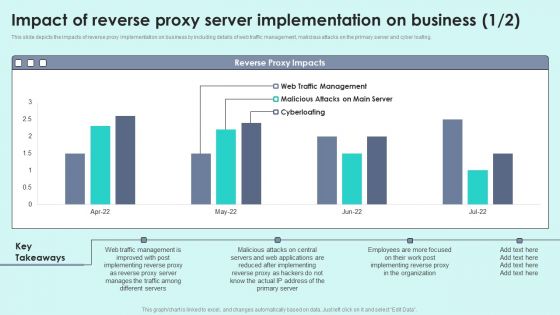
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing.Deliver an awe inspiring pitch with this creative Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF bundle. Topics like After Implementing, Manages Traffic, Different Servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
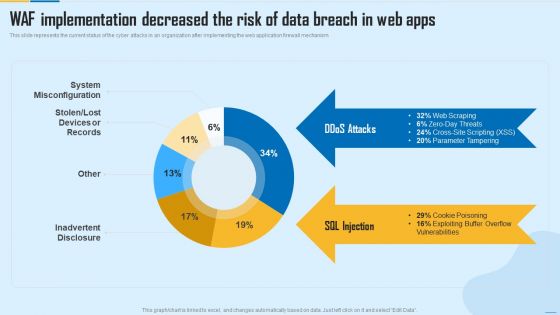
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF bundle. Topics like Organization Systems, Networks, Internal can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
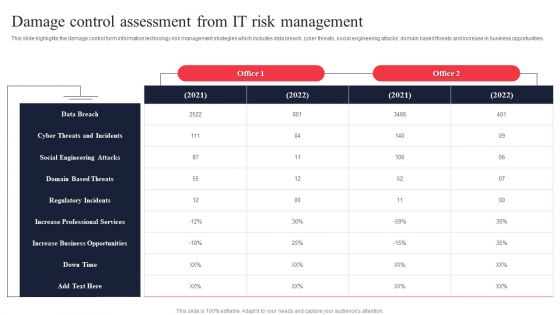
IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
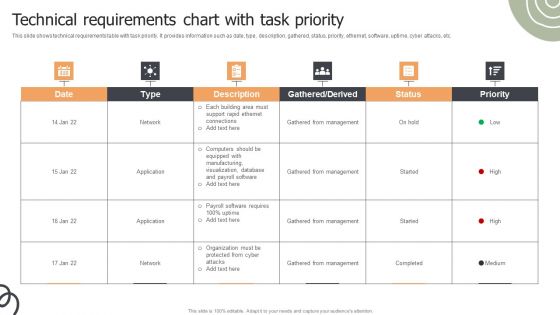
Technical Requirements Chart With Task Priority Ppt Infographics Styles PDF
This slide shows technical requirements table with task priority. It provides information such as date, type, description, gathered, status, priority, ethernet, software, uptime, cyber attacks, etc. Pitch your topic with ease and precision using this Technical Requirements Chart With Task Priority Ppt Infographics Styles PDF. This layout presents information on Gathered From Management, Network, Application. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Digital Terrorism Types And Categories With Examples Sample PDF
This slide shows various categories of cyber terrorism attacks according to their severity . It include categories such as simple unstructured, advance structured, complex coordinated etc. Showcasing this set of slides titled Digital Terrorism Types And Categories With Examples Sample PDF. The topics addressed in these templates are Advance Structured, Complex Coordinated, Simple Unstructured. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF
This slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf today and make your presentation stand out from the rest

Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
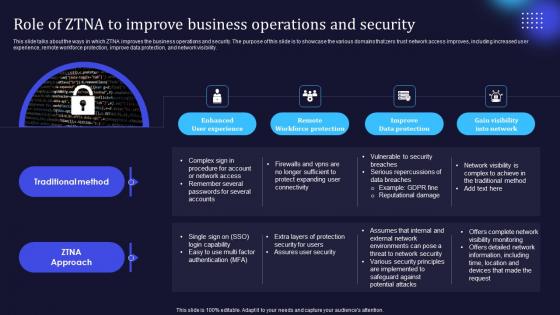
Zero Trust Model Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Boost your pitch with our creative Zero Trust Model Role Of ZTNA To Improve Business Operations And Security. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Deploying Docker Container And Kubernetes Within Organization Best Security Measures In Kubernetes Ppt PowerPoint Presentation PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization best security measures in kubernetes ppt powerpoint presentation pdf. This is a ten stage process. The stages in this process are enables auditing provide limited direct access kubernetes nodes, resources quota, authorized repository, rules resources, implement, network segmentation, log everything production environment, restrict access to etcd. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Security IT Prepare And Deploy Strong IT Policies Ppt Icon Design Ideas PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security it prepare and deploy strong it policies ppt icon design ideas pdf bundle. Topics like it policies, management, access, policies, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
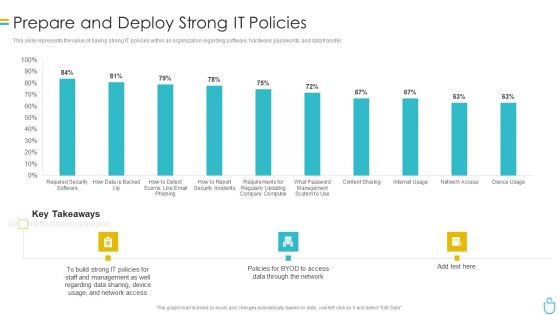
Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Prepare And Deploy Strong It Policies Template PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this desktop security management prepare and deploy strong it policies template pdf. Use them to share invaluable insights on management, data, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Security IT Attacks Experienced By Company Ppt Show Grid PDF
This slide shows the impact on the organizations financial condition due to network attacks in the past financial year 2021. Deliver an awe inspiring pitch with this creative information technology security it attacks experienced by company ppt show grid pdf bundle. Topics like it attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Example PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security prepare and deploy strong it policies ppt icon graphics example pdf bundle. Topics like management, it policies, network access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
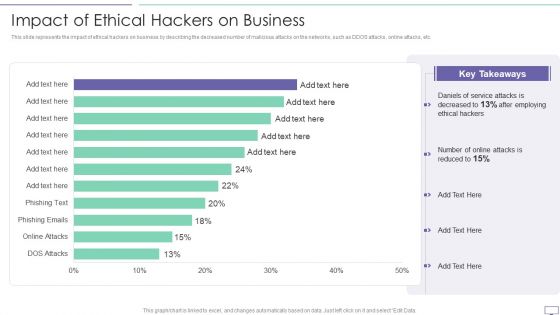
IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
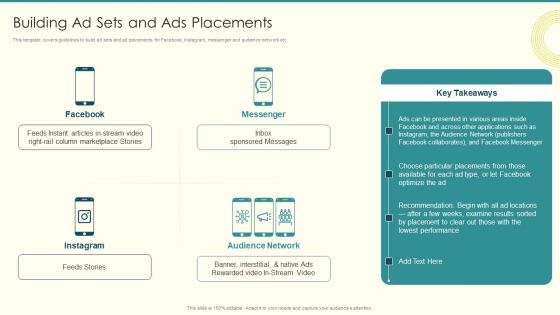
Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF
This template covers guidelines to build ad sets and ad placements for Facebook, Instagram, messenger and audience network etc. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF. Use them to share invaluable insights on Column Marketplace, Presented Various, Choose Particular and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF. Use them to share invaluable insights on Demographics, Social Networks, Sessions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
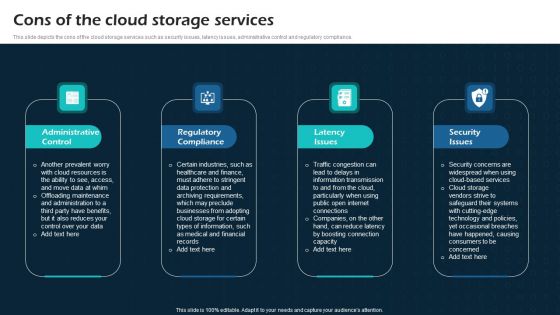
Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF
This slide depicts the cons of the cloud storage services such as security issues, latency issues, administrative control and regulatory compliance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF
This slide depicts the hybrid cloud storage service, its implementation method, and advantages such as Flexibility and security, cost effectiveness and excellence in risk management. If you are looking for a format to display your unique thoughts, then the professionally designed Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

 Home
Home