Cybersecurity

Considerations For Open Ran Implementation Revolutionizing Mobile Networks Mockup PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Create an editable Considerations For Open Ran Implementation Revolutionizing Mobile Networks Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Considerations For Open Ran Implementation Revolutionizing Mobile Networks Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Email Security Market Research Report Ppt PowerPoint Presentation Complete Deck With Slides

Global Cloud Based Email Security Market Ppt PowerPoint Presentation Complete Deck With Slides
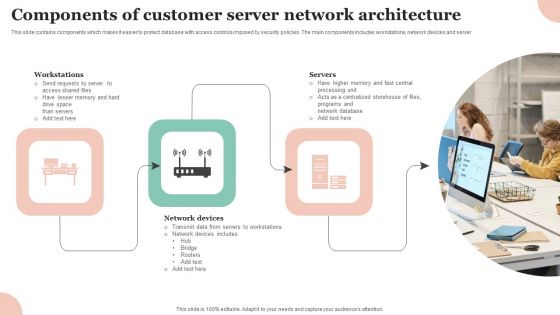
Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Zero Trust Network Access Performance Tracking Dashboard Template PDF
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Find a pre-designed and impeccable Zero Trust Network Access Performance Tracking Dashboard Template PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
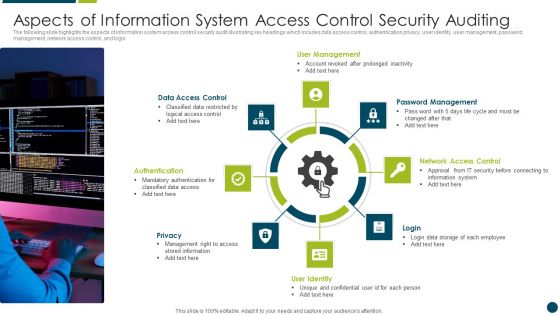
Aspects Of Information System Access Control Security Auditing Diagrams PDF
The following slide highlights the aspects of information system access control security audit illustrating key headings which incudes data access control, authentication privacy, user identity, user management, password management, network access control, and login Presenting Aspects Of Information System Access Control Security Auditing Diagrams PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Management, Data Access Control, Network Access Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
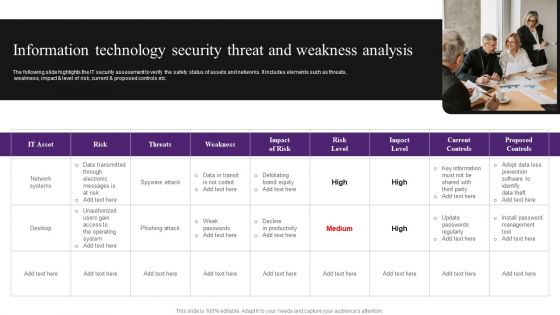
Information Technology Security Threat And Weakness Analysis Diagrams PDF
The following slide highlights the IT security assessment to verify the safety status of assets and networks. It includes elements such as threats, weakness, impact and level of risk, current and proposed controls etc. Persuade your audience using this Information Technology Security Threat And Weakness Analysis Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Risk, Network Systems, Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
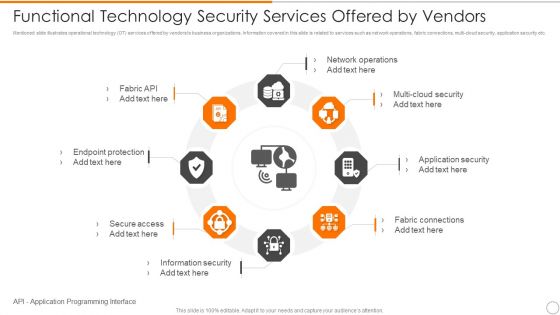
Functional Technology Security Services Offered By Vendors Microsoft PDF
Persuade your audience using this functional technology security services offered by vendors microsoft pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including network operations, security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Developing Business Analytics Framework Addressing Different Network Information PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a Developing Business Analytics Framework Addressing Different Network Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Fault Management , Performance Management, Configuration Management You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
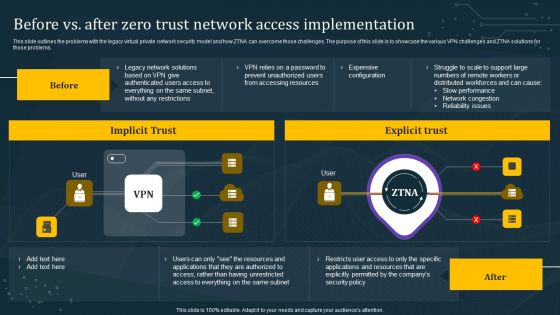
Before Vs After Zero Trust Network Access Implementation Background PDF
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Zero Trust Network Access Implementation Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
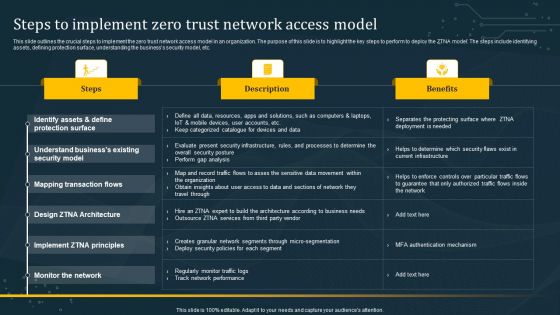
Steps To Implement Zero Trust Network Access Model Graphics PDF
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Steps To Implement Zero Trust Network Access Model Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
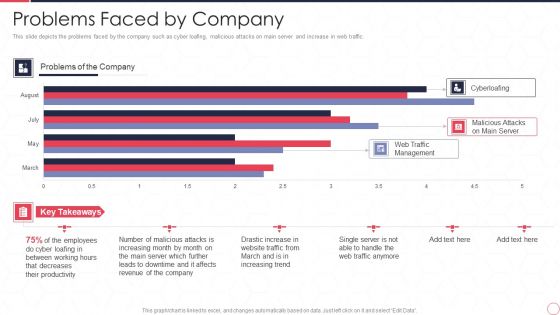
Reverse Proxy Server IT Problems Faced By Company Ppt Summary Inspiration PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic. Deliver and pitch your topic in the best possible manner with this reverse proxy server it problems faced by company ppt summary inspiration pdf. Use them to share invaluable insights on web traffic management, malicious attacks on main server, cyberloafing, employee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
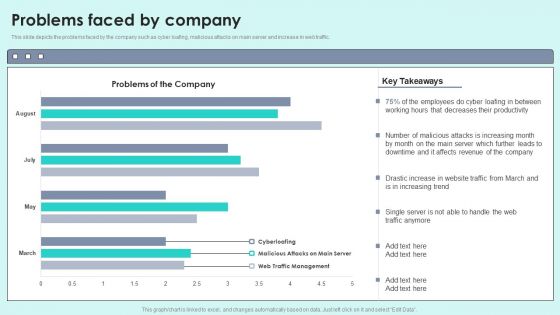
Problems Faced By Company Reverse Proxy For Load Balancing Designs PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic.Deliver and pitch your topic in the best possible manner with this Problems Faced By Company Reverse Proxy For Load Balancing Designs PDF. Use them to share invaluable insights on Decreases Productivity, Malicious Attacks, Affects Revenue and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Software Defined Perimeter Solution Infrastructure Elements PDF
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Deliver an awe inspiring pitch with this creative Software Defined Perimeter Solution Infrastructure Elements PDF bundle. Topics like System Analyst, Services, Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
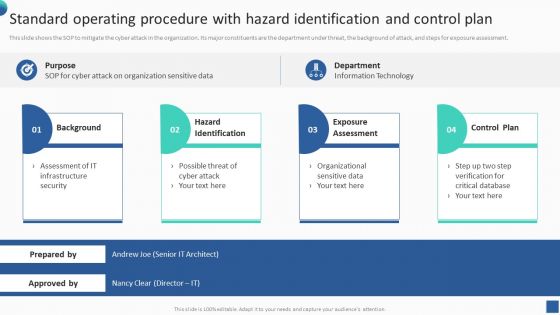
Bundle Of SOP Templates Standard Operating Procedure With Hazard Identification And Control Information PDF
This slide shows the SOP to mitigate the cyber attack in the organization. Its major constituents are the department under threat, the background of attack, and steps for exposure assessment. There are so many reasons you need a Bundle Of SOP Templates Standard Operating Procedure With Hazard Identification And Control Information PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Internet Security Threat Analysis Plan With Agents And Tactics Ppt PowerPoint Presentation Gallery Infographic Template PDF
Showcasing this set of slides titled internet security threat analysis plan with agents and tactics ppt powerpoint presentation gallery infographic template pdf. The topics addressed in these templates are corporations, hacktivists, cyber fighters. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
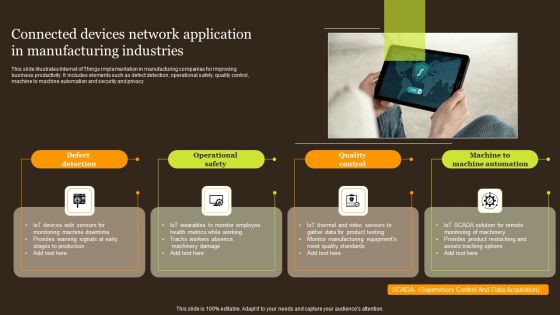
Connected Devices Network Application In Manufacturing Industries Portrait PDF
This slide illustrates Internet of Things implementation in manufacturing companies for improving business productivity. It includes elements such as defect detection, operational safety, quality control, machine to machine automation and security and privacy. Presenting Connected Devices Network Application In Manufacturing Industries Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Defect Detection, Operational Safety, Quality Control . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
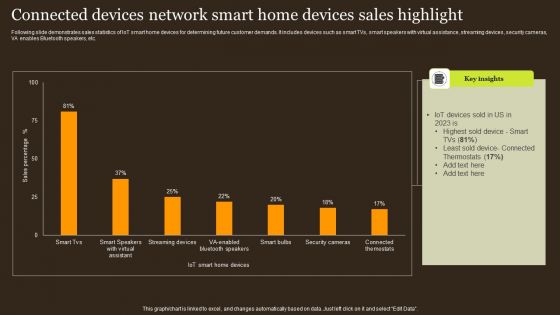
Connected Devices Network Smart Home Devices Sales Highlight Structure PDF
Following slide demonstrates sales statistics of IoT smart home devices for determining future customer demands. It includes devices such as smart TVs, smart speakers with virtual assistance, streaming devices, security cameras, VA enables Bluetooth speakers, etc. Showcasing this set of slides titled Connected Devices Network Smart Home Devices Sales Highlight Structure PDF. The topics addressed in these templates are Iot Devices, Least Sold Device, Thermostats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
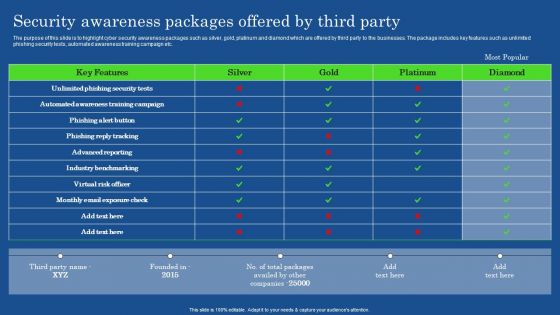
Security Awareness Packages Offered By Third Party Designs PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This Security Awareness Packages Offered By Third Party Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Awareness Packages Offered By Third Party Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
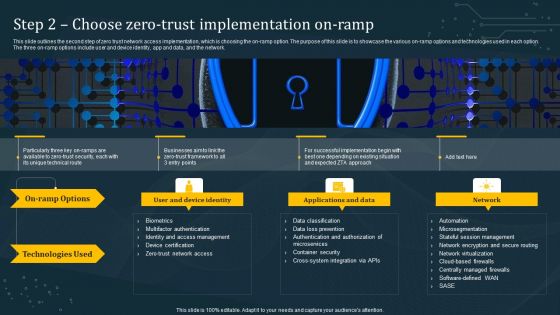
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
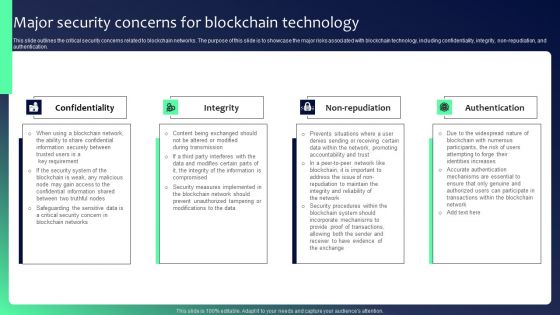
Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF
This slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, non-repudiation, and authentication. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF today and make your presentation stand out from the rest
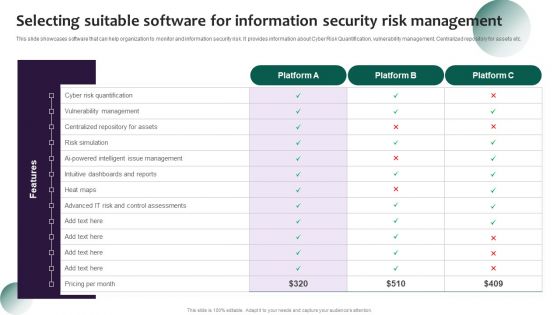
Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF
This slide showcases software that can help organization to monitor and information security risk. It provides information about Cyber Risk Quantification, vulnerability management, Centralized repository for assets etc. Get a simple yet stunning designed Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
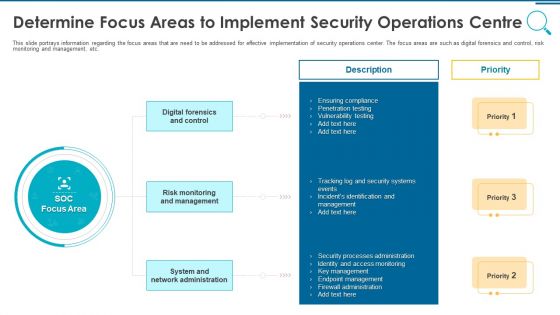
Information And Technology Security Operations Determine Focus Areas To Implement Security Operations Centre Download PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a information and technology security operations determine focus areas to implement security operations centre download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security and process integration determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information Operational Outlook Of Security Awareness Structure PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered. Slidegeeks has constructed Prevention Of Information Operational Outlook Of Security Awareness Structure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Prevention Of Information Security Awareness Training Program Challenges Icons PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Prevention Of Information Security Awareness Training Program Challenges Icons PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Security Awareness Training Program Challenges Ppt Styles Clipart PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Security Awareness Training Program Challenges Ppt Styles Clipart PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Secure Access Service Edge Importance Ppt Outline Graphics Example PDF
This slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. This modern and well arranged Secure Access Service Edge Importance Ppt Outline Graphics Example PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
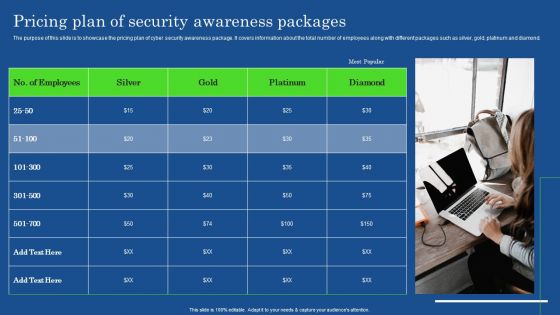
Pricing Plan Of Security Awareness Packages Slides PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Pricing Plan Of Security Awareness Packages Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

OP Risk Management Operational Risks Events Forecasting In 2021 Designs PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver an awe inspiring pitch with this creative op risk management operational risks events forecasting in 2021 designs pdf bundle. Topics like client and business practices, erosion of multilateral trading rules, cyber attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Initiating Hazard Managing Structure Firm Operational Risks Events Forecasting In 2021 Designs PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this initiating hazard managing structure firm operational risks events forecasting in 2021 designs pdf. Use them to share invaluable insights on operational risk events, clients, business practices, cyber attacks, internal and external frauds and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Risk Management Structure In Financial Companies Operational Risks Events Forecasting In 2021 Rules PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risks events forecasting in 2021 rules pdf bundle. Topics like business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF bundle. Topics like Errors Done By Employees, Technical Failures, Phishing Emails, Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF. Use them to share invaluable insights on Technical Failures, Phishing Emails, Cyber Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
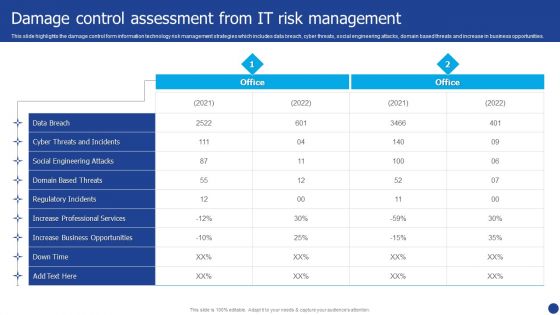
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
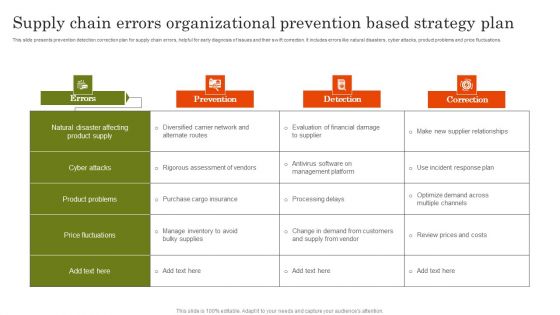
Supply Chain Errors Organizational Prevention Based Strategy Plan Topics PDF
This slide presents prevention detection correction plan for supply chain errors, helpful for early diagnosis of issues and their swift correction. It includes errors like natural disasters, cyber attacks, product problems and price fluctuations. Present the topic in a bit more detail with this Supply Chain Errors Organizational Prevention Based Strategy Plan Topics PDF. Use it as a tool for discussion and navigation on Cyber Attacks, Product Problems, Price Fluctuations. This template is free to edit as deemed fit for your organization. Therefore download it now.
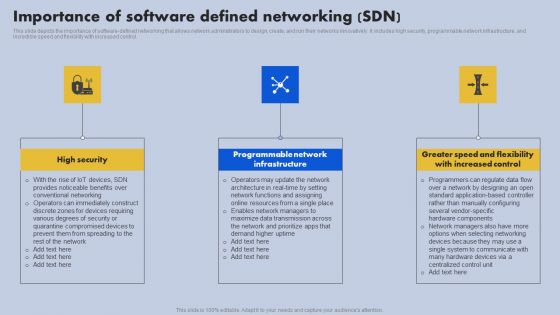
Importance Of Software Defined Networking SDN Ppt File Inspiration PDF
This slide depicts the importance of software-defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Slidegeeks has constructed Importance Of Software Defined Networking SDN Ppt File Inspiration PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
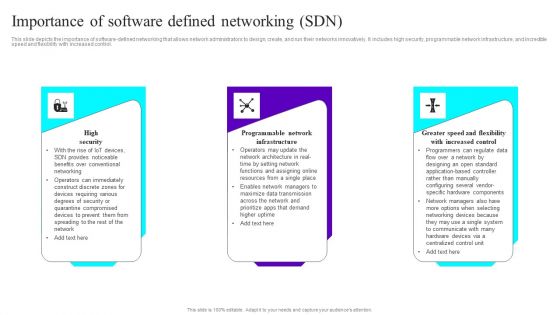
Importance Of Software Defined Networking SDN Ppt Ideas Good PDF
This slide depicts the importance of software-defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Slidegeeks has constructed Importance Of Software Defined Networking SDN Ppt Ideas Good PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
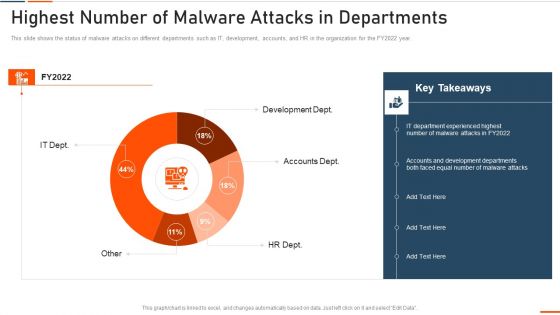
Information Technology Security Highest Number Of Malware Attacks In Departments Ppt Styles Slide Portrait PDF
This slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver and pitch your topic in the best possible manner with this information technology security highest number of malware attacks in departments ppt styles slide portrait pdf. Use them to share invaluable insights on phishing, network, intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
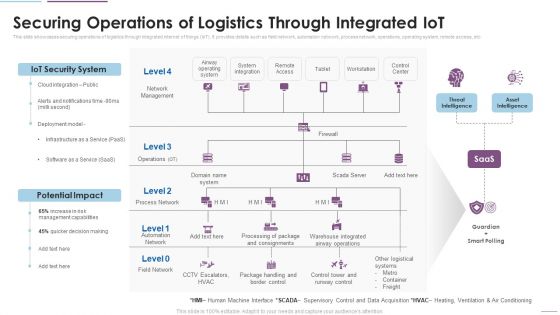
Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. This is a Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IoT Security System, Potential Impact, Network Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Program Framework Key Components Ppt Inspiration Ideas PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this information security program framework key components ppt inspiration ideas pdf. Use them to share invaluable insights on network security, application security, vendor management, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf
Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. This modern and well arranged Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Roadmap To Implement Zero Trust Network Access Model Structure PDF
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Want to ace your presentation in front of a live audience Our Roadmap To Implement Zero Trust Network Access Model Structure PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Top Zero Trust Network Access Software Solutions Microsoft PDF
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Top Zero Trust Network Access Software Solutions Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Top Zero Trust Network Access Software Solutions Microsoft PDF.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.

Zero Trust Network Access Implementation Challenges Rules PDF
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Implementation Challenges Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Implementation Challenges Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Implementation Challenges Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
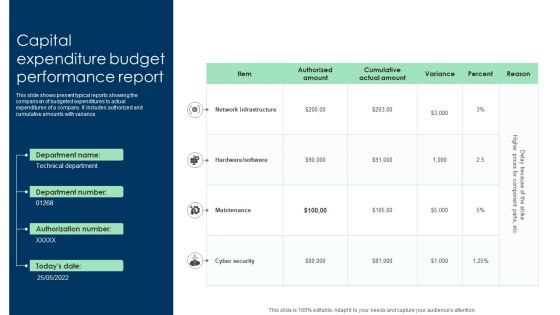
Capital Expenditure Budget Performance Report Ppt Inspiration Graphics PDF
This slide shows present typical reports showing the comparison of budgeted expenditures to actual expenditures of a company. It includes authorized and cumulative amounts with variance. Showcasing this set of slides titled Capital Expenditure Budget Performance Report Ppt Inspiration Graphics PDF. The topics addressed in these templates are Network Infrastructure, Maintenance, Cyber Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
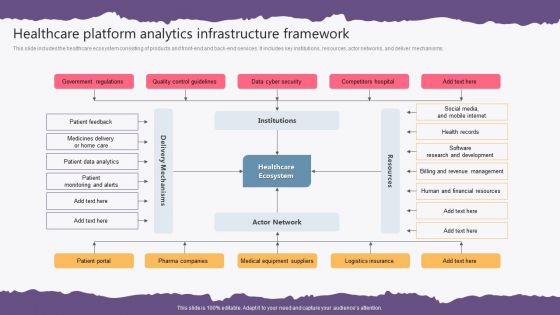
Healthcare Platform Analytics Infrastructure Framework Background PDF
This slide includes the healthcare ecosystem consisting of products and front-end and back-end services. It includes key institutions, resources, actor networks, and deliver mechanisms. Pitch your topic with ease and precision using this Healthcare Platform Analytics Infrastructure Framework Background PDF. This layout presents information on Government Regulations, Quality Control Guidelines, Data Cyber Security, Competitors Hospital. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
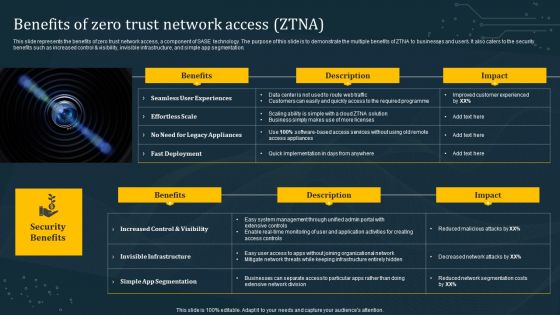
Benefits Of Zero Trust Network Access ZTNA Download PDF
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Present like a pro with Benefits Of Zero Trust Network Access ZTNA Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Timeline To Implement Zero Trust Network Access Model Rules PDF
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline To Implement Zero Trust Network Access Model Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline To Implement Zero Trust Network Access Model Rules PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
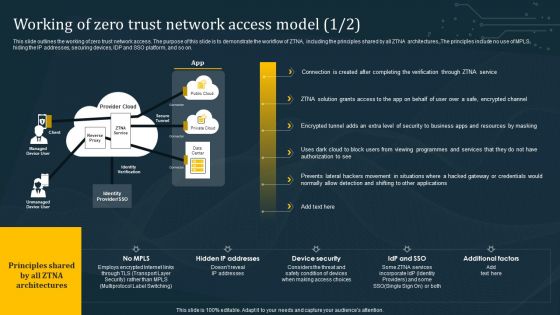
Working Of Zero Trust Network Access Model Summary PDF
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Working Of Zero Trust Network Access Model Summary PDF from Slidegeeks and deliver a wonderful presentation.

Zero Trust Network Access System Use Cases Summary PDF
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Boost your pitch with our creative Zero Trust Network Access System Use Cases Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Determine Established Security Centre Overview Ppt Show Visual Aids PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative determine established security centre overview ppt show visual aids pdf bundle. Topics like security, network, systems, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Certified Information Systems Security Professional Cissp Examination Details Elements PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Deliver an awe inspiring pitch with this creative certified information systems security professional cissp examination details elements pdf bundle. Topics like requirements, network security, security engineering, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home