Cyber Threat
Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Develop Corporate Cyber Security Risk Mitigation Plan Roadmap For Organization Cyber Protection Proposal Summary PDF
Presenting develop corporate cyber security risk mitigation plan roadmap for organization cyber protection proposal summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap, organization cyber protection. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
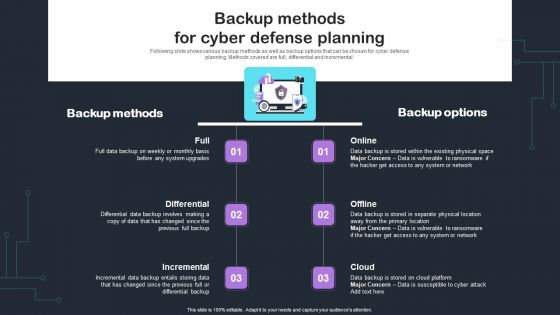
Cyber Risks And Incident Response Playbook Backup Methods For Cyber Defense Planning Portrait PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental. There are so many reasons you need a Cyber Risks And Incident Response Playbook Backup Methods For Cyber Defense Planning Portrait PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Strategies To Mitigate Cyber Security Risks Categorization Of Cyber Risks Ppt Model Designs Download PDF
Presenting this set of slides with name strategies to mitigate cyber security risks categorization of cyber risks ppt model designs download pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Dashboard Cyber Risk Management Ppt Professional Display PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard cyber risk management ppt professional display pdf. The topics discussed in these slides are risks threshold top 5 vulnerabilities, risk rating breakdown, action plan breakdown, risk heat map. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Categorization Of Cyber Risks Ppt PowerPoint Presentation Portfolio Sample PDF
Presenting this set of slides with name cyber security implementation framework categorization of cyber risks ppt powerpoint presentation portfolio sample pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Dashboard Cyber Risk Management Ppt Outline Structure PDF
Presenting this set of slides with name cyber security implementation framework dashboard cyber risk management ppt outline structure pdf. The topics discussed in these slides are risk rating breakdown, risk analysis progress, average risk threshold, response progress for risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Incident Reporting By Different Cyber Departments Summary PDF
Presenting this set of slides with name strategies to mitigate cyber security risks incident reporting by different cyber departments summary pdf. This is a one stage process. The stages in this process are number incidents, person involved incident, average cost per incident, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
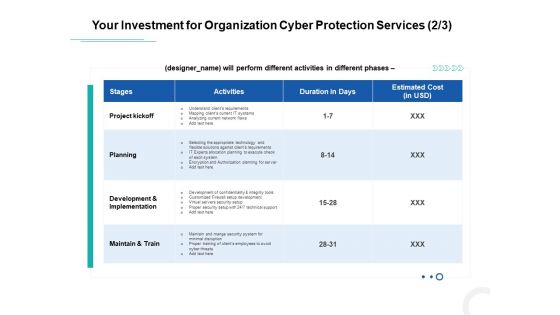
Develop Corporate Cyber Security Risk Mitigation Plan Your Investment For Organization Cyber Protection Service Mockup PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan your investment for organization cyber protection service mockup pdf bundle. Topics like project kickoff, planning, development and implementation, maintain and train can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Are you searching for a CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF from Slidegeeks today.
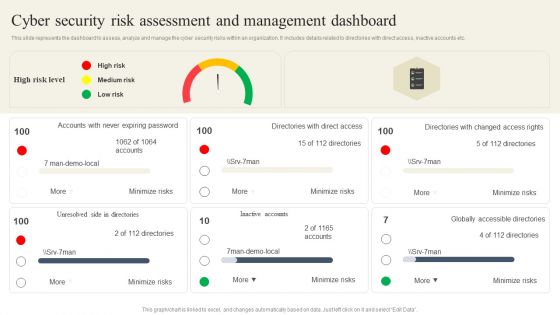
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. This CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
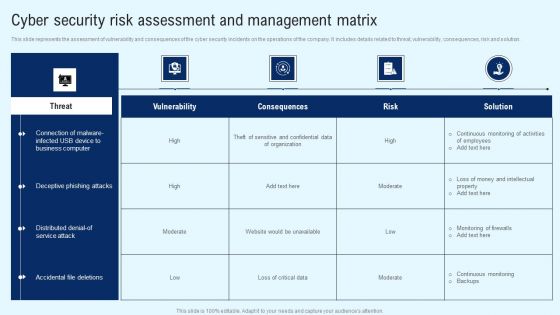
Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Get a simple yet stunning designed Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
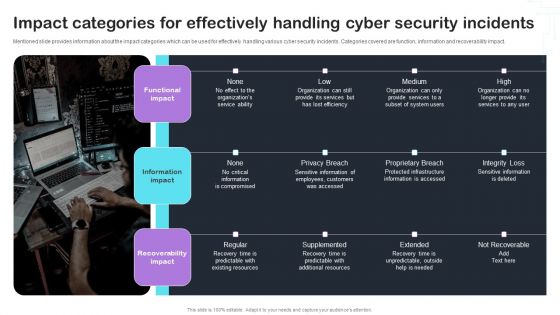
Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. This Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
Cyber Security For Your Organization Agenda For Cyber Security Management Ppt Tips PDF
Presenting this set of slides with name cyber security for your organization agenda for cyber security management ppt tips pdf. This is a one stage process. The stages in this process are roles and responsibilities, management, executives responsible, risk management, optimize cybersecurity risk framework, executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Agenda For Cyber Security Management Ppt PowerPoint Presentation Gallery Ideas PDF
Presenting this set of slides with name cyber security implementation framework agenda for cyber security management ppt powerpoint presentation gallery ideas pdf. This is a one stage process. The stages in this process are determining roles and responsibilities, risk management, executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
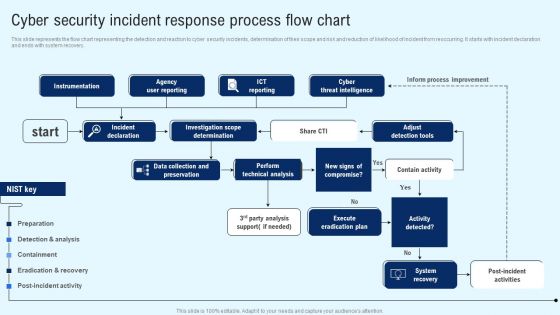
Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Explore a selection of the finest Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
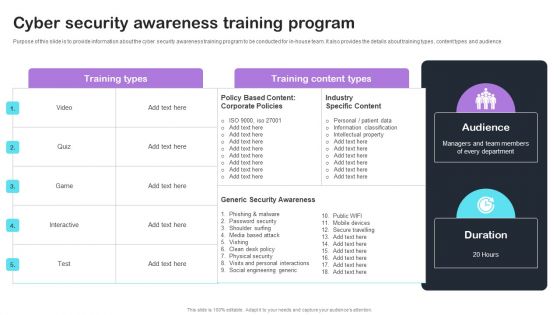
Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cyber Risks And Incident Response Playbook Purpose Of Cyber Risks And Incident Response Playbook Download PDF
Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Cyber Risks And Incident Response Playbook Purpose Of Cyber Risks And Incident Response Playbook Download PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Cyber Risks And Incident Response Playbook Purpose Of Cyber Risks And Incident Response Playbook Download PDF.

Strategies To Mitigate Cyber Security Risks Agenda For Cyber Security Risks Ppt Infographics Graphics Design PDF
Presenting this set of slides with name strategies to mitigate cyber security risks agenda for cyber security risks ppt infographics graphics design pdf. This is a one stage process. The stages in this process are determining roles and responsibilities, senior management, executives responsible, risk management, presenting optimize cybersecurity, risk framework. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
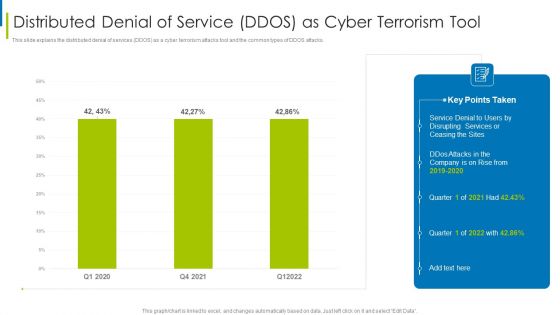
Cyber Terrorism Assault Distributed Denial Of Service DDOS As Cyber Terrorism Tool Slides PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism attacks tool and the common types of DDOS attacks.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault distributed denial of service ddos as cyber terrorism tool slides pdf Use them to share invaluable insights on Make A Risk Assessment, Determine The Importance Of Assets, Make A Complete Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF today and make your presentation stand out from the rest.

Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Strategies To Mitigate Cyber Security Risks Cyber Security Governance Ppt Styles Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cyber security governance ppt styles model pdf. This is a one stage process. The stages in this process are senior management, steering committee and executive management, ciso steering committee, business strategy, risk management, information, security strategy, security action plan, policies, standards organisation, objectives security requirements, security programs, implementation, security objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Develop Corporate Cyber Security Risk Mitigation Plan Cover Letter For Organization Cyber Protection Services Inspiration PDF
Presenting develop corporate cyber security risk mitigation plan cover letter for organization cyber protection services inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like systems and servers, achieve goals, secure organization information, network security monitoring. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
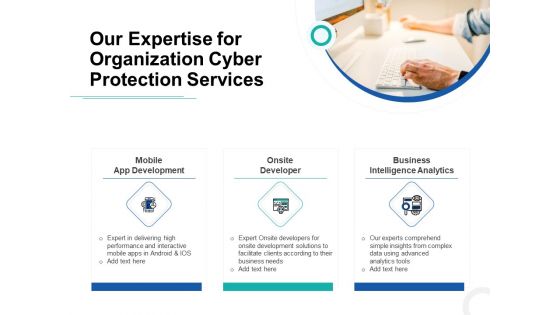
Develop Corporate Cyber Security Risk Mitigation Plan Our Expertise For Organization Cyber Protection Services Background PDF
Presenting develop corporate cyber security risk mitigation plan our expertise for organization cyber protection services background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like mobile app development, onsite developer, business intelligence analytic. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
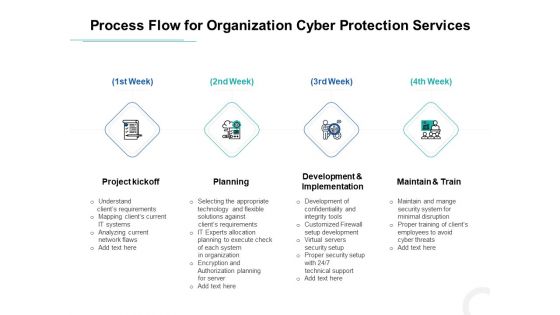
Develop Corporate Cyber Security Risk Mitigation Plan Process Flow For Organization Cyber Protection Services Background PDF
This is a develop corporate cyber security risk mitigation plan process flow for organization cyber protection services background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, maintain and train. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Develop Corporate Cyber Security Risk Mitigation Plan Timeframe For Organization Cyber Protection Services Structure PDF
This is a develop corporate cyber security risk mitigation plan timeframe for organization cyber protection services structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, results. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Develop Corporate Cyber Security Risk Mitigation Plan Why Us For Organization Cyber Protection Services Sample PDF
Presenting develop corporate cyber security risk mitigation plan why us for organization cyber protection services sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like knowledge, system security, net development, it support services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
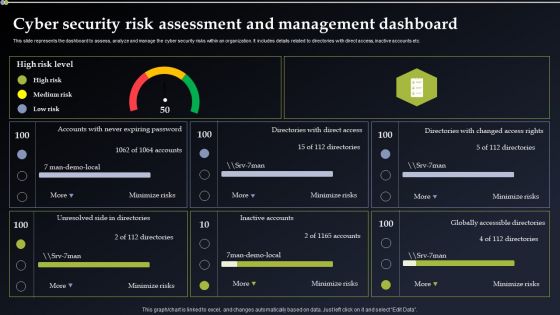
Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
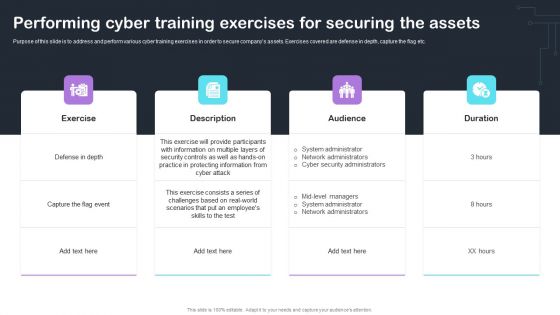
Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Retrieve professionally designed Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Russian Cyber Attacks On Ukraine IT Cyber Officials Urge Background PDF
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines. Presenting russian cyber attacks on ukraine it cyber officials urge background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, organizations, risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
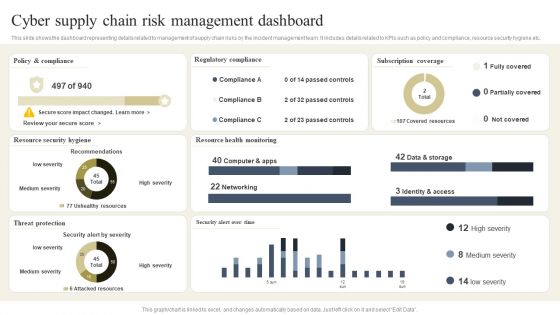
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
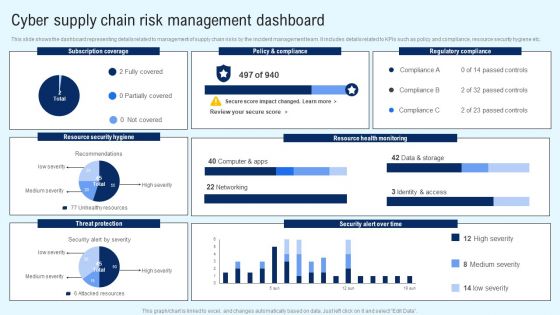
Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
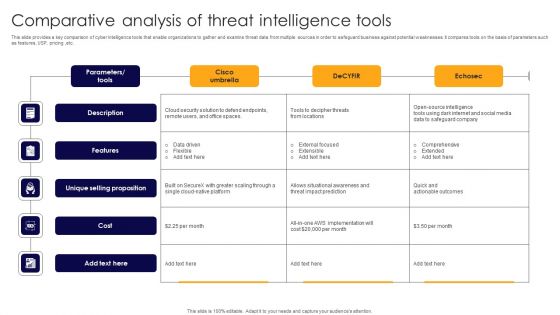
Comparative Analysis Of Threat Intelligence Tools Rules PDF
This slide provides a key comparison of cyber intelligence tools that enable organizations to gather and examine threat data from multiple sources in order to safeguard business against potential weaknesses. It compares tools on the basis of parameters such as features, USP, pricing ,etc. Showcasing this set of slides titled Comparative Analysis Of Threat Intelligence Tools Rules PDF. The topics addressed in these templates are Description, Features, Unique Selling Proposition. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
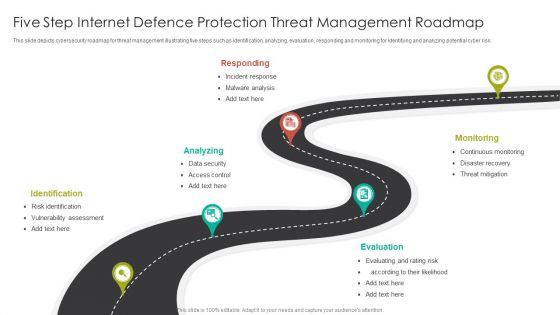
Five Step Internet Defence Protection Threat Management Roadmap Diagrams PDF
This slide depicts cybersecurity roadmap for threat management illustrating five steps such as identification, analyzing, evaluation, responding and monitoring for identifying and analyzing potential cyber risk.Persuade your audience using this Five Step Internet Defence Protection Threat Management Roadmap Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Analyzing, Responding. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Attack On Web Applications Ppt Outline Files PDF
This slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Presenting Cyber Security Attack On Web Applications Ppt Outline Files PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Password Attack, Session Hijacking Attacks, Eavesdropping Attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
RCA Action Plan For Business Cyber Security Icons PDF
This slide shows root cause analysis action plan to identify and provide strategies for overcoming cyber security threats. It include root cause, action plan and outcomes, etc. Showcasing this set of slides titled RCA Action Plan For Business Cyber Security Icons PDF Elements. The topics addressed in these templates are Root Cause, Action Plan, Outcomes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Core Competencies Of Internet Security Threat Portrait Pdf
This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.Showcasing this set of slides titled Core Competencies Of Internet Security Threat Portrait Pdf The topics addressed in these templates are Cyber Transformation, Cloud Computing, Financial Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Risk Icon Indicating Malware Attack Elements PDF
Presenting cyber risk icon indicating malware attack elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber risk icon indicating malware attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Content Cyber Terrorism Assault Rules Designs PDF
This is a table of content cyber terrorism assault rules designs pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment matrix of cyber terrorism, impact of implementing, dashboard for threat tracking You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
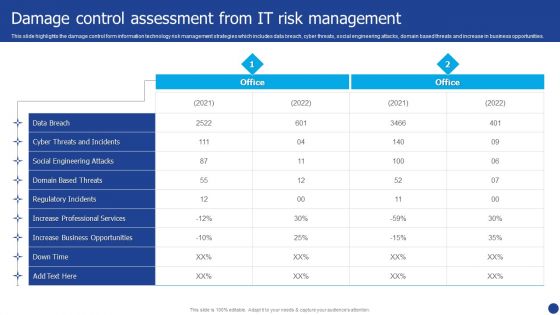
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
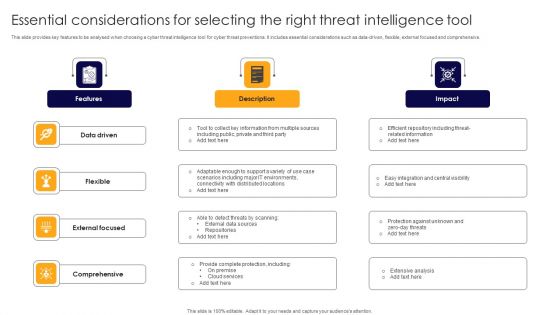
Essential Considerations For Selecting The Right Threat Intelligence Tool Themes PDF
This slide provides key features to be analysed when choosing a cyber threat intelligence tool for cyber threat preventions. It includes essential considerations such as data-driven, flexible, external focused and comprehensive. Presenting Essential Considerations For Selecting The Right Threat Intelligence Tool Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Driven, Flexible, External Focused. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
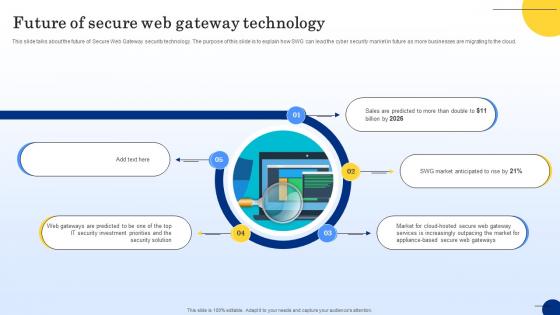
Future Of Secure Web Gateway Technology Web Threat Protection System
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Future Of Secure Web Gateway Technology Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cyber Risk Security Planning With Educate And Retest Stage Demonstration PDF
The following slide highlights the cyber threat security planning to minimize threats in organizations. It include six stages to deploy cyber threat to organization. Presenting cyber risk security planning with educate and retest stage demonstration pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including assess, choose, educate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
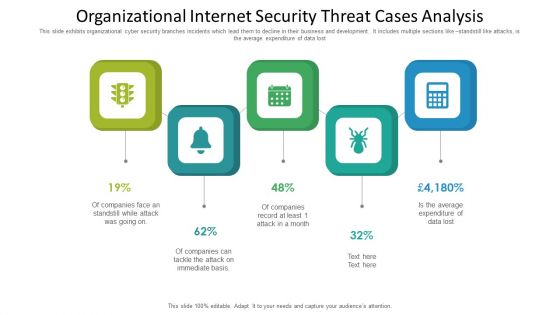
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
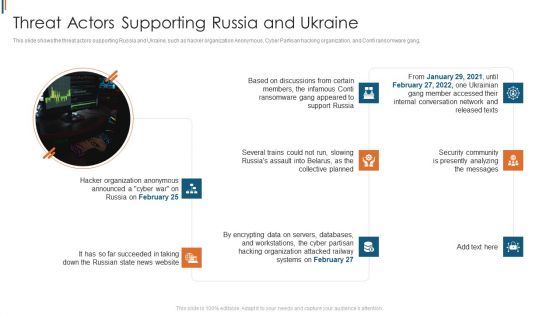
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
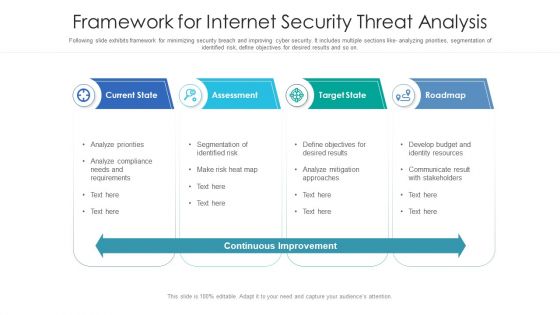
Framework For Internet Security Threat Analysis Structure PDF
Following slide exhibits framework for minimizing security breach and improving cyber security. It includes multiple sections like- analyzing priorities, segmentation of identified risk, define objectives for desired results and so on. Showcasing this set of slides titled framework for internet security threat analysis structure pdf. The topics addressed in these templates are current state, assessment, target state, roadmap. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
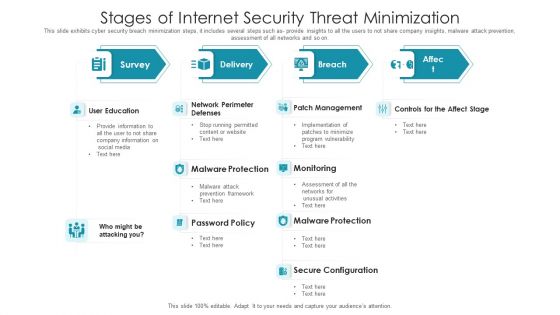
Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
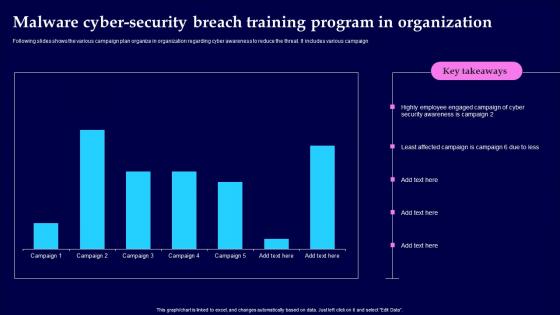
Malware Cyber Security Breach Training Program In Organization Designs Pdf
Following slides shows the various campaign plan organize in organization regarding cyber awareness to reduce the threat. It includes various campaign Pitch your topic with ease and precision using this Malware Cyber Security Breach Training Program In Organization Designs Pdf This layout presents information on Malware Cyber Security Breach, Training Program In Organization It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Steps For IT Infra Cyber Security Assessment Background PDF
The following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Presenting Steps For IT Infra Cyber Security Assessment Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Evaluation, Vulnerability Identification, Exposure Determination. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

How Chatgpt Can Help In Preventing Cyber Crimes Slides PDF
This slide demonstrates the various applications of ChatGPT in the field of cybersecurity. The purpose of this slide is to explain how ChatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Chatgpt Can Help In Preventing Cyber Crimes Slides PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
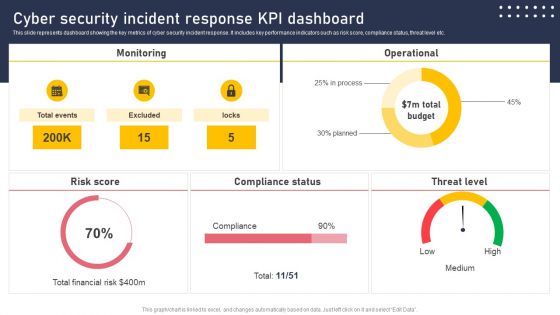
Cyber Security Incident Response KPI Dashboard Microsoft PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Slidegeeks has constructed Cyber Security Incident Response KPI Dashboard Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
Cyber Security Team Analytics Dashboard With KPI Metrics Icons PDF
The following slide shows cyber analytics dashboard to monitor and inspect threats and accordingly plan preventive actions. It includes open and resolved incidents and tickets. Pitch your topic with ease and precision using this Cyber Security Team Analytics Dashboard With KPI Metrics Icons PDF. This layout presents information on Energy Security Team, Digital Security Center, Security Operations Center. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Problems Management And Action Plan Microsoft PDF
The following slide illustrates the cyber security risk management plan to outline business security threats and draft proposed strategies. It also includes elements such as objectives, issues, breach response actions, employee training etc. Persuade your audience using this Cyber Security Problems Management And Action Plan Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Breach Response Actions, Employee Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
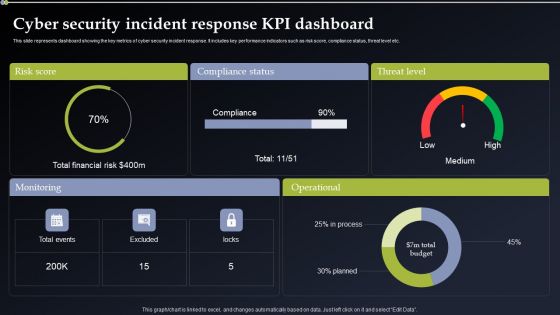
Cyber Security Incident Response KPI Dashboard Pictures PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Do you know about Slidesgeeks Cyber Security Incident Response KPI Dashboard Pictures PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
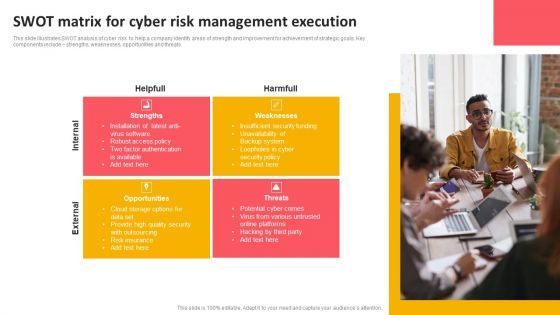
SWOT Matrix For Cyber Risk Management Execution Topics PDF
This slide illustrates SWOT analysis of cyber risk to help a company identify areas of strength and improvement for achievement of strategic goals. Key components include strengths, weaknesses, opportunities and threats. Presenting SWOT Matrix For Cyber Risk Management Execution Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strengths, Weaknesses, Opportunities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home