Cyber Threat
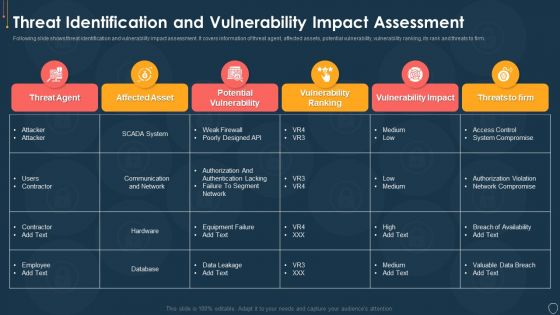
Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enhancing Cyber Safety With Vulnerability Administration Threat Intelligence Services Information PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. This is a enhancing cyber safety with vulnerability administration threat intelligence services information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global intelligence, local intelligence, other services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
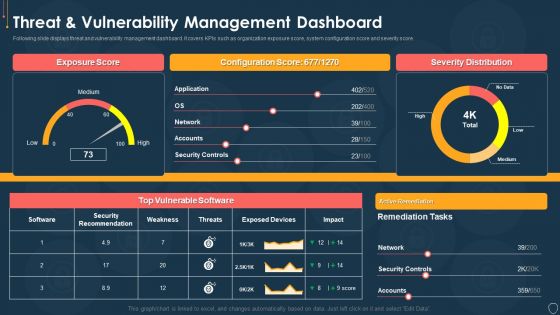
Cyber Security Risk Management Plan Threat And Vulnerability Management Dashboard Portrait PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat and vulnerability management dashboard portrait pdf. Use them to share invaluable insights on exposure score, configuration score, severity distribution, vulnerable software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Determine Threat Management Team Structure Professional PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a cyber safety incident management determine threat management team structure professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Emerging Threats In Cyber Security Ppt PowerPoint Presentation Model Images PDF
Presenting emerging threats in cyber security ppt powerpoint presentation model images pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including emerging threats in cyber security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF
The following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. This Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cyber Safety Incident Management Determine Several Threat Actors Profile Themes PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative cyber safety incident management determine several threat actors profile themes pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
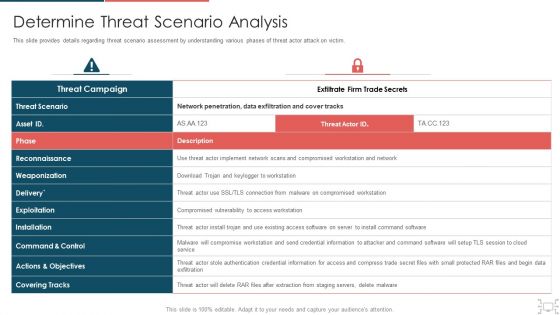
Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF
This slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Presenting Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Probe, Initial Attack, Expanded Attack, Data Lift. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

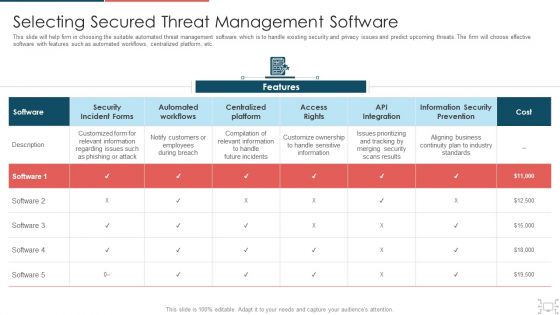
Cyber Safety Incident Management Selecting Secured Threat Management Software Information PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative cyber safety incident management selecting secured threat management software information pdf bundle. Topics like selecting secured threat management software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
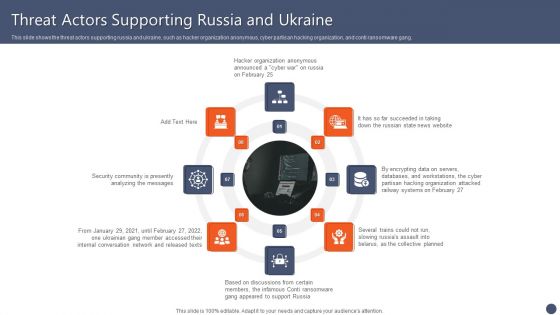
Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cyber Security Administration In Organization Determine Several Threat Actors Profile Sample PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization determine several threat actors profile sample pdf. Use them to share invaluable insights on determine several threat actors profile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF
The given slide provides the key activities to be done to alleviate the effects of cyber threats. It includes managing social media profiles, backing up the data, crosschecking privacy and security settings etc. Showcasing this set of slides titled Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF. The topics addressed in these templates are Concerned Areas, Social Media Profiles, Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
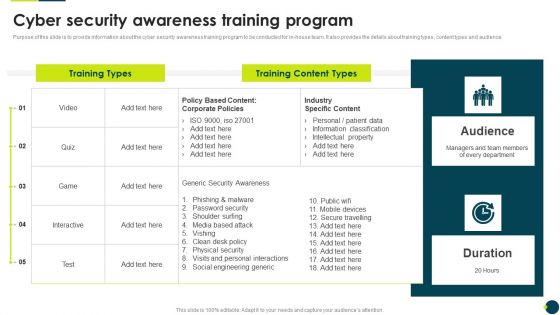
IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Safety Incident Management Impact Analysis For Effective Threat Management Structure PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. This is a cyber safety incident management impact analysis for effective threat management structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis for effective threat management in securing workplace. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
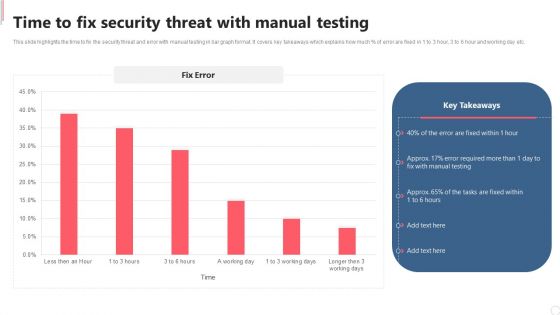
Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. This Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
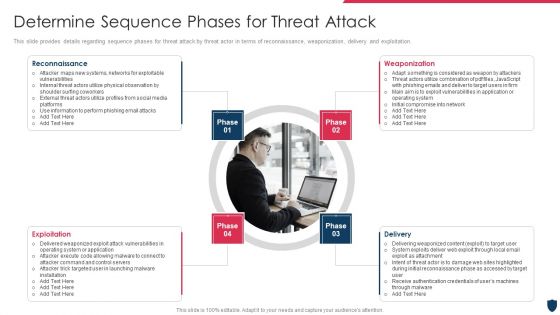
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Budget For Effective Threat Management At Workplace Structure PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative cyber security administration in organization budget for effective threat management at workplace structure pdf bundle. Topics like incident management, onboarding, process, release can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
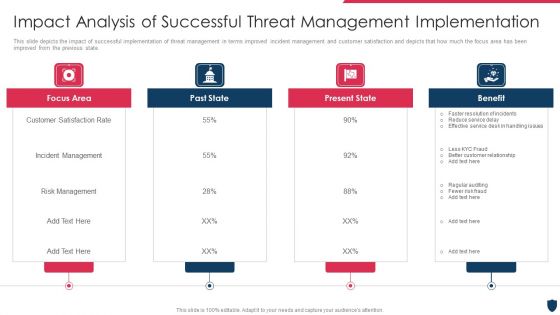
Cyber Safety Incident Management Impact Analysis Of Successful Threat Management Implementation Summary PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. This is a cyber safety incident management impact analysis of successful threat management implementation summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like focus area, past state, present state, benefit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
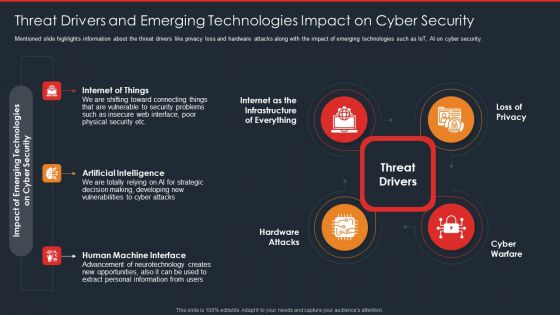
Data Safety Initiatives Threat Drivers And Emerging Technologies Impact On Cyber Security Brochure PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a data safety initiatives threat drivers and emerging technologies impact on cyber security brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat drivers, loss privacy, cyber warfare, hardware attacks, artificial intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
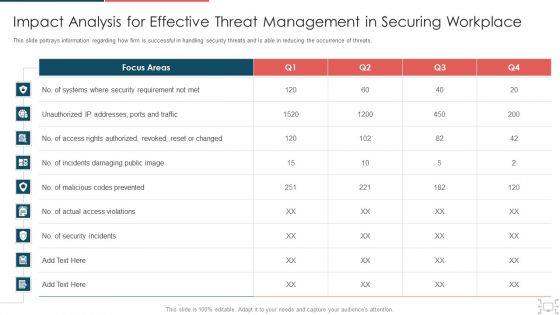
Cyber Security Administration In Organization Impact Analysis For Effective Threat Management Securing Rules PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative cyber security administration in organization impact analysis for effective threat management securing rules pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Drivers And Emerging Technologies Impact On Cyber Security Ppt Slides Graphic Images PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a threat drivers and emerging technologies impact on cyber security ppt slides graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, developing, strategic, opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
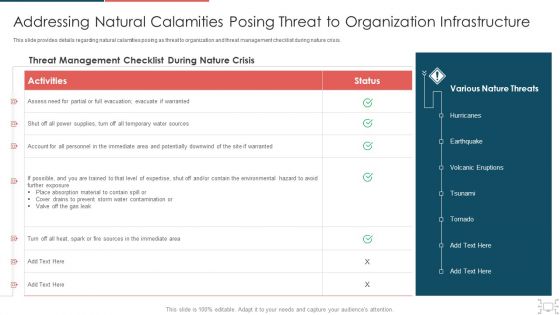
Cyber Security Administration In Organization Addressing Natural Calamities Posing Threat Sample PDF
This slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an awe inspiring pitch with this creative cyber security administration in organization addressing natural calamities posing threat sample pdf bundle. Topics like sources, evacuation, environmental, contamination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Comparative Assessment Of Various Threat Agents Infographics PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization comparative assessment of various threat agents infographics pdf. Use them to share invaluable insights on social engineering, operations, maintenance, redundancy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
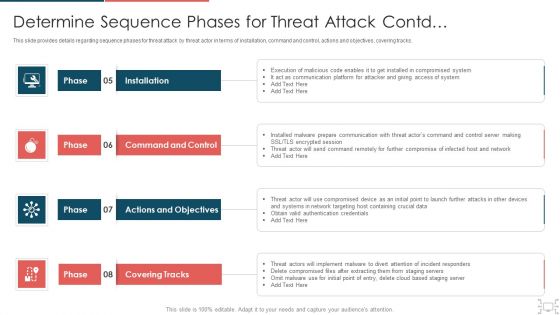
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
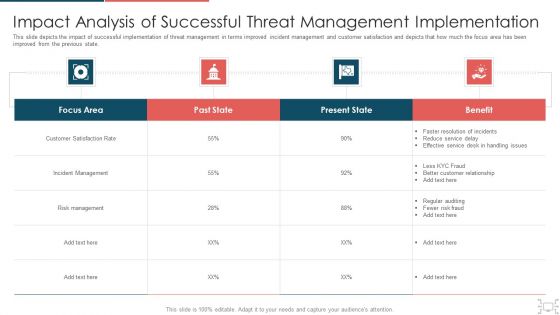
Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Threats Landscape Dashboard For Cyber Security Program Management Ppt Gallery Images PDF
This slide shows risk landscape dashboard for cyber security program management which contains threat level by month, current threat posture, threats by source, threats by owner, risks by threat and threat register. This can help businesses in effective management of risks and counter measures. Showcasing this set of slides titled Business Threats Landscape Dashboard For Cyber Security Program Management Ppt Gallery Images PDF. The topics addressed in these templates are Current Threat Posture, Threat Register, Source. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
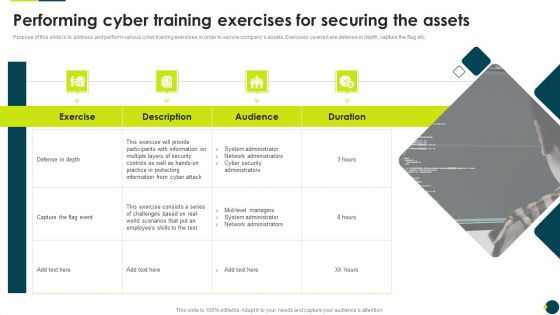
IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF
This slide illustrates risk landscape dashboard with cyber attacks analysis which contains malware attack frequency, country wise attacks, top 10 attacks, etc. It can assist IT managers in analyzing top threats so that they can be dealt with proper efficiency. Pitch your topic with ease and precision using this Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF. This layout presents information on Malware Attack Frequency, Every Minute, Every Second. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
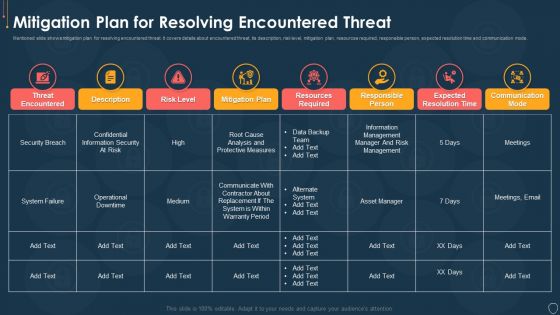
Cyber Security Risk Management Plan Mitigation Plan For Resolving Encountered Threat Pictures PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an awe inspiring pitch with this creative cyber security risk management plan mitigation plan for resolving encountered threat pictures pdf bundle. Topics like threat encountered, mitigation plan, responsible person, communication mode, risk level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
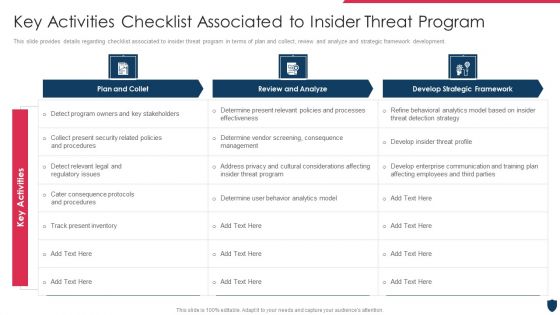
Cyber Safety Incident Management Key Activities Checklist Associated To Insider Threat Program Download PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver and pitch your topic in the best possible manner with this cyber safety incident management key activities checklist associated to insider threat program download pdf. Use them to share invaluable insights on plan and collet, review and analyze, develop strategic framework, key activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
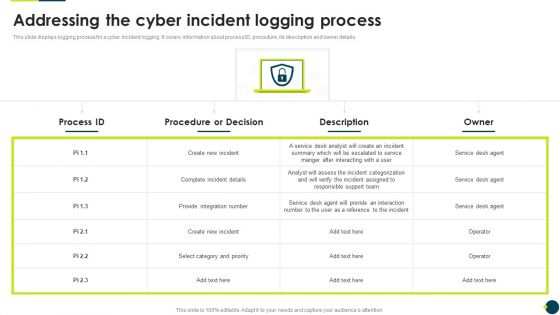
IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF. Use them to share invaluable insights on Provide Integration, Responsible Support, Assess The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Chart Showing Technology Threats Methods And Technology For Cyber Security Ppt PowerPoint Presentation Ideas Slideshow PDF
Presenting chart showing technology threats methods and technology for cyber security ppt powerpoint presentation ideas slideshow pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer security attributes, attack methods, technology for internet security, confidentiality, integrity, privacy, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Safety Incident Management Statistics Associated To Workplace Threats Elements PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver and pitch your topic in the best possible manner with this cyber safety incident management statistics associated to workplace threats elements pdf. Use them to share invaluable insights on cyber attacks costs, organizations, organizations have, organizations face, data records and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.Presenting IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Differential, Incremental, Differential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
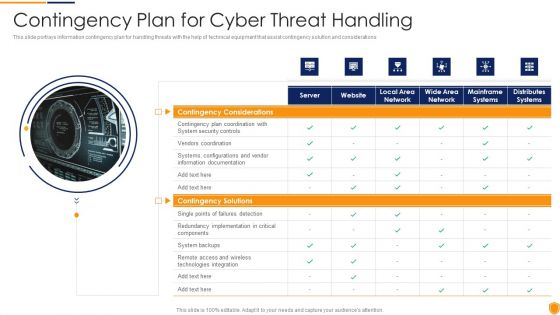
Mitigating Cybersecurity Threats And Vulnerabilities Contingency Plan For Cyber Infographics PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities contingency plan for cyber infographics pdf. Use them to share invaluable insights on contingency solutions, contingency considerations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
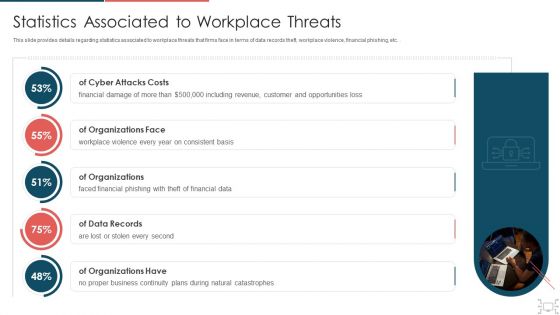
Cyber Security Administration In Organization Statistics Associated To Workplace Threats Microsoft PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc.. Deliver an awe inspiring pitch with this creative cyber security administration in organization statistics associated to workplace threats microsoft pdf bundle. Topics like organizations, consistent, financial, business, catastrophes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
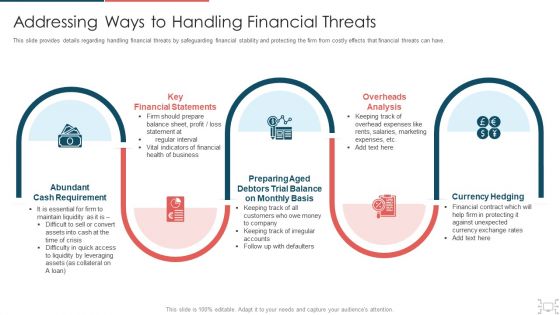
cyber security administration in organization addressing ways to handling financial threats summary pdf
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. This is a cyber security administration in organization addressing ways to handling financial threats summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, statements, requirement, preparing, balance . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Defining Categories Of Information Security Threats Structure PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. This is a cyber security risk management plan defining categories of information security threats structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like human error, natural disaster, environmental control failures, deliberate software attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
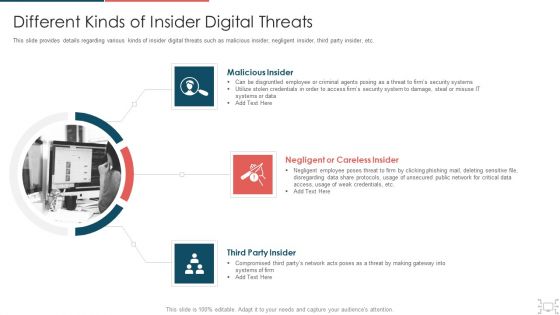
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Various Types Of Workplace Violence And Threats Infographics PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber safety incident management various types of workplace violence and threats infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stalking, physical assault, harassment or intimidation, property damage, weapon assault . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
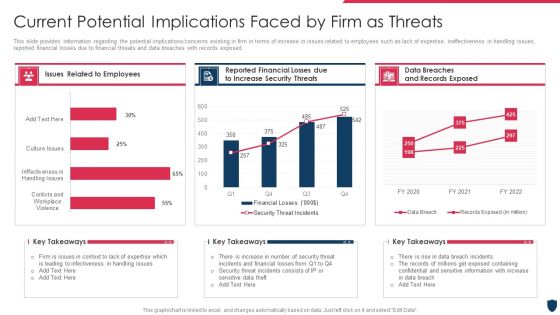
Cyber Safety Incident Management Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative cyber safety incident management current potential implications faced by firm as threats clipart pdf bundle. Topics like issues related to employees, data breaches and records exposed, reported financial losses due to increase security threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
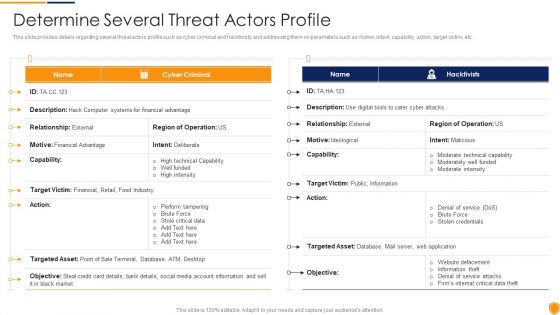
Mitigating Cybersecurity Threats And Vulnerabilities Determine Several Threat Structure PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities determine several threat structure pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Threat Intelligence Process Demonstration PDF
This slide depicts cyber threat intelligence process for improving the overall security posture of the organization, by providing actionable intelligence about the threats. It includes phases such as set, gather, analyse and act. Presenting Corporate Threat Intelligence Process Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fact Based Decision Making, Strategic Response Incidents, Collect Data System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF today and make your presentation stand out from the rest.
Building An Effective Threat Intelligence Framework Icons PDF
This slide showcases steps to create a framework for effective cyber threat intelligence that will help prevent firms from cyber threats. It includes steps such as scope definition, defines specific goals, cyber threat intelligence tools and continuous refinement. Presenting Building An Effective Threat Intelligence Framework Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Scope Definition, Define Specific Goals, Cyber Threat Intelligence Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
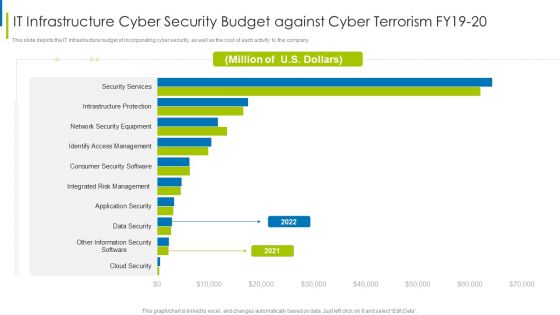
Cyber Terrorism Assault IT Infrastructure Cyber Security Budget Against Cyber Terrorism FY19 20 Themes PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault it infrastructure cyber security budget against cyber terrorism fy19 20 themes pdf Use them to share invaluable insights on cloud security, integrated risk management, identify access management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
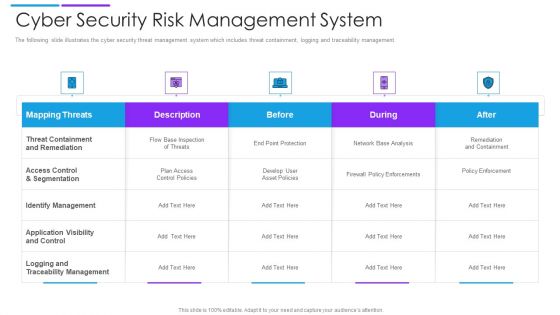
Cyber Security Risk Management System Microsoft PDF
The following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Pitch your topic with ease and precision using this cyber security risk management system microsoft pdf. This layout presents information on mapping threats, threat containment and remediation, identify management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
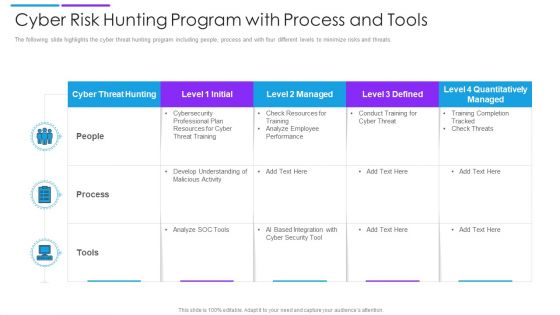
Cyber Risk Hunting Program With Process And Tools Elements PDF
The following slide highlights the cyber threat hunting program including people, process and with four different levels to minimize risks and threats. Showcasing this set of slides titled cyber risk hunting program with process and tools elements pdf. The topics addressed in these templates are cyber threat hunting, quantitatively managed, cyber threat training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Threat Management At Workplace Determine Several Threat Actors Profile Ideas Pdf
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative threat management at workplace determine several threat actors profile ideas pdf bundle. Topics like hacktivists, cyber criminal, moderate intensity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home