Cyber Security Operations

Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
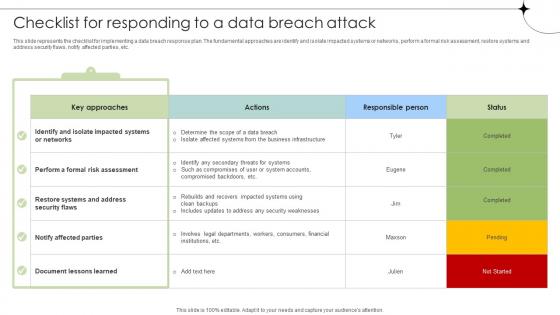
Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
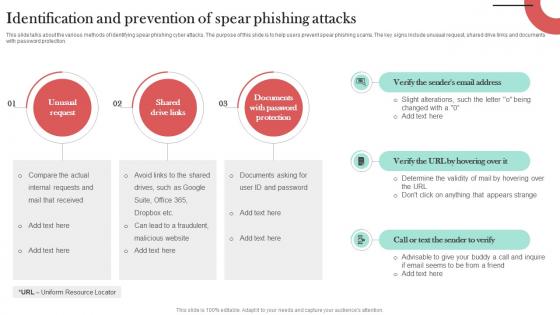
Identification And Prevention Of Spear Man In The Middle Phishing IT
This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Presenting this PowerPoint presentation, titled Identification And Prevention Of Spear Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Identification And Prevention Of Spear Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Identification And Prevention Of Spear Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
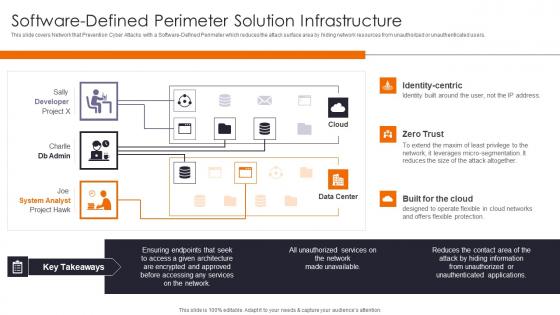
Software Defined Perimeter Enhancing Workload Efficiency Through Cloud Architecture Pictures Pdf
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Present like a pro with Software Defined Perimeter Enhancing Workload Efficiency Through Cloud Architecture Pictures Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Iot Device Management Overview And Requirements Iot Device Management Rules Pdf
This slide exhibits an overview and needs of IoT device management to protect confidential information from potential breaches. It covers the increase in the number of cyber attacks, data breaches attack, etc. Get a simple yet stunning designed Iot Device Management Overview And Requirements Iot Device Management Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Iot Device Management Overview And Requirements Iot Device Management Rules Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
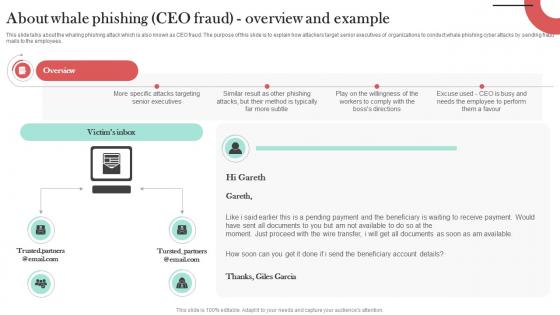
About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT
This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Find highly impressive About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
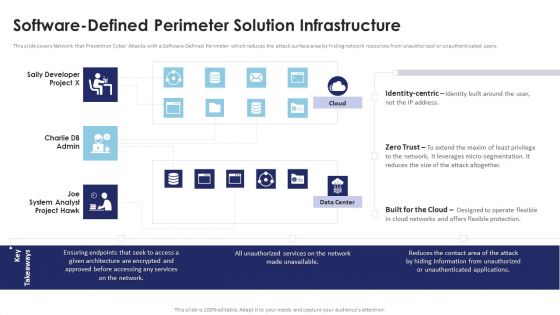
Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Are you searching for a Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF from Slidegeeks today.
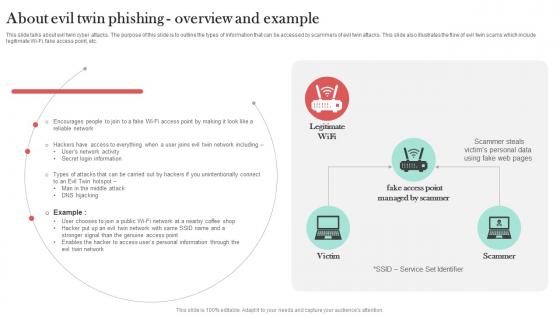
About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
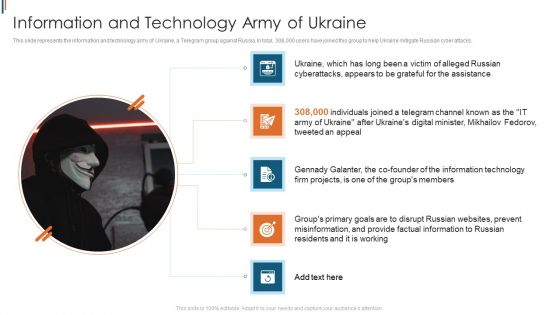
Ukraine Cyberwarfare Information And Technology Army Of Ukraine Topics Pdf
This slide represents the information and technology army of Ukraine, a Telegram group against Russia. In total, 308,000 users have joined this group to help Ukraine mitigate Russian cyber attacks. Presenting ukraine cyberwarfare information and technology army of ukraine topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like ukraine, which has long been a victim of alleged russian cyberattacks, appears to be grateful for the assistance, gennady galanter, the co founder of the information technology firm projects, is one of the groups members. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
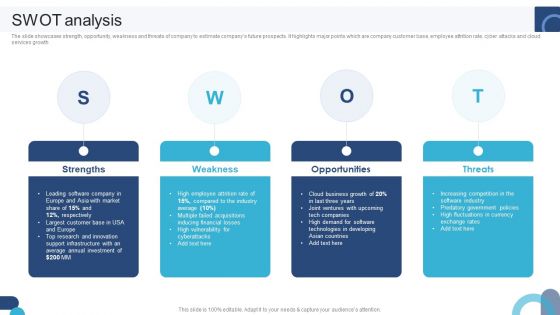
Digital Application Software Development Business Profile SWOT Analysis Structure PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth This Digital Application Software Development Business Profile SWOT Analysis Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Digital Products Company Outline SWOT Analysis Diagrams PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Find highly impressive Digital Products Company Outline SWOT Analysis Diagrams PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Products Company Outline SWOT Analysis Diagrams PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

About Pharming Phishing Identification Man In The Middle Phishing IT
This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give About Pharming Phishing Identification Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable About Pharming Phishing Identification Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Reverse Proxy Web Server Impacts Of Reverse Proxy Web Server Application Inspiration PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Reverse Proxy Web Server Impacts Of Reverse Proxy Web Server Application Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
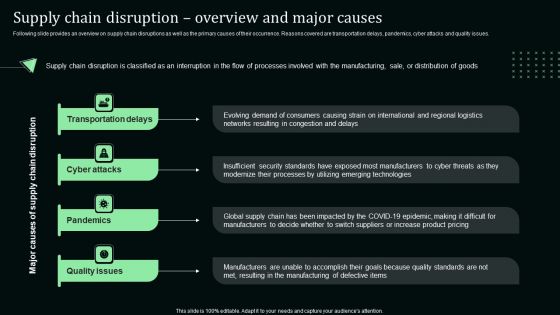
Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF

Strategies For Dynamic Supply Chain Agility Supply Chain Disruption Overview And Major Causes Template PDF
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues. Get a simple yet stunning designed Strategies For Dynamic Supply Chain Agility Supply Chain Disruption Overview And Major Causes Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Strategies For Dynamic Supply Chain Agility Supply Chain Disruption Overview And Major Causes Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues. If you are looking for a format to display your unique thoughts, then the professionally designed Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
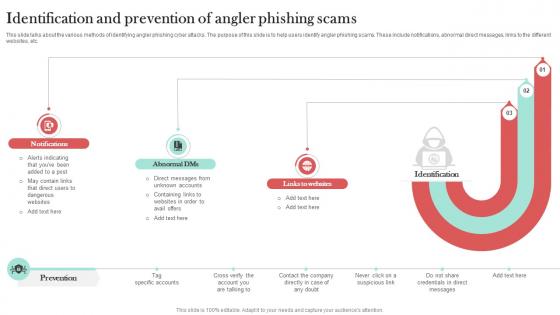
Identification And Prevention Of Angler Man In The Middle Phishing IT
This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Slidegeeks has constructed Identification And Prevention Of Angler Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
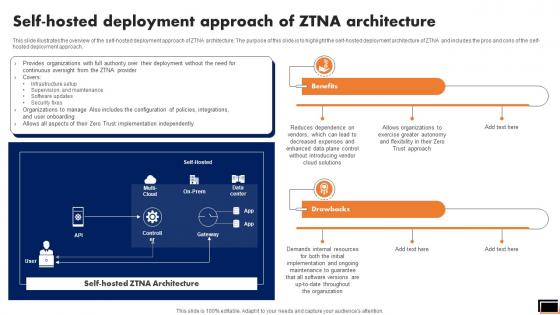
Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Do you know about Slidesgeeks Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF
This slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF
The following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber-attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Get a simple yet stunning designed Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. If you are looking for a format to display your unique thoughts, then the professionally designed IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Web Consulting Business Assessment Of Monthly Actual Spending On Modification
Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management. Present like a pro with Web Consulting Business Assessment Of Monthly Actual Spending On Modification. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Managing Technical And Non Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. Explore a selection of the finest Managing Technical And Non Estimated Annual Budget Plan For Web Company here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Managing Technical And Non Estimated Annual Budget Plan For Web Company to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
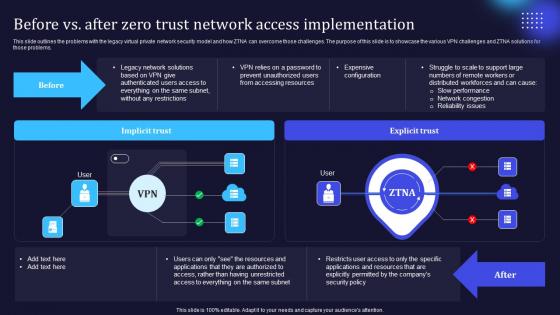
Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
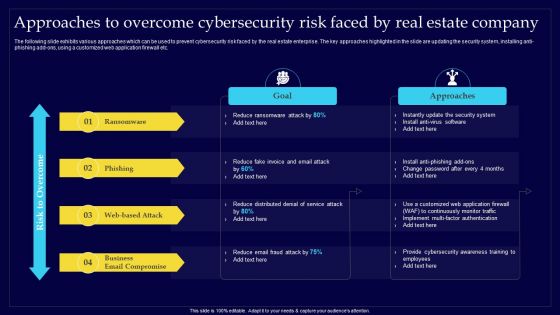
Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Create an editable Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF
This slide represents the companys IT policy implementation budget for FY2022. It covers the details of the software application and security services that need to be purchased and updated. This Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Business Model Paubox Capital Funding Pitch Deck Download Pdf
This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Business Model Paubox Capital Funding Pitch Deck Download Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Business Model Paubox Capital Funding Pitch Deck Download Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
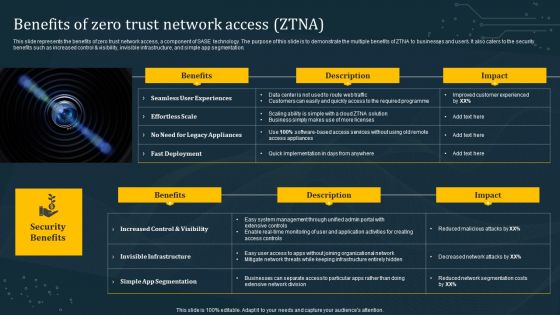
Benefits Of Zero Trust Network Access ZTNA Download PDF
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Present like a pro with Benefits Of Zero Trust Network Access ZTNA Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
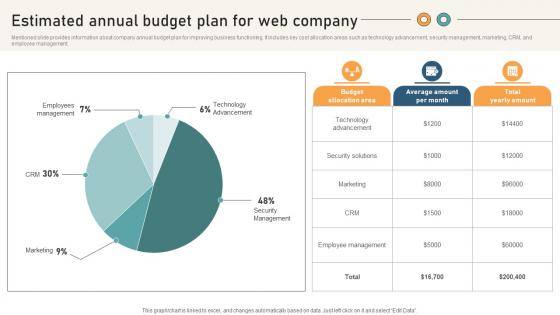
Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company.

WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF
This slide represents the steps to be considered by organizations to maximize the benefits of WAF. The purpose of this slide is to showcase the best practices businesses can consider for successful web application firewall implementation, such as support for app security goals, evaluation and testing, and resource listing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
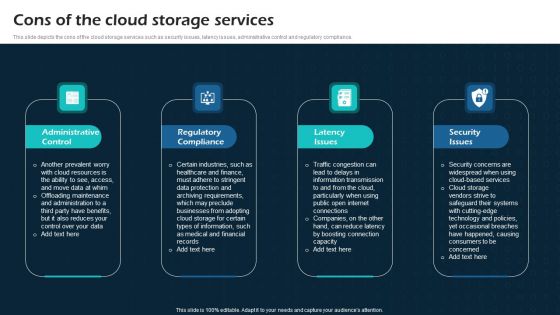
Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF
This slide depicts the cons of the cloud storage services such as security issues, latency issues, administrative control and regulatory compliance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Benefits Of Zero Trust Network Access ZTNA Ppt Layouts Example PDF
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Benefits Of Zero Trust Network Access ZTNA Ppt Layouts Example PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Existing Products And Service Offerings Of Firm Stakeholder Engagement Plan For Launch Event Ideas PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Take your projects to the next level with our ultimate collection of Existing Products And Service Offerings Of Firm Stakeholder Engagement Plan For Launch Event Ideas PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.
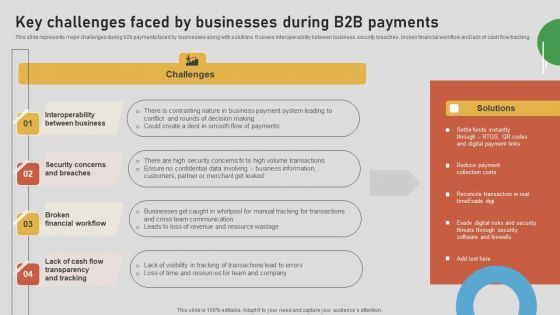
Introduction To B2B Online Shopping Payment Options Key Challenges Faced By Businesses Formats PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. This modern and well arranged Introduction To B2B Online Shopping Payment Options Key Challenges Faced By Businesses Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

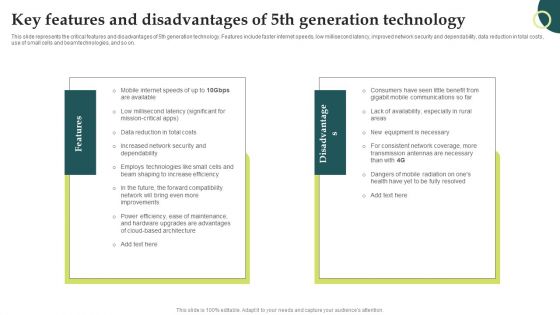
Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
Evolution Of Wireless Technologies Key Features And Disadvantages Of 5Th Generation Structure PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Evolution Of Wireless Technologies Key Features And Disadvantages Of 5Th Generation Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
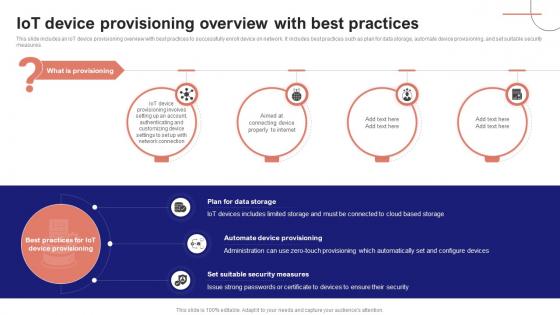
IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT Ss V
This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V can be your best option for delivering a presentation. Represent everything in detail using IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Guidelines To Successfully Develop Flexible Work Policy Professional PDF
The following slide showcases important instructions related to the work from home WFH policy that can assist corporates to draft rules and regulations for remote employees. It contains information about security protocols, online meeting etiquette, expenditure, and team building activities. Welcome to our selection of the Guidelines To Successfully Develop Flexible Work Policy Professional PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Implementing Adaptive Work Arrangements Guidelines To Successfully Develop Flexible Work Policy Pictures PDF
The following slide showcases important instructions related to the work from home WFH policy that can assist corporates to draft rules and regulations for remote employees. It contains information about security protocols, online meeting etiquette, expenditure, and team building activities. This modern and well arranged Implementing Adaptive Work Arrangements Guidelines To Successfully Develop Flexible Work Policy Pictures PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

WAF Features And Capabilities Ppt Pictures Designs Download PDF
This slide represents the capabilities and characteristics of a Web Application Firewall security solution. This slide aims to showcase the various features of WAF, including AI-powered traffic patterns, attack signature databases, application profiling, customization, correlation engines, and so on. Slidegeeks has constructed WAF Features And Capabilities Ppt Pictures Designs Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

WAF Features Monitoring Introduction Ppt Outline Example Topics PDF
This slide represents the overview of Web Application Firewall monitoring. The purpose of this slide is to give the outline of WAF monitoring and its working flow. The components include a security center, alerts, application gateway, WAF, event hubs, log analytics, and storage. Presenting this PowerPoint presentation, titled WAF Features Monitoring Introduction Ppt Outline Example Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this WAF Features Monitoring Introduction Ppt Outline Example Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable WAF Features Monitoring Introduction Ppt Outline Example Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
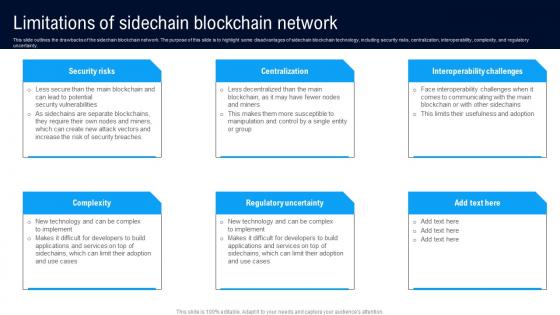
Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf
This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
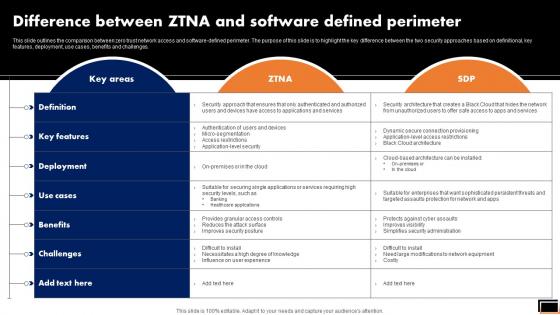
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

IT Application Services Company Outline Case Study Software Development Infographics PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting IT Application Services Company Outline Case Study Software Development Infographics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Layered Security, Implemented, Developed Web. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. Presenting Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Tracking Products, Securing Operations, Managing Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Is Iot Significant In Overall Logistics Sample PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. This is a How Is Iot Significant In Overall Logistics Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking Products, Securing Operations, Managing Vehicles. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home