Cyber Security Operations
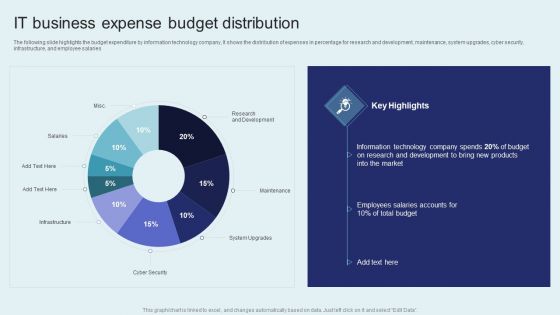
IT Firm Financial Statement IT Business Expense Budget Distribution Pictures PDF
The following slide highlights the budget expenditure by information technology company, It shows the distribution of expenses in percentage for research and development, maintenance, system upgrades, cyber security, infrastructure, and employee salaries. There are so many reasons you need a IT Firm Financial Statement IT Business Expense Budget Distribution Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
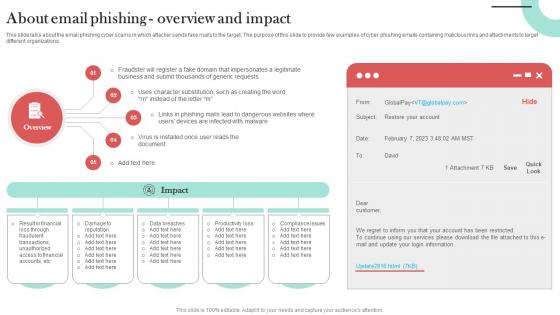
About Email Phishing Overview And Impact Man In The Middle Phishing IT
This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Create an editable About Email Phishing Overview And Impact Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Email Phishing Overview And Impact Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
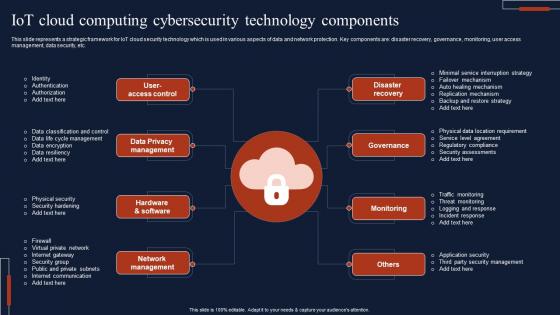
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Project Management Calendar With Duration Ppt Show Graphics Example PDF
This slide focuses on the project management timeline which covers miscellaneous tasks, corporate marketing and operations with research and development project, event invite, strategic plans, company brochure, email newsletters, social media campaign, etc. Showcasing this set of slides titled Business Project Management Calendar With Duration Ppt Show Graphics Example PDF. The topics addressed in these templates are Miscellaneous Task, Corporate Marketing, Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf
This slide represents the process checklist in order to develop web applications. It further includes activities such as design, UX, SEO checks, readability checks, performance checks, security checks, etc. Showcasing this set of slides titled Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf. The topics addressed in these templates are Readability Checks, Performance Checks, Security Checks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
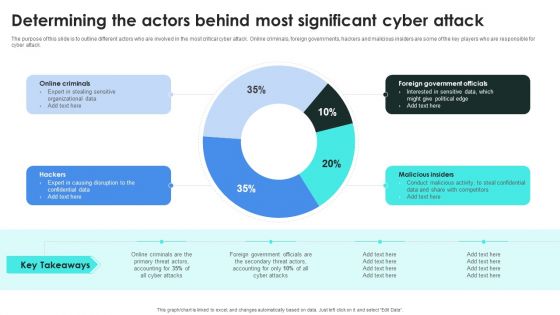
Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Web App Firewall Services IT Features Of WAF Protection Against The OWASP Vulnerabilities Graphics PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a web app firewall services it features of waf protection against the owasp vulnerabilities graphics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, data exposure, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major 5G Protection And Privacy Challenges Themes PDF
The following slide highlights the top safety and protection challenges in 5G network to safeguard sensitive data from hackers. It includes elements such as architecture, security and encryption, location and data privacy etc. Presenting Major 5G Protection And Privacy Challenges Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Privacy, Location Privacy, Security And Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Roles And Responsibilities Of Risk Management Team Cybersecurity Risk Assessment Infographics PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roles And Responsibilities Of Risk Management Team Cybersecurity Risk Assessment Infographics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Growth Of Ethical Hacking Profession Ppt Infographic Template Templates PDF
This slide represents the growth of the ethical hacking profession, including annual salary, hiring companies, and designation such as information security officer, computer forensics engineer, ethical hacker, and network security engineer. Deliver and pitch your topic in the best possible manner with this growth of ethical hacking profession ppt infographic template templates pdf. Use them to share invaluable insights on growth of ethical hacking profession and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
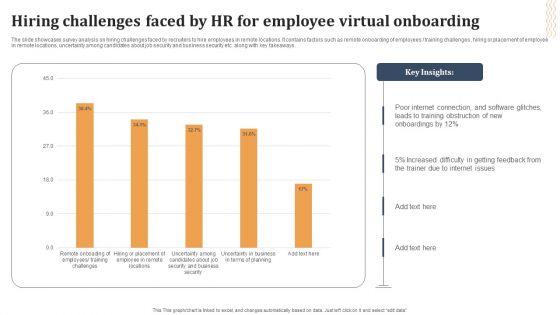
Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF
The slide showcases survey analysis on hiring challenges faced by recruiters to hire employees in remote locations. It contains factors such as remote onboarding of employees training challenges , hiring or placement of employee in remote locations, uncertainty among candidates about job security and business security etc. along with key takeaways. Showcasing this set of slides titled Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF. The topics addressed in these templates are Internet Connection, Software Glitches, Internet Issues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Open Source WAF Features Ppt Portfolio Influencers PDF
This slide represents the characteristics of an open-source Web Application Firewall. The purpose of this slide is to give an overview of the primary features of open-source WAF, including continuous passive security assessment, real-time application security monitoring, full HTTP traffic logging, and web application hardening. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Open Source WAF Features Ppt Portfolio Influencers PDF from Slidegeeks and deliver a wonderful presentation.

Preventive Measures For Man In The Middle Man In The Middle Phishing IT
This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Get a simple yet stunning designed Preventive Measures For Man In The Middle Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Preventive Measures For Man In The Middle Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Data Breach Prevention Recognition Problem Faced By The Organization Elements PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a data breach prevention recognition problem faced by the organization elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, organization, problem, security awareness, training programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. Presenting Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Service Availability, Security Assurance, Secured Identities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
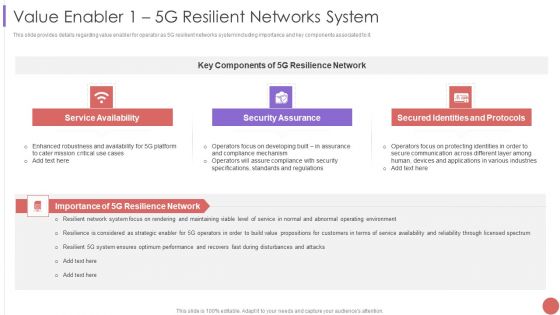
Value Enabler 1 5G Resilient Networks System Professional PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Value Enabler 1 5G Resilient Networks System Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Availability, Security Assurance, Secured Identities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Terrorism Attack Trends Post Russia Ukraine War Graphics PDF
This slides shows cyber attack trends on different countries post Russia-Ukraine War. It include countries such as Russia, Ukraine, United States etc. Pitch your topic with ease and precision using this Digital Terrorism Attack Trends Post Russia Ukraine War Graphics PDF. This layout presents information on Organization, Digital Terrorism Attack Trends. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

About Spear Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Spear Phishing Overview And Example Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Spear Phishing Overview And Example Man In The Middle Phishing IT today and make your presentation stand out from the rest
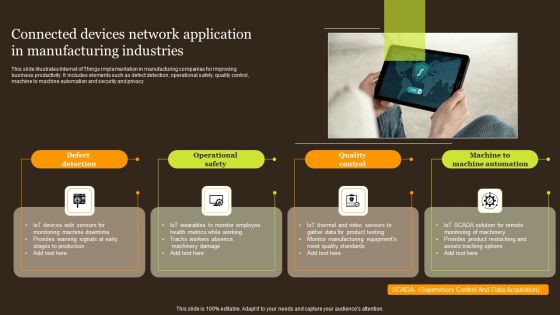
Connected Devices Network Application In Manufacturing Industries Portrait PDF
This slide illustrates Internet of Things implementation in manufacturing companies for improving business productivity. It includes elements such as defect detection, operational safety, quality control, machine to machine automation and security and privacy. Presenting Connected Devices Network Application In Manufacturing Industries Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Defect Detection, Operational Safety, Quality Control . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Software Defined Perimeter Solution Infrastructure Elements PDF
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Deliver an awe inspiring pitch with this creative Software Defined Perimeter Solution Infrastructure Elements PDF bundle. Topics like System Analyst, Services, Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IOT Authorization And Authentication For Cybersecurity Management Sample Pdf
This slide provides multiple authorization protocols that helps businesses and organizations to ensure effective and secure management of operations and data transmission. The three protocols are one-way, two-way, and three-way authentication. Showcasing this set of slides titled IOT Authorization And Authentication For Cybersecurity Management Sample Pdf The topics addressed in these templates are One Way Authentication, Two Way Authentication All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
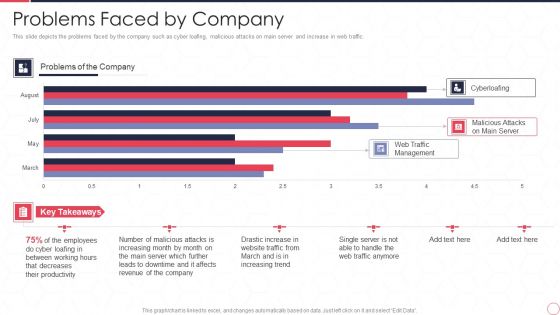
Reverse Proxy Server IT Problems Faced By Company Ppt Summary Inspiration PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic. Deliver and pitch your topic in the best possible manner with this reverse proxy server it problems faced by company ppt summary inspiration pdf. Use them to share invaluable insights on web traffic management, malicious attacks on main server, cyberloafing, employee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
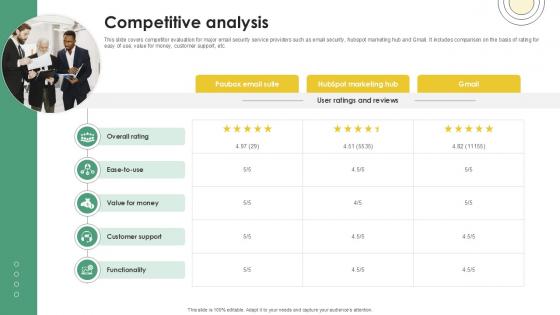
Competitive Analysis Email And Data Protection Platform Capital Funding Pitch Deck PPT Example
This slide covers competitor evaluation for major email security service providers such as email security, hubspot marketing hub and Gmail. It includes comparison on the basis of rating for easy of use, value for money, customer support, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Competitive Analysis Email And Data Protection Platform Capital Funding Pitch Deck PPT Example a try. Our experts have put a lot of knowledge and effort into creating this impeccable Competitive Analysis Email And Data Protection Platform Capital Funding Pitch Deck PPT Example. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
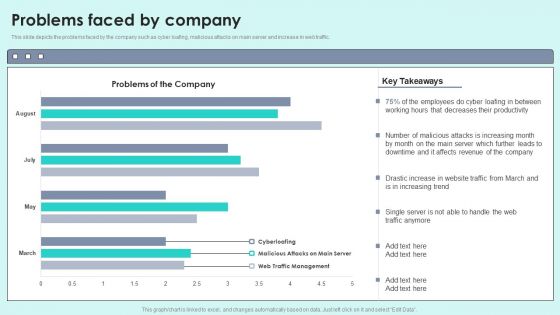
Problems Faced By Company Reverse Proxy For Load Balancing Designs PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic.Deliver and pitch your topic in the best possible manner with this Problems Faced By Company Reverse Proxy For Load Balancing Designs PDF. Use them to share invaluable insights on Decreases Productivity, Malicious Attacks, Affects Revenue and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
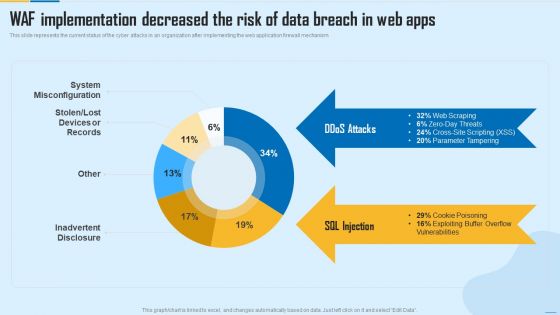
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Key Ways Of Incident Response Planning With Human Observations Ppt PowerPoint Presentation File Sample PDF
Persuade your audience using this key ways of incident response planning with human observations ppt powerpoint presentation file sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including physical alarm, cyber attack, human observations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Redundant Array Of Independent Disks Storage IT Checklist To Implement RAID In Business Formats PDF
This slide depicts the checklist to implement RAID in business describing guidelines to follow while implementing RAID. Deliver an awe inspiring pitch with this creative redundant array of independent disks storage it checklist to implement raid in business formats pdf bundle. Topics like organization, implement, cyber attacks, budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
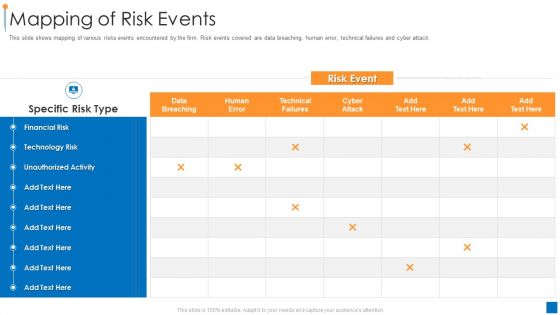
International Organization Standardization 270001 Mapping Of Risk Events Slides PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative international organization standardization 270001 mapping of risk events slides pdf bundle. Topics like financial risk, technology risk, unauthorized activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Statistics Associated To Workplace Threats Summary PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver an awe inspiring pitch with this creative threat management at workplace statistics associated to workplace threats summary pdf bundle. Topics like cyber attacks costs, organization, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
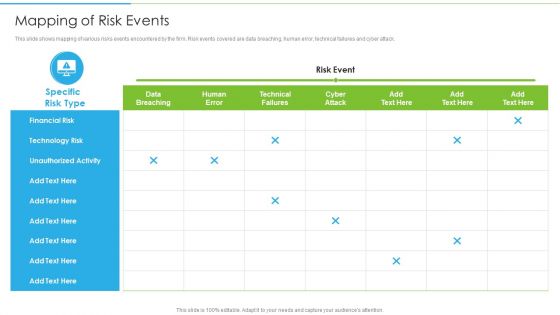
Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF bundle. Topics like Financial Risk, Technology Risk, Unauthorized Activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
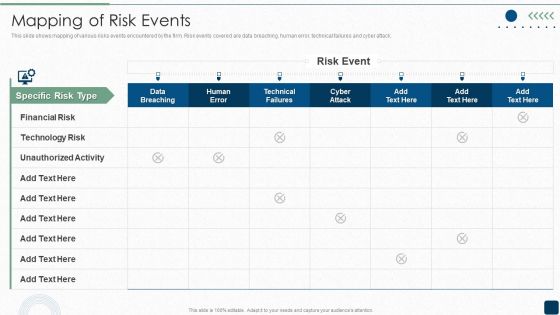
Mapping Of Risk Events Infographics PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative Mapping Of Risk Events Infographics PDF bundle. Topics like Financial Risk, Unauthorized Activity, Technology Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF bundle. Topics like Unauthorized Activity, Technology Risk, Financial Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
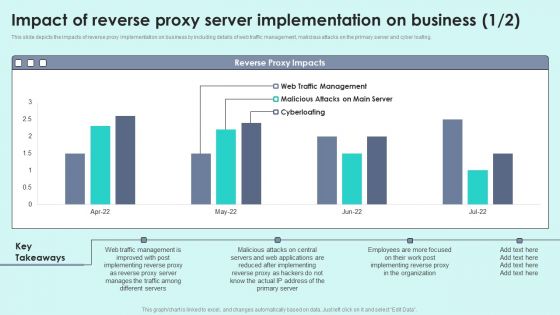
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing.Deliver an awe inspiring pitch with this creative Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF bundle. Topics like After Implementing, Manages Traffic, Different Servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF bundle. Topics like Organization Systems, Networks, Internal can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
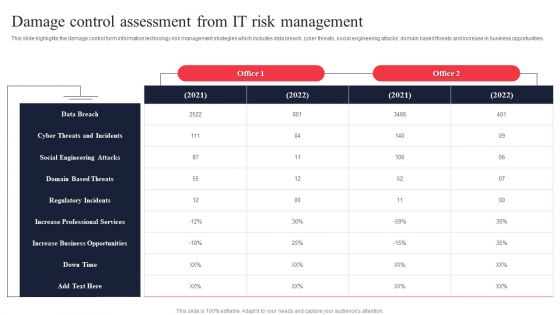
IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
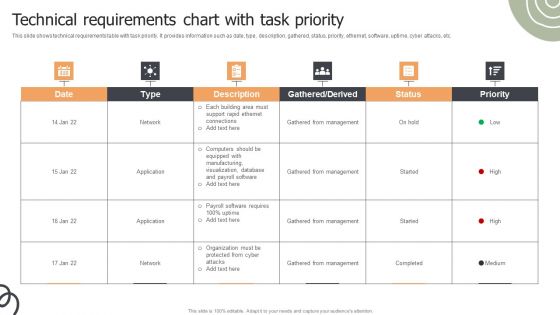
Technical Requirements Chart With Task Priority Ppt Infographics Styles PDF
This slide shows technical requirements table with task priority. It provides information such as date, type, description, gathered, status, priority, ethernet, software, uptime, cyber attacks, etc. Pitch your topic with ease and precision using this Technical Requirements Chart With Task Priority Ppt Infographics Styles PDF. This layout presents information on Gathered From Management, Network, Application. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Digital Terrorism Types And Categories With Examples Sample PDF
This slide shows various categories of cyber terrorism attacks according to their severity . It include categories such as simple unstructured, advance structured, complex coordinated etc. Showcasing this set of slides titled Digital Terrorism Types And Categories With Examples Sample PDF. The topics addressed in these templates are Advance Structured, Complex Coordinated, Simple Unstructured. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Consultancy Services Company Profile Offers Diverse Range Of Products Rules PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a IT Consultancy Services Company Profile Offers Diverse Range Of Products Rules PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Parts Accessories, Computer Repair. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Solutions Business Profile Offers Diverse Range Of Products Themes PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a Information Technology Solutions Business Profile Offers Diverse Range Of Products Themes PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Productivity Applications, Parts Accessories. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Small Business Venture Company Profile Offers Diverse Range Of Products Clipart PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a Small Business Venture Company Profile Offers Diverse Range Of Products Clipart PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Advanced Monitoring, Management Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Technology Ppt Business Intelligence And Big Data In Cloud
This is a technology ppt business intelligence and big data in cloud. This is a four stage process. The stages in this process are better, quicker business decision making, views of business operations and performance, historical, current, predictive, performance management, bench marking, predictive analytics, data mining, internal data, sales return, web email, finance, product analysis, industry analysis, social analysis.

Reverse Proxy Server IT Why To Use Reverse Proxy Server Ppt Gallery Good PDF
This slide depicts why to use reverse proxy servers, including control over cyber loafing, bandwidth saving, privacy benefits, security, and access to blocked resources. Presenting reverse proxy server it why to use reverse proxy server ppt gallery good pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like employees, privacy benefits, advanced security, access to blocked, resources and websites. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Analysis For Phishing Attacks Awareness Training Tools Rules PDF
This slide covers comparative analysis for phishing awareness training tools for effective decision making. It involves features such simulate top cyber attacks, assess employees, monitor and analyse results and measurable impact. Showcasing this set of slides titled Comparative Analysis For Phishing Attacks Awareness Training Tools Rules PDF. The topics addressed in these templates are Analyse Results, Measurable Impact, Living Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Industry Transformation Approaches Banking Sector Employee Development Top Digital Industry Trends Of Banking Mockup PDF
This slide shows some of the top digital industry trends in banking that are most widely adopted such as seamless payments, next gen and digital banks, mobile applications, robotics process automation and ai artificial intelligence, cybersecurity etc. This is a industry transformation approaches banking sector employee development top digital industry trends of banking mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like seamless payments, mobile applications, cyber security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Supplier Performance Assessment Based On Procurement Risks Ppt PowerPoint Presentation File Slides PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Present like a pro with Supplier Performance Assessment Based On Procurement Risks Ppt PowerPoint Presentation File Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Technological Change Management Training Plan Introduction Of New Technology Ppt PowerPoint Presentation File Backgrounds PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. There are so many reasons you need a Technological Change Management Training Plan Introduction Of New Technology Ppt PowerPoint Presentation File Backgrounds PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Quantum Key Distribution Applications Of Quantum Computing Background PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc.This is a Quantum Key Distribution Applications Of Quantum Computing Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Artificial Intelligence, Design And Development, Cybersecurity And Cryptography You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
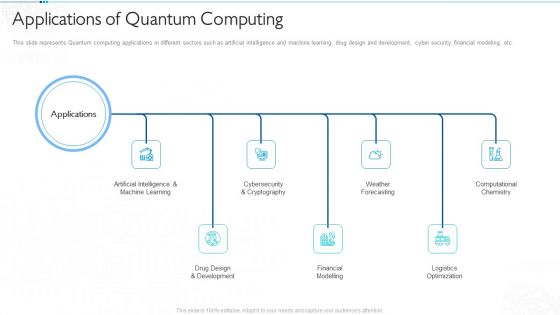
Quantum Computing For Everyone IT Applications Of Quantum Computing Infographics PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc. Presenting quantum computing for everyone it applications of quantum computing infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like artificial intelligence and machine learning, drug design and development, financial modelling, weather forecasting, logistics optimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Applications Of Quantum Computing Ppt Pictures Templates PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc. This is a Applications Of Quantum Computing Ppt Pictures Templates PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Financial Modelling, Weather Forecasting, Logistics Optimization, Computational Chemistry. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Applications Of Quantum Computing Ppt Professional Format PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc. This is a Applications Of Quantum Computing Ppt Professional Format PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Financial Modelling, Logistics Optimization, Applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Assurance, Service Availability, Protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why ESO System Center Is Required Ppt PowerPoint Presentation File Skills PDF
This slide covers need of enterprise security operation center. It involves reasons such as continuous monitoring, centralized visibility, reduced cybersecurity costs and ensures better collaboration. Presenting Why ESO System Center Is Required Ppt PowerPoint Presentation File Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Continuous Monitoring, Centralized Visibility, Reduced Cybersecurity Costs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

ESO System Center Best Practices Ppt PowerPoint Presentation File Structure PDF
This slide covers enterprise security operation center best practices. It involves practices such as setting up right time, align strategy with business goals, leverage best tools and continuously monitor network. Presenting ESO System Center Best Practices Ppt PowerPoint Presentation File Structure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Practices, Leverage Best Tools, Continuously Monitor Network. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Services And Consulting Company Profile Offers Diverse Range Of Products Themes PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a IT Services And Consulting Company Profile Offers Diverse Range Of Products Themes PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Parts And Accessories, Business Management Software, Advanced Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home