Application Security

Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
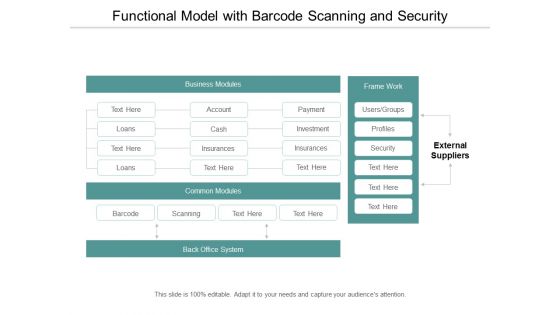
Functional Model With Barcode Scanning And Security Ppt Powerpoint Presentation Layouts Design Ideas
This is a functional model with barcode scanning and security ppt powerpoint presentation layouts design ideas. This is a four stage process. The stages in this process are functional architecture, functional planning, functional designing.
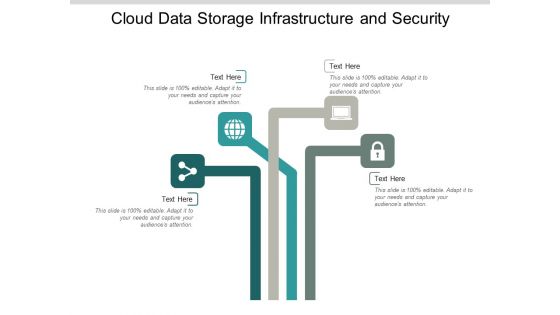
Cloud Data Storage Infrastructure And Security Ppt Powerpoint Presentation Model Show
This is a cloud data storage infrastructure and security ppt powerpoint presentation model show. This is a four stage process. The stages in this process are data management, data centre, storage system.

Recent Global Security Market Trends Behavior Marketing Ppt PowerPoint Presentation Model Slideshow
This is a recent global security market trends behavior marketing ppt powerpoint presentation model slideshow. This is a six stage process. The stages in this process are business, management, marketing.

RPA Operating Model With Security And Compliance Ppt PowerPoint Presentation Model Styles PDF
Presenting rpa operating model with security and compliance ppt powerpoint presentation model styles pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including strategy leadership and organizational fit, organizational enablement and change, deployment and operations, security and compliance, technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
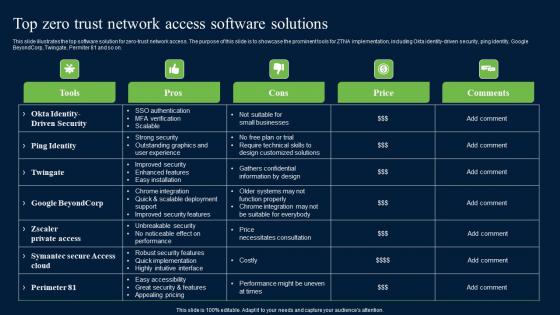
Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
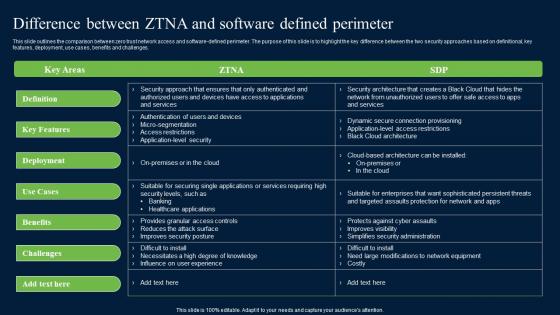
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
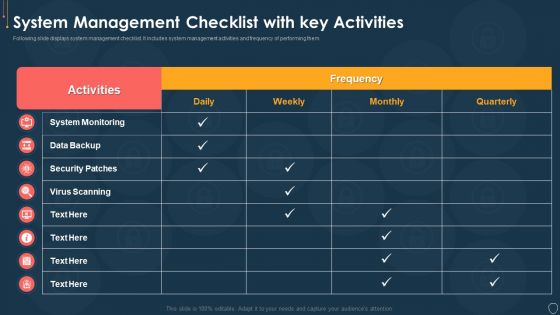
Cyber Security Risk Management Plan System Management Checklist With Key Activities Structure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative cyber security risk management plan system management checklist with key activities structure pdf bundle. Topics like system monitoring, data backup, security patches, virus scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Impact On Security Infrastructure Structure PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this effective it risk management process impact on security infrastructure structure pdf. Use them to share invaluable insights on target, risk, performance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
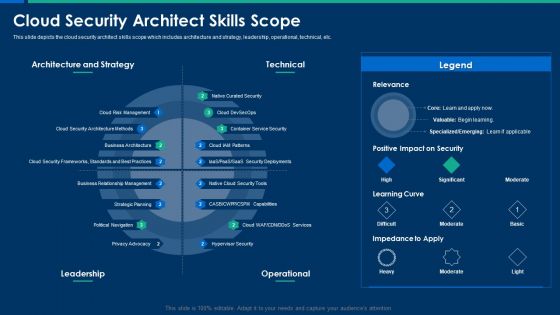
CIO Role In Digital Evolution Cloud Security Architect Skills Scope Structure PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational, technical, etc. Deliver and pitch your topic in the best possible manner with this CIO Role In Digital Evolution Cloud Security Architect Skills Scope Structure PDF. Use them to share invaluable insights on Architecture Strategy, Risk Management, Business Architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
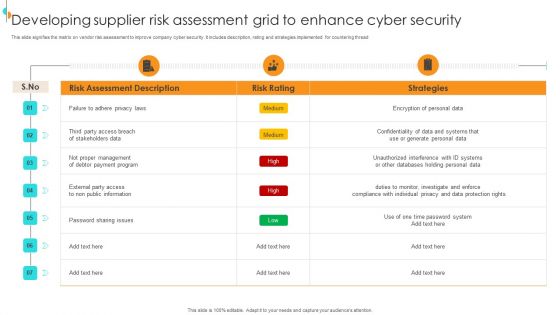
Developing Supplier Risk Assessment Grid To Enhance Cyber Security Structure PDF

Big Data Security Model With Identity And Access Management Ppt PowerPoint Presentation Inspiration Good PDF
Pitch your topic with ease and precision using this big data security model with identity and access management ppt powerpoint presentation inspiration good pdf. This layout presents information on identity and access management, data protection and privacy, infrastructure security and integrity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
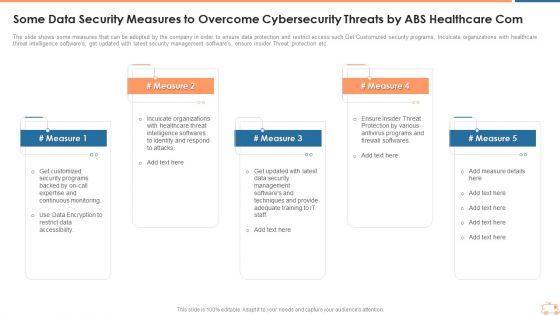
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
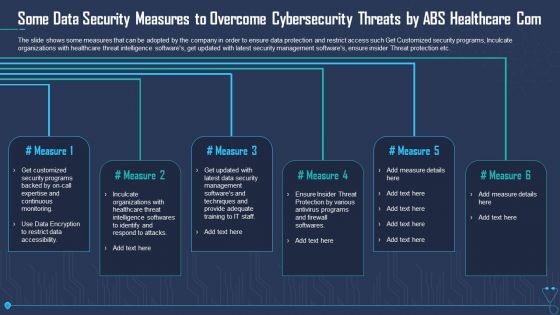
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
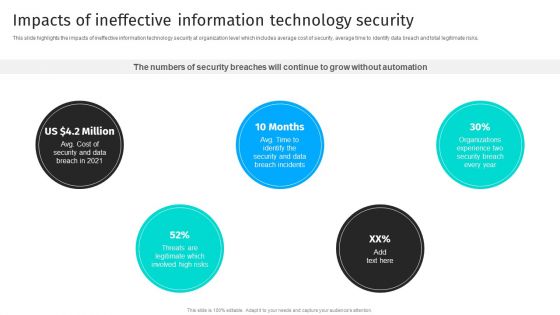
Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks.If you are looking for a format to display your unique thoughts, then the professionally designed Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security Master Reference Data Model Ppt PowerPoint Presentation Gallery Example File Cpb Pdf
Presenting this set of slides with name security master reference data model ppt powerpoint presentation gallery example file cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like security master reference data model to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vector For Cloud Computing And Security Model Icon Ppt PowerPoint Presentation Icon Samples PDF
Persuade your audience using this vector for cloud computing and security model icon ppt powerpoint presentation icon samples pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector for cloud computing and security model icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Risk Mitigation Strategy Model Icon With Security Shield Symbol Ppt PowerPoint Presentation Icon Inspiration PDF
Persuade your audience using this risk mitigation strategy model icon with security shield symbol ppt powerpoint presentation icon inspiration pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including risk mitigation strategy model icon with security shield symbol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Technology Trends Ppt PowerPoint Presentation Model Graphics Download Cpb
Presenting this set of slides with name cyber security technology trends ppt powerpoint presentation model graphics download cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber security technology trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
E Commerce Cyber Security Threats Ppt PowerPoint Presentation Model Maker Cpb
Presenting this set of slides with name e commerce cyber security threats ppt powerpoint presentation model maker cpb. This is an editable Powerpoint three stages graphic that deals with topics like e commerce cyber security threats to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Big Data Security Market Overview Ppt PowerPoint Presentation Model Sample Cpb
Presenting this set of slides with name big data security market overview ppt powerpoint presentation model sample cpb. This is an editable Powerpoint five stages graphic that deals with topics like big data security market overview to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Small Medium Business Cyber Security ICS Ppt PowerPoint Presentation Model Inspiration Cpb
Presenting this set of slides with name small medium business cyber security ics ppt powerpoint presentation model inspiration cpb. This is an editable Powerpoint four stages graphic that deals with topics like small medium business cyber security ics to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Innovation Tech Insights Security Operations Ppt PowerPoint Presentation Model Slideshow Cpb
Presenting this set of slides with name innovation tech insights security operations ppt powerpoint presentation model slideshow cpb. This is an editable Powerpoint four stages graphic that deals with topics like innovation tech insights security operations to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Cyber Security Vs Data Science Ppt PowerPoint Presentation Model Infographics Cpb
Presenting this set of slides with name cyber security vs data science ppt powerpoint presentation model infographics cpb. This is an editable Powerpoint three stages graphic that deals with topics like cyber security vs data science to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Security Testing Tools Cloud Computing Ppt PowerPoint Presentation Model Example File Cpb Pdf
Presenting this set of slides with name security testing tools cloud computing ppt powerpoint presentation model example file cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like security testing tools cloud computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Technology Overview Cloud Access Security Ppt PowerPoint Presentation Model Ideas Cpb Pdf
Presenting this set of slides with name technology overview cloud access security ppt powerpoint presentation model ideas cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like technology overview cloud access security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Global Cloud Based Email Security Market Key Stats Ppt Model Design Inspiration PDF
Presenting this set of slides with name global cloud based email security market key stats ppt model design inspiration pdf. This is a five stage process. The stages in this process are 25 percent companies have stand alone security department, 95 percent of malware are delivered via e mails. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Assessment Template Ppt PowerPoint Presentation Model Background Designs Cpb Pdf
Presenting this set of slides with name security assessment template ppt powerpoint presentation model background designs cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like security assessment template to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Risk Assessment Checklist Ppt PowerPoint Presentation Model Good Cpb Pdf
Presenting this set of slides with name security risk assessment checklist ppt powerpoint presentation model good cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like security risk assessment checklist to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Corporate International Security Guidelines Vector Icon Ppt PowerPoint Presentation Model Example Introduction PDF
Persuade your audience using this corporate international security guidelines vector icon ppt powerpoint presentation model example introduction pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including corporate international security guidelines vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

United States Marine Officers Port Security Officers On Patrol 01 Ppt PowerPoint Presentation Model Good PDF
Pitch your topic with ease and precision using this united states marine officers port security officers on patrol 01 ppt powerpoint presentation model good pdf. This layout presents information on united states marine officers port security officers on patrol 01. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Guard With Surveillance System Vector Icon Ppt PowerPoint Presentation File Model PDF
Persuade your audience using this security guard with surveillance system vector icon ppt powerpoint presentation file model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security guard with surveillance system vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Employee Engagement Model With Recognition And Security Ppt File Templates PDF
Persuade your audience using this employee engagement model with recognition and security ppt file templates pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including recognition, exciting work, security, education, conditions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF bundle. Topics like System Monitoring, Data Backup, Security Patches, Virus Scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Table Of Contents Brochure PDF
This is a Risk Management Model For Data Security Table Of Contents Brochure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing Risks, Defining Risk Level, Setting Scenario, Security Control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
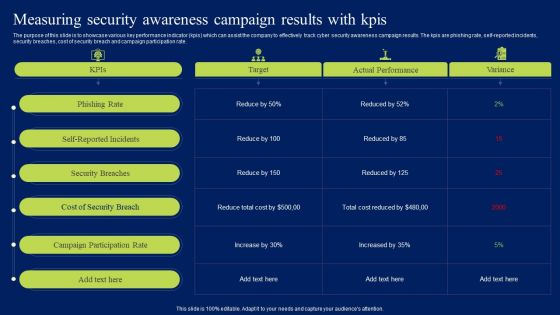
Measuring Security Awareness Campaign Results With Kpis Ppt Summary Sample PDF
The purpose of this slide is to showcase various key performance indicator kpis which can assist the company to effectively track cyber security awareness campaign results. The kpis are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. This modern and well-arranged Measuring Security Awareness Campaign Results With Kpis Ppt Summary Sample PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Staff Background PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security operations implementation timeline staff background pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
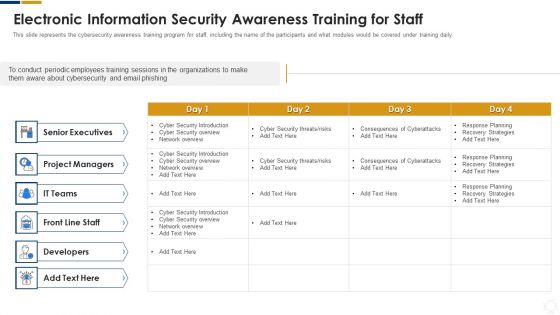
Cybersecurity Electronic Information Security Awareness Training For Staff Ppt Layouts Deck PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative cybersecurity electronic information security awareness training for staff ppt layouts deck pdf bundle. Topics like project managers, developers, senior executives, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Construction Management Services And Action Plan Interdependence Resiliency And Security Portrait PDF
Presenting construction management services and action plan interdependence resiliency and security portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, dimensions of infrastructure security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Utilizing Infrastructure Management Using Latest Methods Interdependence Resiliency And Security Themes PDF
This is a utilizing infrastructure management using latest methods interdependence resiliency and security themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical infrastructure dependencies and interdependencies assessment framework, infrastructure resilience wheel, lifecycle adaptive components resilience framework, dimensions infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Infrastructure As A Service Iaas Ppt Ideas Information PDF
This slide represents the responsibilities under the IaaS model, it also shows the different advantages of the IaaS model along with its downsides. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Infrastructure As A Service Iaas Ppt Ideas Information PDF. Use them to share invaluable insights on Cloud Security, Organizations Experience, IaaS Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.
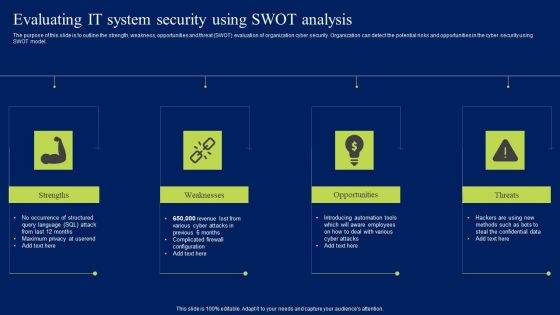
Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

IT Development Company Pitch Deck Problems Faced By Companies Security Introduction PDF
This is a it development company pitch deck problems faced by companies security introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poor network security, backup issues, software concerns, qualified experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Security Solutions Budget For Effective Secops System Management Rules PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this organizational security solutions budget for effective secops system management rules pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Budget For Effective Secops System Management Brochure PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security and process integration budget for effective secops system management brochure pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
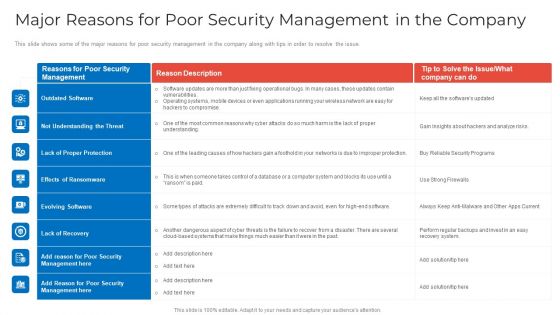
Major Reasons For Poor Security Management In The Company Topics PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company topics pdf bundle. Topics like outdated software, lack of proper protection, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
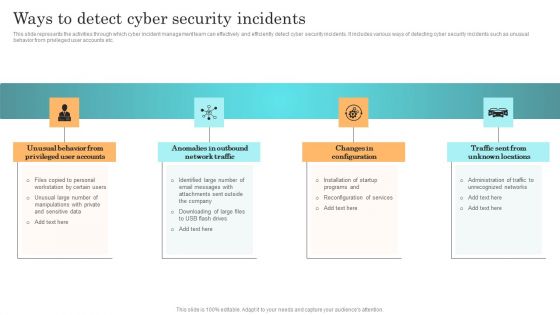
Incident Response Techniques Deployement Ways To Detect Cyber Security Incidents Infographics PDF

Global Cyber Terrorism Incidents On The Rise IT Timeline For Implementation Of Cyber Security Download PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it timeline for implementation of cyber security download pdf. Use them to share invaluable insights on business, network, perform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Construction Engineering And Industrial Facility Management Interdependence Resiliency And Security Graphics PDF
This is a construction engineering and industrial facility management interdependence resiliency and security graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determining Firm Current Capabilities In Managing Mobile Devices Mobile Device Security Management Summary PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Deliver and pitch your topic in the best possible manner with this Determining Firm Current Capabilities In Managing Mobile Devices Mobile Device Security Management Summary PDF. Use them to share invaluable insights on Asset Management, Critical Infrastructure, Recovering Capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Determining Firm Current Capabilities In Managing Business Mobile Device Security Management Graphics PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Find a pre-designed and impeccable Determining Firm Current Capabilities In Managing Business Mobile Device Security Management Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Advantages Of Cloud Computing With Flexibility And Security Ppt PowerPoint Presentation Portfolio Format PDF
Presenting this set of slides with name advantages of cloud computing with flexibility and security ppt powerpoint presentation portfolio format pdf. This is a eight stage process. The stages in this process are flexibility, disaster recovery, automatic software updates, pay as you go, increased collaboration, document control, security, location independent. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
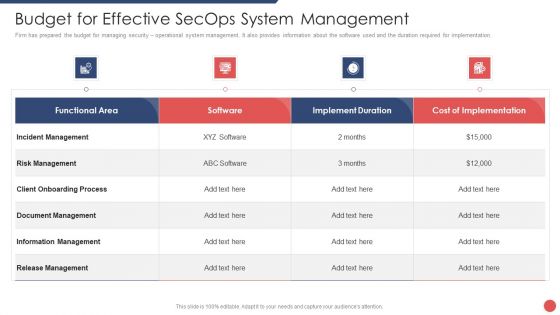
Security Functioning Centre Budget For Effective Secops System Management Formats PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security functioning centre budget for effective secops system management formats pdf. Use them to share invaluable insights on incident management, risk management, client onboarding process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
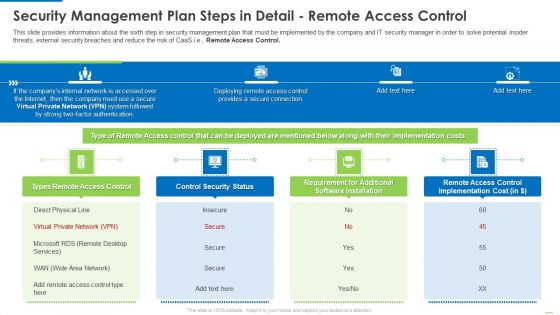
Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home