Application Security
Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V
If you are looking for a format to display your unique thoughts, then the professionally designed Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
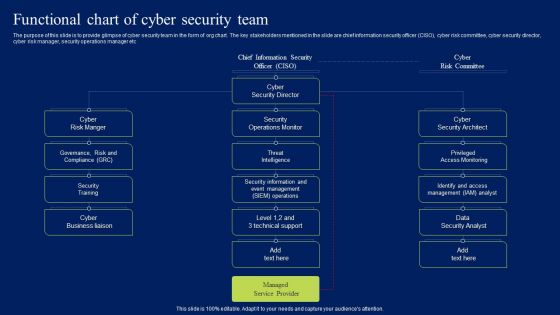
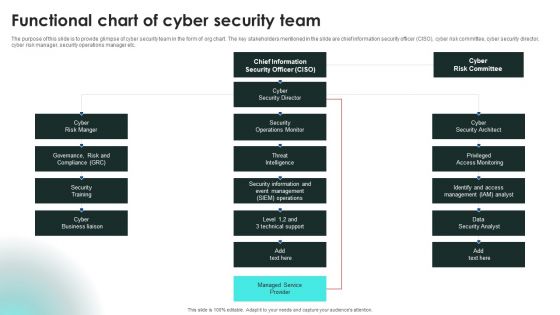
Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Get a simple yet stunning designed Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
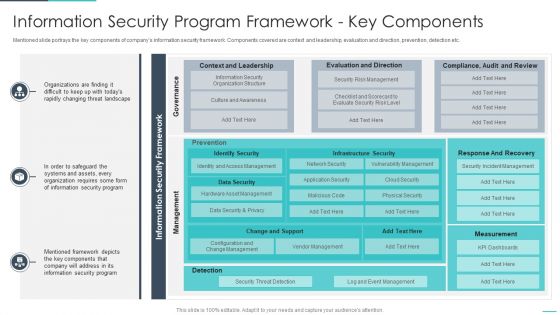
Handling Cyber Threats Digital Era Information Security Program Framework Ppt Model Summary PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era information security program framework ppt model summary pdf. Use them to share invaluable insights on information security program framework key components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
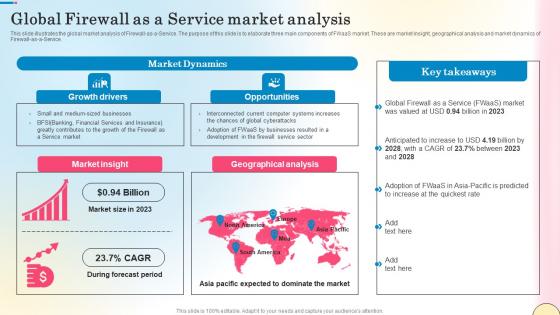
Global Firewall As A Service Market Analysis Network Security Pictures Pdf
This slide illustrates the global market analysis of Firewall-as-a-Service. The purpose of this slide is to elaborate three main components of FWaaS market. These are market insight, geographical analysis and market dynamics of Firewall-as-a-Service. This modern and well-arranged Global Firewall As A Service Market Analysis Network Security Pictures Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Supply Chain Management Strategy To Provide Layered Security Across Networks Brochure PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Strategy To Provide Layered Security Across Networks Brochure PDF. Use them to share invaluable insights on Formulate Network, Access Rules, Particular Applications, Bandwidth Access Limitation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Supply Chain Management Iot Security Lock For Safe Fleet Management Download PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Iot Security Lock For Safe Fleet Management Download PDF. Use them to share invaluable insights on Key Applications, Potential Impact, Multiple Positioning Methods and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
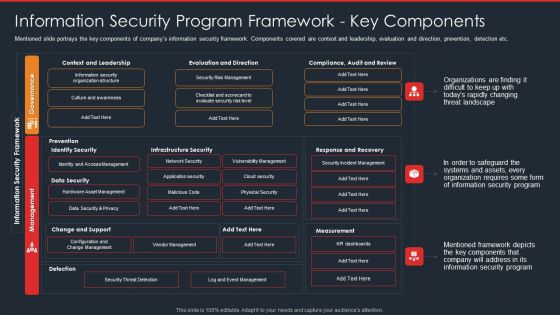
Data Safety Initiatives Information Security Program Framework Key Components Diagrams PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this data safety initiatives information security program framework key components diagrams pdf. Use them to share invaluable insights on governance, management, context and leadership, evaluation and direction, infrastructure security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
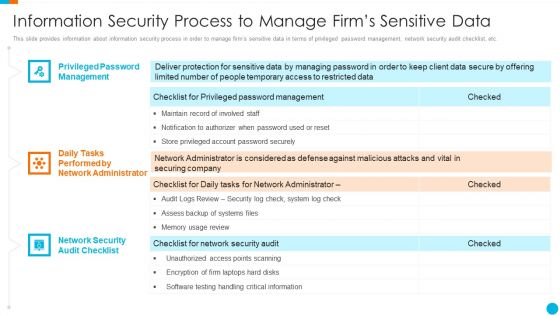
Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V
This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players. If you are looking for a format to display your unique thoughts, then the professionally designed Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
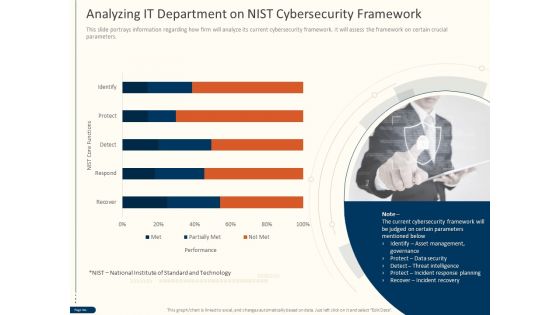
Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
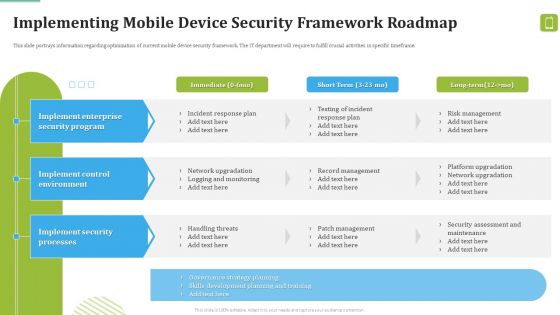
MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF bundle. Topics like Implement Enterprise, Security Program, Implement Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
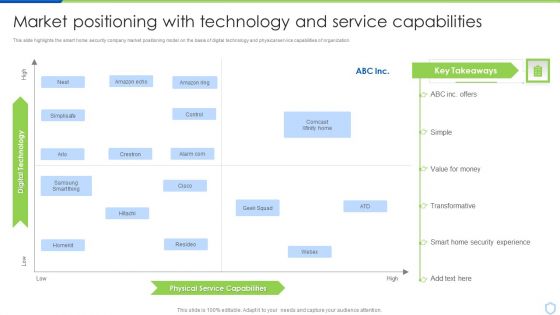
Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF bundle. Topics like Monitoring, Bluestone Security, Launched Integrated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
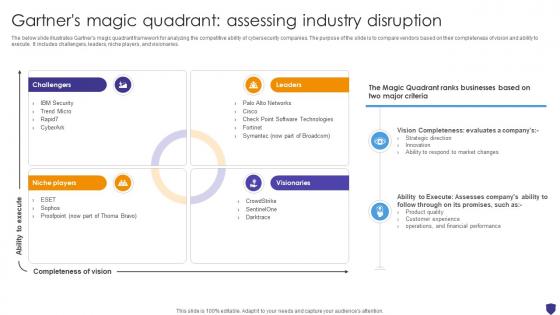
Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V
The below slide illustrates Gartners magic quadrant framework for analyzing the competitive ability of cybersecurity companies. The purpose of the slide is to compare vendors based on their completeness of vision and ability to execute. It includes challengers, leaders, niche players, and visionaries. Find highly impressive Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF
This slide portrays information regarding development of corporate security governance framework including board of directors, senior executives, steering committees in order to ensure the effective corporate security governance. Create an editable Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
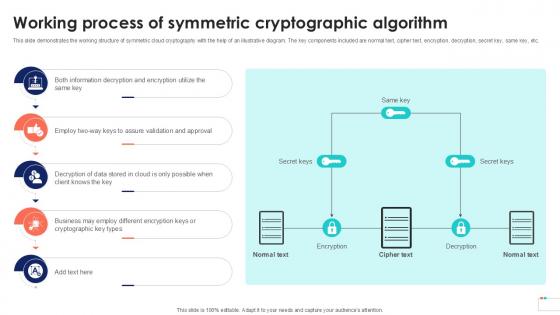
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
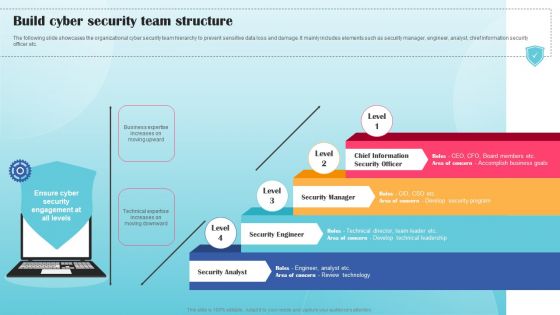
Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF
The following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Devops Engineer Capabilities Software Security Skills Ppt Slides Graphics Template PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. This is a devops engineer capabilities software security skills ppt slides graphics template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vulnerability management, threat investigation, compliance monitoring, security training, code analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. There are so many reasons you need a Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Information Security Governance Model For Business Ppt PowerPoint Presentation Show Graphics PDF
Persuade your audience using this information security governance model for business ppt powerpoint presentation show graphics pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including vision information security, information security principles, operational instructions and technical specification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
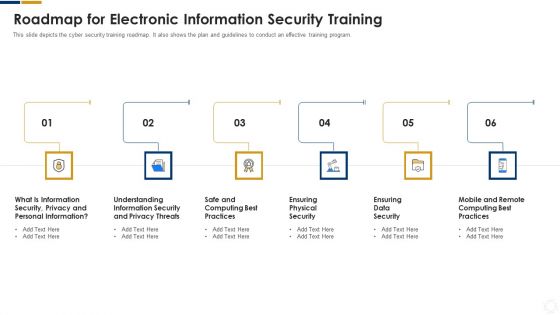
Cybersecurity Roadmap For Electronic Information Security Training Ppt Layouts Model PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting cybersecurity roadmap for electronic information security training ppt layouts model pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
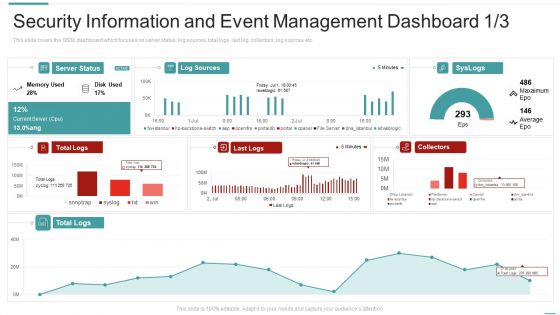
Risk Recognition Automation Security Information And Event Management Dashboard Ppt Model Elements PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard ppt model elements pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. There are so many reasons you need a Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Role, Position, Responsibility, Chief Information Officer, Information Management Manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
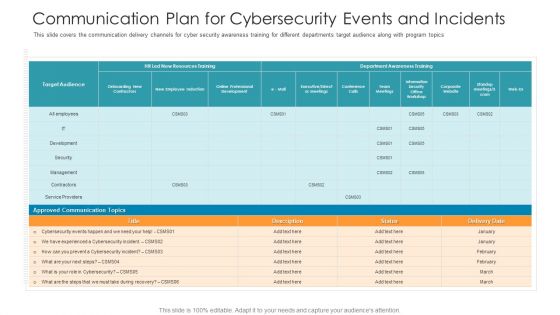
Communication Plan For Cybersecurity Events And Incidents Hacking Prevention Awareness Training For IT Security Background PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this communication plan for cybersecurity events and incidents hacking prevention awareness training for it security background pdf. Use them to share invaluable insights on development, security, management, cybersecurity, communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
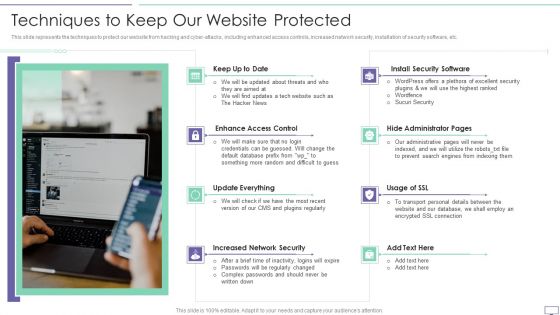
IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
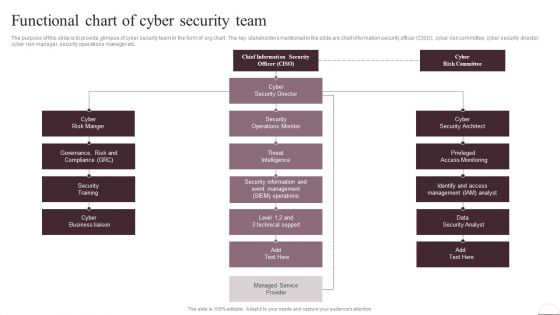
Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
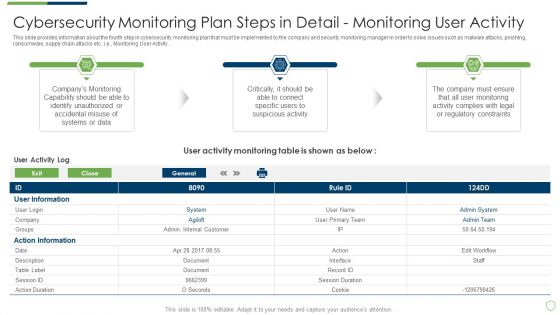
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Structure PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring structure pdf. Use them to share invaluable insights on cybersecurity monitoring tools to be implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Managing Information Technology Security 30 Days Plan Ppt Professional Examples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 30 days plan ppt professional examples pdf bundle. Topics like managing information technology security 30 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing Information Technology Security 60 Days Plan Ppt Ideas Graphics PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing information technology security 60 days plan ppt ideas graphics pdf . Use them to share invaluable insights on managing information technology security 60 days plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Building Trust With IoT Security IoT Device Management Platforms Comparison IoT SS V
This slide displays the most popular IoT device management platforms that help to automate connected device monitoring. It includes platforms such as Bytebeam, Cico IoT, Azure IoT Hub, and AWS IoT Core. The Building Trust With IoT Security IoT Device Management Platforms Comparison IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Managing Information Technology Security 60 Days Ppt Infographic Template Samples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 60 days ppt infographic template samples pdf bundle. Topics like managing information technology security 60 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Model For IT Risk Control Strategies Security Risk Management Ppt Ideas Portrait PDF
This slide shows the model that depicts IT security risk management which focuses on identification, protection, detection, response and recovery planning with security asset management, governance, data security, detection processes, risk analysis and planning, etc. Persuade your audience using this Model For IT Risk Control Strategies Security Risk Management Ppt Ideas Portrait PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identifying, Protecting, Detecting. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Timeline For The Implementation Of IT Security IT Ppt Inspiration Portrait PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of it security it ppt inspiration portrait pdf bundle. Topics like network, internal security, perform, phishing exercise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Timeline For The Implementation Of Electronic Information Security Ppt Infographic Template Information PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative cybersecurity timeline for the implementation of electronic information security ppt infographic template information pdf bundle. Topics like security documentation, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline For The Implementation Of Information Technology Security Ppt Portfolio Slideshow PDF
This slide shows the timeline for network security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of information technology security ppt portfolio slideshow pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. Presenting Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Smart Home Services, Acquired Bluestone Security, System Product Catalogue, Launched Different CCTV, 2010 To 2022. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
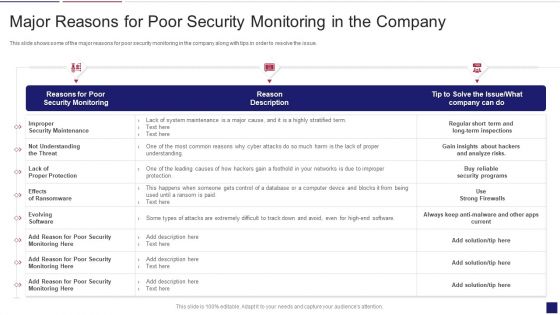
Continuous Development Evaluation Plan Eliminate Cyber Attacks Major Reasons For Poor Security Topics PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
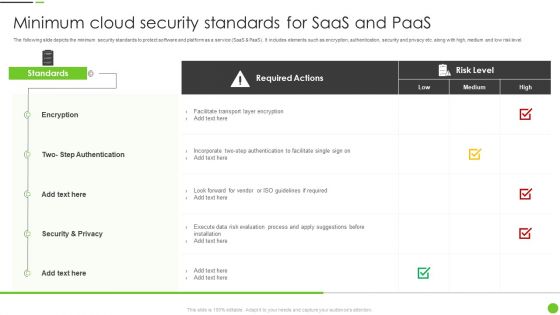
Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF
The following slide depicts the minimum security standards to protect software and platform as a service SaaS and PaaS. It includes elements such as encryption, authentication, security and privacy etc. along with high, medium and low risk level. Pitch your topic with ease and precision using this Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF. This layout presents information on Required Actions, Encryption, Security And Privacy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Model Canvas Security Service Provider Business Model BMC SS V
This slide provides the business model canvas of the company. It involves key partners, key activities, USP, customer relationships, customer segments, channels, revenue streams, channels, key resources, cost structure. Find a pre-designed and impeccable Business Model Canvas Security Service Provider Business Model BMC SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide illustrates the SaaS security to meet business needs and ensure data management. It includes four major elements such as vendor management, cloud security, business engagement, communicate proactively etc. Presenting Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vendor Management, Cloud Security, Business Engagement, Communicate Proactively. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
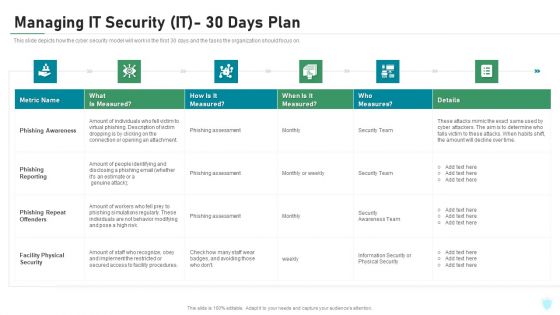
Managing IT Security IT 30 Days Plan Ppt Gallery Graphics Download PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing it security it 30 days plan ppt gallery graphics download pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Managing Electronic Information Security 30 Days Plan Ppt Layouts Design Ideas PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this cybersecurity managing electronic information security 30 days plan ppt layouts design ideas pdf. Use them to share invaluable insights on measured, metric, awareness, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Managing Electronic Information Security 90 Days Plan Ppt Pictures Example Introduction PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this cybersecurity managing electronic information security 90 days plan ppt pictures example introduction pdf. Use them to share invaluable insights on measured, awareness, security, communication methods and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
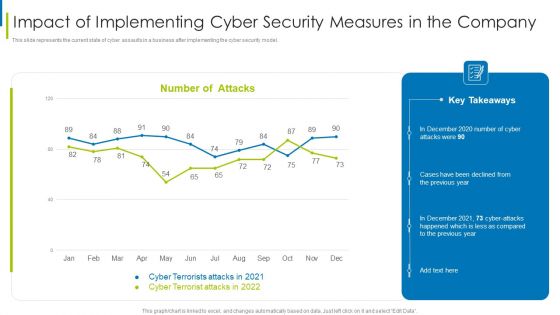
Cyber Terrorism Assault Impact Of Implementing Cyber Security Measures In The Company Professional PDF
This slide represents the current state of cyber assaults in a business after implementing the cyber security model.Deliver an awe inspiring pitch with this creative cyber terrorism assault impact of implementing cyber security measures in the company professional pdf bundle. Topics like impact of implementing cyber security measures in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF
Mentioned slide outlines various tools for managed security service. Email security software, endpoint protection and firewall are some of the comprehensive tools which will assist the organization in closely monitoring the advance threats. Showcasing this set of slides titled Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF. The topics addressed in these templates are Endpoint Protection, Firewall, Email Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF
This slide represents the introduction to software defined networking that helps network managers to manage network resources faster. It also includes its components such as applications, control plane, SDN controller, SDN datapath, data plane, switches, and so on. Presenting this PowerPoint presentation, titled SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
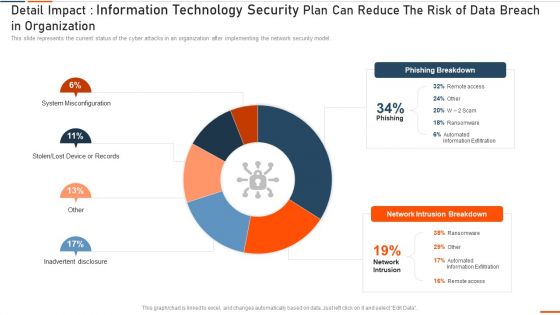
Detail Impact Information Technology Security Plan Can Reduce Ppt Show Slide Download PDF
This slide represents the current status of the cyber attacks in an organization after implementing the network security model. Deliver an awe inspiring pitch with this creative it security detail impact detail impact information technology security plan can reduce ppt show slide download pdf bundle. Topics like detail impact information technology security plan can reduce the risk of data breach in organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF
The following slide showcases the impact of software as a service SaaS security in developing business. It includes key elements such as scalability, security, customization, maintenance, availability, IT cost etc. Showcasing this set of slides titled Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF. The topics addressed in these templates are Scalability, Security, Customization, Maintenance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V
The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V from Slidegeeks and deliver a wonderful presentation.
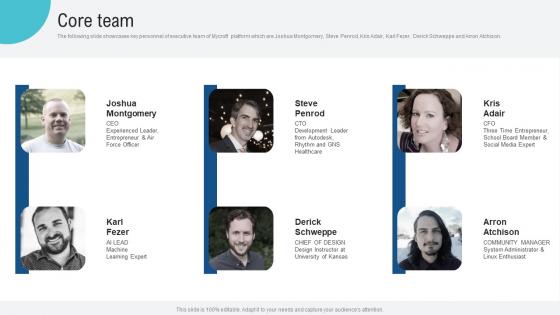
Core Team Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf
The following slide showcases key personnel of executive team of Mycroft platform which are Joshua Montgomery, Steve Penrod, Kris Adair, Karl Fezer, Derick Schweppe and Arron Atchison. This modern and well arranged Core Team Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Managing Electronic Information Security 60 Days Plan Ppt Ideas Graphics Tutorials PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative cybersecurity managing electronic information security 60 days plan ppt ideas graphics tutorials pdf bundle. Topics like measured, security, team, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF bundle. Topics like Technology Controls, Information Security Processes, Security Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Roadmap To Implement New Security Strategies Information PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fiveteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

 Home
Home