Access Icon
Icons Slide For Web Access Control Solution IT Ppt File Backgrounds
Download our innovative and attention grabbing Icons Slide For Web Access Control Solution IT Ppt File Backgrounds template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
Market Access With Research And Planning Ppt PowerPoint Presentation Icon Graphics Download
Presenting this set of slides with name market access with research and planning ppt powerpoint presentation icon graphics download. This is a eight stage process. The stages in this process are development, strategy, research. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
File Sharing And Document Management Access Change Review Ppt PowerPoint Presentation Slides Icons
This is a file sharing and document management access change review ppt powerpoint presentation slides icons. This is a five stage process. The stages in this process are document review, document analysis, document evaluation.
5G Radio Access Network Architecture Overview 5G Functional Architecture Icons PDF
This slide represents the overview of the 5G radio access network architecture and its components, including distributed unit, central unit, radio hardware unit, and so on.Deliver and pitch your topic in the best possible manner with this 5G Radio Access Network Architecture Overview 5G Functional Architecture Icons PDF. Use them to share invaluable insights on disaggregation pushed, faster interoperability, features technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Initiatives To Build Identity And Access Management Development Plan Six Months Roadmap Icons
Presenting the initiatives to build identity and access management development plan six months roadmap icons. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Successful Initiatives To Identity And Access Management Development Plan Three Months Roadmap Icons
Presenting our jaw-dropping successful initiatives to identity and access management development plan three months roadmap icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
Info Security Define Access Control Measures For Employees Ppt PowerPoint Presentation Gallery Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Presenting info security define access control measures for employees ppt powerpoint presentation gallery icon pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like access data, personnel according, duties or roles, organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Define Access Control Measures For Employees IT Security IT Ppt Professional Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a define access control measures for employees it security it ppt professional icon pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, access data, networks, responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Website Accessibility And Web Hosting Vector Icon Ppt PowerPoint Presentation Gallery Icon PDF
Persuade your audience using this website accessibility and web hosting vector icon ppt powerpoint presentation gallery icon pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including website accessibility and web hosting vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Access Control Management With User Id And Password Ppt PowerPoint Presentation Icon Introduction
This is a access control management with user id and password ppt powerpoint presentation icon introduction. This is a three stage process. The stages in this process are access rights, access management, business.
Icons Slide For Empowering Organization With Zero Trust Network Access Designs PDF
The Icons Slide For Empowering Organization With Zero Trust Network Access Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Strategic Database Accessibility Management Objectives On Multiple Domain Icon Diagrams PDF
This slide covers 3 main goals of data lifecycle management to organise large data volumes . It includes objectives such as data confidentiality , data availability and long-term structural integrity.Pitch your topic with ease and precision using this Strategic Database Accessibility Management Objectives On Multiple Domain Icon Diagrams PDF. This layout presents information on Strategic Database, Accessibility Management, Objectives On Multiple. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
VR And AR IT Data Becomes More Accessible With AR And VR Ppt Icon Infographics PDF
This slide represents how data becomes more accessible with augmented and virtual reality and how augmented reality bridges the gap between the real world and the digital world. Deliver and pitch your topic in the best possible manner with this vr and ar it data becomes more accessible with ar and vr ppt icon infographics pdf. Use them to share invaluable insights on training, marketing, businesses, virtual reality, smart manufacturing, analysts and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Access Management Powerpoint Slide Themes
This is a access management powerpoint slide themes. This is a five stage process. The stages in this process are access management, service desk, technical management, it operations management, application management.
User Accessing Smart Home Application On Mobile Ppt PowerPoint Presentation Icon Example PDF
Presenting this set of slides with name user accessing smart home application on mobile ppt powerpoint presentation icon example pdf. This is a one stage process. The stage in this process is user accessing smart home application on mobile. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Person Accessing Online Networking Apps On Mobile Ppt PowerPoint Presentation Icon Styles PDF
Presenting this set of slides with name person accessing online networking apps on mobile ppt powerpoint presentation icon styles pdf. This is a one stage process. The stage in this process is person accessing online networking apps on mobile. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For Effective Data Preparation To Make Data Accessible And Ready For Processing Designs PDF
Help your business to create an attention grabbing presentation using our icons slide for effective data preparation to make data accessible and ready for processing designs pdf set of slides. The slide contains innovative icons that can be flexibly edited. Choose this icons slide for effective data preparation to make data accessible and ready for processing designs pdf template to create a satisfactory experience for your customers. Go ahead and click the download button.
Icons Slide For Effective Data Management To Make Information Accessible And Ready For Processing Brochure PDF
Presenting our innovatively structured Icons Slide For Effective Data Management To Make Information Accessible And Ready For Processing Brochure PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
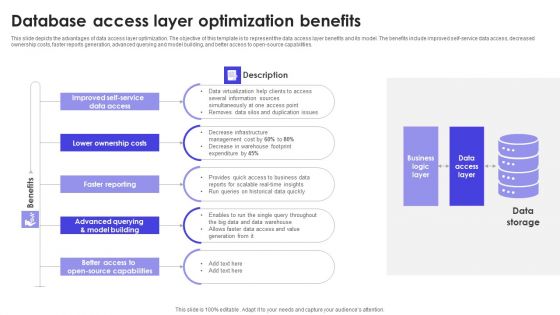
Database Access Layer Optimization Benefits Slides PDF
This slide depicts the advantages of data access layer optimization. The objective of this template is to represent the data access layer benefits and its model. The benefits include improved self-service data access, decreased ownership costs, faster reports generation, advanced querying and model building, and better access to open-source capabilities. Presenting Database Access Layer Optimization Benefits Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Benefits, Lower Ownership Costs, Faster Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Inventory Management Access Diagram Powerpoint Themes
This is a inventory management access diagram powerpoint themes. This is a eight stage process. The stages in this process are product inventory, product sales, physical inventory, store manager, engage, measure, accounting manager, supplier manager.

Zero Trust Network Access Main Pillars Of Zero Network Trust Access
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Do you know about Slidesgeeks Zero Trust Network Access Main Pillars Of Zero Network Trust Access These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
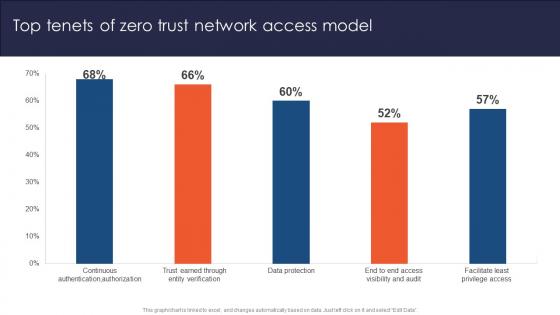
Zero Trust Network Access Top Tenets Of Zero Trust Network Access Model
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Top Tenets Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Initiatives For Access Governance Identity And Access Management Development Plan Five Year Roadmap Themes
We present our initiatives for access governance identity and access management development plan five year roadmap themes. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched initiatives for access governance identity and access management development plan five year roadmap themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
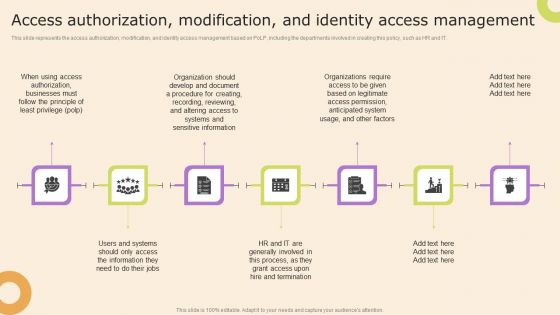
Information Technology Policy And Processes Access Authorization Modification And Identity Access Themes PDF
This slide represents the access authorization, modification, and identity access management based on PoLP, including the departments involved in creating this policy, such as HR and IT. Create an editable Information Technology Policy And Processes Access Authorization Modification And Identity Access Themes PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Information Technology Policy And Processes Access Authorization Modification And Identity Access Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
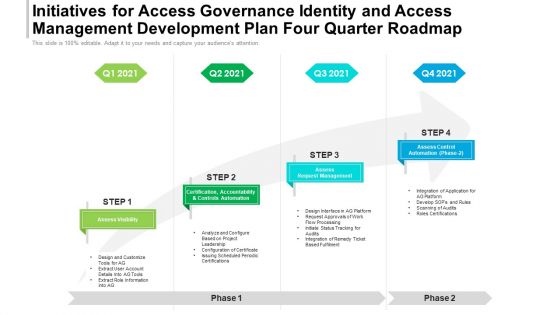
Initiatives For Access Governance Identity And Access Management Development Plan Four Quarter Roadmap Guidelines
Presenting our innovatively-structured initiatives for access governance identity and access management development plan four quarter roadmap guidelines Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Initiatives For Access Governance Identity And Access Management Development Plan Half Yearly Roadmap Graphics
Introducing our initiatives for access governance identity and access management development plan half yearly roadmap graphics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Initiatives For Access Governance Identity And Access Management Development Plan Six Months Roadmap Rules
Presenting the initiatives for access governance identity and access management development plan six months roadmap rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Initiatives For Access Governance Identity And Access Management Development Plan Three Months Roadmap Slides
Presenting our jaw-dropping initiatives for access governance identity and access management development plan three months roadmap slides. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Zero Trust Network Access System Use Cases Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Present like a pro with Zero Trust Network Access System Use Cases Themes Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
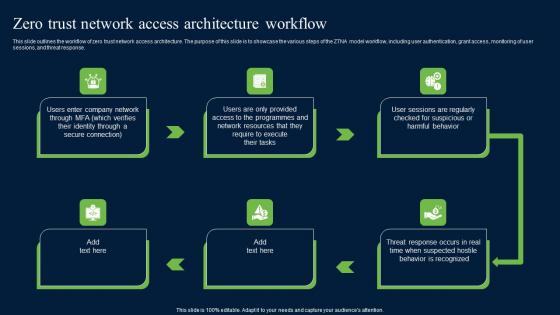
Zero Trust Network Access Architecture Workflow Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Architecture Workflow Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Architecture Workflow Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Zero Trust Model Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Model Zero Trust Network Access System Use Cases that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Zero Trust Network Access System Use Cases from Slidegeeks today.

Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Table Of Contents Web Access Control Solution Ppt Diagram Images
Get a simple yet stunning designed Table Of Contents Web Access Control Solution Ppt Diagram Images. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Table Of Contents Web Access Control Solution Ppt Diagram Images can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Agenda For Zero Trust Network Access Ppt Diagram Graph Charts
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Agenda For Zero Trust Network Access Ppt Diagram Graph Charts a try. Our experts have put a lot of knowledge and effort into creating this impeccable Agenda For Zero Trust Network Access Ppt Diagram Graph Charts. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Network Access Computer PowerPoint Themes And PowerPoint Slides 0411
Microsoft PowerPoint Theme and Slide with network access of computer

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Are you searching for a Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation from Slidegeeks today.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today.
Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard
This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc. Get a simple yet stunning designed Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
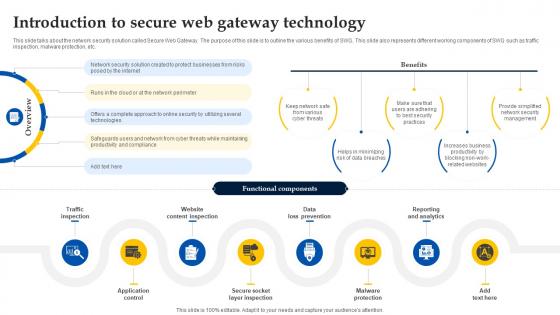
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Secure Web Gateway Implementation Methodology Inline Web Access Control Solution
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Create an editable Secure Web Gateway Implementation Methodology Inline Web Access Control Solution that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Secure Web Gateway Implementation Methodology Inline Web Access Control Solution is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
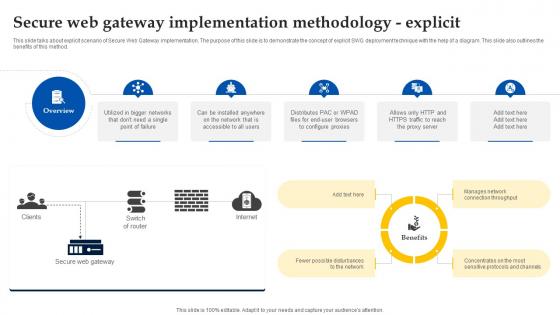
Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit
This slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit a try. Our experts have put a lot of knowledge and effort into creating this impeccable Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Web Access Control Solution Industry Wise Market Segmentation Of Swg
This slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Web Access Control Solution Industry Wise Market Segmentation Of Swg from Slidegeeks and deliver a wonderful presentation.
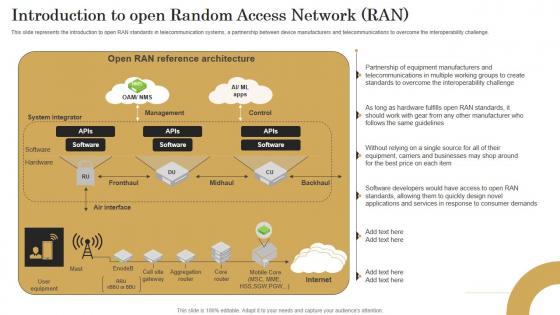
Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF
This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF can be your best option for delivering a presentation. Represent everything in detail using Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Ensure Security And Access Controls Ppt PowerPoint Presentation Portfolio Images
This is a ensure security and access controls ppt powerpoint presentation portfolio images. This is a two stage process. The stages in this process are icons, strategy, business, management, marketing.
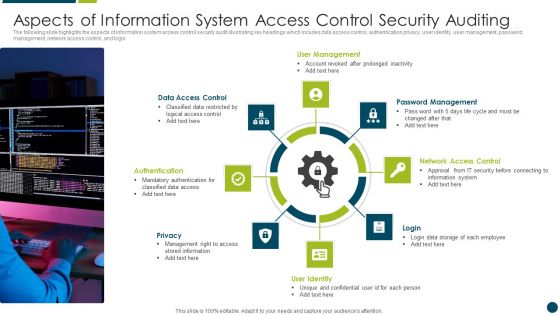
Aspects Of Information System Access Control Security Auditing Diagrams PDF
The following slide highlights the aspects of information system access control security audit illustrating key headings which incudes data access control, authentication privacy, user identity, user management, password management, network access control, and login Presenting Aspects Of Information System Access Control Security Auditing Diagrams PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Management, Data Access Control, Network Access Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Web Access Control Solution Prominent Users Of Secure Web Gateway
Do you know about Slidesgeeks Web Access Control Solution Prominent Users Of Secure Web Gateway These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Steps To Create Database Access Layer Slides PDF
This slide outlines the guidelines for creating a data access layer for an organizational structure. The objective of this slide is to demonstrate the data access layer creation phases. The key steps include creating the design, designing data access components, designing data helper components, and designing service agents. Showcasing this set of slides titled Steps To Create Database Access Layer Slides PDF. The topics addressed in these templates are Data Access Components, Create Design, Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
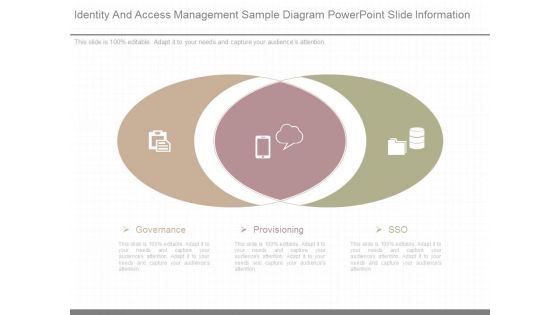
Identity And Access Management Sample Diagram Powerpoint Slide Information
This is a identity and access management sample diagram powerpoint slide information. This is a two stage process. The stages in this process are governance, provisioning, sso.
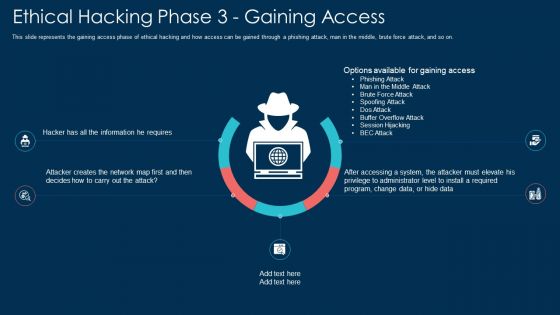
Ethical Hacking Phase 3 Gaining Access Ppt Pictures Vector PDF
This slide represents the gaining access phase of ethical hacking and how access can be gained through a phishing attack, man in the middle, brute force attack, and so on. This is a ethical hacking phase 3 gaining access ppt pictures vector pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, required. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Identity And Access Management Sample Diagram Ppt Slides
This is a identity and access management sample diagram ppt slides. This is a nine stage process. The stages in this process are auditors, itsm change management, end users and key users, identity and access administrators, administrators owners, legacy, cloud, sap, ad.

Dashboard To Access Online Promotion Effectiveness Template PDF Pictures PDF
Showcasing this set of slides titled Dashboard To Access Online Promotion Effectiveness Template PDF Pictures PDF The topics addressed in these templates are Dashboard To Access Online Promotion Effectiveness All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
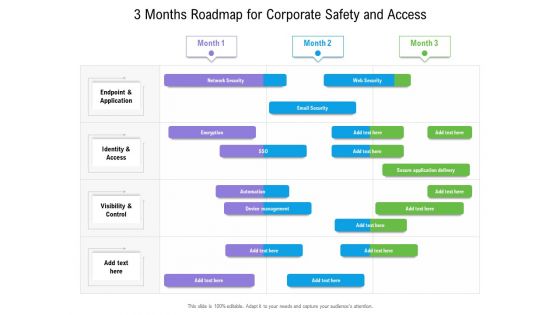
3 Months Roadmap For Corporate Safety And Access Diagrams
We present our 3 months roadmap for corporate safety and access diagrams. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 3 months roadmap for corporate safety and access diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
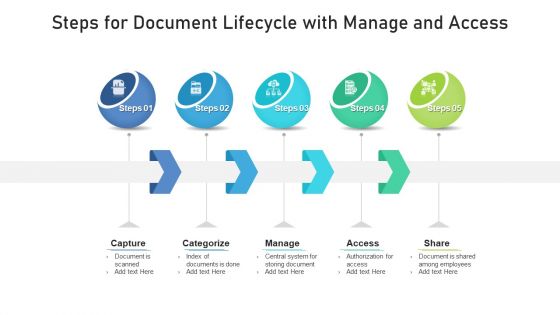
Steps For Document Lifecycle With Manage And Access Template PDF
Presenting steps for document lifecycle with manage and access template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including capture, categorize, manage, access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Based Identify And Access Management Technique Introduction PDF
Presenting Cloud Based Identify And Access Management Technique Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Based Identify, Access Management, Technique. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
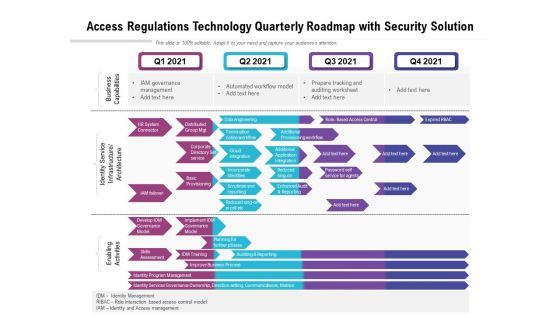
Access Regulations Technology Quarterly Roadmap With Security Solution Graphics
We present our access regulations technology quarterly roadmap with security solution graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched access regulations technology quarterly roadmap with security solution graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Facial Recognition Access Regulations Technology Five Years Roadmap Brochure
We present our facial recognition access regulations technology five years roadmap brochure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched facial recognition access regulations technology five years roadmap brochure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Five Years Roadmap For Access Regulations Technology Roll Out Clipart
We present our five years roadmap for access regulations technology roll out clipart. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five years roadmap for access regulations technology roll out clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Quarterly Technology Implementation Roadmap Of Iris Access Regulations System Topics
We present our quarterly technology implementation roadmap of iris access regulations system topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly technology implementation roadmap of iris access regulations system topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

 Home
Home