Threat Intelligence Framework Powerpoint Presentation Slides PPT Template
Our Threat Intelligence Framework Powerpoint Presentation Slides PPT Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideGeeks and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideGeeks product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
 Impress Your
Impress Your Audience
 100%
100% Editable
Google Slides
Features of these PowerPoint presentation slides:
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide highlights the presentation title: Threat Intelligence Framework.
Slide 2: This slide states Agenda of the presentation.
Slide 3: This slide shows Table of Content for the presentation.
Slide 4: This slide highlights title for topics that are to be covered next in the template.
Slide 5: This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose.
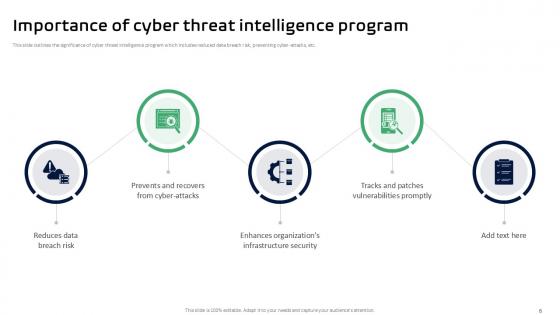
Slide 6: This slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber-attacks, etc.
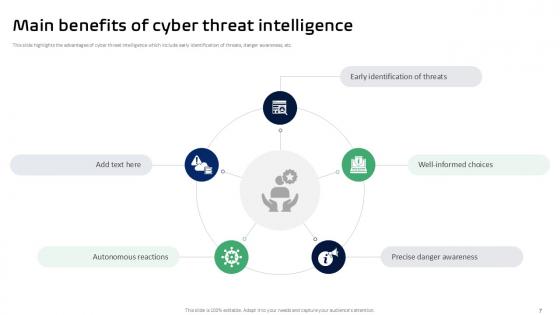
Slide 7: This slide highlights the advantages of cyber threat intelligence which include early identification of threats, danger awareness, etc.
Slide 8: This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc.
Slide 9: This slide outlines the various elements of cyber threat intelligence which include people, process, technology, budgeting, etc.
Slide 10: This slide highlights title for topics that are to be covered next in the template.
Slide 11: This slide showcases the characteristics of tactical cyber threat intelligence which includes its features such as machine readable, automated, etc.
Slide 12: This slide outlines the features of second type of cyber threat intelligence, which is, operation cyber threat intelligence.
Slide 13: This slide discusses the characteristics of strategic cyber threat intelligence which includes the features and objectives.
Slide 14: This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc.
Slide 15: This slide highlights title for topics that are to be covered next in the template.
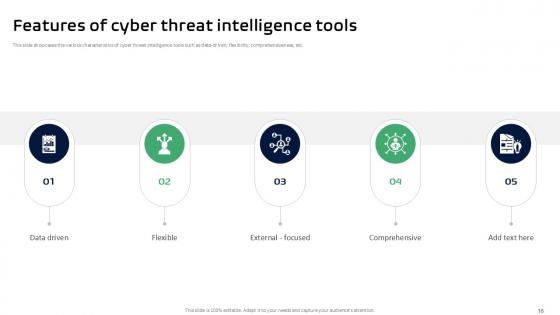
Slide 16: This slide showcases the various characteristics of cyber threat intelligence tools such as data-driven, flexibility, comprehensiveness, etc.
Slide 17: This slide represents the various tools used for cyber threat intelligence along with their features and cost.
Slide 18: This slide highlights title for topics that are to be covered next in the template.
Slide 19: This slide highlights the characteristic of cyber threat intelligence platform which includes dynamic intelligence feed, smart data virtualization, etc.
Slide 20: This slide discusses the different platforms of cyber threat intelligence which include Anomali ThreatStream, Dataminr Pulse, etc.
Slide 21: This slide highlights title for topics that are to be covered next in the template.
Slide 22: This slide outlines the process phases to construct cyber threat intelligence framework such as threat vector identification, compiling intelligence, etc.
Slide 23: This slide represents cyber threat intelligence operationalize framework with factors such as alerts for monitoring, threat intelligence, etc.
Slide 24: This slide represents the process phases of cyber threat intelligence lifecycle such as establishing roadmap, collecting data, etc.
Slide 25: This slide highlights title for topics that are to be covered next in the template.
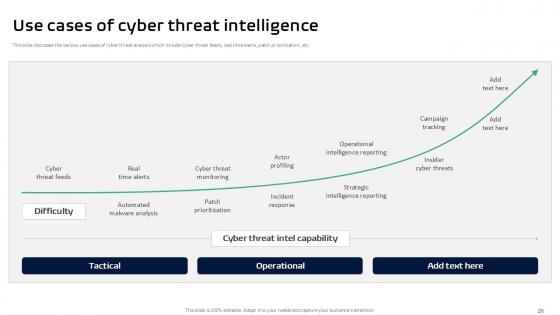
Slide 26: This slide discusses the various use cases of cyber threat analysis which include cyber threat feeds, real time alerts, patch prioritization, etc.
Slide 27: This slide highlights title for topics that are to be covered next in the template.
Slide 28: This slide showcases the problems and related solutions of implementing cyber threat intelligence which include overloaded data, complicated integration, etc.
Slide 29: This slide highlights title for topics that are to be covered next in the template.
Slide 30: This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc.
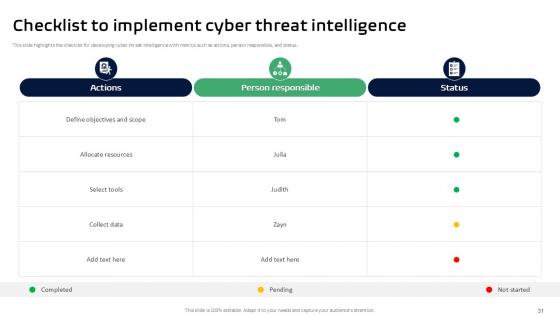
Slide 31: This slide highlights the checklist for developing cyber threat intelligence with metrics such as actions, person responsible, and status.
Slide 32: This slide highlights title for topics that are to be covered next in the template.
Slide 33: This slide outlines the training schedule of cyber threat intelligence which includes three days with different time slots for various learning's.
Slide 34: This slide discusses the budget allocation for cyber threat intelligence design which includes components such as categories, estimated and actual cost.
Slide 35: This slide highlights title for topics that are to be covered next in the template.
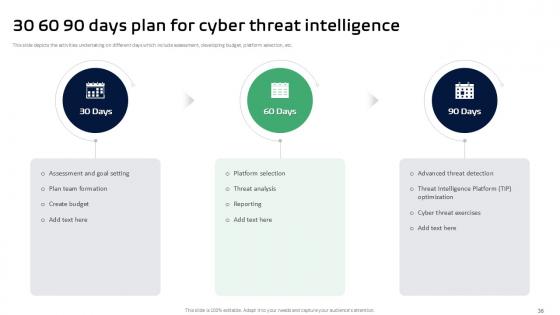
Slide 36: This slide depicts the activities undertaking on different days which include assessment, developing budget, platform selection, etc.
Slide 37: This slide showcases the steps that an organization should take while deploying cyber threat intelligence such as recognizing needs, assembling data, etc.
Slide 38: This slide showcases the vulnerability analyzing dashboard for cyber threat intelligence based on various parameters such as issue status, severity, etc.
Slide 39: This slide represents the vulnerability analyzing dashboard for cyber threat intelligence based on various parameters such as threat detection, risk, etc.
Slide 40: This slide highlights title for topics that are to be covered next in the template.
Slide 41: This slide showcases the different performance metrics and how cyber threat intelligence have improved these metrics.
Slide 42: This slide highlights title for topics that are to be covered next in the template.
Slide 43: This slide represents the cyber threat intelligence case study at Fintech industry including the challenges faced and the solutions provided.
Slide 44: This slide contains all the icons used in this presentation.
Slide 45: This slide is titled as Additional Slides for moving forward.
Slide 46: This slide represents what all is included in strategic cyber threat intelligence reports such as policy documents, research reports, etc.
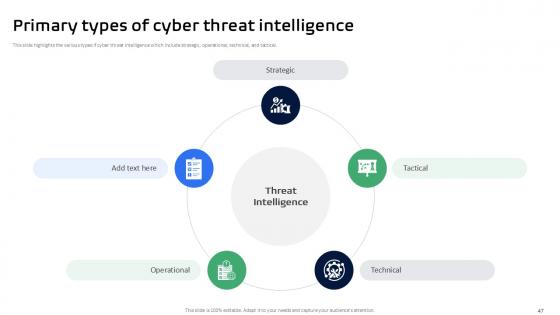
Slide 47: This slide highlights the various types if cyber threat intelligence which include strategic, operational, technical, and tactical.
Slide 48: This slide shows Post It Notes. Post your important notes here.
Slide 49: This is a Timeline slide. Show data related to time intervals here.
Slide 50: This slide presents Roadmap with additional textboxes.
Slide 51: This is a Financial slide. Show your finance related stuff here.
Slide 52: This slide shows SWOT describing- Strength, Weakness, Opportunity, and Threat.
Slide 53: This is an Idea Generation slide to state a new idea or highlight information, specifications, etc.
Slide 54: This is Our Mission slide with related imagery and text.
Slide 55: This is a Thank You slide with address, contact numbers and email address.
Threat Intelligence Framework Powerpoint Presentation Slides PPT Template with all 63 slides:
Use our Threat Intelligence Framework Powerpoint Presentation Slides PPT Template to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
Most Relevant Reviews
-
Great product with highly impressive and engaging designs.
-
Informative presentations that are easily editable.

 Home
Home