Watering Hole PowerPoint Presentation Templates and Google Slides
-
Introduction To Watering Hole Phishing Man In The Middle Phishing IT
This slide talks about the watering hole phishing attacks which trick the victim to do activities compromising their personal data. The purpose of this slide is to describe the idea behind the working of watering hole scams which can target a group of individuals. Take your projects to the next level with our ultimate collection of Introduction To Watering Hole Phishing Man In The Middle Phishing IT. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
-
Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT
This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation OrganizationICAO scam, Ccleaner scam and Holy Water scam. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
-
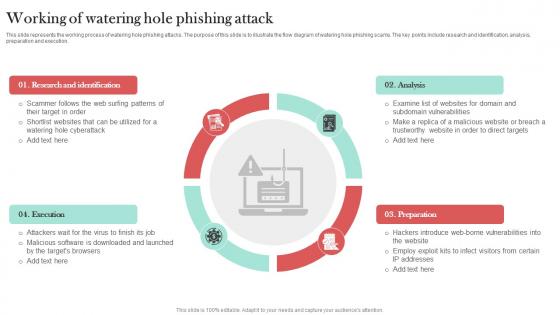
Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT
This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. This Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.