Vulnerable PowerPoint Presentation Templates and Google Slides
-
Zombie Load System Vulnerability In Powerpoint And Google Slides Cpb
Introducing our well designed Zombie Load System Vulnerability In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Zombie Load System Vulnerability. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
-
Vulnerability Assessment In Powerpoint And Google Slides Cpb
Introducing our well designed Vulnerability Assessment In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Vulnerability Assessment. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
-
Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation.
-
Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V
This slide highlights security concerns in various areas of internet of things system in order to effectively address and mitigate such risks. It includes various components Of IoT ecosystem such as web and mobile application, cloud, communications, gateways, IoT sensors, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
-
Comparative Analysis Of Vulnerability Scanning Application Security Testing
This slide showcases the difference between vulnerability scanning and penetration testing based on aspects such as nature, purpose, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparative Analysis Of Vulnerability Scanning Application Security Testing and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
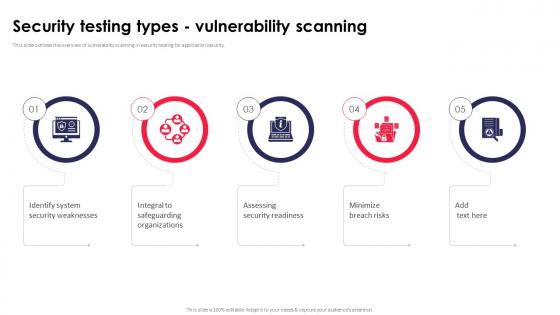
Security Testing Types Vulnerability Scanning Application Security Testing
This slide outlines the overview of vulnerability scanning in security testing for application security. Do you know about Slidesgeeks Security Testing Types Vulnerability Scanning Application Security Testing These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
-
Tools For Vulnerability Scanning In Security Testing Application Security Testing
This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc. Retrieve professionally designed Tools For Vulnerability Scanning In Security Testing Application Security Testing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
-
Blockchain Basics Understanding Ways To Protect Dao From Vulnerability Attacks BCT SS V
This slide mentions measures that can be taken to protect DAOs from third party attacks. It includes limiting value of attacks, increasing cost of acquiring voting power, increasing cost of attacks etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Blockchain Basics Understanding Ways To Protect Dao From Vulnerability Attacks BCT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
-
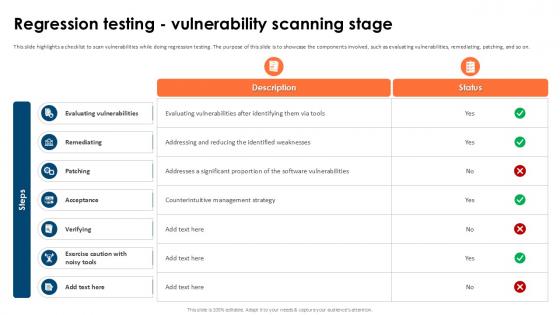
Regression Testing Vulnerability Scanning Stage Corrective Regression Testing Ppt Example
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. Boost your pitch with our creative Regression Testing Vulnerability Scanning Stage Corrective Regression Testing Ppt Example. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
-
Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
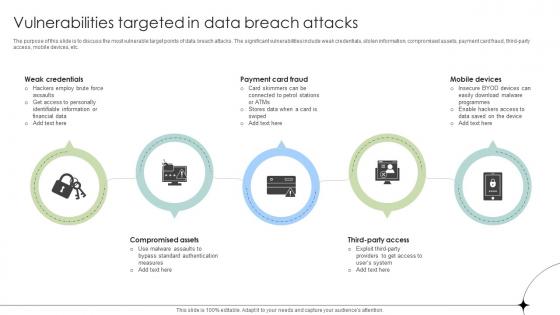
Vulnerabilities Targeted In Data Breach Attacks Data Fortification Strengthening Defenses
The purpose of this slide is to discuss the most vulnerable target points of data breach attacks. The significant vulnerabilities include weak credentials, stolen information, compromised assets, payment card fraud, third-party access, mobile devices, etc. Slidegeeks is here to make your presentations a breeze with Vulnerabilities Targeted In Data Breach Attacks Data Fortification Strengthening Defenses With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
-
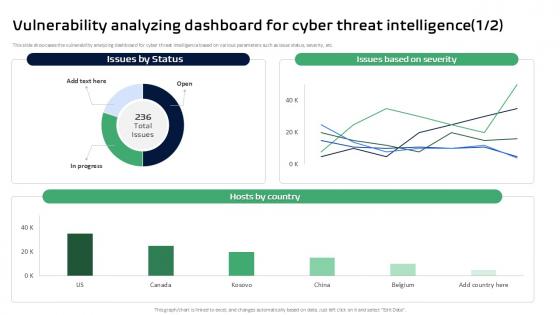
Vulnerability Analyzing Dashboard For Cyber Threat Intelligence Ppt Sample
This slide showcases the vulnerability analyzing dashboard for cyber threat intelligence based on various parameters such as issue status, severity, etc. This Vulnerability Analyzing Dashboard For Cyber Threat Intelligence Ppt Sample from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
-
Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. This Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
-
Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. This Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today