Vulnerability identified PowerPoint Presentation Templates and Google Slides
-
Company Vulnerability Administration Identify Sources Of Vulnerability Information Structure PDF
This is a company vulnerability administration identify sources of vulnerability information structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identify assets in use, model numbers for hardware, version numbers for software, location of the component. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Vulnerability Assessment Methodology Risk Identification Cost Ppt Professional Display PDF
Presenting this set of slides with name vulnerability assessment methodology risk identification cost ppt professional display pdf. This is a six stage process. The stages in this process are cost, resources, environmental, scope, communication, time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
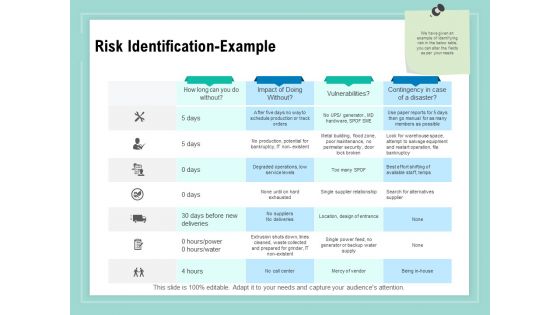
Vulnerability Assessment Methodology Risk Identification Example Ppt Portfolio Topics PDF
Presenting this set of slides with name vulnerability assessment methodology risk identification example ppt portfolio topics pdf. The topics discussed in these slides are contingency in case of a disaster, vulnerabilities, impact of doing without, how long can you do without. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Identification Treat Ppt Visual Aids Deck PDF
Presenting this set of slides with name vulnerability assessment methodology risk identification treat ppt visual aids deck pdf. This is a four stage process. The stages in this process are transfer, terminate, treat, tolerate. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
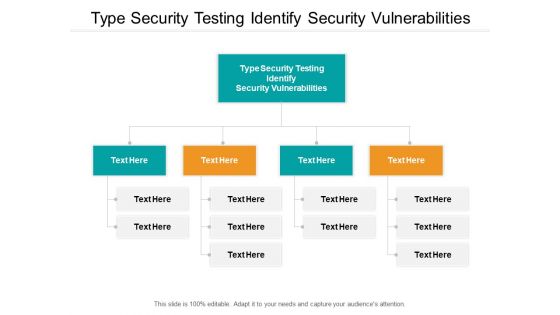
Type Security Testing Identify Security Vulnerabilities Ppt PowerPoint Presentation Inspiration Themes Cpb
Presenting this set of slides with name type security testing identify security vulnerabilities ppt powerpoint presentation inspiration themes cpb. This is an editable Powerpoint five stages graphic that deals with topics like type security testing identify security vulnerabilities to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
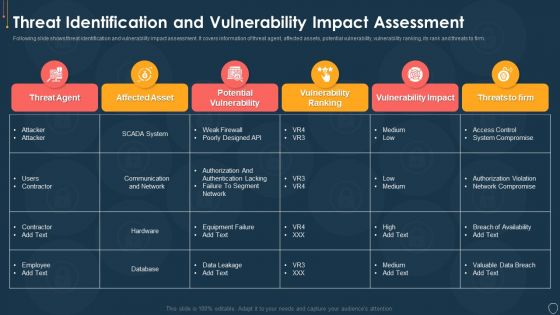
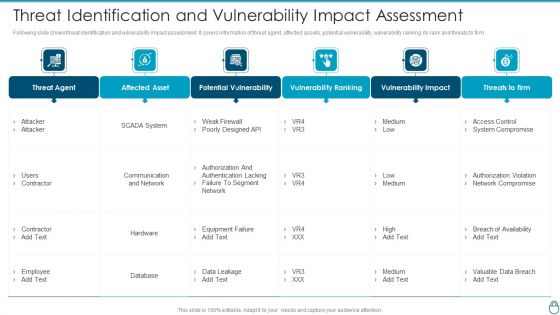
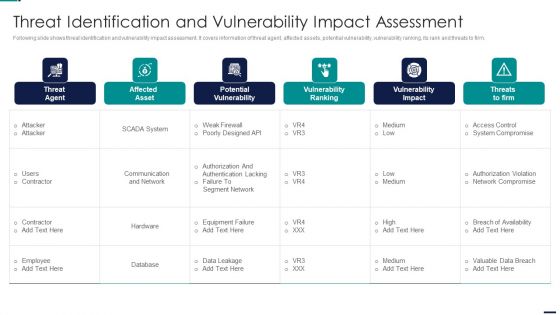
Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF bundle. Topics like Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Effective IT Risk Management Process Threat Identification And Vulnerability Professional PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative effective it risk management process threat identification and vulnerability professional pdf bundle. Topics like potential vulnerability, system, network, designed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
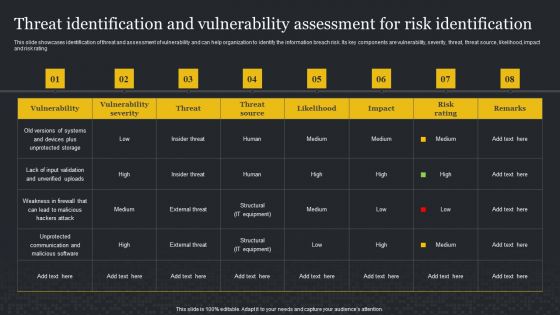
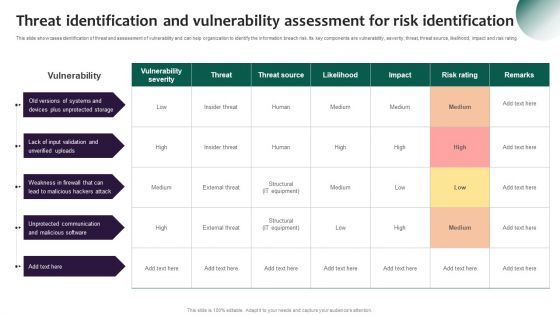
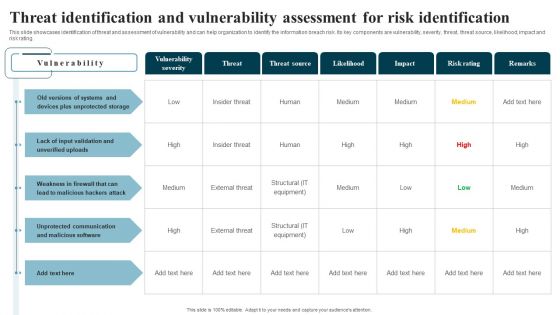
Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF. Use them to share invaluable insights on Vulnerability Severity, Unprotected Storage, Unprotected Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
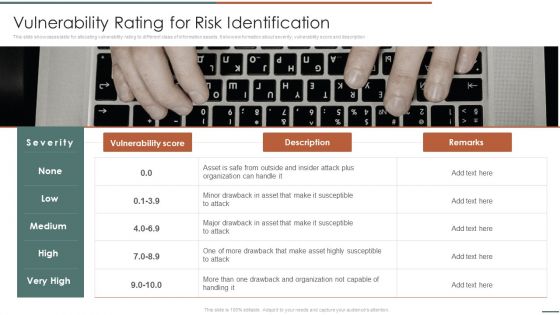
Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description.This is a Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drawback And Organization, Drawback Asset, Vulnerability Score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Get a simple yet stunning designed Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
-
Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF
Retrieve professionally designed Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
-
Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Vulnerability Identification And Administration Plan Checklist Brochure PDF
This slide defines the checklist for vulnerability identification and management program. It includes information related to assets effected, vulnerability rankings and threats. Pitch your topic with ease and precision using this Vulnerability Identification And Administration Plan Checklist Brochure PDF. This layout presents information on Assets Affected, Potential Vulnerability, Vulnerability Ranking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. Find highly impressive Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
-
Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF
The following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Are you searching for a Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF from Slidegeeks today.
-
Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
-
Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Are you searching for a Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF from Slidegeeks today.
-
Identifying Inherent Risk Factors Minimizing Customer Transaction Vulnerabilities Portrait Pdf
This slide showcases identifying inherent risk factors and measures. It provides information about customer base, products, services, delivery channels, jurisdictions, qualitative factors, location, customer risk rating, transparency, fund transfer, etc. Presenting this PowerPoint presentation, titled Identifying Inherent Risk Factors Minimizing Customer Transaction Vulnerabilities Portrait Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Identifying Inherent Risk Factors Minimizing Customer Transaction Vulnerabilities Portrait Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Identifying Inherent Risk Factors Minimizing Customer Transaction Vulnerabilities Portrait Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.