Vulnerability Data PowerPoint Presentation Templates and Google Slides
-
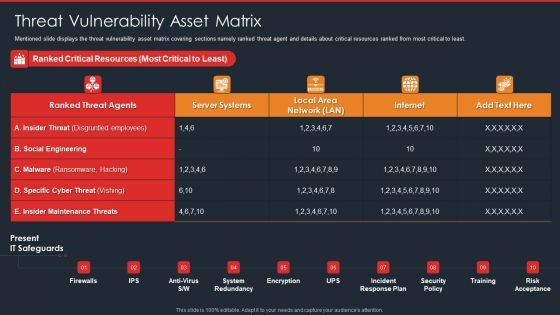
Data Safety Initiatives Threat Vulnerability Asset Matrix Themes PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this data safety initiatives threat vulnerability asset matrix themes pdf. Use them to share invaluable insights on ranked threat agents, insider threat, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
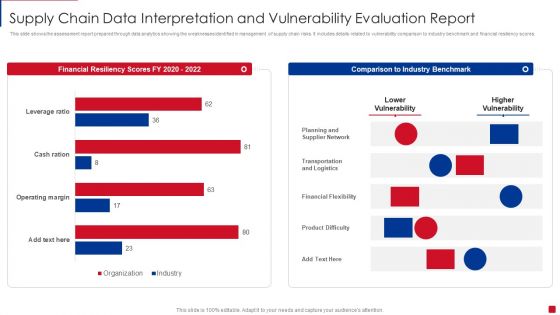
Supply Chain Data Interpretation And Vulnerability Evaluation Report Pictures PDF
This slide shows the assessment report prepared through data analytics showing the weaknesses identified in management of supply chain risks. It includes details related to vulnerability comparison to industry benchmark and financial resiliency scores Showcasing this set of slides titled Supply Chain Data Interpretation And Vulnerability Evaluation Report Pictures PDF. The topics addressed in these templates are Planning And Supplier Network, Transportation And Logistics, Financial Flexibility. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF. Use them to share invaluable insights on Vulnerability Ranking, High, LOW, MEDIUM, Attack Organization, Occurrence Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
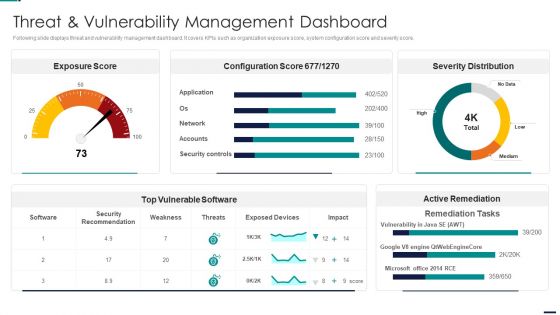
Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF bundle. Topics like Exposure Score, Configuration Score, Severity Distribution, Top Vulnerable Software, Active Remediation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
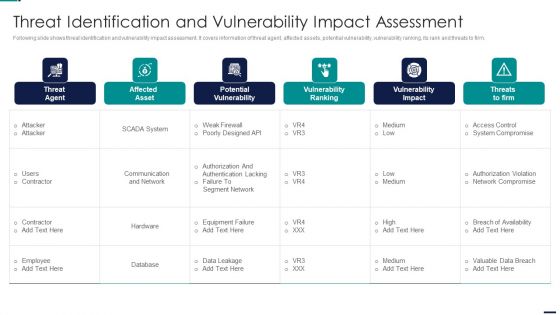
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
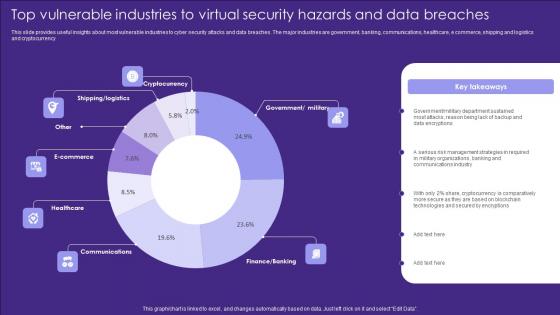
Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf
This slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Pitch your topic with ease and precision using this Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf. This layout presents information on Cryptocurrency, Ecommerce, Healthcare. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Database Vulnerability Handling Process Flowchart Icon Guidelines Pdf
Pitch your topic with ease and precision using this Database Vulnerability Handling Process Flowchart Icon Guidelines Pdf. This layout presents information on Database Vulnerability, Handling Process Flowchart Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Data Breach Response Plan Fix Vulnerabilities Data Breach Prevention Information Pdf
This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc. This modern and well-arranged Data Breach Response Plan Fix Vulnerabilities Data Breach Prevention Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
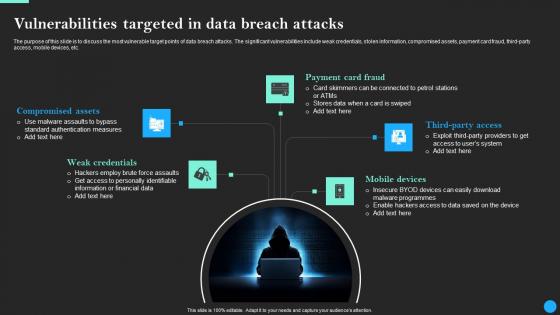
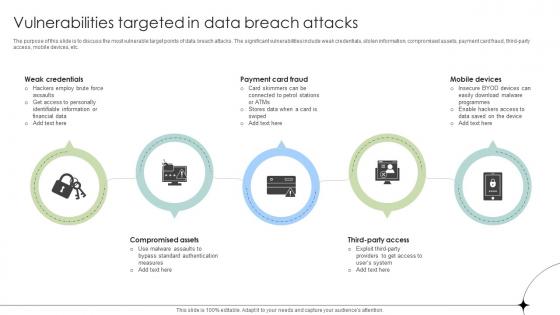
Vulnerabilities Targeted In Data Breach Attacks Data Breach Prevention Inspiration Pdf
Slidegeeks is here to make your presentations a breeze with Vulnerabilities Targeted In Data Breach Attacks Data Breach Prevention Inspiration Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
-
Vulnerability Data In Powerpoint And Google Slides Cpb
Introducing our well designed Vulnerability Data In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Vulnerability Data. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
-
Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation.
-
Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
Vulnerabilities Targeted In Data Breach Attacks Data Fortification Strengthening Defenses
The purpose of this slide is to discuss the most vulnerable target points of data breach attacks. The significant vulnerabilities include weak credentials, stolen information, compromised assets, payment card fraud, third-party access, mobile devices, etc. Slidegeeks is here to make your presentations a breeze with Vulnerabilities Targeted In Data Breach Attacks Data Fortification Strengthening Defenses With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first