Vulnerability assessment PowerPoint Presentation Templates and Google Slides
-
Vulnerability Assessment Methodology Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name vulnerability assessment methodology ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are analysis, assessment, management, matrix, strategies. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Ppt Presentation Background Images
This is a vulnerability assessment ppt presentation background images. This is a four stage process. The stages in this process are device discovery, service enumeration, service enumeration, validation.
-
Vulnerability Assessment And Penetration In Network Security Ppt Powerpoint Slides
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.
-
Vulnerability Assessment Diagram Powerpoint Images
This is a vulnerability assessment diagram powerpoint images. This is a four stage process. The stages in this process are device discovery, scanning, service enumeration, validation.
-
Enterprise Vulnerability Assessment Ppt PowerPoint Presentation Layouts Graphics Template Cpb
This is a enterprise vulnerability assessment ppt powerpoint presentation layouts graphics template cpb. This is a one stage process. The stages in this process are enterprise vulnerability assessment.
-
Vulnerability Assessment Companies Ppt PowerPoint Presentation Outline Graphics Design Cpb
This is a vulnerability assessment companies ppt powerpoint presentation outline graphics design cpb. This is a five stage process. The stages in this process are vulnerability assessment companies.
-
4 Types Of Security Assessment With Threat And Vulnerability Ppt PowerPoint Presentation Outline Inspiration PDF
Presenting 4 types of security assessment with threat and vulnerability ppt powerpoint presentation outline inspiration pdf. to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including risk assessment, vulnerability assessment, threat assessment, impact assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Company Vulnerability Administration Assess And Improve The Capability Demonstration Pictures PDF
This is a company vulnerability administration assess and improve the capability demonstration pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like overview, determine the state of the program, collect and analyze program information, improve the capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Company Vulnerability Administration Conduct Vulnerability Assessment Activities Elements PDF
This is a company vulnerability administration conduct vulnerability assessment activities elements pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like execute vulnerability scans, execute vulnerability assessments, personnel should possess the skills to appropriately execute the tasks defined, individuals need to be trained to use the specific tools, techniques, and methodologies . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Company Vulnerability Administration Determine Approved Methods Of Vulnerability Assessment Microsoft PDF
Presenting company vulnerability administration determine approved methods of vulnerability assessment microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine the methods required by regulation, determine the methods required to meet the operational requirements, determine the legal implications, determine the impact imposed by candidate methods. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Vulnerability Assessment Methodology About Our Company Ppt Model Format Ideas PDF
Presenting this set of slides with name vulnerability assessment methodology about our company ppt model format ideas pdf. This is a three stage process. The stages in this process are preferred by many, value client, target audiences. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Circular Diagram Ppt Icon Summary PDF
Presenting this set of slides with name vulnerability assessment methodology circular diagram ppt icon summary pdf. This is a six stage process. The stages in this process are circular diagram. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
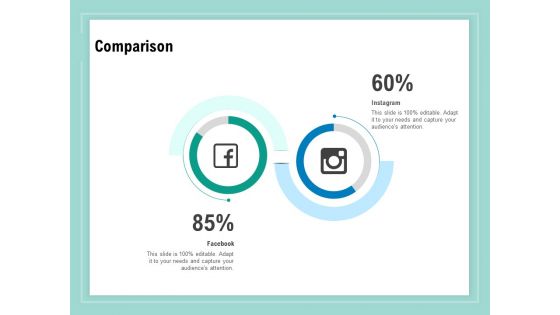
Vulnerability Assessment Methodology Comparison Ppt Show Clipart Images PDF
Presenting this set of slides with name vulnerability assessment methodology comparison ppt show clipart images pdf. This is a two stage process. The stages in this process are comparison. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Content Ppt Summary Infographics PDF
Presenting this set of slides with name vulnerability assessment methodology content ppt summary infographics pdf. The topics discussed in these slides are risk identification, risk register, risk assessment, risk analysis, risk mitigation plan, risk mitigation chart, risk tracker, risk management plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Icons Slide Ppt Styles Files PDF
Presenting this set of slides containing editable icons for topic vulnerability assessment methodology icons slide ppt styles files pdf. All icons in this slide are 100 percent editable. You can replace icons in your deck with any of these icons. Download now and impress your audience.
-
Vulnerability Assessment Methodology Linear Diagram Ppt Icon Graphics PDF
Presenting this set of slides with name vulnerability assessment methodology linear diagram ppt icon graphics pdf. This is a four stage process. The stages in this process are linear diagram. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Post It Notes Ppt Infographic Template Portrait PDF
Presenting this set of slides with name vulnerability assessment methodology post it notes ppt infographic template portrait pdf. This is a three stage process. The stages in this process are post it notes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
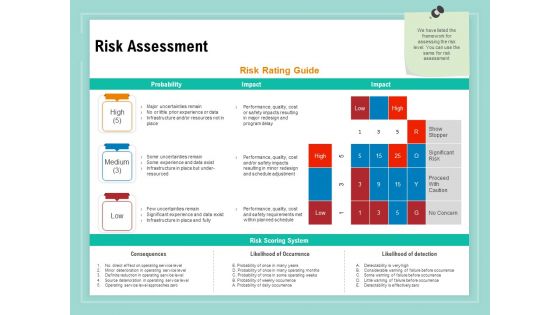
Vulnerability Assessment Methodology Risk Assessment Ppt File Samples PDF
Presenting this set of slides with name vulnerability assessment methodology risk assessment ppt file samples pdf. The topics discussed in these slides are consequences, likelihood of occurrence, likelihood of detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Item Tracking Ppt Professional Format Ideas PDF
Presenting this set of slides with name vulnerability assessment methodology risk item tracking ppt professional format ideas pdf. The topics discussed in these slides are risk item, monthly ranking, risk resolution. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Register Ppt Ideas Elements PDF
Presenting this set of slides with name vulnerability assessment methodology risk register ppt ideas elements pdf. The topics discussed in these slides are types of risk, description of risk, impact, risk reduction strategy, contingency plans, risk owner. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Tracker Ppt Icon Brochure PDF
Presenting this set of slides with name vulnerability assessment methodology risk tracker ppt icon brochure pdf. The topics discussed in these slides are description of risk, impact, high level, risk owner, risk response, notes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Roadmap Ppt Layouts Deck PDF
Presenting this set of slides with name vulnerability assessment methodology roadmap ppt layouts deck pdf. This is a five stage process. The stages in this process are roadmap. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Target Ppt Infographic Template Templates PDF
Presenting this set of slides with name vulnerability assessment methodology target ppt infographic template templates pdf. This is a four stage process. The stages in this process are target. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Thank You Ppt Infographic Template Designs PDF
Presenting this set of slides with name vulnerability assessment methodology thank you ppt infographic template designs pdf. This is a one stage process. The stages in this process are thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Timeline Ppt File Demonstration PDF
Presenting this set of slides with name vulnerability assessment methodology timeline ppt file demonstration pdf. This is a four stage process. The stages in this process are timeline, 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
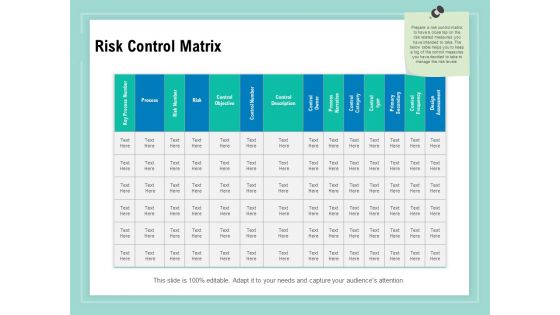
Vulnerability Assessment Methodology Risk Control Matrix Ppt Portfolio Infographics PDF
Presenting this set of slides with name vulnerability assessment methodology risk control matrix ppt portfolio infographics pdf. The topics discussed in these slides are key process number, process, risk number, risk, control objective, control number, control description, control owner, process narrative. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Mitigation Chart Ppt Portfolio Background Images PDF
Presenting this set of slides with name vulnerability assessment methodology risk mitigation chart ppt portfolio background images pdf. The topics discussed in these slides are scope creep, insufficient testing, insufficient resources. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Mitigation Plan Ppt Pictures Skills PDF
Presenting this set of slides with name vulnerability assessment methodology risk mitigation plan ppt pictures skills pdf. The topics discussed in these slides are category, identified risk, mitigation plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
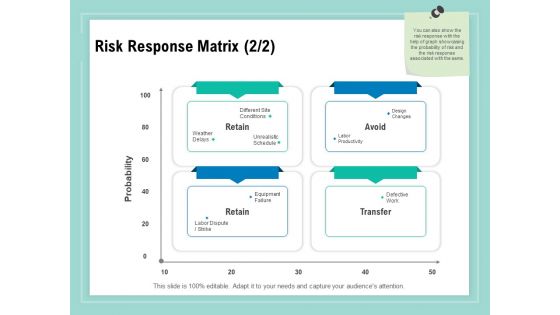
Vulnerability Assessment Methodology Risk Response Matrix Ppt Diagram Ppt PDF
Presenting this set of slides with name vulnerability assessment methodology risk response matrix ppt diagram ppt pdf. This is a four stage process. The stages in this process are retain, avoid, transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Response Plan Ppt Pictures PDF
Presenting this set of slides with name vulnerability assessment methodology risk response plan ppt pictures pdf. This is a eight stage process. The stages in this process are exploit, enhance, share, accept, avoid, mitigate, transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Venn Diagram Ppt Portfolio Clipart PDF
Presenting this set of slides with name vulnerability assessment methodology venn diagram ppt portfolio clipart pdf. This is a five stage process. The stages in this process are venn diagram. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Meet Our Awesome Team Ppt Infographic Template Slide PDF
Presenting this set of slides with name vulnerability assessment methodology meet our awesome team ppt infographic template slide pdf. This is a three stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
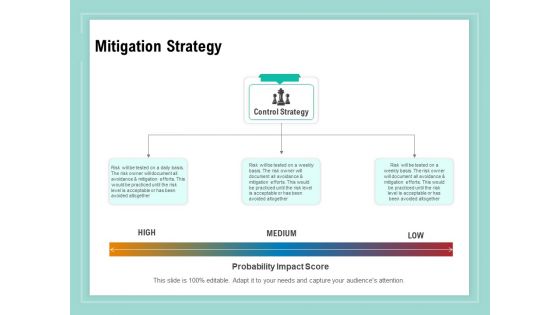
Vulnerability Assessment Methodology Mitigation Strategy Ppt Infographic Template Examples PDF
Presenting this set of slides with name vulnerability assessment methodology mitigation strategy ppt infographic template examples pdf. This is a three stage process. The stages in this process are high, medium, low. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Analysis Complex Ppt Outline Gridlines PDF
Presenting this set of slides with name vulnerability assessment methodology risk analysis complex ppt outline gridlines pdf. The topics discussed in these slides are description of risk, control measures, risk analysis, additional control, risk analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
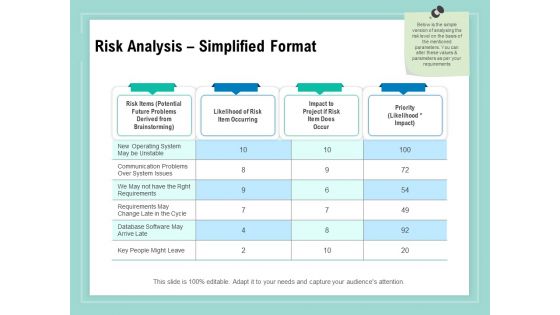
Vulnerability Assessment Methodology Risk Analysis Simplified Format Ppt Outline File Formats
Presenting this set of slides with name vulnerability assessment methodology risk analysis simplified format ppt outline file formats. The topics discussed in these slides are risk items, likelihood of risk item occurring, impact to project if risk item does occur, priority. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Assessment Contd Ppt Show Graphic Images PDF
Presenting this set of slides with name vulnerability assessment methodology risk assessment contd ppt show graphic images pdf. The topics discussed in these slides are extreme risk, high risk, moderate risk, low risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Identification Cost Ppt Professional Display PDF
Presenting this set of slides with name vulnerability assessment methodology risk identification cost ppt professional display pdf. This is a six stage process. The stages in this process are cost, resources, environmental, scope, communication, time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
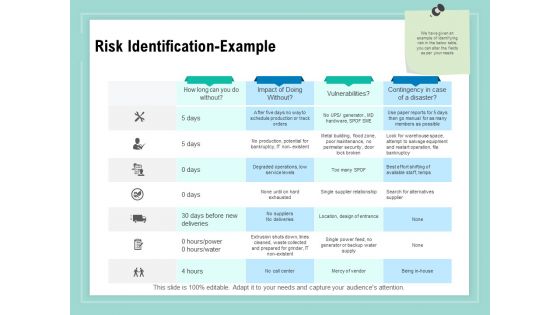
Vulnerability Assessment Methodology Risk Identification Example Ppt Portfolio Topics PDF
Presenting this set of slides with name vulnerability assessment methodology risk identification example ppt portfolio topics pdf. The topics discussed in these slides are contingency in case of a disaster, vulnerabilities, impact of doing without, how long can you do without. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Identification Treat Ppt Visual Aids Deck PDF
Presenting this set of slides with name vulnerability assessment methodology risk identification treat ppt visual aids deck pdf. This is a four stage process. The stages in this process are transfer, terminate, treat, tolerate. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Management Plan Ppt Inspiration Backgrounds PDF
Presenting this set of slides with name vulnerability assessment methodology risk management plan ppt inspiration backgrounds pdf. The topics discussed in these slides are types of risk, outcome, existing risk treatment actions in place, rating, proposed risk treatment actions to mitigate risk, additional resources, target date, person responsible. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Vulnerability Assessment Methodology Risk Mitigation Strategies Ppt Portfolio Templates PDF
Presenting this set of slides with name vulnerability assessment methodology risk mitigation strategies ppt portfolio templates pdf. The topics discussed in these slides are technical risks, cost risks, schedule risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Steps Of Vulnerability Assessment With Creating Backups Ppt PowerPoint Presentation Model Background Images PDF
Presenting this set of slides with name steps of vulnerability assessment with creating backups ppt powerpoint presentation model background images pdf. This is a eight stage process. The stages in this process are build an inventory of all it assets, categorize by risk and priority, monitor and evaluate patch updates, create backups, implement configuration management, implement configuration management, maintained patches regularly, document patch management process. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Internet Things Vulnerability Assessment Ppt PowerPoint Presentation Ideas Backgrounds Cpb Pdf
Presenting this set of slides with name internet things vulnerability assessment ppt powerpoint presentation ideas backgrounds cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like internet things vulnerability assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
Internet Things Vulnerability Assessment Ppt PowerPoint Presentation Slides Graphics Pictures Cpb
Presenting this set of slides with name internet things vulnerability assessment ppt powerpoint presentation slides graphics pictures cpb. This is an editable Powerpoint five stages graphic that deals with topics like internet things vulnerability assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
Web Vulnerability Assessment Ppt PowerPoint Presentation Layouts Slides Cpb
Presenting this set of slides with name web vulnerability assessment ppt powerpoint presentation layouts slides cpb. This is an editable Powerpoint five stages graphic that deals with topics like web vulnerability assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
Vulnerability Assessment Steps Ppt PowerPoint Presentation Model Icon Cpb
Presenting this set of slides with name vulnerability assessment steps ppt powerpoint presentation model icon cpb. This is an editable Powerpoint six stages graphic that deals with topics like vulnerability assessment steps to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
Vulnerability Assessment Matrix With Severity And Criticality Ppt PowerPoint Presentation Icon Infographic Template PDF
Presenting this set of slides with name vulnerability assessment matrix with severity and criticality ppt powerpoint presentation icon infographic template pdf. This is a five stage process. The stages in this process are vulnerability, severity, criticality. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
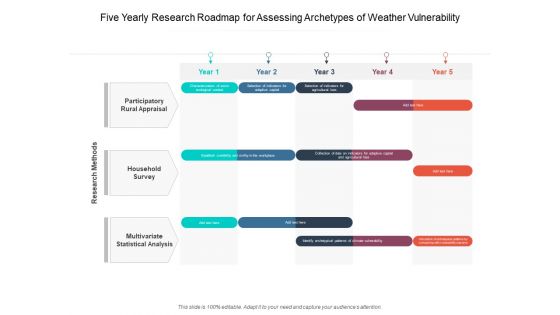
Five Yearly Research Roadmap For Assessing Archetypes Of Weather Vulnerability Microsoft
We present our five yearly research roadmap for assessing archetypes of weather vulnerability microsoft. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five yearly research roadmap for assessing archetypes of weather vulnerability microsoft in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
-
Half Yearly Research Roadmap For Assessing Archetypes Of Weather Vulnerability Sample
We present our half yearly research roadmap for assessing archetypes of weather vulnerability sample. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly research roadmap for assessing archetypes of weather vulnerability sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
-
Quarterly Research Roadmap For Assessing Archetypes Of Weather Vulnerability Formats
We present our quarterly research roadmap for assessing archetypes of weather vulnerability formats. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched quarterly research roadmap for assessing archetypes of weather vulnerability formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
-
Six Months Research Roadmap For Assessing Archetypes Of Weather Vulnerability Background
We present our six months research roadmap for assessing archetypes of weather vulnerability background. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months research roadmap for assessing archetypes of weather vulnerability background in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
-
Three Months Research Roadmap For Assessing Archetypes Of Weather Vulnerability Introduction
We present our three months research roadmap for assessing archetypes of weather vulnerability introduction. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched three months research roadmap for assessing archetypes of weather vulnerability introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
-
Internet Security Risk Assessment Report With Vulnerability And Impact Ppt PowerPoint Presentation Icon Backgrounds PDF
Pitch your topic with ease and precision using this internet security risk assessment report with vulnerability and impact ppt powerpoint presentation icon backgrounds pdf. This layout presents information on vulnerability, asset, impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
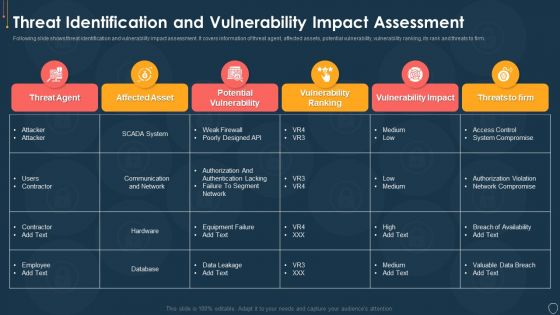
Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
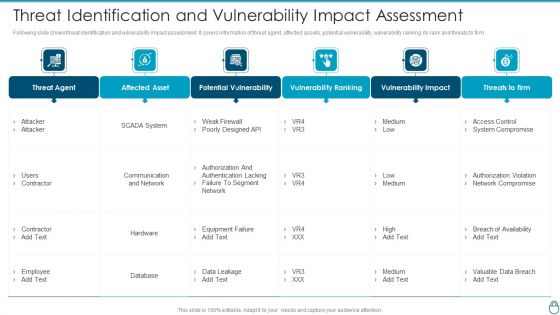
Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF bundle. Topics like Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Mitigating Cybersecurity Threats And Vulnerabilities Comparative Assessment Of Various Background PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities comparative assessment of various background pdf bundle. Topics like social engineering, insider threat, maintenance threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
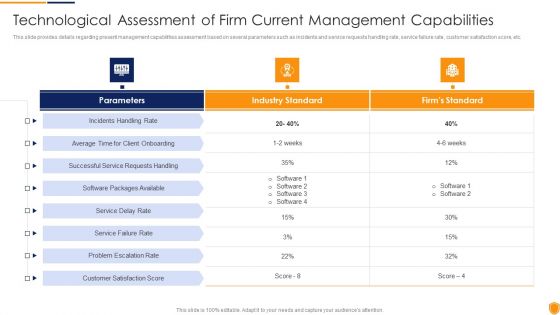
Mitigating Cybersecurity Threats And Vulnerabilities Technological Assessment Sample PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities technological assessment sample pdf bundle. Topics like Industry Standard, Firms Standard, Client Onboarding, Service Failure Rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
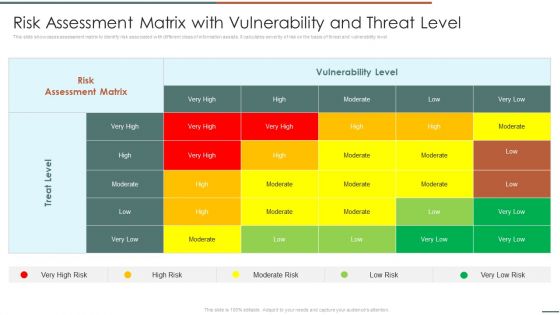
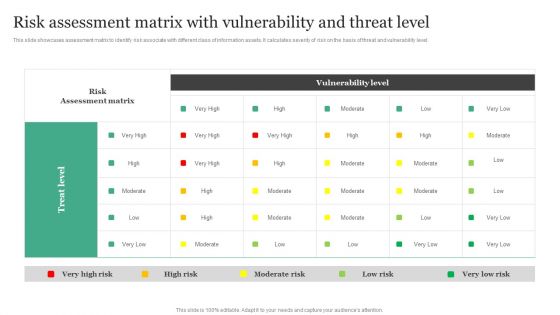
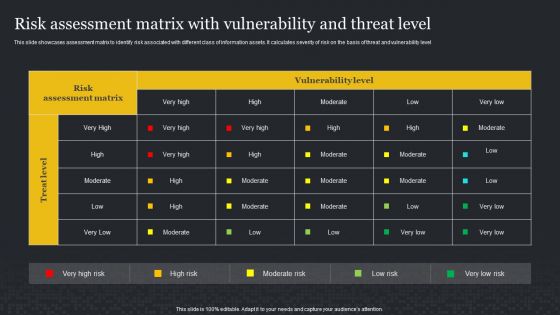
Information Security Risk Evaluation Risk Assessment Matrix With Vulnerability And Threat Level Mockup PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Risk Assessment Matrix With Vulnerability And Threat Level Mockup PDF bundle. Topics like Risk Assessment, Vulnerability Level, Treat Level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
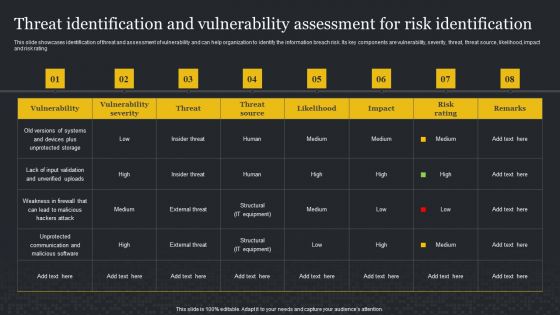
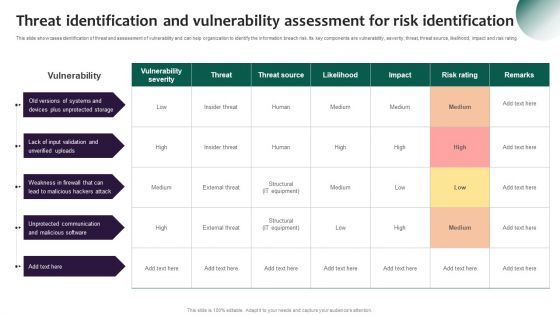
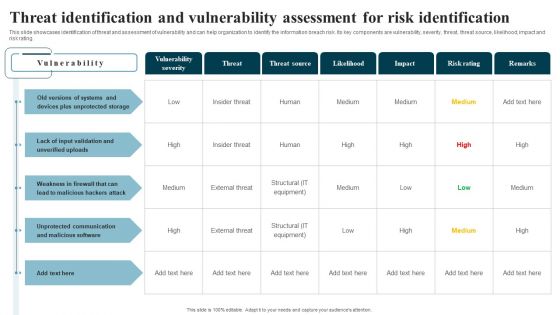
Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF. Use them to share invaluable insights on Vulnerability Severity, Unprotected Storage, Unprotected Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
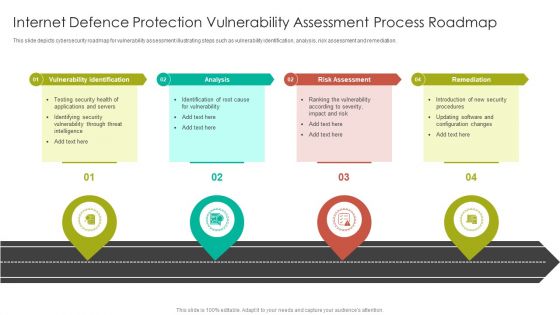
Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF
This slide depicts cybersecurity roadmap for vulnerability assessment illustrating steps such as vulnerability identification, analysis, risk assessment and remediation.Presenting Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Identification, Risk Assessment, Remediation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
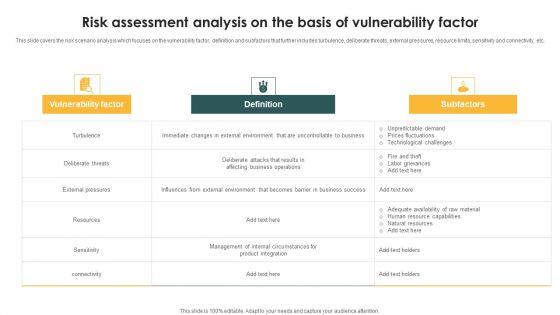
Risk Assessment Analysis On The Basis Of Vulnerability Factor Ppt PowerPoint Presentation Gallery Example Introduction PDF
This slide covers the risk scenario analysis which focuses on the vulnerability factor, definition and subfactors that further includes turbulence, deliberate threats, external pressures, resource limits, sensitivity and connectivity, etc. Showcasing this set of slides titled Risk Assessment Analysis On The Basis Of Vulnerability Factor Ppt PowerPoint Presentation Gallery Example Introduction PDF. The topics addressed in these templates are Vulnerability Factor, Definition, Subfactors, Turbulence. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF
This slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level.Boost your pitch with our creative Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
-
Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Get a simple yet stunning designed Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
-
Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Find highly impressive Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF for your upcoming presentation. All the presentation templates are 100 parcent editable and you can change the color and personalize the content accordingly. Download now.
-
Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Explore a selection of the finest Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
-
Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
-
Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
-
Corporate Vulnerability Analysis Assessment Model Elements PDF
This slide showcases the enterprise vulnerability management assessment model that routinely checks the network for flaws, provides risk insights, and aids in immediately closing the loop on vulnerability management. It also includes stages such as asset discovery, scanning, remediation, assessment, etc. Presenting Corporate Vulnerability Analysis Assessment Model Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Assessment, Vulnerability Scanning, Asset Discovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
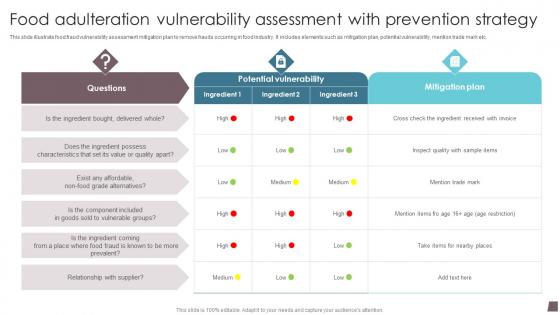
Food Adulteration Vulnerability Assessment With Prevention Strategy Formats Pdf
This slide illustrate food fraud vulnerability assessment mitigation plan to remove frauds occurring in food industry. It includes elements such as mitigation plan, potential vulnerability, mention trade mark etc. Showcasing this set of slides titled Food Adulteration Vulnerability Assessment With Prevention Strategy Formats Pdf. The topics addressed in these templates are Strategy, Food, Vulnerability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
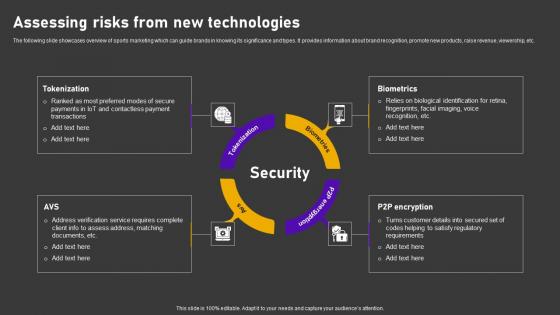
Assessing Risks From New Minimizing Customer Transaction Vulnerabilities Professional Pdf
The following slide showcases overview of sports marketing which can guide brands in knowing its significance and types. It provides information about brand recognition, promote new products, raise revenue, viewership, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Assessing Risks From New Minimizing Customer Transaction Vulnerabilities Professional Pdf from Slidegeeks and deliver a wonderful presentation.
-
Vulnerability Assessment In Powerpoint And Google Slides Cpb
Introducing our well designed Vulnerability Assessment In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Vulnerability Assessment. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.