Threat source PowerPoint Presentation Templates and Google Slides
-
Threat Intelligence Sources Ppt PowerPoint Presentation Pictures Designs Cpb Pdf
Presenting this set of slides with name threat intelligence sources ppt powerpoint presentation pictures designs cpb pdf. This is an editable Powerpoint eleven stages graphic that deals with topics like threat intelligence sources to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
Mitigation Strategies For Operational Threat Operational Risk Event Sources And Causes Ppt Inspiration Introduction PDF
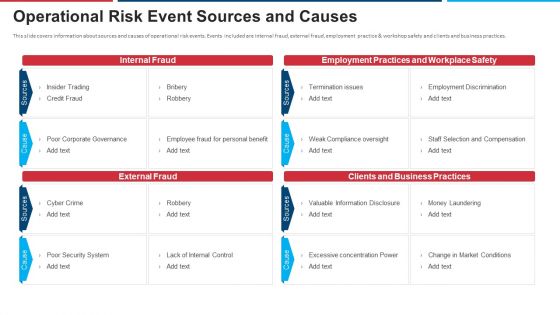
This slide covers information about sources and causes of operational risk events. Events included are internal fraud, external fraud, employment practice and workshop safety and clients and business practices. Deliver an awe inspiring pitch with this creative mitigation strategies for operational threat operational risk event sources and causes ppt inspiration introduction pdf bundle. Topics like internal fraud, external fraud, employment practices and workplace safety, clients and business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Threat Management At Workplace Addressing Internal And External Sources Of Threat Data Microsoft Pdf
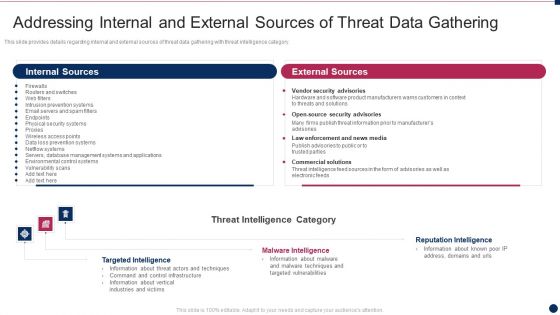
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver and pitch your topic in the best possible manner with this threat management at workplace addressing internal and external sources of threat data microsoft pdf. Use them to share invaluable insights on vendor security advisories, law enforcement and news media, commercial solutions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF
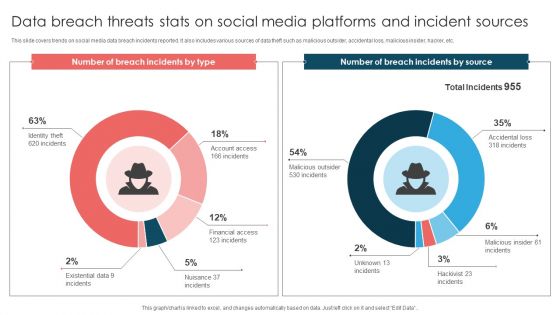
This slide covers trends on social media data breach incidents reported. It also includes various sources of data theft such as malicious outsider, accidental loss, malicious insider, hacker, etc. Pitch your topic with ease and precision using this Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF. This layout presents information on Number Breach, Total Incidents, Malicious Insider. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Information Technology Threat Mitigation Methods IT Vulnerabilities With Threat Source And Action Template PDF
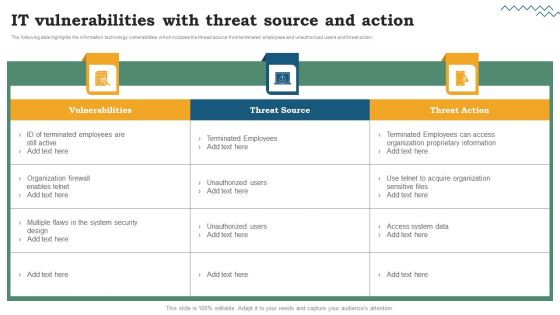
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. This is a Information Technology Threat Mitigation Methods IT Vulnerabilities With Threat Source And Action Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerabilities, Threat Source, Threat Action. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Information Technology Threat Mitigation Methods Information Technology Risks Form Human Threat Source Ideas PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Information Technology Risks Form Human Threat Source Ideas PDF bundle. Topics like Computer Criminal, Industrial Espionage, System Intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Information Technology Risks Form Human Threat Source Summary PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. If you are looking for a format to display your unique thoughts, then the professionally designed Information Technology Risks Form Human Threat Source Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Technology Risks Form Human Threat Source Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
-
IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.
-
IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
-
IT System Risk Management Guide IT Vulnerabilities With Threat Source And Action Guidelines PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created IT System Risk Management Guide IT Vulnerabilities With Threat Source And Action Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
-
Software Development Life Cycle Planning IT Vulnerabilities With Threat Source And Action Structure PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Welcome to our selection of the Software Development Life Cycle Planning IT Vulnerabilities With Threat Source And Action Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
-
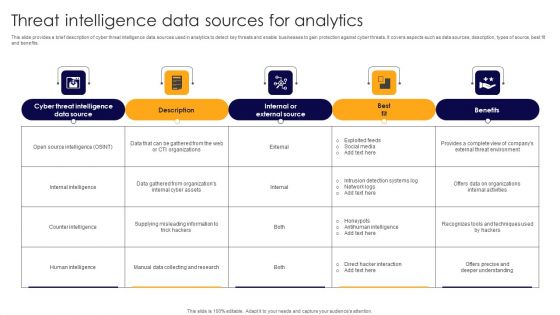
Threat Intelligence Data Sources For Analytics Ideas PDF
This slide provides a brief description of cyber threat intelligence data sources used in analytics to detect key threats and enable businesses to gain protection against cyber threats. It covers aspects such as data sources, description, types of source, best fit and benefits. Showcasing this set of slides titled Threat Intelligence Data Sources For Analytics Ideas PDF. The topics addressed in these templates are Exploited Feeds, Social Media, Intrusion Detection Systems Log. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Addressing Internal And External Sources Of Threat Data Monitoring Digital Assets Demonstration Pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Addressing Internal And External Sources Of Threat Data Monitoring Digital Assets Demonstration Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Addressing Internal And External Sources Of Threat Data Monitoring Digital Assets Demonstration Pdf