Threat procedure PowerPoint Presentation Templates and Google Slides
-
Threat Procedure Ppt PowerPoint Presentation Complete Deck With Slides
This Threat Procedure Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing thriteen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Threat Procedure Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.
-
Procedure Advancements Banking Department Swot Analysis Threats Clipart PDF
The slide shows the key threats which might affect the companys operations in future. Major points include competitive market, operational risks, legal risks etc. This is a procedure advancements banking department swot analysis threats clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threats, competition, operational risk, legal risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
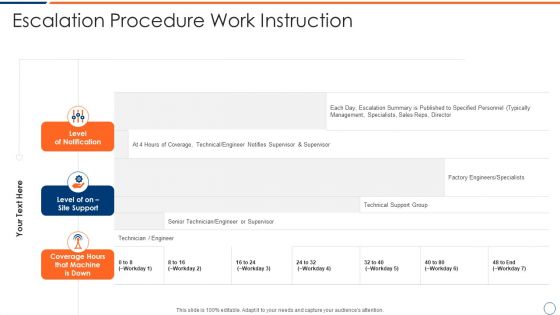
How To Intensify Project Threats Escalation Procedure Work Instruction Elements PDF
This is a how to intensify project threats escalation procedure work instruction elements pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like level of notification, level of on site support, coverage hours that machine is down. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Circle Procedure Infographic To Manage Threat Detection And Response Ppt Styles Sample PDF
Persuade your audience using this circle procedure infographic to manage threat detection and response ppt styles sample pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including circle procedure infographic to manage threat detection and response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
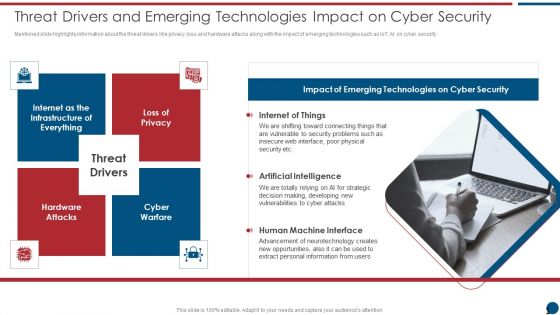
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
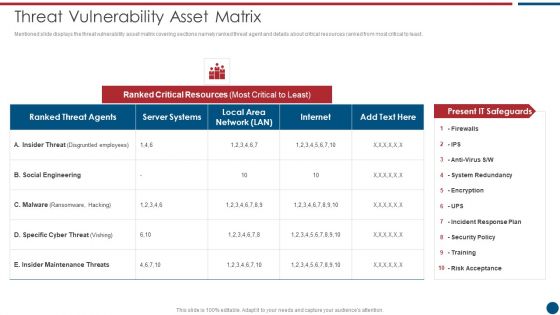
Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF bundle. Topics like Ranked Critical, Server Systems, Social Engineering can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Threat Management Strategy With Control Procedures Pictures PDF
This slide focuses on the risk mitigation plan that covers risks related to business, project environment, vendor project manager and project team support which includes targets and control procedures such as implement status reporting, involving vendors, etc. Showcasing this set of slides titled Threat Management Strategy With Control Procedures Pictures PDF. The topics addressed in these templates are Project Environment, Business, Project Team Support. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Retail Business Product Planning Procedure Risk Management Plan To Mitigate Threats Designs PDF
This slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Deliver and pitch your topic in the best possible manner with this Retail Business Product Planning Procedure Risk Management Plan To Mitigate Threats Designs PDF. Use them to share invaluable insights on Contingency Plan, Secondary Risk, Probability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
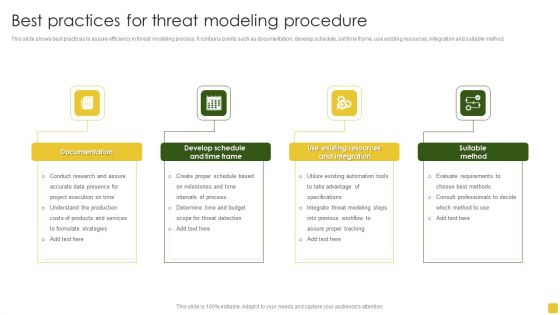
Best Practices For Threat Modeling Procedure Themes PDF
This slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method.Presenting Best Practices For Threat Modeling Procedure Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Project Execution, Determine Budget, Existing Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Business Application Threat Modeling Procedure Designs PDF
This slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Persuade your audience using this Business Application Threat Modeling Procedure Designs PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Examine Existing, Understand Capabilities, Recommendations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Business Threat Modeling Procedure Icon Designs PDF
Showcasing this set of slides titled Business Threat Modeling Procedure Icon Designs PDF. The topics addressed in these templates are Business Threat, Modeling Procedure Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
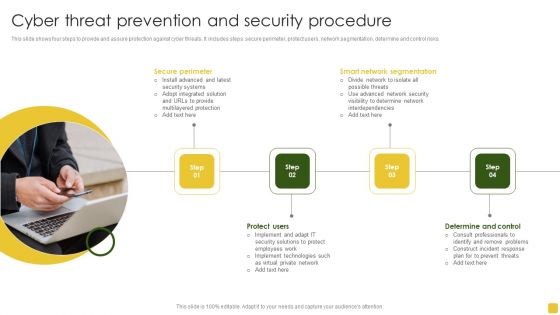
Cyber Threat Prevention And Security Procedure Elements PDF
This slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Presenting Cyber Threat Prevention And Security Procedure Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Control, Smart Network Segmentation, Secure Perimeter. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
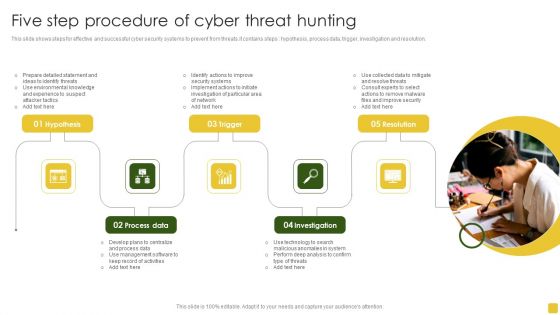
Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Insider Threat Mitigation And Protection Procedure Professional PDF
This slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage.Presenting Insider Threat Mitigation And Protection Procedure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigation Program, Compile Information, Determine Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
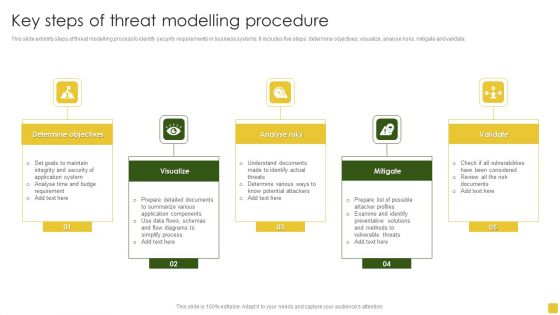
Key Steps Of Threat Modelling Procedure Brochure PDF
This slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate.Persuade your audience using this Key Steps Of Threat Modelling Procedure Brochure PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Determine Objectives, Preventative Solutions, Determine Various Ways. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Procedure To Conduct Business Threat Assessment Topics PDF
This slide exhibits process to perform business threat assessment that helps to identify and develop mitigation strategies. It includes four steps identify threats, assess threats, develop controls and evaluate response.Presenting Procedure To Conduct Business Threat Assessment Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Threats, Examine Threats, Develop Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
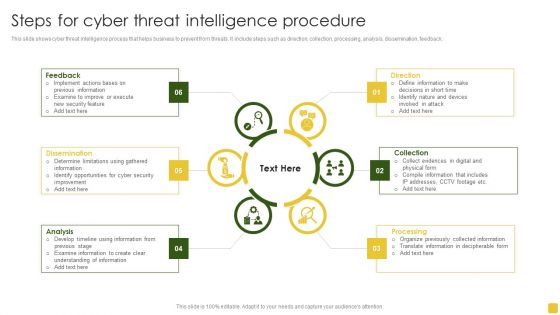
Steps For Cyber Threat Intelligence Procedure Ideas PDF
This slide shows cyber threat intelligence process that helps business to prevent from threats. It include steps such as direction, collection, processing, analysis, dissemination, feedback.Persuade your audience using this Steps For Cyber Threat Intelligence Procedure Ideas PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Previous Information, Examine Improve, Determine Limitations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
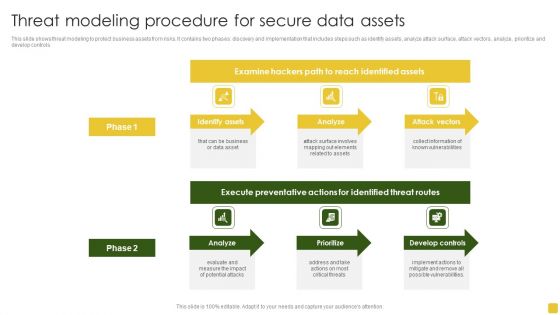
Threat Modeling Procedure For Secure Data Assets Formats PDF
This slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Pitch your topic with ease and precision using this Threat Modeling Procedure For Secure Data Assets Formats PDF. This layout presents information on Execute Preventative, Identified Threat, Develop Controls. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
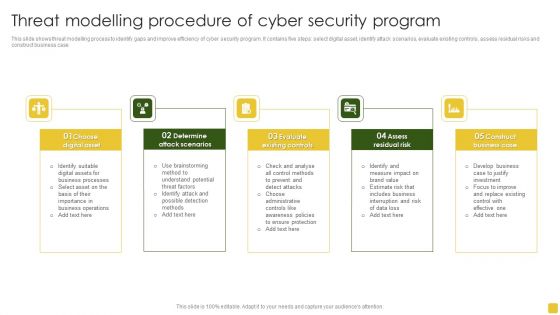
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.