Threat assessment PowerPoint Presentation Templates and Google Slides
-
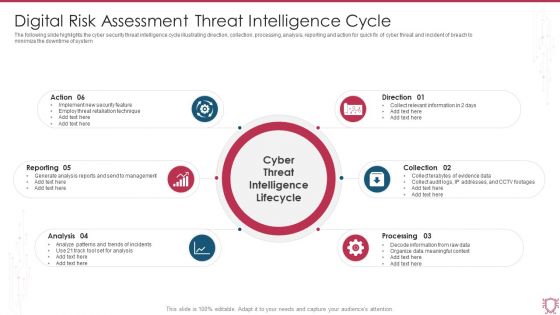
Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF
The following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Persuade your audience using this Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Reporting, Analysis, Processing, Direction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
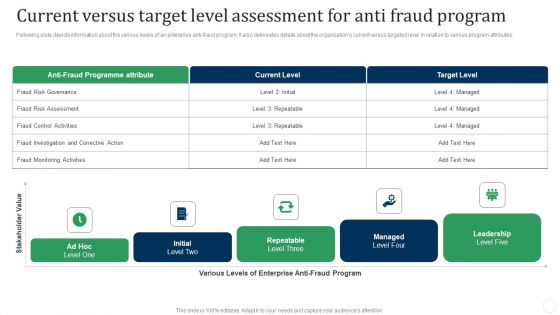
Current Versus Target Level Assessment For Anti Fraud Program Fraud Threat Administration Guide Microsoft PDF
Following slide depicts information about the various levels of an enterprise anti-fraud program. It also delineates details about the organizations current versus targeted level in relation to various program attributes.Deliver an awe inspiring pitch with this creative Current Versus Target Level Assessment For Anti Fraud Program Fraud Threat Administration Guide Microsoft PDF bundle. Topics like Programmed Attribute, Fraud Investigation, Monitoring Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
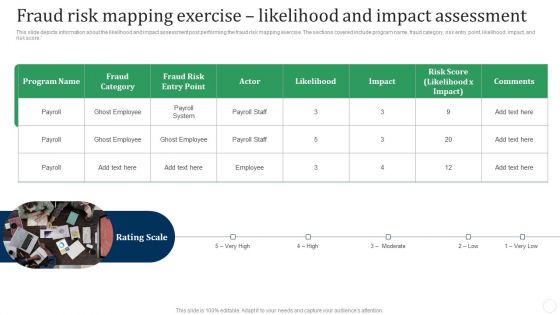
Fraud Risk Mapping Exercise Likelihood And Impact Assessment Fraud Threat Administration Guide Demonstration PDF
This slide depicts information about the likelihood and impact assessment post performing the fraud risk mapping exercise. The sections covered include program name, fraud category, risk entry point, likelihood, impact, and risk score.This is a Fraud Risk Mapping Exercise Likelihood And Impact Assessment Fraud Threat Administration Guide Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Fraud Category, Ghost Employee, Fraud Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Risk Management Icon Indicating Threat Assessment Download PDF
Presenting Risk Management Icon Indicating Threat Assessment Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Management Icon Indicating, Threat Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
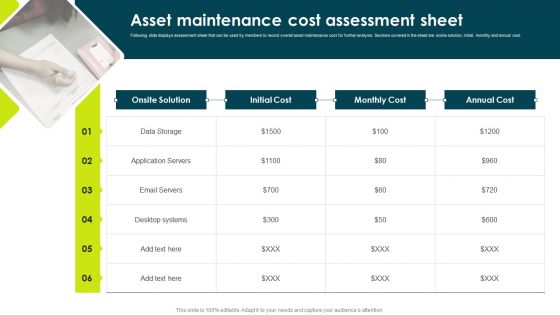
IT Threats Response Playbook Asset Maintenance Cost Assessment Sheet Clipart PDF
Following slide displays assessment sheet that can be used by members to record overall asset maintenance cost for further analysis. Sections covered in the sheet are onsite solution, initial, monthly and annual cost.This is a IT Threats Response Playbook Asset Maintenance Cost Assessment Sheet Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Servers, Desktop Systems, Onsite Solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
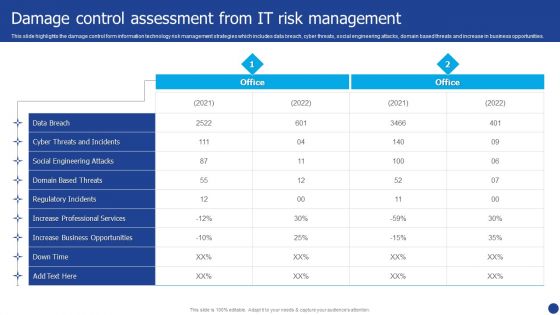
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
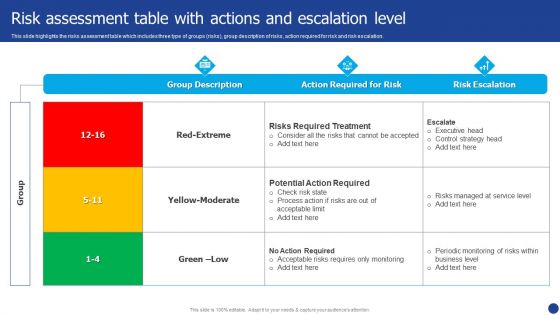
Information Technology Threat Mitigation Methods Risk Assessment Table With Actions And Escalation Level Elements PDF
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Risk Assessment Table With Actions And Escalation Level Elements PDF bundle. Topics like Action Required For Risk, Risk Escalation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
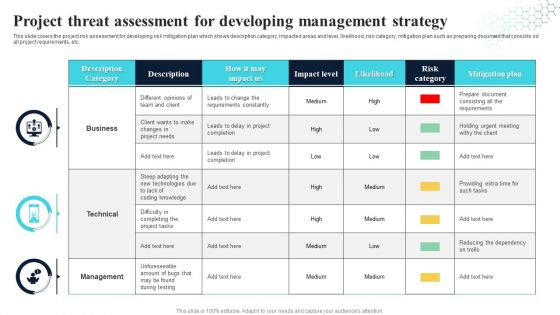
Project Threat Assessment For Developing Management Strategy Information PDF
This slide covers the project risk assessment for developing risk mitigation plan which shows description category, impacted areas and level, likelihood, risk category, mitigation plan such as preparing document that consists od all project requirements, etc. Showcasing this set of slides titled Project Threat Assessment For Developing Management Strategy Information PDF. The topics addressed in these templates are Technical, Management, Business. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Supplier Threat Management Strategy With Assessment Infographics PDF
This slide shows the supplier risk mitigation plan which includes identification, assessment, prioritization, planning and management that focuses on the potential risks for vendors, assessing likelihood and impact, identify top priority threats, mitigation action plans, etc. Presenting Supplier Threat Management Strategy With Assessment Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prioritize, Identify, Assess, Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
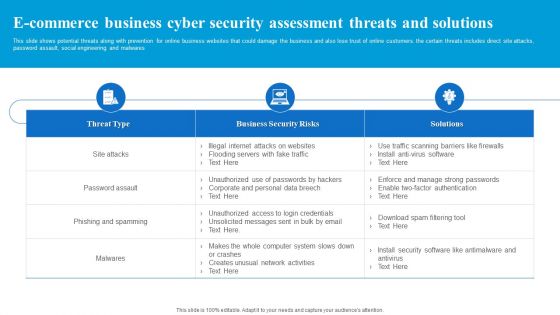
E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF
This slide shows potential threats along with prevention for online business websites that could damage the business and also lose trust of online customers. the certain threats includes direct site attacks, password assault, social engineering and malwares. Showcasing this set of slides titled E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF. The topics addressed in these templates are Business Security Risks, Threat Type, Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on.Presenting Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Compliance Violations In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.This is a Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Serious Repercussions, Data In The Business, Organizations Should You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
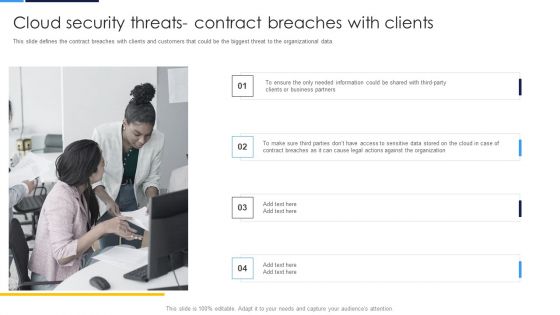
Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data.Presenting Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Partners, Contract Breaches, Against The Organization In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.This is a Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Rival Organizations, Cybercriminals, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Presenting Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Storage Locations, Natural Disasters, Massive Impact. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
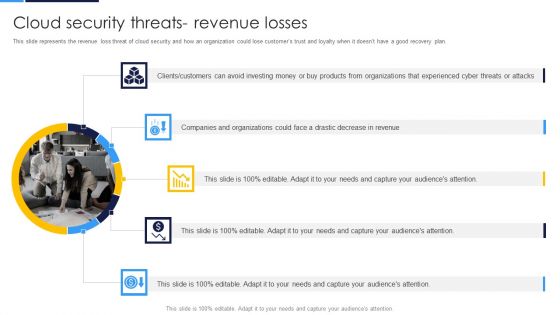
Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
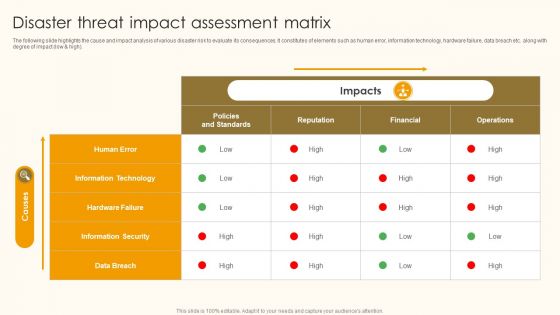
Disaster Threat Impact Assessment Matrix Ppt Ideas Design Templates PDF
The following slide highlights the cause and impact analysis of various disaster risk to evaluate its consequences. It constitutes of elements such as human error, information technology, hardware failure, data breach etc. along with degree of impact low and high. Showcasing this set of slides titled Disaster Threat Impact Assessment Matrix Ppt Ideas Design Templates PDF. The topics addressed in these templates are Human Error, Information Technology, Hardware Failure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Disaster Threat Severity Assessment Icon Ppt Show Slides PDF
Persuade your audience using this Disaster Threat Severity Assessment Icon Ppt Show Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Disaster Threat, Severity Assessment, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
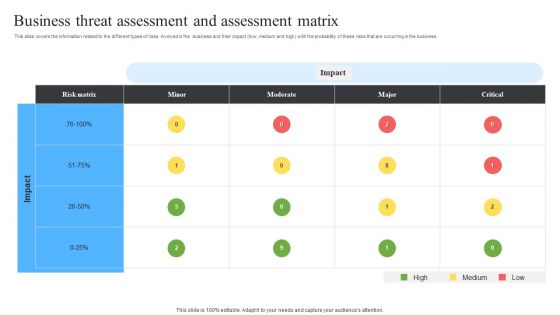
Business Threat Assessment And Assessment Matrix Ppt Infographics Good PDF
This slide covers the information related to the different types of risks involved in the business and their impact low, medium and high with the probability of these risks that are occurring in the business. Showcasing this set of slides titled Business Threat Assessment And Assessment Matrix Ppt Infographics Good PDF. The topics addressed in these templates are Risk Matrix, Moderate, Critical, High, Low, Medium. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Mutual Funds Threat Assessment With Credit Rating Ppt Professional Icons PDF
This slide shows the risk analysis of mutual funds. It also includes credit ratings, risk level , likelihood of the risk occurrence and assets under management. Pitch your topic with ease and precision using this Mutual Funds Threat Assessment With Credit Rating Ppt Professional Icons PDF. This layout presents information on Schemes, Credit Rating, Risk Level, Likelihood. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Product Threat Assessment And Analysis Checklist Ppt Icon Files PDF
This slide covers the check points under the assessment of risks that could come up during the product manufacturing or selling. It helps in analyzing the problems and to know what have to be done. Showcasing this set of slides titled Product Threat Assessment And Analysis Checklist Ppt Icon Files PDF. The topics addressed in these templates are Check Point, Defect Statement, Appropriate Column. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Project Threat Assessment Plan With Severity Ppt Professional Design Inspiration PDF
This slide contains the multiple risk that occurs while working on a project . It also includes the likelihood , severity with the plans to reduce the risk. Showcasing this set of slides titled Project Threat Assessment Plan With Severity Ppt Professional Design Inspiration PDF. The topics addressed in these templates are Risk, Likelihood, Severity, Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Project Threat Assessment With Date And Impact Ppt File Layout Ideas PDF
This slide covers the risk of the projects that have occurred during the working with their impact on the project and the description of the risk. It also includes the employee ID and the owners who are dealing with these risks. Pitch your topic with ease and precision using this Project Threat Assessment With Date And Impact Ppt File Layout Ideas PDF. This layout presents information on Employee ID, Risk Description, Project Design Incomplete. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
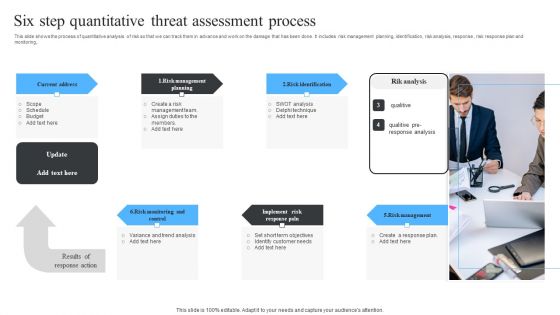
Six Step Quantitative Threat Assessment Process Ppt Gallery Portrait PDF
This slide shows the process of quantitative analysis of risk so that we can track them in advance and work on the damage that has been done. It includes risk management planning, identification, risk analysis, response, risk response plan and monitoring, Presenting Six Step Quantitative Threat Assessment Process Ppt Gallery Portrait PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Current Address, Risk Identification, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Threat Assessment Icon With Magnifying Glass Ppt Icon Topics PDF
Presenting Threat Assessment Icon With Magnifying Glass Ppt Icon Topics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threat Assessment Icon, Magnifying Glass. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Threat Assessment Process Icon With Statistics Ppt Slides Styles PDF
Persuade your audience using this Threat Assessment Process Icon With Statistics Ppt Slides Styles PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Threat Assessment Process, Icon With Statistics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
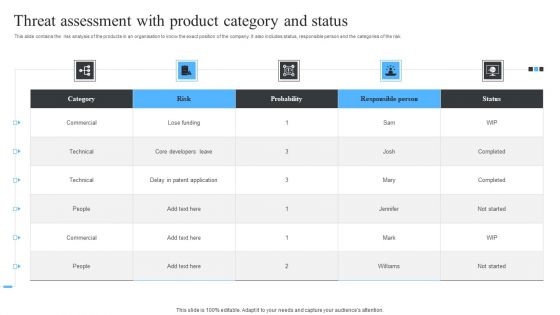
Threat Assessment With Product Category And Status Ppt Slides Master Slide PDF
This slide contains the risk analysis of the products in an organisation to know the exact position of the company. It also includes status, responsible person and the categories of the risk. Pitch your topic with ease and precision using this Threat Assessment With Product Category And Status Ppt Slides Master Slide PDF. This layout presents information on Risk, Probability, Commercial. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Five Step Financial Data Threats Assessment Process Ppt Infographic Template File Formats PDF
This slide covers five steps process for risk assessment of financial data. It includes steps as formation of data security governance framework, identify data set, financial liabilities risk assessment, prioritization of data sets and budget preparation. Presenting Five Step Financial Data Threats Assessment Process Ppt Infographic Template File Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Maturity Path, Budget Preparation, Prioritize Data Sets, Identify Data Set. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Key Components Of Risk Assessment With Threat Type Ppt PowerPoint Presentation File Summary PDF
This slide focuses on the key components of risk scenario which focuses on management, threat type, event, resource and time that further includes staff members, contractors, competitors, natural disasters, modifications, processes, data management, interruptions, etc. Persuade your audience using this Key Components Of Risk Assessment With Threat Type Ppt PowerPoint Presentation File Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Management, Threat Type, Event, Time. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
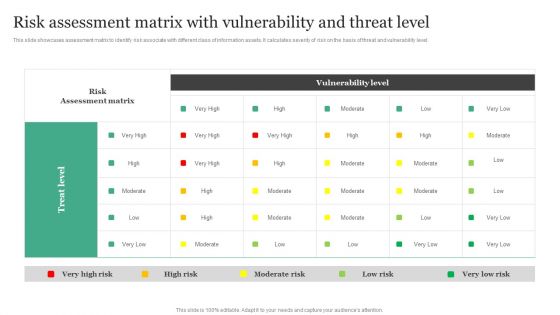
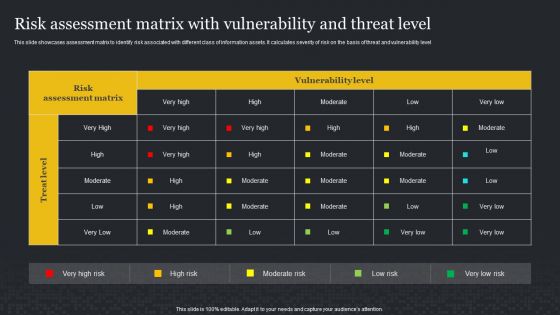
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF
This slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level.Boost your pitch with our creative Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
-
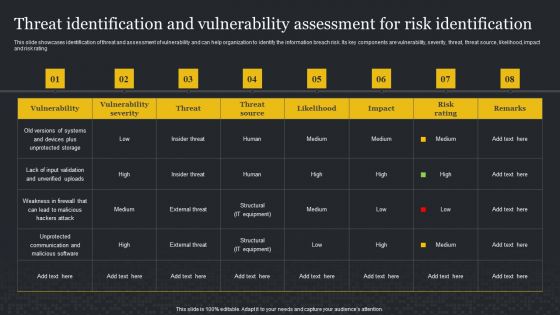
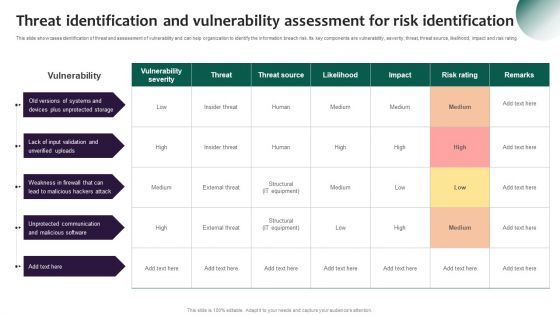
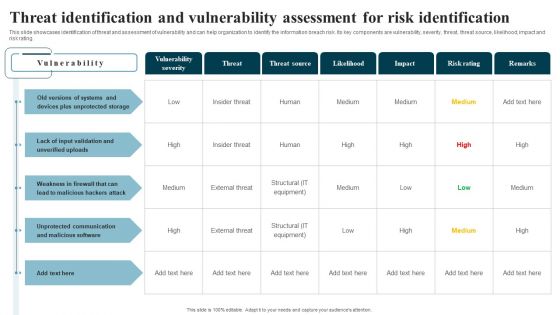
Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Get a simple yet stunning designed Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
-
Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. Find a pre-designed and impeccable Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
-
Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
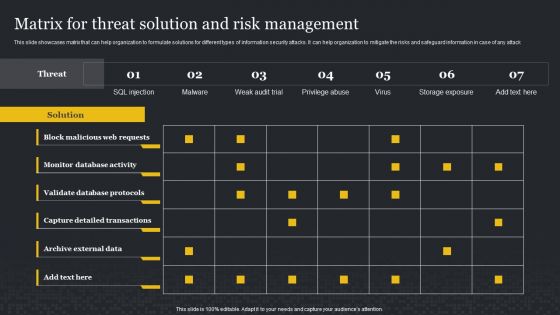
Matrix For Threat Solution And Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Get a simple yet stunning designed Matrix For Threat Solution And Risk Management Cybersecurity Risk Assessment Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Matrix For Threat Solution And Risk Management Cybersecurity Risk Assessment Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
-
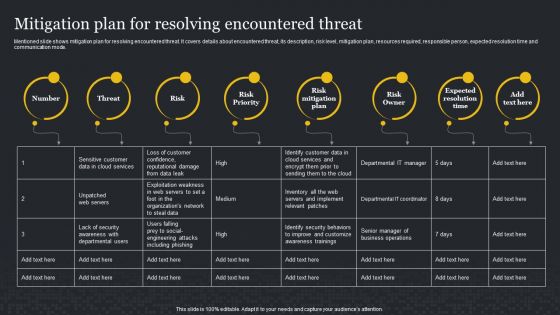
Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Find highly impressive Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF for your upcoming presentation. All the presentation templates are 100 parcent editable and you can change the color and personalize the content accordingly. Download now.
-
Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF
-
Procedure To Conduct Business Threat Assessment Topics PDF
This slide exhibits process to perform business threat assessment that helps to identify and develop mitigation strategies. It includes four steps identify threats, assess threats, develop controls and evaluate response.Presenting Procedure To Conduct Business Threat Assessment Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Threats, Examine Threats, Develop Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Online Security Threat And Risk Assessment Matrix Formats PDF
This slide showcases digital safety risk assessment matrix which helps analyze impact of threat on business processes. It provides information regarding hacking, data breaches, information misuse, malicious attacks and system failure. Showcasing this set of slides titled Online Security Threat And Risk Assessment Matrix Formats PDF. The topics addressed in these templates are Information Misuse, Data Breaches, Malicious Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Explore a selection of the finest Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
-
Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
-
Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
-
Assessment Of Amazon Brand Performance Major Threats That Creates Obstacles Brochure PDF
This slide provides information regarding SWOT analysis technique utilized by Amazon to evaluate its competitive positioning. The slide highlighting threats faced by Amazon causing potential issues in terms of data and online privacy risk, aggressive pricing strategies, etc. Want to ace your presentation in front of a live audience Our Assessment Of Amazon Brand Performance Major Threats That Creates Obstacles Brochure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
-
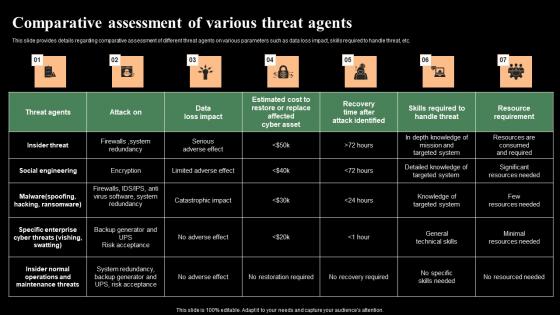
Comparative Assessment Of Various Threat Agents Monitoring Digital Assets Sample Pdf
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Find a pre-designed and impeccable Comparative Assessment Of Various Threat Agents Monitoring Digital Assets Sample Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
-
Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf
The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf.