Security Rules PowerPoint Presentation Templates and Google Slides
-
Cyber Security Network Security Ppt PowerPoint Presentation Show Rules
This is a cyber security network security ppt powerpoint presentation show rules. This is a nine stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
-
Security Governance Icon Ppt PowerPoint Presentation Layouts Rules
This is a security governance icon ppt powerpoint presentation layouts rules. This is a four stage process. The stages in this process are risk management icon, governance icon, compliance icon.
-
Mobile Device Security Best Practices Ppt PowerPoint Presentation Outline Rules Cpb
This is a mobile device security best practices ppt powerpoint presentation outline rules cpb. This is a four stage process. The stages in this process are mobile device security best practices.
-
Business Organizational Security Management Ppt PowerPoint Presentation Pictures Rules
Presenting this set of slides with name business organizational security management ppt powerpoint presentation pictures rules. This is an editable Powerpoint three stages graphic that deals with topics like business organizational security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
Cyber Security Rules And Regulations With Accuracy Ppt PowerPoint Presentation Slides Outfit
Presenting this set of slides with name cyber security rules and regulations with accuracy ppt powerpoint presentation slides outfit. This is a six stage process. The stages in this process are purpose and manner of collection, accuracy and duration of retention, use of personal data, security of personal data, information to be generally available, access to personal data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Uniformed Security Next Steps In The Security Guard Services Proposal Rules PDF
Presenting uniformed security next steps in the security guard services proposal rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like next steps. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cloud Based Email Security Market Report Hosted E Mail Security Ppt Ideas Rules PDF
This slide displays the overview and key features of hosted E Mail Security. This is a cloud based email security market report hosted e mail security ppt ideas rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintenance, security, miscellaneous, protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Data Folder Security Vector Icon Ppt PowerPoint Presentation File Rules PDF
Persuade your audience using this data folder security vector icon ppt powerpoint presentation file rules pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including data folder security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Half Yearly Information Technology Security Roadmap For Continuous Threat Analysis Rules
Presenting the half yearly information technology security roadmap for continuous threat analysis rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
-
Half Yearly Network Information Technology Security Development Roadmap Rules
Presenting our jaw dropping half yearly network information technology security development roadmap rules. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
-
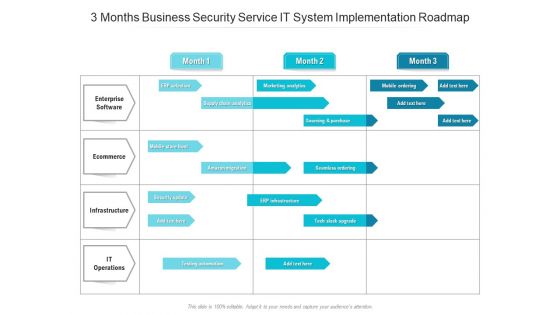
3 Months Business Security Service IT System Implementation Roadmap Rules
We present our 3 months business security service it system implementation roadmap rules. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched 3 months business security service it system implementation roadmap rules in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
-
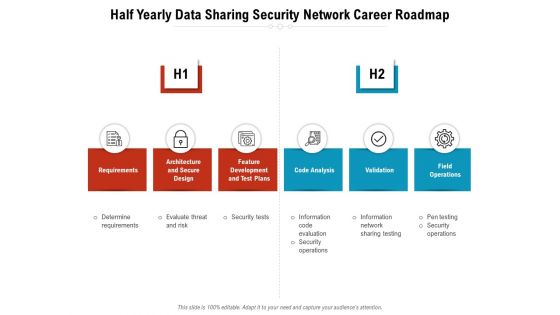
Half Yearly Data Sharing Security Network Career Roadmap Rules
We present our half yearly data sharing security network career roadmap rules. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly data sharing security network career roadmap rules in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
-
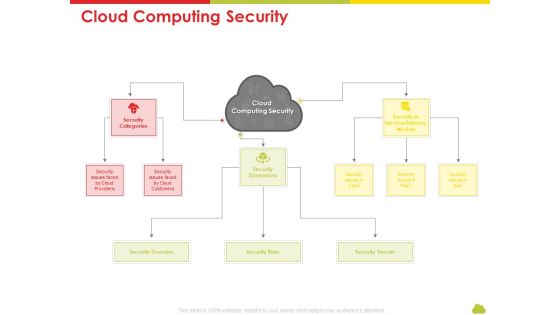
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Cloud Computing Security Rules PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan cloud computing security rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like risks, threats, domains, service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Business Firms Safety And Security Rules Vector Icon Ppt PowerPoint Presentation Gallery Maker PDF
Persuade your audience using this business firms safety and security rules vector icon ppt powerpoint presentation gallery maker pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including business firms safety and security rules vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
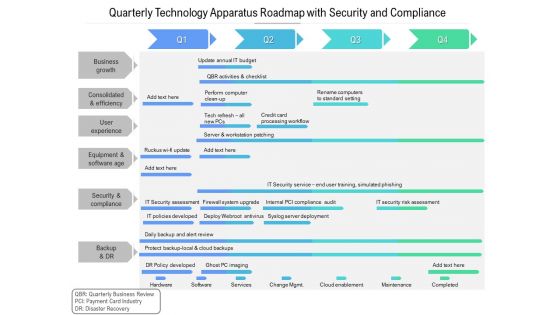
Quarterly Technology Apparatus Roadmap With Security And Compliance Rules
Presenting the quarterly technology apparatus roadmap with security and compliance rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
-
Person Opening Office Door With Security Access Control System Ppt PowerPoint Presentation Styles Rules PDF
Presenting person opening office door with security access control system ppt powerpoint presentation styles rules pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including person opening office door with security access control system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Security Capability Services Ppt PowerPoint Presentation Portfolio Rules Cpb Pdf
Presenting this set of slides with name security capability services ppt powerpoint presentation portfolio rules cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like security capability services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
Computer Security Incident Handling Cybersecurity Contingency Plan Business Impact Analysis Rules PDF
Presenting this set of slides with name computer security incident handling cybersecurity contingency plan business impact analysis rules pdf. The topics discussed in these slides are business processes, vital resources, impact, recovery priorities, max allowable outage time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Computer Security Incident Handling Business Impact Assessment Ppt Infographics Rules PDF
Presenting this set of slides with name computer security incident handling business impact assessment ppt infographics rules pdf. The topics discussed in these slides are strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Strategies To Mitigate Cyber Security Risks Financial Ppt Icon Rules PDF
Presenting this set of slides with name strategies to mitigate cyber security risks financial ppt icon rules pdf. This is a three stage process. The stages in this process are revenue, deposits, net income. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Security Rule Technical Regulations Ppt PowerPoint Presentation Pictures Inspiration Cpb
Presenting this set of slides with name security rule technical regulations ppt powerpoint presentation pictures inspiration cpb. This is an editable Powerpoint five stages graphic that deals with topics like security rule technical regulations to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
Security Assessment Checklist Ppt PowerPoint Presentation Model Rules Cpb Pdf
Presenting this set of slides with name security assessment checklist ppt powerpoint presentation model rules cpb pdf. This is an editable Powerpoint nine stages graphic that deals with topics like security assessment checklist to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
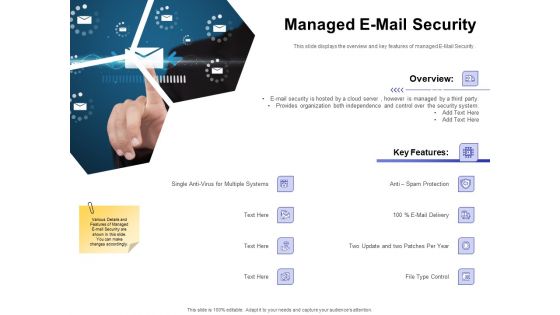
Global Cloud Based Email Security Market Managed E Mail Security Rules PDF
Presenting this set of slides with name global cloud based email security market managed e mail security rules pdf. This is a two stage process. The stages in this process are e mail security is hosted by a cloud server, however is managed by a third party, provides organization both independence and control over the security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
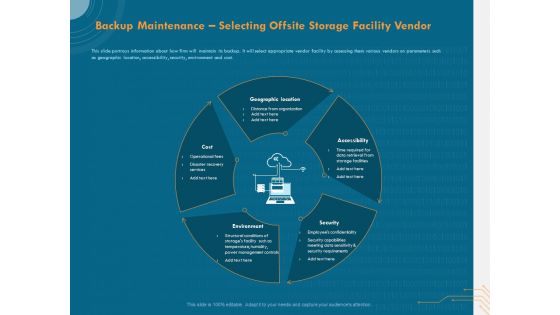
Cyber Security Implementation Framework Backup Maintenance Selecting Offsite Storage Facility Vendor Rules PDF
Presenting this set of slides with name cyber security implementation framework backup maintenance selecting offsite storage facility vendor rules pdf. This is a five stage process. The stages in this process are geographic location, accessibility, security, environment, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
-
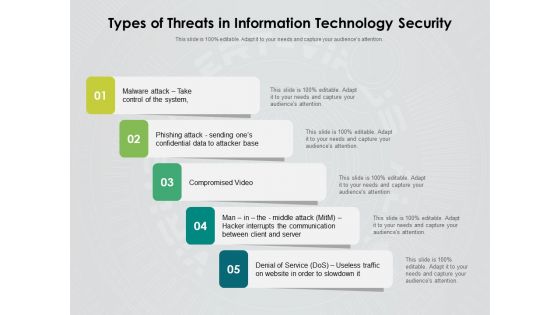
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Organization Three Months Automation Machinery Roadmapping With Security And Compliance Rules
Introducing our organization three months automation machinery roadmapping with security and compliance rules. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
-
Construction Management Services And Action Plan 4 Dimensions Of Infrastructure Security Rules PDF
Presenting construction management services and action plan 4 dimensions of infrastructure security rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Workforce Security Realization Coaching Plan Security Training Program Frameworks Contd Rules PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks contd rules pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
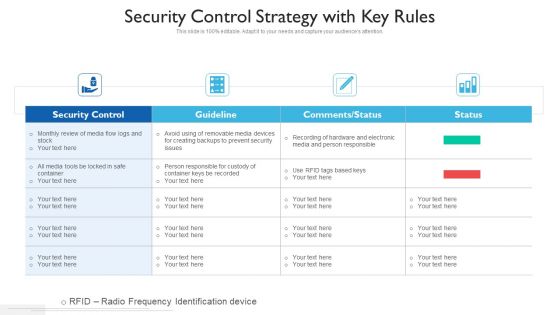
Security Control Strategy With Key Rules Ppt PowerPoint Presentation Gallery Clipart PDF
Showcasing this set of slides titled security control strategy with key rules ppt powerpoint presentation gallery clipart pdf. The topics addressed in these templates are security control, guideline, comments or status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
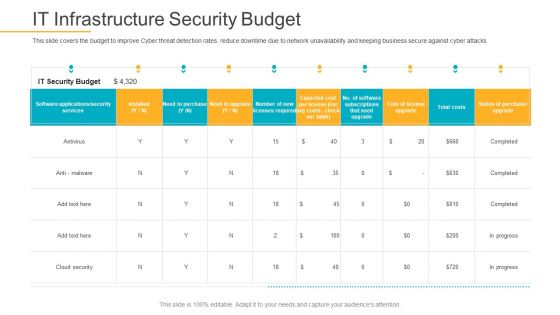
Data Breach Prevention Recognition IT Infrastructure Security Budget Rules PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition it infrastructure security budget rules pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
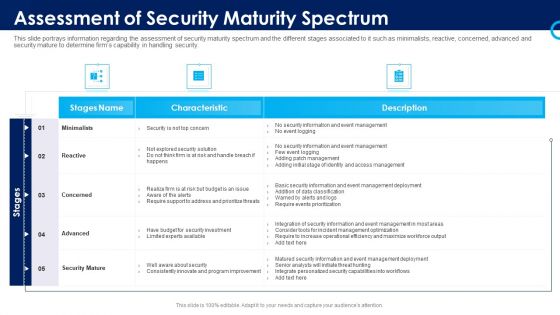
Organizational Security Solutions Assessment Of Security Maturity Spectrum Rules PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative organizational security solutions assessment of security maturity spectrum rules pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Organizational Security Solutions Budget For Effective Secops System Management Rules PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this organizational security solutions budget for effective secops system management rules pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Different Training Formats For Different Organizational Levels Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. This is a different training formats for different organizational levels hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interactive protection simulation, automated security awareness platform, cybersecurity for it online. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Problem Faced By The Organization Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a problem faced by the organization hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, cybersecurity, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
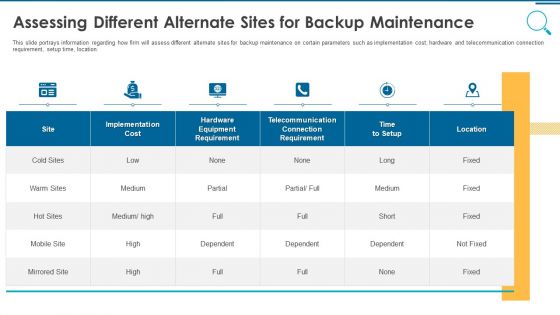
Information And Technology Security Operations Assessing Different Alternate Sites For Backup Maintenance Rules PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this information and technology security operations assessing different alternate sites for backup maintenance rules pdf. Use them to share invaluable insights on implementation, cost, location, telecommunication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Information And Technology Security Operations How Security Concerns Affect Firm In Present Times Rules PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative information and technology security operations how security concerns affect firm in present times rules pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
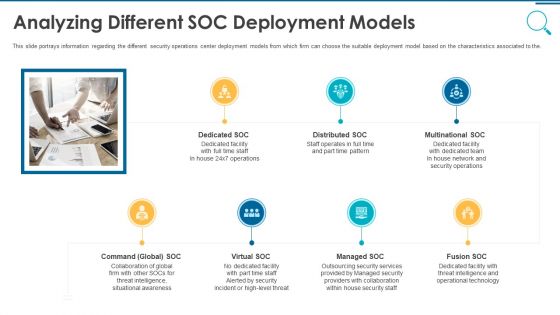
Information And Technology Security Operations Analyzing Different SOC Deployment Models Rules PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a information and technology security operations analyzing different soc deployment models rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
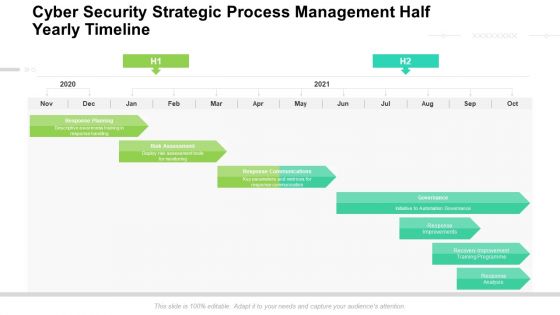
Cyber Security Strategic Process Management Half Yearly Timeline Rules
Presenting our innovatively structured cyber security strategic process management half yearly timeline rules Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
-
Organizational Network Staff Learning Security Awareness New Strategies For Learning Rules PDF
This slide cover effective way to build cybersafe across on organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness new strategies for learning rules pdf bundle. Topics like human centric training, manage and control, targeted training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Security And Process Integration Determine Security Risks Dashboard Rules PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this security and process integration determine security risks dashboard rules pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
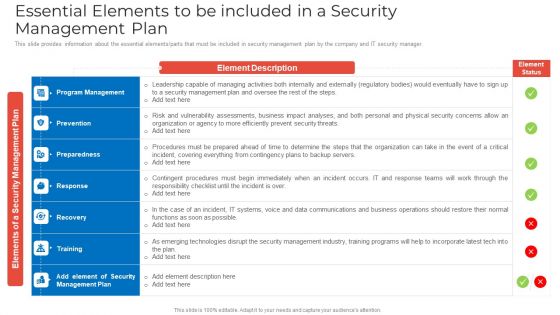
Essential Elements To Be Included In A Security Management Plan Rules PDF
This slide provides information about the essential elements parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan rules pdf bundle. Topics like program management, prevention, preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Implementing Security Management Strategy To Mitigate Risk Timeline Rules PDF
Presenting implementing security management strategy to mitigate risk timeline rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Phase 3 Respond To Cloud Protection Issues Cloud Computing Security IT Ppt Gallery Rules PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this phase 3 respond to cloud protection issues cloud computing security it ppt gallery rules pdf. Use them to share invaluable insights on authentication process, service, web policies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Cloud Security Checklist Backup And Data Recovery Cloud Computing Security IT Ppt Styles Rules PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting cloud security checklist backup and data recovery cloud computing security it ppt styles rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like effective, cloud service, natural disasters, data plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cloud Security Threats Revenue Losses Cloud Computing Security IT Ppt Ideas Rules PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. This is a cloud security threats revenue losses cloud computing security it ppt ideas rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, cyber threats, revenue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
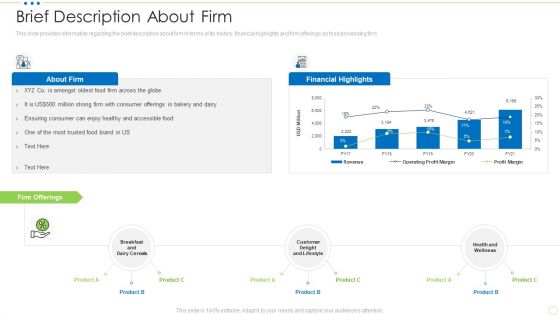
Brief Description About Firm Food Security Excellence Ppt Pictures Rules V
This slide provides information regarding the brief description about firm in terms of its history, financial highlights and firm offerings as food processing firm. Deliver and pitch your topic in the best possible manner with this brief description about firm food security excellence ppt pictures rules v. Use them to share invaluable insights on financial, lifestyle, health and wellness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Common Methods Used To Threaten IT Security IT Ppt Inspiration Rules PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten it security it ppt inspiration rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Guidelines To Create An Advanced Security Management Plan 30 60 90 Days Plan Rules PDF
Presenting guidelines to create an advanced security management plan 30 60 90 days plan rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Major Reasons For Poor Security Management In The Company Rules PDF
Deliver and pitch your topic in the best possible manner with this major reasons for poor security management in the company rules pdf. Use them to share invaluable insights on outdated software, lack of proper protection, lack of recovery and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
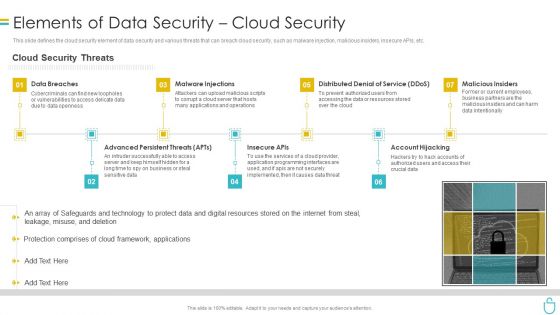
Information Security Elements Of Data Security Cloud Security Ppt Model Rules PDF
This slide defines the cloud security element of data security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting information security elements of data security cloud security ppt model rules pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data breaches, malware injections, distributed denial of service, malicious insiders, account hijacking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
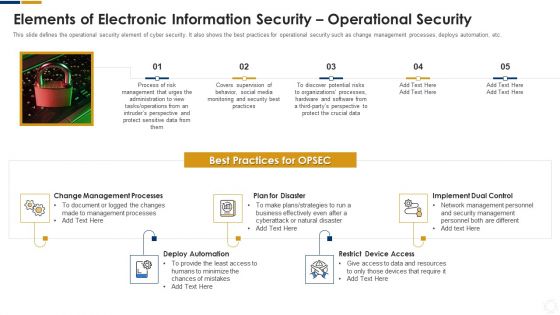
Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
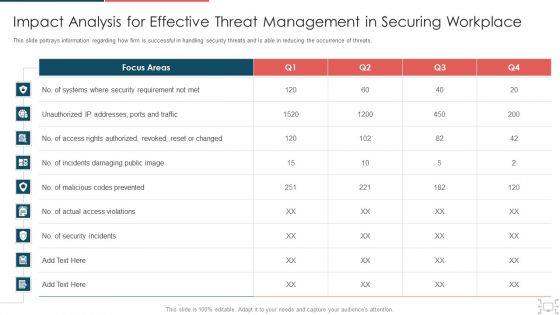
Cyber Security Administration In Organization Impact Analysis For Effective Threat Management Securing Rules PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative cyber security administration in organization impact analysis for effective threat management securing rules pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Face Recognition Security App On Computer Vector Icon Ppt PowerPoint Presentation Gallery Rules PDF
Presenting face recognition security app on computer vector icon ppt powerpoint presentation gallery rules pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including face recognition security app on computer vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
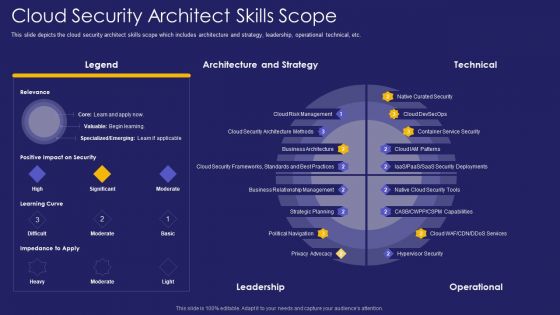
Role IT Team Digital Transformation Cloud Security Architect Skills Scope Rules PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative role it team digital transformation cloud security architect skills scope rules pdf bundle. Topics like architecture, strategy, leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Query Slide Diagram For Secure Cash Endowment Rules PDF
Persuade your audience using this query slide diagram for secure cash endowment rules pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including query slide diagram for secure cash endowment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
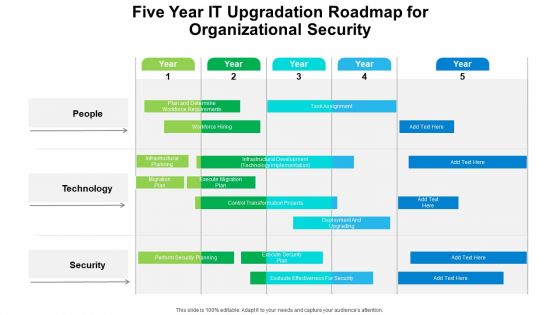
Five Year IT Upgradation Roadmap For Organizational Security Rules
Presenting the five year it upgradation roadmap for organizational security rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
-
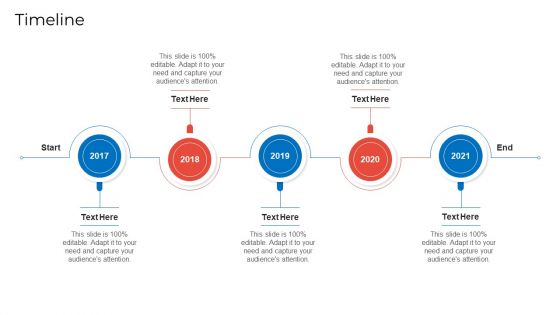
Developing Firm Security Strategy Plan Timeline Rules PDF
This is a developing firm security strategy plan timeline rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Rules PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan rules pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.