Security key PowerPoint Presentation Templates and Google Slides
-
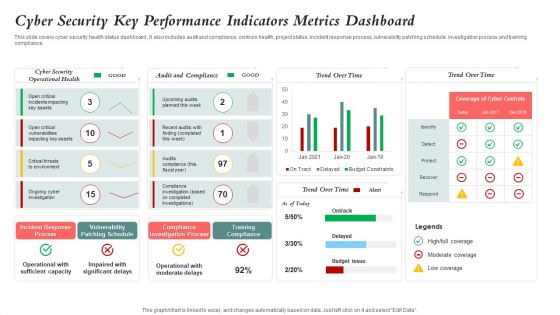
Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF
This slide covers cyber security health status dashboard . It also includes audit and compliance, controls health, project status, incident response process, vulnerability patching schedule, investigation process and training compliance. Pitch your topic with ease and precision using this Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF. This layout presents information on Cyber Security, Vulnerability Patching Schedule, Compliance Investigation Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF
This slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, mobile device management support. This is a Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Device Enrolment, Profile Management, Management Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
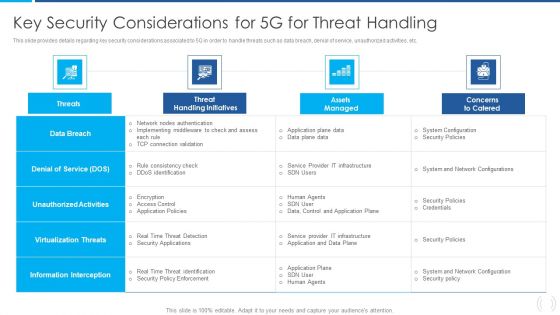
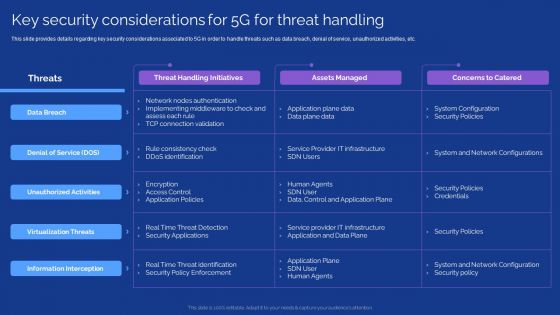
5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
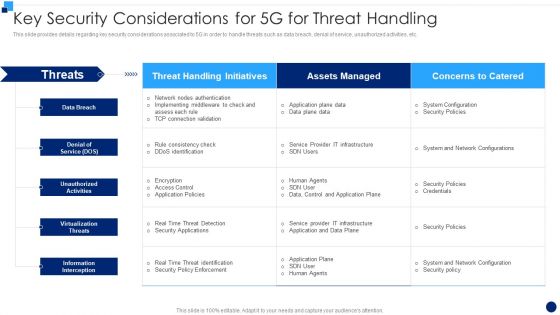
Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Key Challenges In Cloud Security Portrait PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting Key Challenges In Cloud Security Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Daniel Of Service, Compliance Violations, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
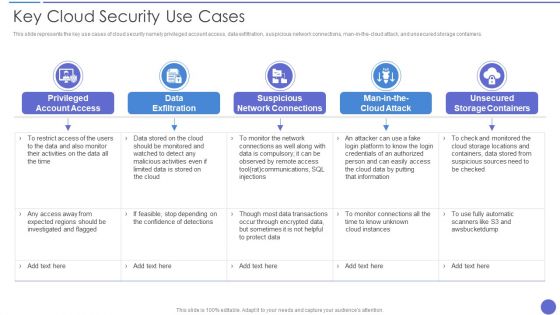
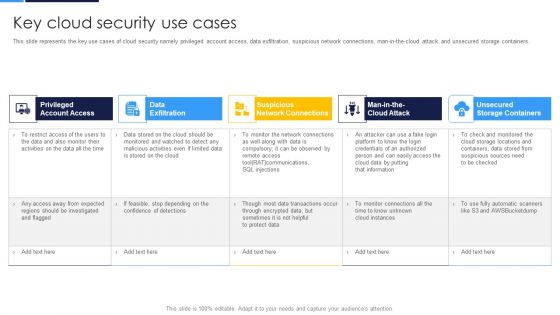
Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
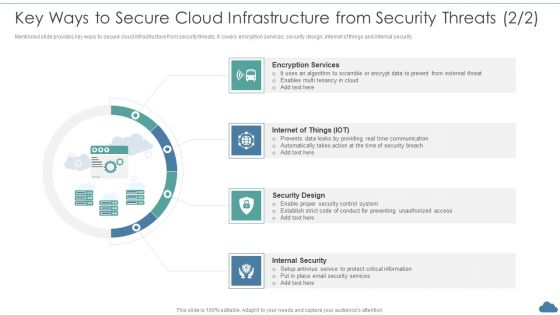
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Investment Banking Security Underwriting Pitchbook Competitor Comparison On The Basis Of Key Financials Pictures PDF
The slide provides the companys comparisons with its competitors on the basis of key financials total revenue, net income, assets under management, employee count, number of IPO deals etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Competitor Comparison On The Basis Of Key Financials Pictures PDF bundle. Topics like Total Revenue, Net Income, Investment Bank can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Investment Banking Security Underwriting Pitchbook IPO Deal Overview Key Points Brochure PDF
The slide provides the overview of IPO deals. It cover the points such as application date, issue price, of shares, amount to be raised, key reasons behind the IPO issue etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Deal Overview Key Points Brochure PDF bundle. Topics like Industry Overview, Reason Behind, Providing Liquidity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
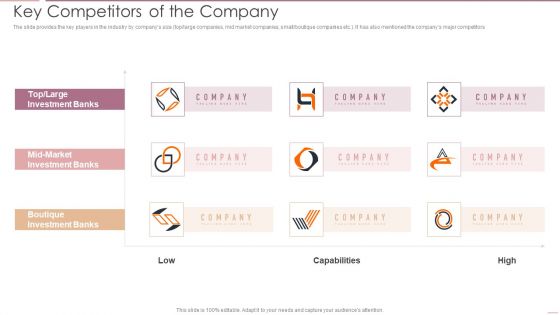
Investment Banking Security Underwriting Pitchbook Key Competitors Of The Company Graphics PDF
The slide provides the key players in the industry by companys size top large companies, mid market companies, small or boutique companies etc.. It has also mentioned the companys major competitors.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Competitors Of The Company Graphics PDF Use them to share invaluable insights on Investment Banks, Boutique Investment, Large Investment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
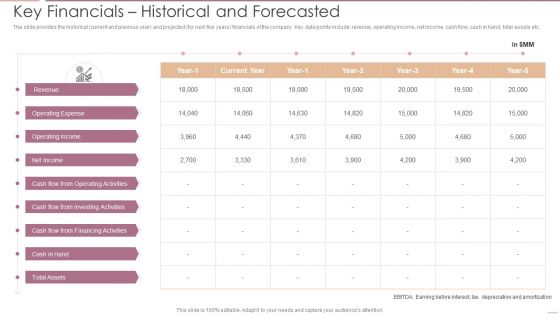
Investment Banking Security Underwriting Pitchbook Key Financials Historical And Forecasted Professional PDF
The slide provides the historical current and previous year and projected for next five year financials of the company. Key data points include revenue, operating income, net income, cash flow, cash in hand, total assets etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Key Financials Historical And Forecasted Professional PDF bundle. Topics like Operating Expense, Operating Income, Operating Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Investment Banking Security Underwriting Pitchbook Key Objectives Of The IPO Issue Slides PDF
The slide provides the companys objectives behind issuing IPO. Key objectives include future expansion, option of alternative currency, cash out option, paying off debts etc. Presenting Investment Banking Security Underwriting Pitchbook Key Objectives Of The IPO Issue Slides PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Expansion, Alternative Currency, Paying Debts In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
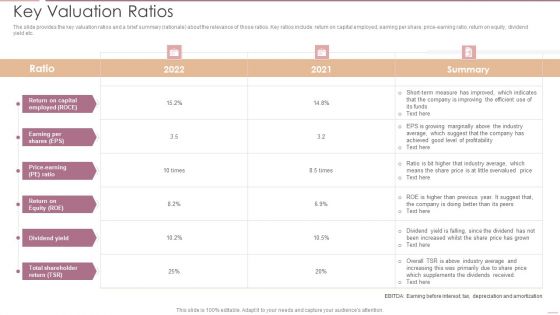
Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF
The slide provides the key valuation ratios and a brief summary rationale about the relevance of those ratios. Key ratios include return on capital employed, earning per share, price-earning ratio, return on equity, dividend yield etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF Use them to share invaluable insights on Measure Improved, Dividends Received, Total Shareholder and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF bundle. Topics like Virtualization Threats, Information Interception, Unauthorized Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
Prevention Of Information Key Statistics Showing The Impact Of Security Awareness Infographics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. This modern and well-arranged Prevention Of Information Key Statistics Showing The Impact Of Security Awareness Infographics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
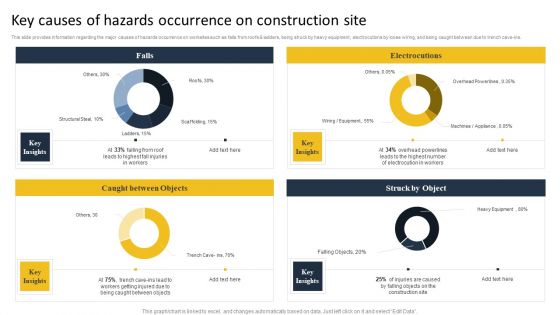
Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF
This slide provides information regarding the major causes of hazards occurrence on worksites such as falls from roofs AND ladders, being struck by heavy equipment, electrocutions by loose wiring, and being caught between due to trench cave-ins. Find a pre designed and impeccable Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for. Download the template from Slidegeeks today and give a unique touch to your presentation.
-
KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF
This slide showcases assessing impact on major operations and workflows. It provides information about customer understanding, knowledge, data management, financial risk management, customer relationship management, client onboarding, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF.
-
KYC Transaction Monitoring System Business Security Key Trends Of Transaction Monitoring Across Us Diagrams PDF
This slide showcases transaction monitoring landscape of united states US. It provides information about transaction volume, suspicious activity report SAR, transaction patterns, structuring, funds circulation, scenarios, cash usage, etc. There are so many reasons you need a KYC Transaction Monitoring System Business Security Key Trends Of Transaction Monitoring Across Us Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
-
Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF
This modern and well arranged Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
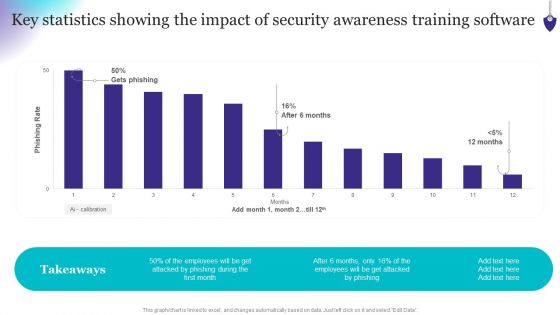
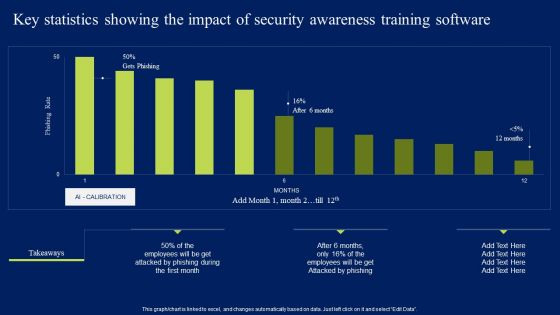
Key Statistics Showing The Impact Of Security Awareness Training Software Elements PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Statistics Showing The Impact Of Security Awareness Training Software Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
-
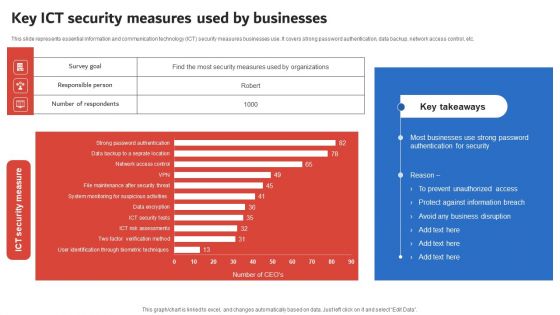
Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
-
Golden Key With Men Security PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with a man standing in a circle around a golden key
-
Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF
The following slide exhibits four practices for selecting managed security service provider. Expertise, cost, business requirements and testimonials are some of the practices which will help the organization in selecting trusted security providers. Persuade your audience using this Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Expertise, Cost, Business Requirements, Testimonials. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
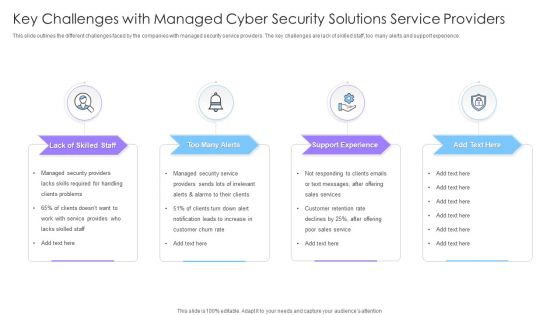
Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF
This slide outlines the different challenges faced by the companies with managed security service providers. The key challenges are lack of skilled staff, too many alerts and support experience. Presenting Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Too Many Alerts, Support Experience, Lack Skilled Staff. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
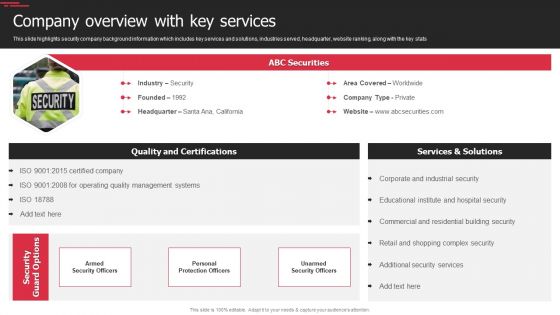
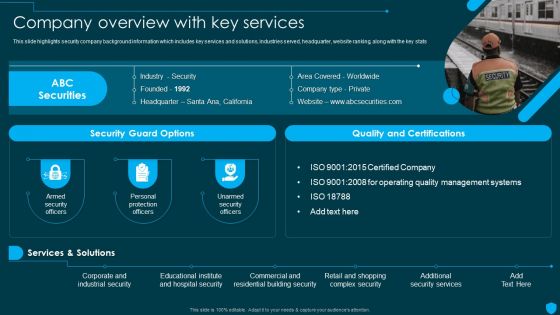
Security Officer Service Company Profile Company Overview With Key Services Background PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. This is a Security Officer Service Company Profile Company Overview With Key Services Background PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ABC Securities, Services And Solutions, Quality And Certifications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Key Benefits Of Cyber Security Awareness Training Background PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide.This is a Key Benefits Of Cyber Security Awareness Training Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drive Awareness, Reduce Threat, Amongst Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Key Stakeholders Of Cyber Security Awareness Training Mockup PDF
Presenting Key Stakeholders Of Cyber Security Awareness Training Mockup PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Senior Mangers, Line Managers, Employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
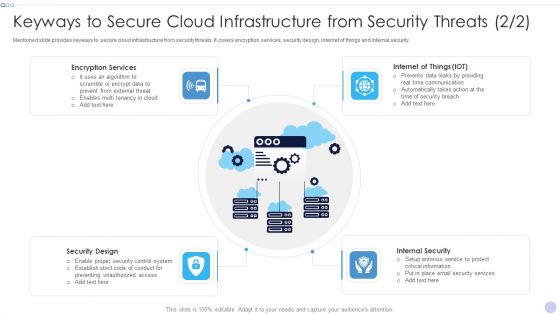
Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF
The following slide highlights multiple solutions to prevent security risks and issues. It also includes elements such as risk evaluation, security awareness, checklist, policies and regulation, recovery plan etc. Presenting Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Risk Evaluation, Security Awareness, Security Checklist, Policies And Regulation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide depicts the SaaS security process to acknowledge the gap and have proactive approach. It mainly constitutes of three phases discover, monitor and protect. Persuade your audience using this Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Discover, Monitor, Protect, Identify Utility, Assess Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Security And Surveillance Company Profile Company Overview With Key Services Professional PDF
This slide highlights security company background information which includes the company services offered, area served, total employees, headquarter, website and company value added services.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Company Overview With Key Services Professional PDF bundle. Topics like Manage Devices, Monitory Services, Services And Solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Security And Surveillance Company Profile Key CSR Initiatives Formats PDF
This slide highlights the corporate social responsibilities activities of security company which includes electric vehicle, blood donation camps, engage empower and educate , free surgeries.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Key CSR Initiatives Formats PDF. Use them to share invaluable insights on Transformative, Security Experience, Digital Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
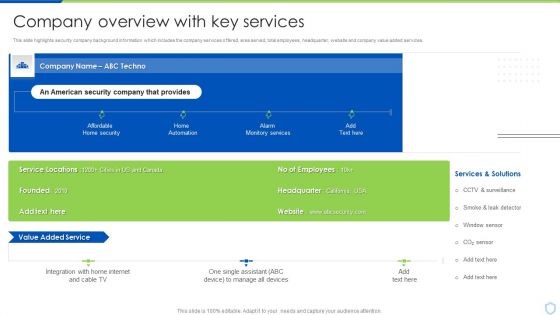
Security Camera System Company Profile Company Overview With Key Services Icons PDF
This slide highlights security company background information which includes the company services offered, area served, total employees, headquarter, website and company value added services.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Company Overview With Key Services Icons PDF bundle. Topics like Monitory Services, Home Automation, Manage All Devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Security Camera System Company Profile Key CSR Initiatives Slides PDF
This slide highlights the corporate social responsibilities activities of security company which includes electric vehicle, blood donation camps, engage empower and educate , free surgeries.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Key CSR Initiatives Slides PDF. Use them to share invaluable insights on Engage Empower, Empowering Lives, Cataract Surgeries and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
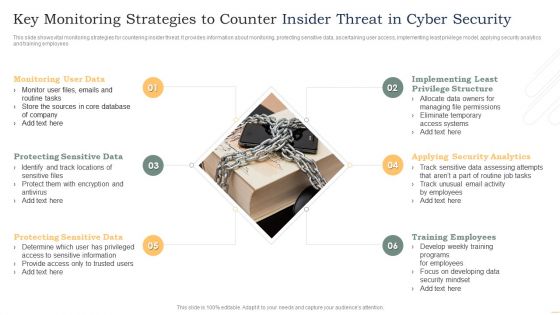
Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Key Components Of People Centric Work Culture Security Ideas PDF
The following slide highlights the key elements of people centric security to prevent data breaches and IT damages. It includes activities such as personalized training, artificial intelligence AI and machine learning ML tools and prompt social engineering attacks etc. Persuade your audience using this Key Components Of People Centric Work Culture Security Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Personalized Training, Artificial Intelligence, Engineering Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Key Objectives Of People Centric Work Culture Security System Infographics PDF
The following slide highlights the main reasons to develop human centric security system for better security features. It mainly includes activities such as establishing secure perimeter, comprehending cause behind user actions, optimizing remote security operations etc. Presenting Key Objectives Of People Centric Work Culture Security System Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Establish Secure Perimeter, Acknowledges Potential Threats, Employee Roles. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF bundle. Topics like Armed Security Officer, Personal Protection Officers, Unarmed Security Officers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs.Presenting Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Compliance Violations, Access Control, Daniel Of Service In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF Use them to share invaluable insights on Account Access, Data Exfiltration, Network Connections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF bundle. Topics like Information Interception, Virtualization Threats, Denial Of Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Key Practices To Implement Digitization Of Security Systems Icons PDF
The following slide highlights best practices which can be implemented by firm for digitization of security systems. The major practices are prioritize automation, start with manual playbooks, adopt automation gradually and invest in the training of IT team. Presenting Key Practices To Implement Digitization Of Security Systems Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Prioritize Automation, Start Manual Playbooks, Adopt Automation Gradually. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
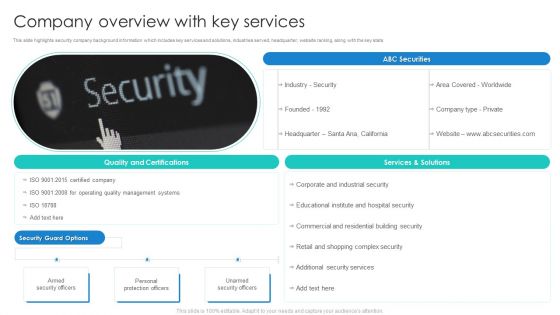
Security Agency Business Profile Company Overview With Key Services Inspiration PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Company Overview With Key Services Inspiration PDF bundle. Topics like Quality Management Systems, Industrial Security, Security Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
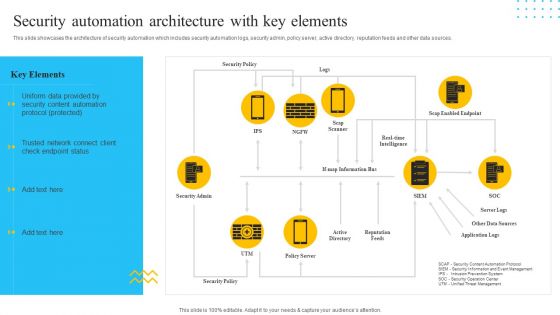
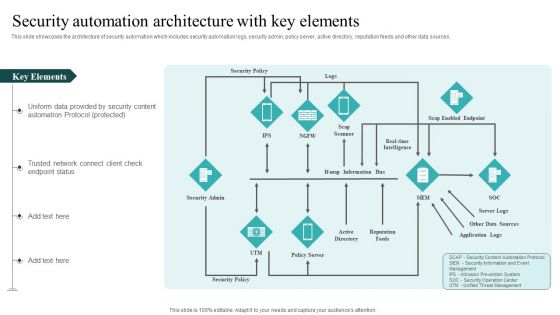
IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Presenting IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Policy, Security Admin, Reputation Feeds. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
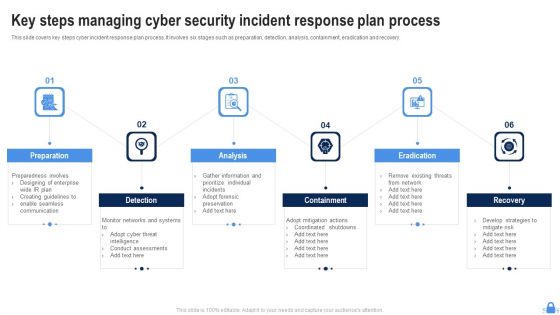
Key Steps Managing Cyber Security Incident Response Plan Process Portrait PDF
This slide covers key steps cyber incident response plan process. It involves six stages such as preparation, detection, analysis, containment, eradication and recovery. Persuade your audience using this Key Steps Managing Cyber Security Incident Response Plan Process Portrait PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Preparation, Detection, Analysis, Eradication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
-
Security And Human Resource Services Business Profile Company Overview With Key Template PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Security And Human Resource Services Business Profile Company Overview With Key Template PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security And Human Resource Services Business Profile Company Overview With Key Template PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. This modern and well arranged Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
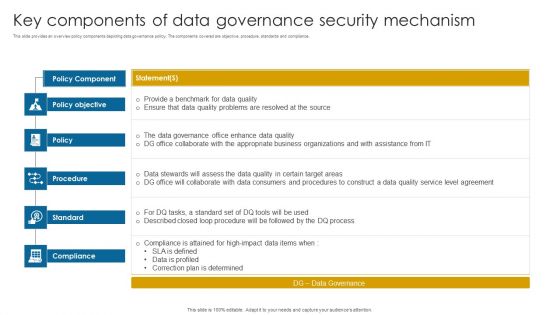
Key Components Of Data Governance Security Mechanism Information PDF
This slide provides an overview policy components depicting data governance policy. The components covered are objective, procedure, standards and compliance.Pitch your topic with ease and precision using this Key Components Of Data Governance Security Mechanism Information PDF. This layout presents information on Data Governance, Compliance Attained, Correction Determined. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
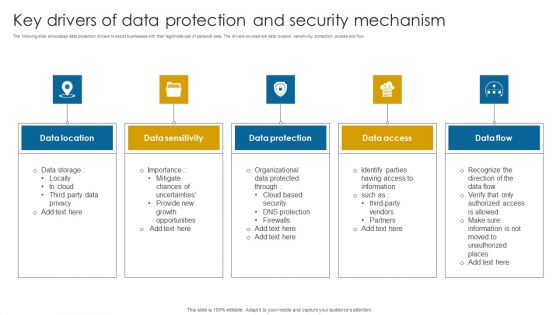
Key Drivers Of Data Protection And Security Mechanism Infographics PDF
The following slide showcases data protection drivers to assist businesses with their legitimate use of personal data. The drivers covered are data location, sensitivity, protection, access and flow.Presenting Key Drivers Of Data Protection And Security Mechanism Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Location, Data Sensitivity, Data Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
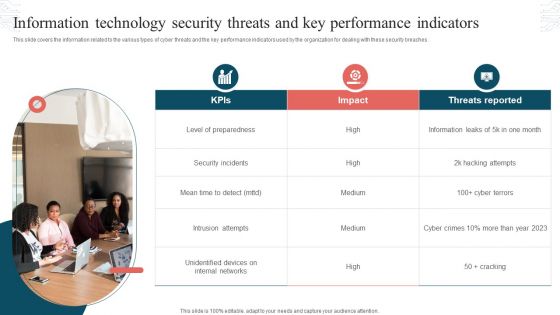
Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.