Secure method PowerPoint Presentation Templates and Google Slides
-
Methods To Develop Advanced IT Security Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This methods to develop advanced it security monitoring plan ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
-
Security Methodology Diagram Powerpoint Topics
This is a security methodology diagram powerpoint topics. This is a six stage process. The stages in this process are device protection, data separation, security operation, security organization, leak protection, sharing protection.
-
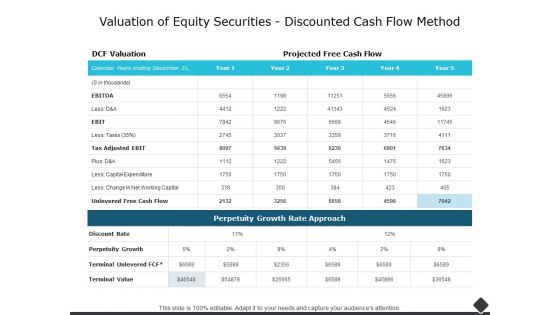
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Styles Example
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation styles example. This is a two stage process. The stages in this process are business, management, marketing, compare.
-
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Model Icon
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation model icon. This is a three stage process. The stages in this process are business, management, marketing, compare.
-
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Outline Designs
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation outline designs. The topics discussed in this diagram are business, management, marketing, compare. This is a completely editable PowerPoint presentation, and is available for immediate download.
-
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Infographic Template Introduction
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation infographic template introduction. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.
-
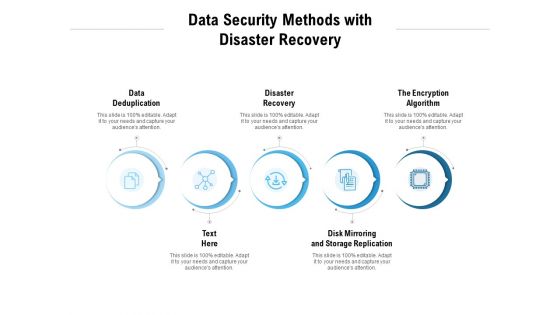
Data Security Methods With Disaster Recovery Ppt PowerPoint Presentation Pictures Vector
Presenting this set of slides with name data security methods with disaster recovery ppt powerpoint presentation pictures vector. This is a five stage process. The stages in this process are data deduplication, disaster recovery, the encryption algorithm, disk mirroring and storage replication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
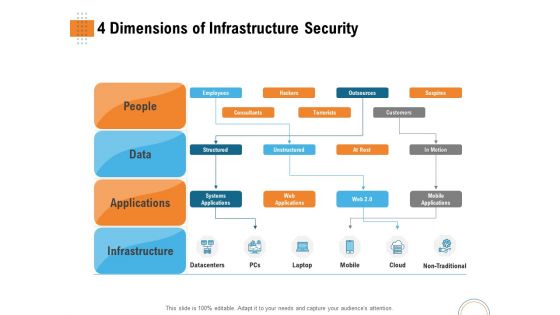
Utilizing Infrastructure Management Using Latest Methods 4 Dimensions Of Infrastructure Security Introduction PDF
Presenting utilizing infrastructure management using latest methods 4 dimensions of infrastructure security introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like people, data, applications, infrastructure, datacentres, mobile, cloud, non traditional. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Utilizing Infrastructure Management Using Latest Methods Interdependence Resiliency And Security Themes PDF
This is a utilizing infrastructure management using latest methods interdependence resiliency and security themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical infrastructure dependencies and interdependencies assessment framework, infrastructure resilience wheel, lifecycle adaptive components resilience framework, dimensions infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Chart Showing Technology Threats Methods And Technology For Cyber Security Ppt PowerPoint Presentation Ideas Slideshow PDF
Presenting chart showing technology threats methods and technology for cyber security ppt powerpoint presentation ideas slideshow pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer security attributes, attack methods, technology for internet security, confidentiality, integrity, privacy, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
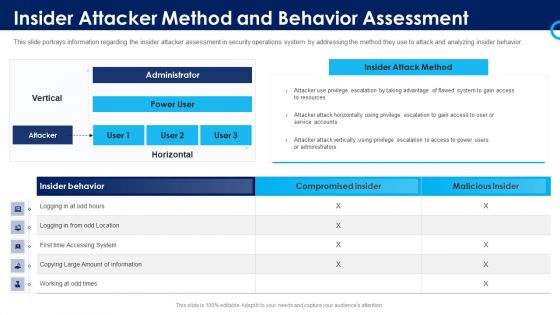
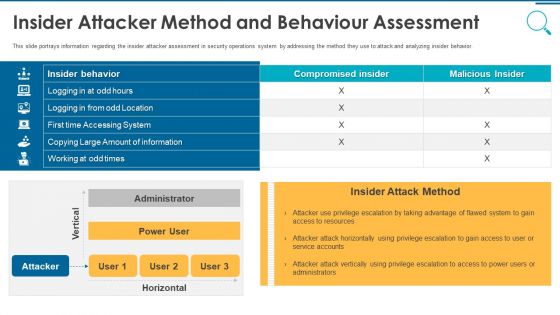
Organizational Security Solutions Insider Attacker Method And Behavior Assessment Introduction PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this organizational security solutions insider attacker method and behavior assessment introduction pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Security Functioning Centre Insider Attacker Method And Behaviour Assessment Ideas PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security functioning centre insider attacker method and behaviour assessment ideas pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Information And Technology Security Operations Insider Attacker Method And Behaviour Assessment Inspiration PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this information and technology security operations insider attacker method and behaviour assessment inspiration pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Security And Process Integration Insider Attacker Method And Behaviour Assessment Microsoft PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security and process integration insider attacker method and behaviour assessment microsoft pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
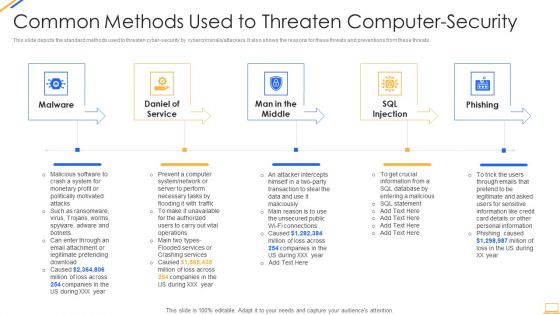
Common Methods Used To Threaten IT Security IT Ppt Inspiration Rules PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten it security it ppt inspiration rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
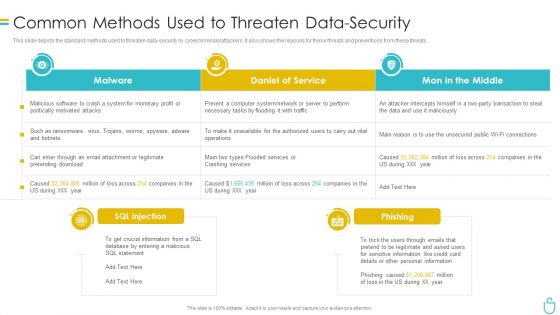
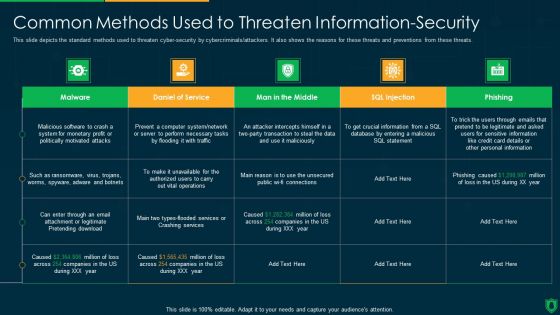
Information Security Common Methods Used To Threaten Data Security Ppt Show Model PDF
This slide depicts the standard methods used to threaten data security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver and pitch your topic in the best possible manner with this information security common methods used to threaten data security ppt show model pdf. Use them to share invaluable insights on system, daniel of service, man in the middle and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Cybersecurity Common Methods Used To Threaten Electronic Information Security Ppt Infographics Inspiration PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a cybersecurity common methods used to threaten electronic information security ppt infographics inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
IT Security Common Methods Used To Threaten Information Technology Security Ppt Layouts Graphics PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a it security common methods used to threaten information technology security ppt layouts graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Agenda For Methods To Develop Advanced IT Security Monitoring Plan Graphics PDF
This is a agenda for methods to develop advanced it security monitoring plan graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collecting and analyzing, key performance indicators, potential security monitoring threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Icons Slide For Methods To Develop Advanced IT Security Monitoring Plan Slides PDF
Presenting our innovatively structured icons slide for methods to develop advanced it security monitoring plan slides pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
-
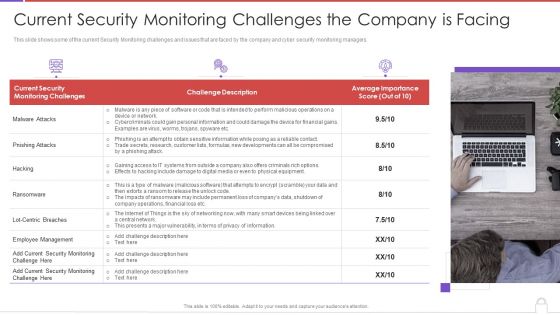
Methods To Develop Advanced Current Security Monitoring Challenges The Company Is Facing Professional PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a methods to develop advanced current security monitoring challenges the company is facing professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current security, monitoring challenges, challenge description, average importance score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
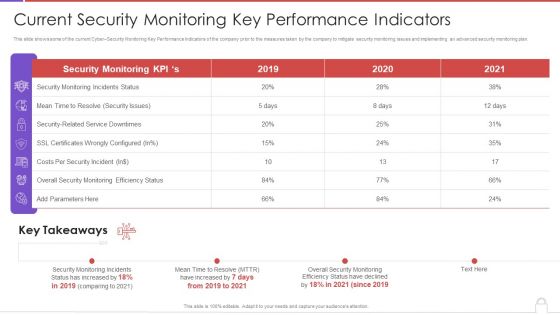
Methods To Develop Advanced Current Security Monitoring Key Performance Indicators Formats PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative methods to develop advanced current security monitoring key performance indicators formats pdf bundle. Topics like monitoring incidents status, security issues, costs per security incident, 2019 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Methods To Develop Advanced Essential Elements Of Security Monitoring Plan Formats PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver and pitch your topic in the best possible manner with this methods to develop advanced essential elements of security monitoring plan formats pdf. Use them to share invaluable insights on network security, critical infrastructure, cloud security, application security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Methods To Develop Advanced Estimated Security Monitoring Key Performance Indicators Structure PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an awe inspiring pitch with this creative methods to develop advanced estimated security monitoring key performance indicators structure pdf bundle. Topics like security monitoring kpis, costs per security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Methods To Develop Major Reasons For Poor Security Monitoring In The Company Information PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver and pitch your topic in the best possible manner with this methods to develop major reasons for poor security monitoring in the company information pdf. Use them to share invaluable insights on improper security maintenance, evolving software, high end software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
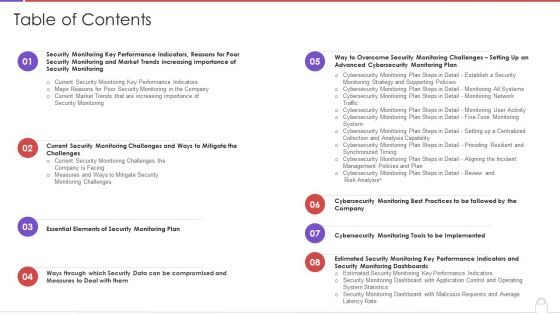
Table Of Contents Methods To Develop Advanced It Security Monitoring Plan Structure PDF
Deliver and pitch your topic in the best possible manner with this table of contents methods to develop advanced it security monitoring plan structure pdf. Use them to share invaluable insights on security monitoring, key performance indicators, security monitoring plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Desktop Security Management Common Methods Used To Threaten Computer Security Template PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a desktop security management common methods used to threaten computer security template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, services, network, database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
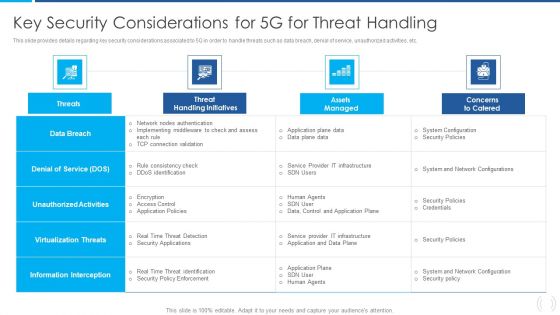
Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF bundle. Topics like Virtualization Threats, Information Interception, Unauthorized Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
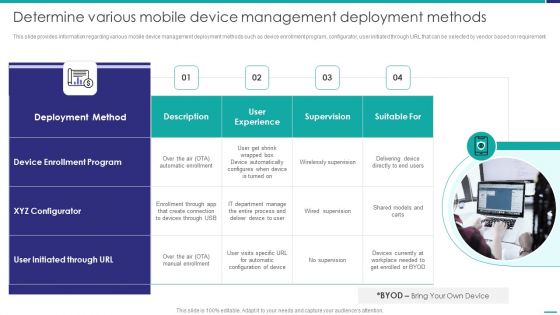
Determine Various Mobile Device Management Deployment Methods Mobile Device Security Management Summary PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. This is a Determine Various Mobile Device Management Deployment Methods Mobile Device Security Management Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enrollment Program, Configurator, Automatic Enrollment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
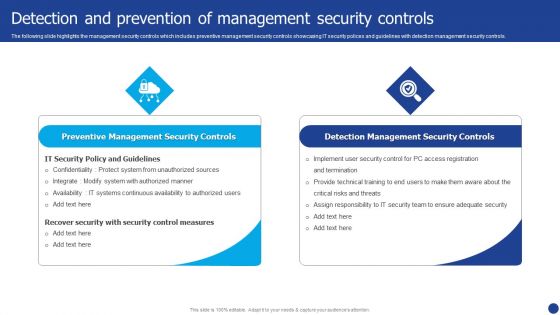
Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Presenting Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Preventive Management Security Controls, Detection Management Security Controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
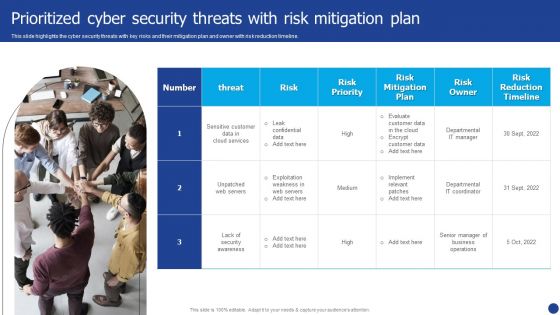
Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. This is a Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Owner, Risk Priority, Risk Mitigation Plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
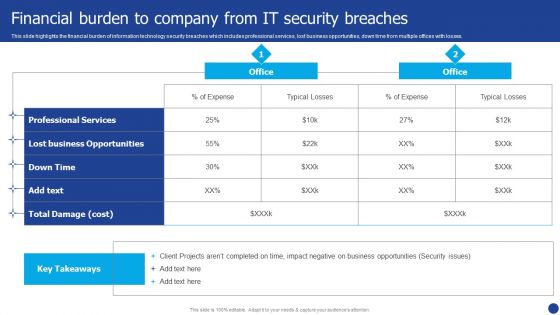
Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF. Use them to share invaluable insights on Professional Services, Lost Business Opportunities, Expense and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
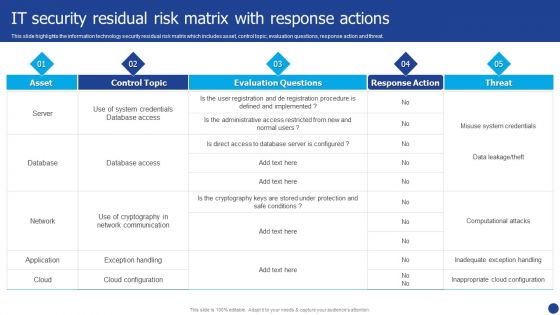
Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
IT Security Awareness Training Program Methods For Effective Results Summary PDF
This slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Presenting IT Security Awareness Training Program Methods For Effective Results Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Involve Games, Engage Friendly Competition, Include Rewards. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
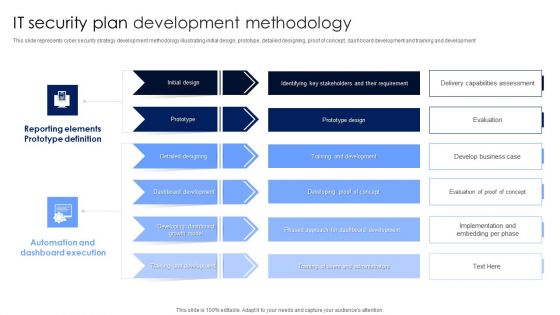
IT Security Plan Development Methodology Microsoft PDF
This slide represents cyber security strategy development methodology illustrating initial design, prototype, detailed designing, proof of concept, dashboard development and training and development. Pitch your topic with ease and precision using this IT Security Plan Development Methodology Microsoft PDF. This layout presents information on Automation And Dashboard Execution, Reporting Elements Prototype Definition, Dashboard Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Blockchain Business Methodology For Business Security Icon Clipart PDF
Persuade your audience using this Blockchain Business Methodology For Business Security Icon Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Business Methodology, Business Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
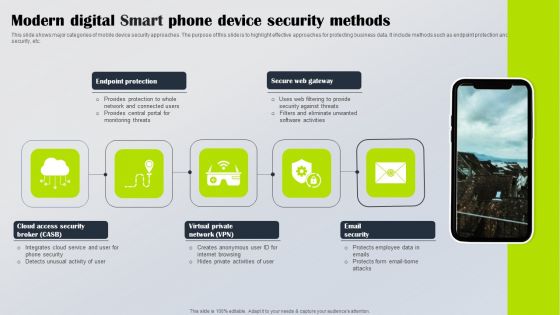
Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
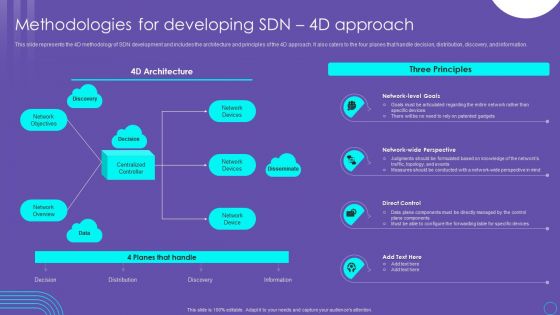
SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF
This slide represents the 4D methodology of SDN development and includes the architecture and principles of the 4D approach. It also caters to the four planes that handle decision, distribution, discovery, and information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF.
-
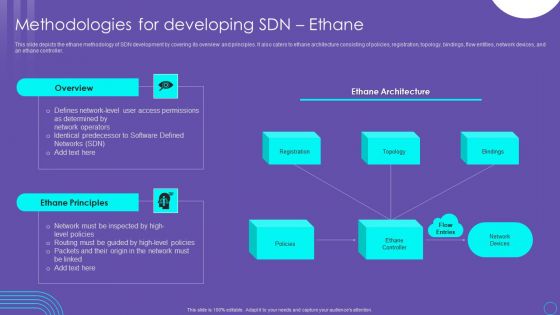
SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. This SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
-
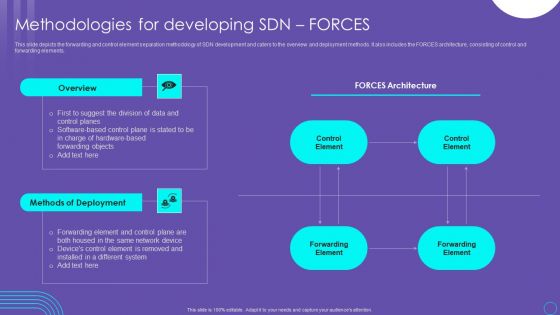
SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF
This slide depicts the forwarding and control element separation methodology of SDN development and caters to the overview and deployment methods. It also includes the FORCES architecture, consisting of control and forwarding elements. Take your projects to the next level with our ultimate collection of SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
-
Software Testing Methodologies To Improve Data Security Graphics PDF
This slides signifies the application testing practises to increase data security. It covers information about steps like build secure environment, create team, simulate end user, adopt shifting left testing methodology and focus on regression testing. Presenting Software Testing Methodologies To Improve Data Security Graphics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Build Secure Testing Environment, Simulate End User Environment, Focus Regression Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Secure Database Access Methods For Cloud Computing Formats PDF
This slide describes the various methods to access the data stored in a cloud environment securely. The purpose of this slide is to represent secure data access for cloud computing users. The methods include cloud-based access through a relational database management system, cloud-based data warehousing and a cloud data lake. Persuade your audience using this Secure Database Access Methods For Cloud Computing Formats PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Data Lake, Data Warehousing, Cloud Service Provider. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
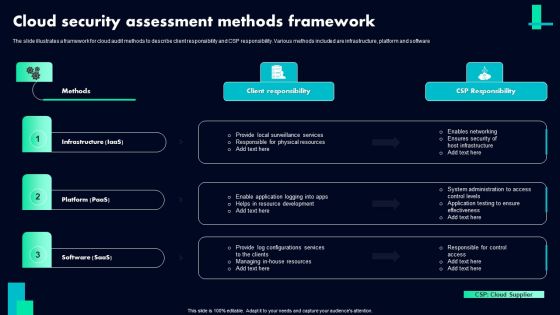
Cloud Security Assessment Methods Framework Ppt PowerPoint Presentation File Clipart PDF
The slide illustrates a framework for cloud audit methods to describe client responsibility and CSP responsibility. Various methods included are infrastructure, platform and software. Pitch your topic with ease and precision using this Cloud Security Assessment Methods Framework Ppt PowerPoint Presentation File Clipart PDF. This layout presents information on Methods, Infrastructure Iaas, Platform Paas, Client Responsibility. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
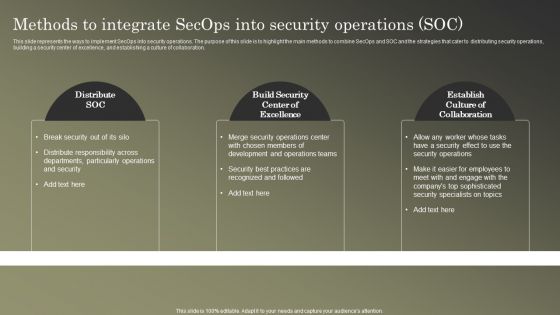
Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF
This slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
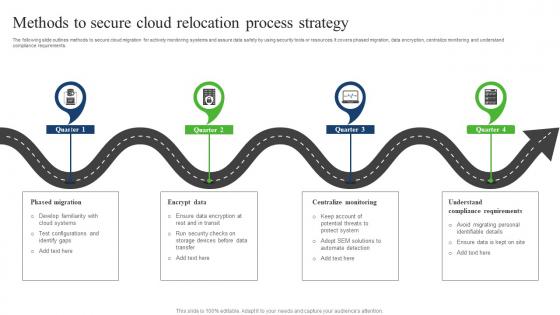
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Major Types Of Distributed Ledger Security Methods Portrait Pdf
This slide highlights types of blockchain security methods aimed at efficiently storing data to execute transaction and perform functions in an open environment. It covers three types public blockchain, private blockchain and consortium blockchain Showcasing this set of slides titled Major Types Of Distributed Ledger Security Methods Portrait Pdf The topics addressed in these templates are Public Blockchain, Private Blockchain, Consortium Blockchain All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Network Security Methods Using Distributed Ledger Technology Introduction Pdf
This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication Pitch your topic with ease and precision using this Network Security Methods Using Distributed Ledger Technology Introduction Pdf This layout presents information on Strong Identities And Authentication, Securing Core Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Secure Web Gateway Implementation Methodology Inline Web Access Control Solution
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Create an editable Secure Web Gateway Implementation Methodology Inline Web Access Control Solution that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Secure Web Gateway Implementation Methodology Inline Web Access Control Solution is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
-
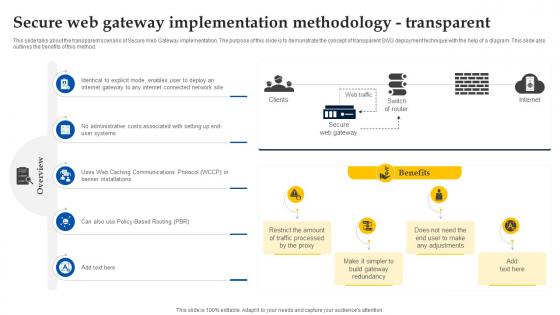
Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
-
Web Access Control Solution Methods To Implement Security Policies On Organizational Networks
This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Take your projects to the next level with our ultimate collection of Web Access Control Solution Methods To Implement Security Policies On Organizational Networks. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
-
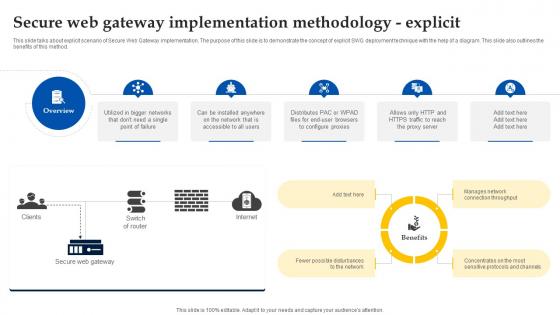
Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit
This slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit a try. Our experts have put a lot of knowledge and effort into creating this impeccable Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
-
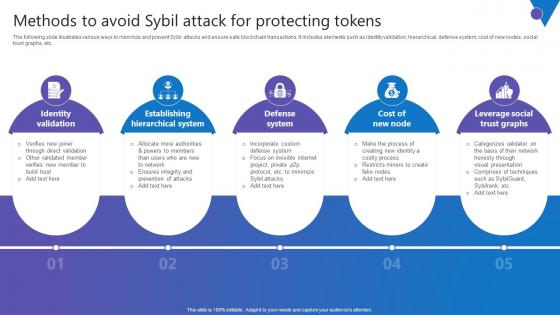
Methods To Avoid Sybil Comprehensive Guide To Blockchain Digital Security Brochure Pdf
The following slide illustrates various ways to minimize and prevent Sybil attacks and ensure safe blockchain transactions. It includes elements such as identity validation, hierarchical, defense system, cost of new nodes, social trust graphs, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Methods To Avoid Sybil Comprehensive Guide To Blockchain Digital Security Brochure Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
Methods To Ensure Smart Comprehensive Guide To Blockchain Digital Security Mockup Pdf
The following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. This modern and well arranged Methods To Ensure Smart Comprehensive Guide To Blockchain Digital Security Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. This Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today