Secure keys PowerPoint Presentation Templates and Google Slides
-
Key Aspects Of 5G Network Security Topics Pdf
This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications. Pitch your topic with ease and precision using this Key Aspects Of 5G Network Security Topics Pdf. This layout presents information on Security Domains, Description, Importance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Internet Security Key Performance Indicators To Track Microsoft Pdf
This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.Showcasing this set of slides titled Internet Security Key Performance Indicators To Track Microsoft Pdf The topics addressed in these templates are Firewall System, Security Standards, Identify Attack All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
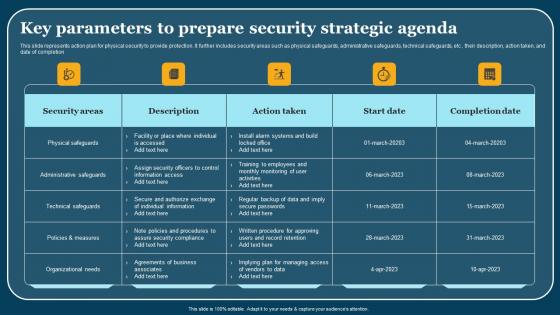
Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
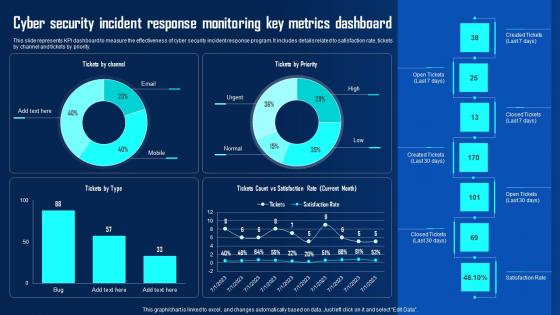
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
-
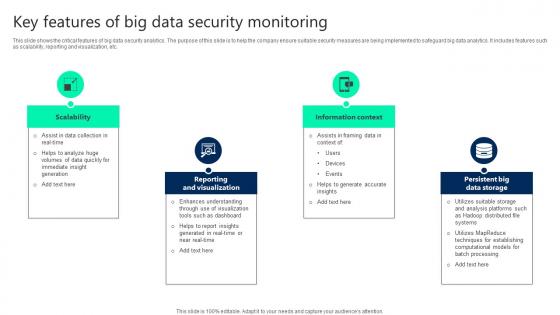
Key Features Of Big Data Security Monitoring Ideas pdf
This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc. Pitch your topic with ease and precision using this Key Features Of Big Data Security Monitoring Ideas pdf. This layout presents information on Scalability, Reporting And Visualization, Information Context. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
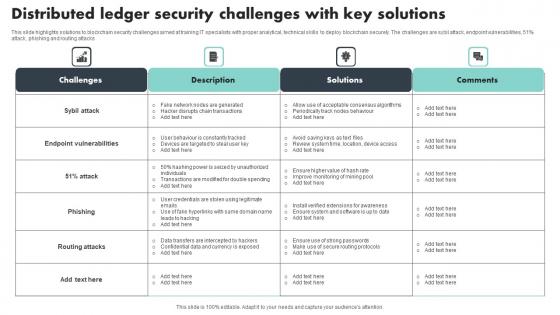
Distributed Ledger Security Challenges With Key Solutions Introduction Pdf
This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51percent attack, phishing and routing attacks Showcasing this set of slides titled Distributed Ledger Security Challenges With Key Solutions Introduction Pdf The topics addressed in these templates are Endpoint Vulnerabilities, Routing Attacks, Phishing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Key Categories Of Distributed Ledger Security Levels Portrait Pdf
This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network Pitch your topic with ease and precision using this Key Categories Of Distributed Ledger Security Levels Portrait Pdf This layout presents information on Transaction Level, Account Level, Programming Level It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
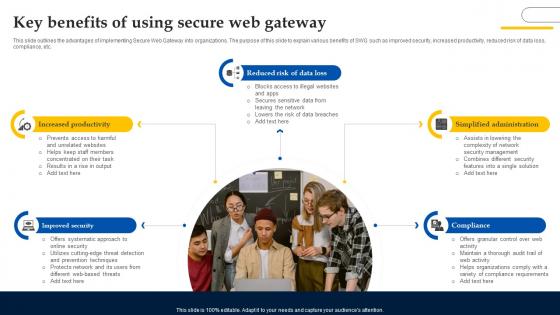
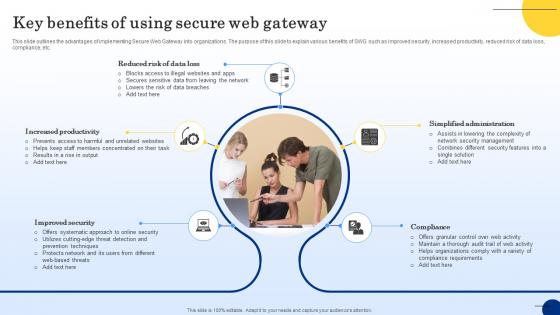
Web Access Control Solution Key Benefits Of Using Secure Web Gateway
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Slidegeeks has constructed Web Access Control Solution Key Benefits Of Using Secure Web Gateway after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
-
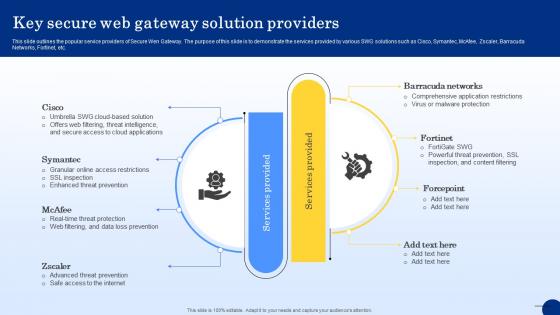
Web Access Control Solution Key Secure Web Gateway Solution Providers
This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Web Access Control Solution Key Secure Web Gateway Solution Providers to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Web Access Control Solution Key Secure Web Gateway Solution Providers.
-
About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf
This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc. Boost your pitch with our creative About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
-
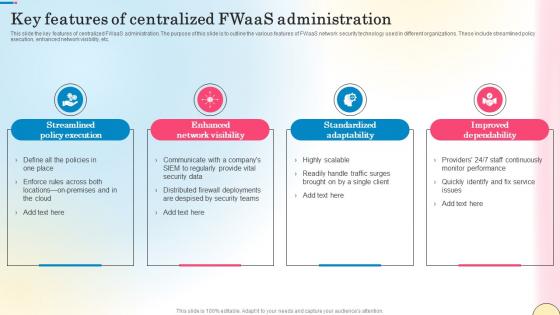
Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf
This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc. Slidegeeks has constructed Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
-
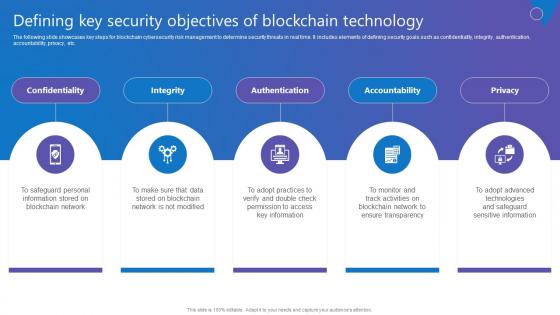
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
-
Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf
The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
-
Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
-
Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf
The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf
The following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as etheruem virtual machine, solidity compiler, etherscan blockchain explorer, etc. Welcome to our selection of the Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today
-
Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
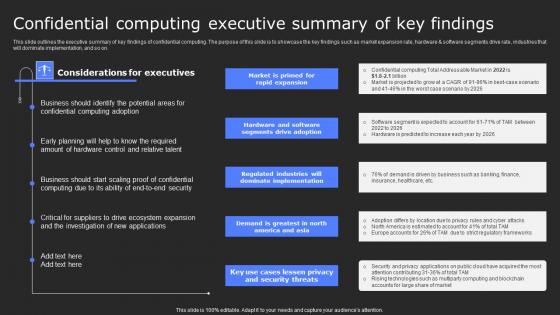
Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf
-
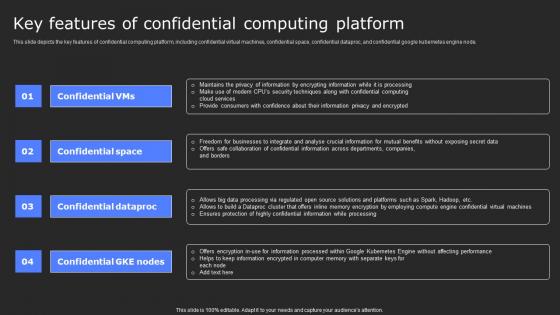
Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential google kubernetes engine node. Create an editable Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
-
Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Create an editable Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
-
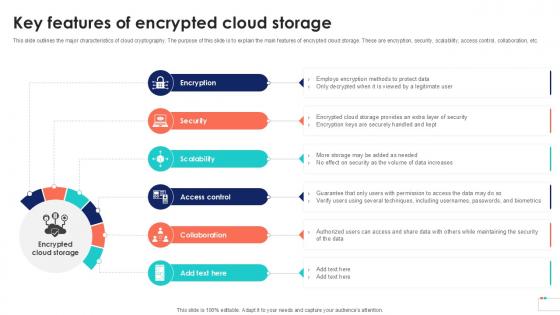
Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
-
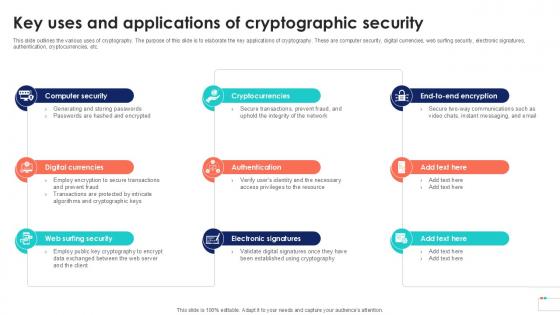
Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Want to ace your presentation in front of a live audience Our Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
-
Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS. Retrieve professionally designed Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
-
The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Find a pre-designed and impeccable The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
-
Key Benefits Of Using Secure Web Gateway Web Threat Protection System
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Welcome to our selection of the Key Benefits Of Using Secure Web Gateway Web Threat Protection System. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
-
Key Secure Web Gateway Solution Providers Web Threat Protection System
This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Secure Web Gateway Solution Providers Web Threat Protection System from Slidegeeks and deliver a wonderful presentation.
-
Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V
This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Get a simple yet stunning designed Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.
-
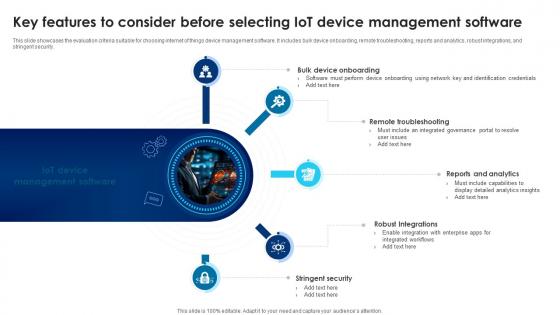
Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V
This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security. Take your projects to the next level with our ultimate collection of Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
-
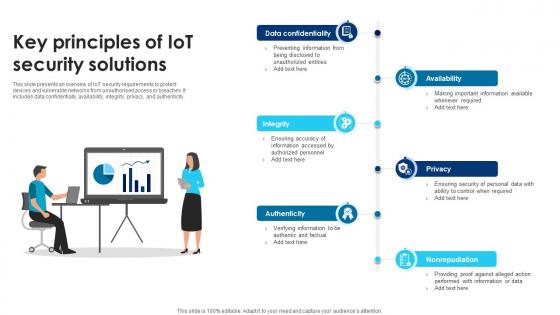
Building Trust With IoT Security Key Principles Of IoT Security Solutions IoT SS V
This slide presents an overview of IoT security requirements to protect devices and vulnerable networks from unauthorised access or breaches. It includes data confidentially, availability, integrity, privacy, and authenticity. Do you know about Slidesgeeks Building Trust With IoT Security Key Principles Of IoT Security Solutions IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
-
Building Trust With IoT Security Key Stats Associated With Connected Devices IoT SS V
This slide showcases year on year growth of connected devices globally. It includes stats data related to connected devise growth, sensors and actuators market size, and China as a largest contributor to consumer IoT devices. Find a pre-designed and impeccable Building Trust With IoT Security Key Stats Associated With Connected Devices IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
-
Building Trust With IoT Security Overview Of IoT Security And Privacy With Key Benefits IoT SS V
This slide presents the benefits of Internet of things devices security and data privacy. It includes benefits such as reduce risk of information leaks, ensures authenticity, reduce financial liabilities, minimise negative impact on business operations. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Overview Of IoT Security And Privacy With Key Benefits IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
-
Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V
This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Key Smart Home Stats For Enhancing Security And Technology Utilizing Smart Appliances IoT SS V
This slide provides an overview of the key statistics related to technology growth, security, video assistant and smart speaker. Major stats covered are a majority of the audience feel confutable using security devices, installation of technologies help homeowners save an average of dollar 98, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Smart Home Stats For Enhancing Security And Technology Utilizing Smart Appliances IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
-
Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain
This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain can be your best option for delivering a presentation. Represent everything in detail using Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
-
Key Activities Security Service Provider Business Model BMC SS V
This slide covers the most curtailed activity the company performs to operate the business successfully. It includes activities such as software development, hardware production, marketing and customer support. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Activities Security Service Provider Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
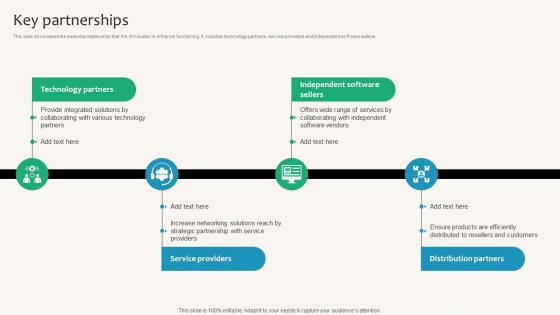
Key Partnerships Security Service Provider Business Model BMC SS V
This slide showcases the essential relationship that the firm builds to enhance functioning. It includes technology partners, service providers and independent software sellers. Present like a pro with Key Partnerships Security Service Provider Business Model BMC SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
-
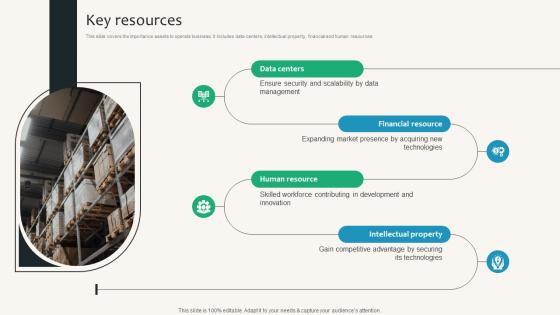
Key Resources Security Service Provider Business Model BMC SS V
This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources. Slidegeeks is here to make your presentations a breeze with Key Resources Security Service Provider Business Model BMC SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
-
Key Benefits Of Implementing Application Security Testing Ppt Powerpoint Icons
This slide highlights the key advantages of application security which include minimum risk exposure, security, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Benefits Of Implementing Application Security Testing Ppt Powerpoint Icons from Slidegeeks and deliver a wonderful presentation.
-
Key Advantages Of IoT Based Atm Security System IoT In Banking For Digital Future IoT SS V
Following slide exhibits various benefits of installing IoT devices and sensors into ATM system assuring remote monitoring and control of banking assts. It includes pointers such as real time data, enhance customer service, cost reduction, etc. This modern and well-arranged Key Advantages Of IoT Based Atm Security System IoT In Banking For Digital Future IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
-
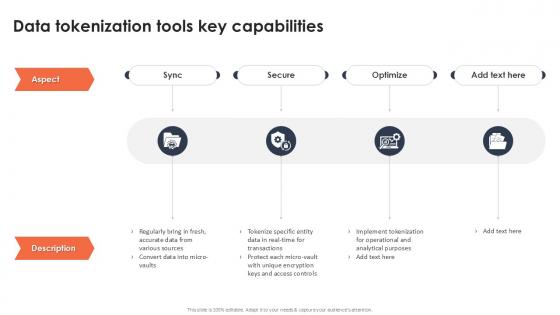
Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint
If you are looking for a format to display your unique thoughts, then the professionally designed Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
-
Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint
This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint from Slidegeeks and deliver a wonderful presentation.
-
About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Want to ace your presentation in front of a live audience Our About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
-
Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example.
-
Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. This Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
-
Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
-
Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example
This slide showcases the principles of security testing such as confidentiality, integrity, authentication, authorization, availability, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
-
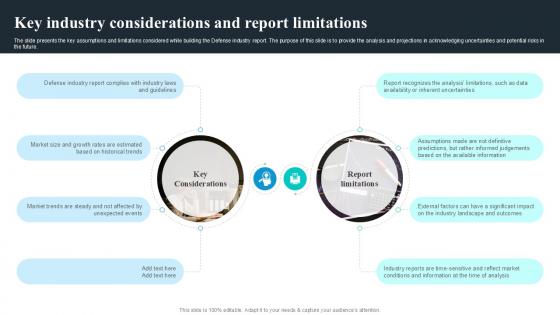
Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. The slide presents the key assumptions and limitations considered while building the Defense industry report. The purpose of this slide is to provide the analysis and projections in acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
-
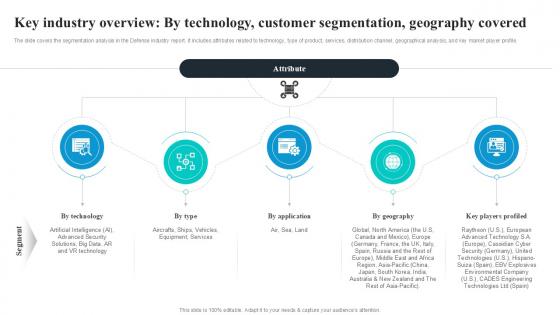
Key Industry Overview By Technology Global Security Industry PPT Template IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Key Industry Overview By Technology Global Security Industry PPT Template IR SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Key Industry Overview By Technology Global Security Industry PPT Template IR SS V
-
Key Takeaways And Strategic Insights Global Security Industry PPT Sample IR SS V
This slide highlights the global Defense insights which are responsible for the growth. The purpose of this slide is to provide a brief insights related to the Defense market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security defense analysis. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Takeaways And Strategic Insights Global Security Industry PPT Sample IR SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.