Risk procedure PowerPoint Presentation Templates and Google Slides
-
Risk Based Procedures To IT Security Addressing The Companies Digitization Levels By Sectors Infographics PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Addressing The Companies Digitization Levels By Sectors Infographics PDF bundle. Topics like Digital Spend, Digitalization Level, Business Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
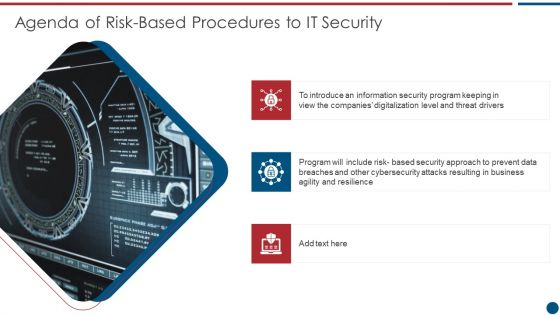
Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF
This is a Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Program Keeping, Threat Drivers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Major Components, Criticality Rating, Failure Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Risk Management, Transparent Communication, Standardized Incident. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
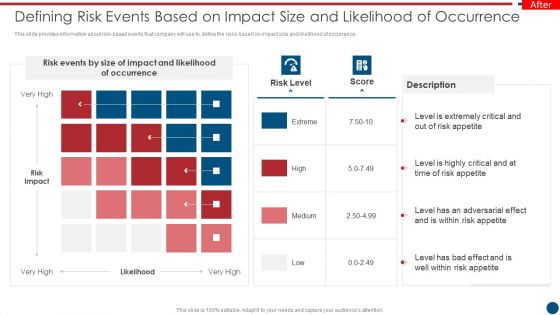
Risk Based Procedures To IT Security Defining Risk Events Based On Impact Size And Likelihood Summary PDF
This slide provides information about risk-based events that company will use to define the risks based on impact size and likelihood of occurrence. This is a Risk Based Procedures To IT Security Defining Risk Events Based On Impact Size And Likelihood Summary PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Events, Risk Impact, Risk Appetite. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manual Vulnerability, Vulnerability Scanning, Automation Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF
Mentioned slide displays a five-day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF bundle. Topics like Assess Security, Gap Analysis, Gap Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Based Procedures To IT Security Encountered Risks Summary And Their Impact Assessment Topics PDF
Mentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Encountered Risks Summary And Their Impact Assessment Topics PDF. Use them to share invaluable insights on Risks Category, High Inherent, Risk Magnitude and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
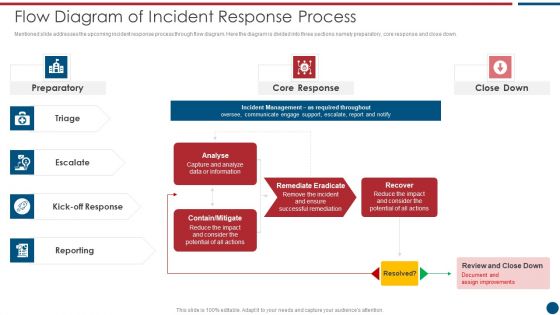
Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF bundle. Topics like Cyberrisk Management, Security Organization, Technology Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. This is a Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Leadership, Evaluation Direction, Change Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
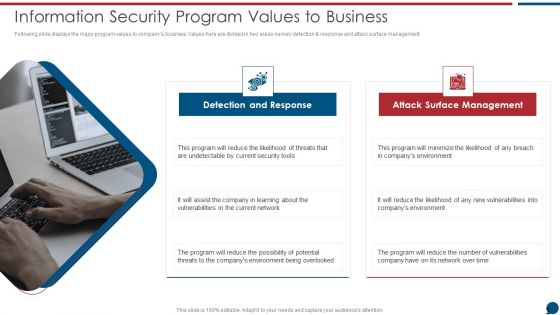
Risk Based Procedures To IT Security Information Security Program Values To Business Infographics PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting Risk Based Procedures To IT Security Information Security Program Values To Business Infographics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Detection Response, Attack Surface, Current Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. This is a Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Desk, Support Team, Provide Integration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
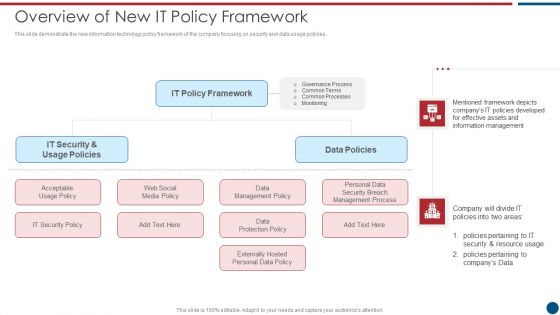
Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like IT Policy, Data Policies, IT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
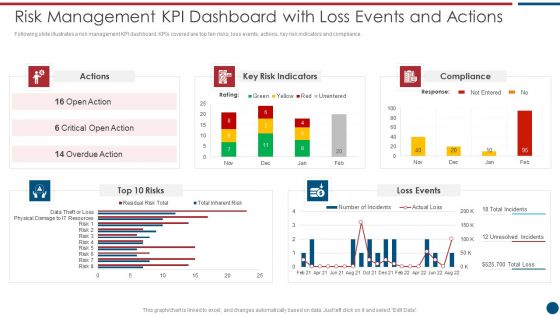
Risk Based Procedures To IT Security Risk Management KPI Dashboard With Loss Events And Actions Mockup PDF
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Risk Management KPI Dashboard With Loss Events And Actions Mockup PDF bundle. Topics like Key Risk, Indicators Compliance, Loss Events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
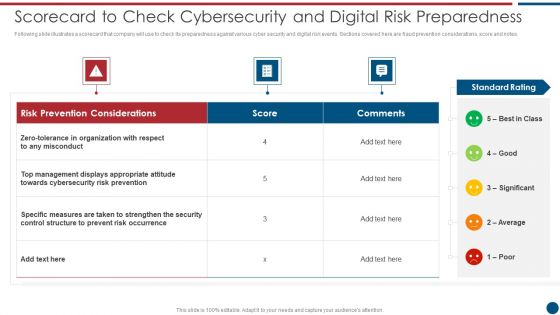
Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF. Use them to share invaluable insights on Risk Prevention, Risk Prevention, Risk Occurrence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
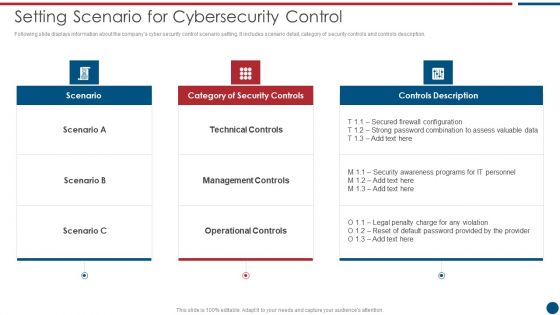
Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF bundle. Topics like Technical Controls, Management Controls, Operational Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
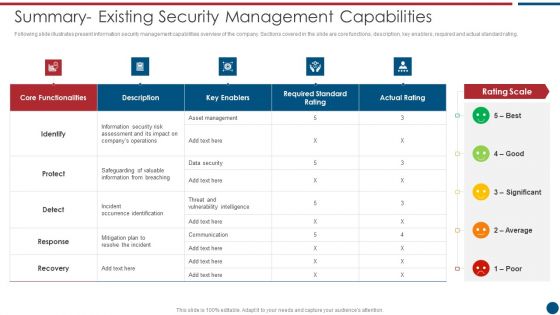
Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Asset Management, Key Enablers, Communication Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
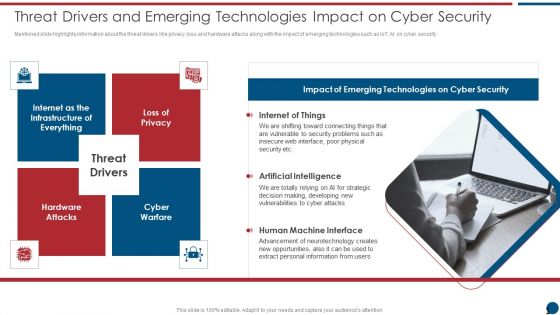
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Icons Slide For Risk Based Procedures To IT Security Ppt PowerPoint Presentation Gallery Vector PDF
Presenting our innovatively structured Icons Slide For Risk Based Procedures To IT Security Ppt PowerPoint Presentation Gallery Vector PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
-
Risk Based Procedures To IT Security Action Plan In Case Of Breaches Ppt PowerPoint Presentation File Model PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Action Plan In Case Of Breaches Ppt PowerPoint Presentation File Model PDF bundle. Topics like Threat Encountered, Communication Mode, Security Breach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
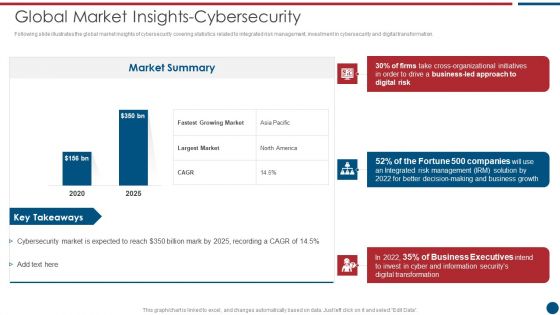
Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF bundle. Topics like Market Summary, Largest Market, Business Led can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Based Procedures To IT Security Risk Governance Structure Ppt PowerPoint Presentation Icon Gallery PDF
Mentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Risk Governance Structure Ppt PowerPoint Presentation Icon Gallery PDF. Use them to share invaluable insights on Risk Management, Board Directors, Strategy Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
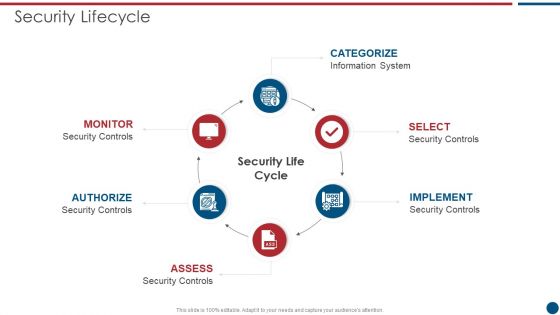
Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF
This is a Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information System, Security Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
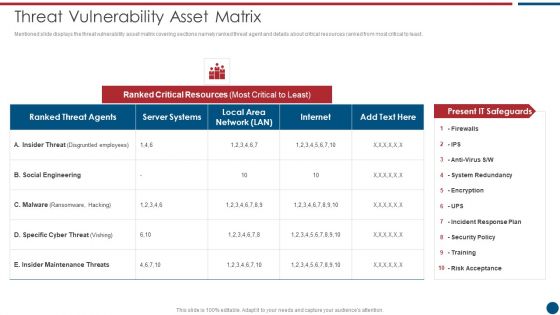
Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF bundle. Topics like Ranked Critical, Server Systems, Social Engineering can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Table Of Contents For Risk Based Procedures To IT Security Wd Ppt PowerPoint Presentation File Professional PDF
This is a Table Of Contents For Risk Based Procedures To IT Security Wd Ppt PowerPoint Presentation File Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Global Market, IoT Products, Companies Digitization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Table Of Contents For Risk Based Procedures To IT Security Slides PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Risk Based Procedures To IT Security Slides PDF bundle. Topics like Gap Identification, Business Priorities, Digitization Levels can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
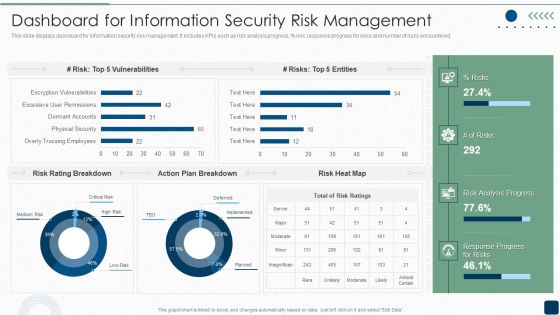
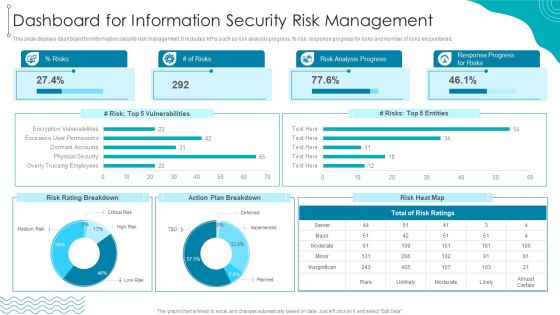
ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF bundle. Topics like Vulnerabilities, Rating Breakdown, Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
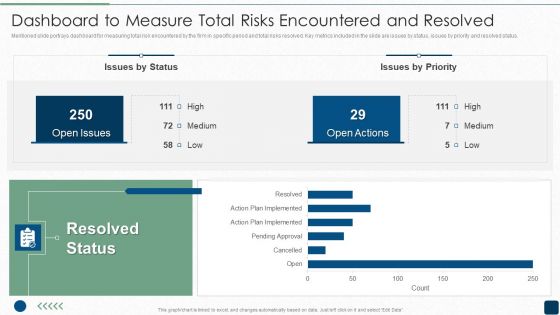
ISO 27001 Certification Procedure Dashboard To Measure Total Risks Encountered And Resolved Topics PDF
Mentioned slide portrays dashboard for measuring total risk encountered by the firm in specific period and total risks resolved. Key metrics included in the slide are issues by status, issues by priority and resolved status.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Dashboard To Measure Total Risks Encountered And Resolved Topics PDF. Use them to share invaluable insights on Resolved Status, Open Issues, Open Actions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
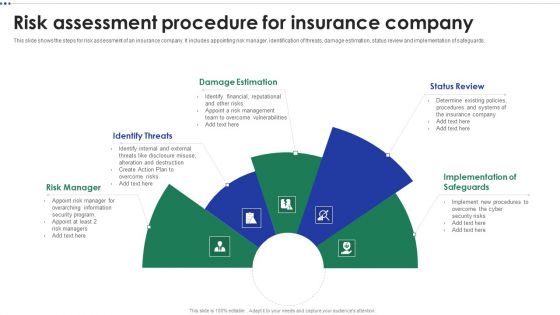
Risk Assessment Procedure For Insurance Company Diagrams PDF
This slide shows the steps for risk assessment of an insurance company. It includes appointing risk manager, identification of threats, damage estimation, status review and implementation of safeguards. Presenting Risk Assessment Procedure For Insurance Company Diagrams PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Threats, Damage Estimation, Status Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF. Use them to share invaluable insights on Analysis Progress, Response Progress, Plan Breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF bundle. Topics like Technical Failures, Phishing Emails, Data Breaching can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
ISO 27001 Organizational Qualifying Procedure Total Risk Events Encountered And Loss Amount Involved Icons PDF
Mentioned slide portrays year over year stats of number of risk events occurred within the firm. It also includes the total amount of loss caused from risk events annually.Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Total Risk Events Encountered And Loss Amount Involved Icons PDF. Use them to share invaluable insights on Highest Occurrence, Company Recorded, Resulting A Monetary and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
ISO 27001 Certification Procedure Defining Risk Level And Impact Score Introduction PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Defining Risk Level And Impact Score Introduction PDF bundle. Topics like Extremely, Immediate Controlling, Operations Of Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
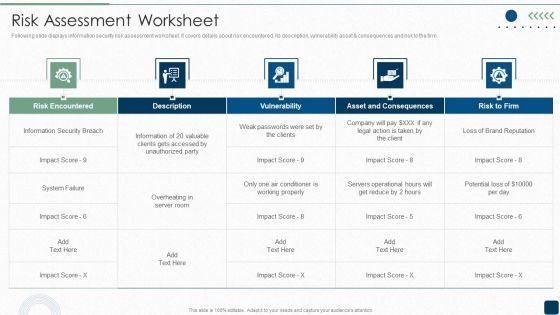
ISO 27001 Certification Procedure Risk Assessment Worksheet Diagrams PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset consequences and risk to the firm.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Risk Assessment Worksheet Diagrams PDF bundle. Topics like Risk Encountered, Asset And Consequences, Information Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
ISO 27001 Organizational Qualifying Procedure Defining Risk Level And Impact Score Microsoft PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Defining Risk Level And Impact Score Microsoft PDF bundle. Topics like Requires Immediate, Effective Controlling, Reputation Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF bundle. Topics like Unauthorized Activity, Technology Risk, Financial Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
ISO 27001 Organizational Qualifying Procedure Mitigation Plan To Resolve Encountered Risk Events Professional PDF
Mentioned slide portrays mitigation plan to resolve the encountered risk events. It includes information of risk encountered, its description, threat level, mitigation plan, resources required, responsibility, resolution time and communication channel.Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Mitigation Plan To Resolve Encountered Risk Events Professional PDF. Use them to share invaluable insights on Resources Required, Estimated Resolution, Communication Channel and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
ISO 27001 Organizational Qualifying Procedure Risk Assessment Worksheet Information PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset consequences and risk to the firm.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Risk Assessment Worksheet Information PDF bundle. Topics like Information Security, Risk Encountered, Asset And Consequences can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
ISO 27001 Organizational Qualifying Procedure Risk Events Reporting And Likelihood Clipart PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Risk Events Reporting And Likelihood Clipart PDF. Use them to share invaluable insights on Risk Encountered, Affected Asset, Area Of Impact and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Retail Business Product Planning Procedure Risk Management Plan To Mitigate Threats Designs PDF
This slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Deliver and pitch your topic in the best possible manner with this Retail Business Product Planning Procedure Risk Management Plan To Mitigate Threats Designs PDF. Use them to share invaluable insights on Contingency Plan, Secondary Risk, Probability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
How Electronic Commerce Financial Procedure Can Be Enhanced Financial Risk Mitigation Plan Graphics PDF
This slide showcases financial risk mitigation plan for ecommerce website. It provides information about finance information, cross border trade, inventory tracking, manual reconciliation, bank receipts, stock valuations, financial technology, etc.Want to ace your presentation in front of a live audience Our How Electronic Commerce Financial Procedure Can Be Enhanced Financial Risk Mitigation Plan Graphics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
-
How Electronic Commerce Financial Procedure Can Be Enhanced Impact Of Financial Risks On Online Designs PDF
This slide depicts impact of financial risks on online store metrics. It provides information about online fraud, frequent chargebacks, high volume of transactions, lengthy delivery time, merchant risk, cyber hacking, customer satisfaction, etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give How Electronic Commerce Financial Procedure Can Be Enhanced Impact Of Financial Risks On Online Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable How Electronic Commerce Financial Procedure Can Be Enhanced Impact Of Financial Risks On Online Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
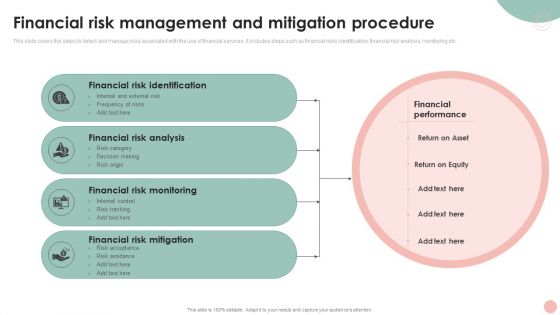
Company Risk Assessment Plan Financial Risk Management And Mitigation Procedure Summary PDF
This slide covers the steps to detect and manage risks associated with the use of financial services. It includes steps such as financial risks identification, financial risk analysis, monitoring etc. Are you in need of a template that can accommodate all of your creative concepts. This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Company Risk Assessment Plan Financial Risk Management And Mitigation Procedure Summary PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
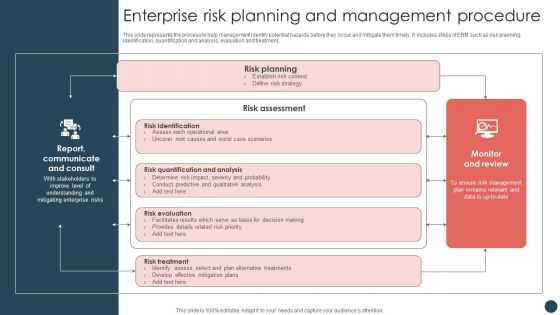
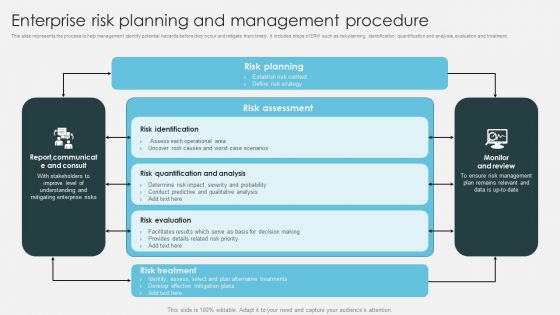
Strategic Risk Management Plan Enterprise Risk Planning And Management Procedure Template PDF
This slide represents the process to help management identify potential hazards before they occur and mitigate them timely. It includes steps of ERM such as risk planning, identification, quantification and analysis, evaluation and treatment. Explore a selection of the finest Strategic Risk Management Plan Enterprise Risk Planning And Management Procedure Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Strategic Risk Management Plan Enterprise Risk Planning And Management Procedure Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
-
Enterprise Risk Management And Mitigation Program Enterprise Risk Planning And Management Procedure Icons PDF
This slide represents the process to help management identify potential hazards before they occur and mitigate them timely. It includes steps of ERM such as risk planning, identification, quantification and analysis, evaluation and treatment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Enterprise Risk Management And Mitigation Program Enterprise Risk Planning And Management Procedure Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Enterprise Risk Management And Mitigation Program Enterprise Risk Planning And Management Procedure Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
-
Strategic Risk Management And Mitigation Plan Enterprise Risk Planning And Management Procedure Formats PDF
This slide represents the process to help management identify potential hazards before they occur and mitigate them timely. It includes steps of ERM such as risk planning, identification, quantification and analysis, evaluation and treatment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Strategic Risk Management And Mitigation Plan Enterprise Risk Planning And Management Procedure Formats PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Strategic Risk Management And Mitigation Plan Enterprise Risk Planning And Management Procedure Formats PDF.
-
Enterprise Risk Planning And Management Procedure Introduction To ERM Professional PDF
This slide represents the process to help management identify potential hazards before they occur and mitigate them timely. It includes steps of ERM such as risk planning, identification, quantification and analysis, evaluation and treatment.Slidegeeks is here to make your presentations a breeze with Enterprise Risk Planning And Management Procedure Introduction To ERM Professional PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
-
Enterprise Risk Management Enterprise Risk Planning And Management Procedure Information PDF
This slide represents the process to help management identify potential hazards before they occur and mitigate them timely. It includes steps of ERM such as risk planning, identification, quantification and analysis, evaluation and treatment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Enterprise Risk Management Enterprise Risk Planning And Management Procedure Information PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
Crisis Response Procedure For Reducing Workplace Risk Brochure PDF
This slide mentions points to consider when formulating emergency procedure for organizations. It includes informing, acting and rescuing employees in an event of emergency. Persuade your audience using this Crisis Response Procedure For Reducing Workplace Risk Brochure PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Inform, Act, Rescue. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Organizational Risk Management Procedure Icon Infographics PDF
Persuade your audience using this Organizational Risk Management Procedure Icon Infographics PDF. This PPT design covers Fourstages, thus making it a great tool to use. It also caters to a variety of topics including Organizational Risk, Management Procedure Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
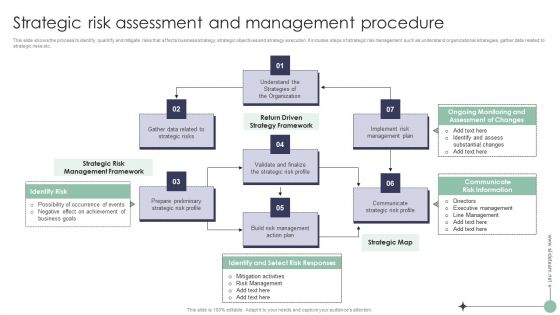
Risk Analysis And Mitigation Plan Strategic Risk Assessment And Management Procedure Background PDF
This slide shows the process to identify, quantify and mitigate risks that affects business strategy, strategic objectives and strategy execution. It includes steps of strategic risk management such as understand organizational strategies, gather data related to strategic risks etc. There are so many reasons you need a Risk Analysis And Mitigation Plan Strategic Risk Assessment And Management Procedure Background PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
-
Operational Risk Assessment And Management Plan Enterprise Risk Planning And Management Procedure Topics PDF
This slide represents the process to help management identify potential hazards before they occur and mitigate them timely. It includes steps of ERM such as risk planning, identification, quantification and analysis, evaluation and treatment. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Operational Risk Assessment And Management Plan Enterprise Risk Planning And Management Procedure Topics PD can be your best option for delivering a presentation. Represent everything in detail using Operational Risk Assessment And Management Plan Enterprise Risk Planning And Management Procedure Topics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.