Protecting proceeds PowerPoint Presentation Templates and Google Slides
-
Blockchain Protection Process Architecture Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this blockchain protection process architecture ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
-
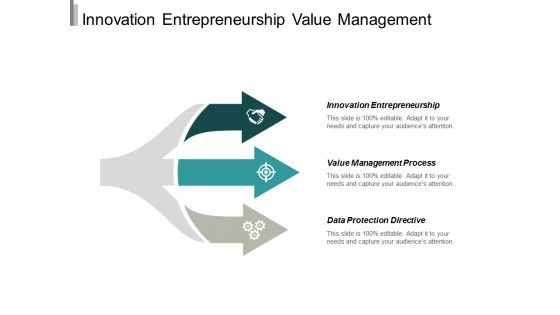
Innovation Entrepreneurship Value Management Process Data Protection Directive Ppt PowerPoint Presentation Professional Layout
This is a innovation entrepreneurship value management process data protection directive ppt powerpoint presentation professional layout. This is a three stage process. The stages in this process are innovation entrepreneurship, value management process, data protection directive.
-
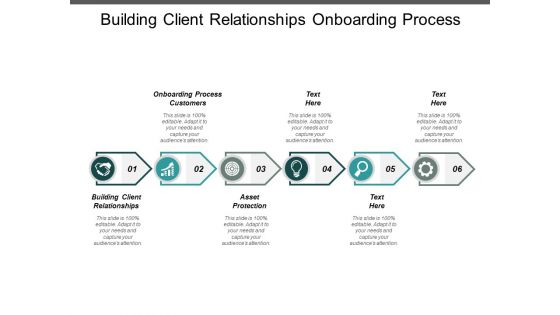
Building Client Relationships Onboarding Process Customers Asset Protection Ppt PowerPoint Presentation Ideas Graphics Example
This is a building client relationships onboarding process customers asset protection ppt powerpoint presentation ideas graphics example. This is a six stage process. The stages in this process are building client relationships, onboarding process customers, asset protection.
-
Business Process Strategy Dollar Sign Protected An Arrow Clipart
Connect The Dots With Our business process strategy dollar sign protected an arrow clipart Powerpoint Templates. Watch The Whole Picture Clearly Emerge. Dot Your Thoughts With Our Arrows Powerpoint Templates. Give Your Demeanor That Propel Look.
-
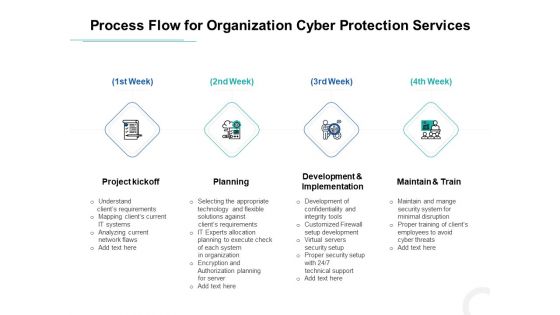
Develop Corporate Cyber Security Risk Mitigation Plan Process Flow For Organization Cyber Protection Services Background PDF
This is a develop corporate cyber security risk mitigation plan process flow for organization cyber protection services background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, maintain and train. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
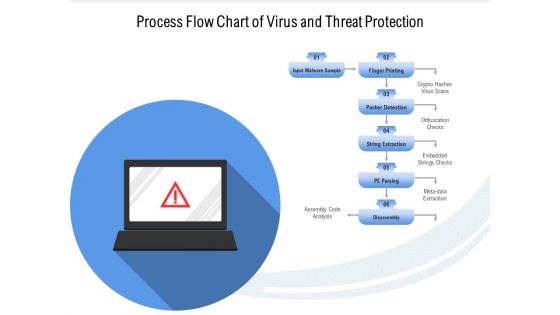
Process Flow Chart Of Virus And Threat Protection Ppt PowerPoint Presentation File Layout PDF
Persuade your audience using this process flow chart of virus and threat protection ppt powerpoint presentation file layout pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including analysis, extraction, obfuscation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
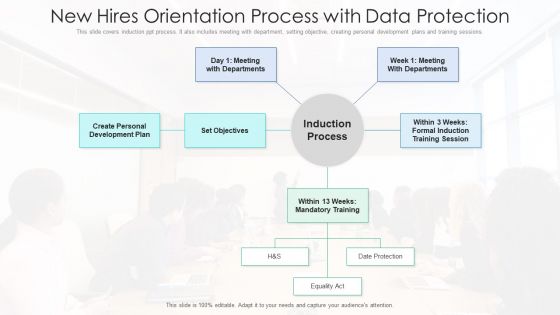
New Hires Orientation Process With Data Protection Ppt PowerPoint Presentation File Graphics Download PDF
This slide covers induction ppt process. It also includes meeting with department, setting objective, creating personal development plans and training sessions. Showcasing this set of slides titled new hires orientation process with data protection ppt powerpoint presentation file graphics download pdf. The topics addressed in these templates are process, training, development. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
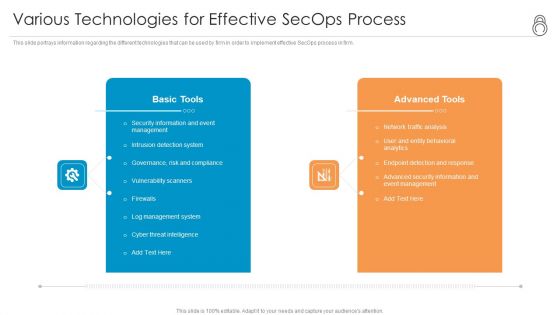
Enhanced Protection Corporate Event Administration Various Technologies For Effective Secops Process Designs PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a enhanced protection corporate event administration various technologies for effective secops process designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
6 Procedure Infographics Of Patent Protect Idea Ppt PowerPoint Presentation File Microsoft PDF
Persuade your audience using this 6 procedure infographics of patent protect idea ppt powerpoint presentation file microsoft pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including 6 procedure infographics of patent protect idea. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
6 Procedure Slide For Data Protection Ppt PowerPoint Presentation Gallery Gridlines PDF
Persuade your audience using this 6 procedure slide for data protection ppt powerpoint presentation gallery gridlines pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including 6 procedure slide for data protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. This is a New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Applicable, Enforcement, Develop Good. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Internet Defence Protection Kill Chain Process Roadmap Guidelines PDF
This slide covers cybersecurity kill chain procedure roadmap illustrating 7 steps such as reconnaissance, weaponisation, payload, exploitation, installation , command control and actions on objectives.Persuade your audience using this Internet Defence Protection Kill Chain Process Roadmap Guidelines PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Weaponization, Exploitation, Command Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Internet Defence Protection Risk Assessment Process Roadmap Diagrams PDF
This slide represents 4 step roadmap for cybersecurity risk assessment procedure illustrating steps such as information gathering, risk identification, risk assessment and risk evaluation.Presenting Internet Defence Protection Risk Assessment Process Roadmap Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Information Gathering, Risk Identification, Risk Assessment . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
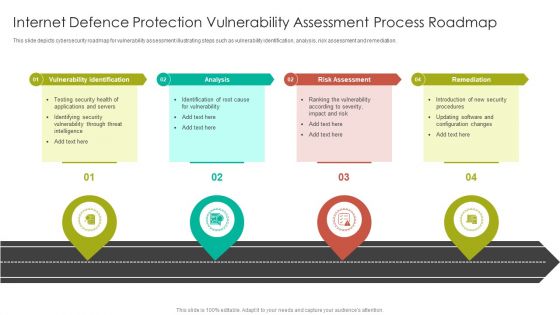
Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF
This slide depicts cybersecurity roadmap for vulnerability assessment illustrating steps such as vulnerability identification, analysis, risk assessment and remediation.Presenting Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Identification, Risk Assessment, Remediation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Data Protection And Information Security Policy And Procedure Guidelines PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Protection And Information Security Policy And Procedure Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Protection And Information Security Policy And Procedure Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
-
Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
New Staff Onboarding Program Data Protection And Information Security Policy And Procedure Sample PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Want to ace your presentation in front of a live audience Our New Staff Onboarding Program Data Protection And Information Security Policy And Procedure Sample PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
-
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Reactive And Proactive Business Information Protection Evaluation Process Sample PDF
This slide covers reactive and proactive business security evaluation process which includes evaluating security based on set standards. Persuade your audience using this Reactive And Proactive Business Information Protection Evaluation Process Sample PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Conventional Reactive, Proactive Security, Evaluation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Insider Threat Mitigation And Protection Procedure Professional PDF
This slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage.Presenting Insider Threat Mitigation And Protection Procedure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigation Program, Compile Information, Determine Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Slidegeeks is here to make your presentations a breeze with Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
-
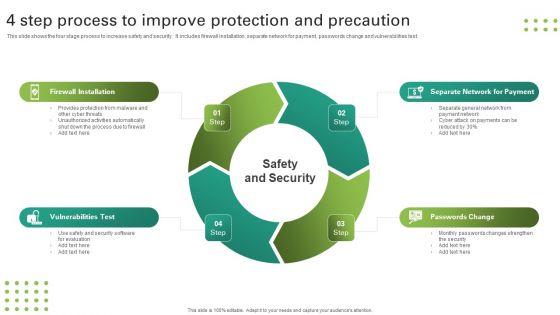
4 Step Process To Improve Protection And Precaution Topics PDF
This slide shows the four stage process to increase safety and security. It includes firewall installation, separate network for payment, passwords change and vulnerabilities test. Persuade your audience using this 4 Step Process To Improve Protection And Precaution Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Firewall Installation, Separate Network For Payment, Passwords Change. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
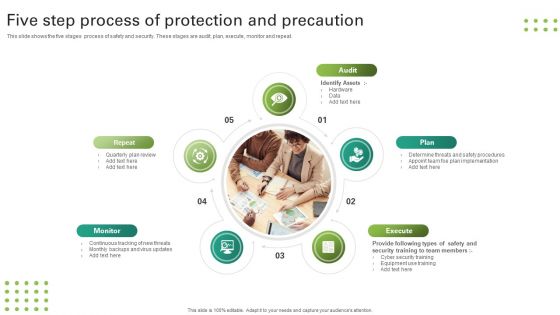
Five Step Process Of Protection And Precaution Formats PDF
This slide shows the five stages process of safety and security. These stages are audit, plan, execute, monitor and repeat. Persuade your audience using this Five Step Process Of Protection And Precaution Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Audit, Plan, Execute. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
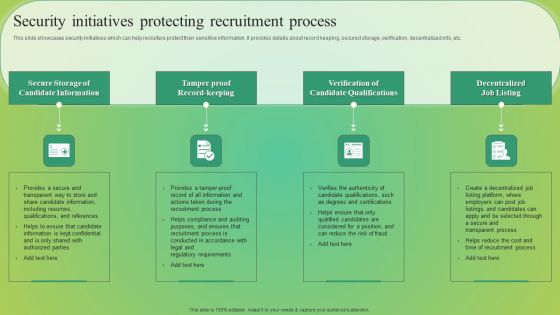
Security Initiatives Protecting Recruitment Process Elements PDF
This slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Slidegeeks is here to make your presentations a breeze with Security Initiatives Protecting Recruitment Process Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
-
Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.