Perimeter Architecture PowerPoint Presentation Templates and Google Slides
-
Software Defined Perimeter Enhancing Workload Efficiency Through Cloud Architecture Pictures Pdf
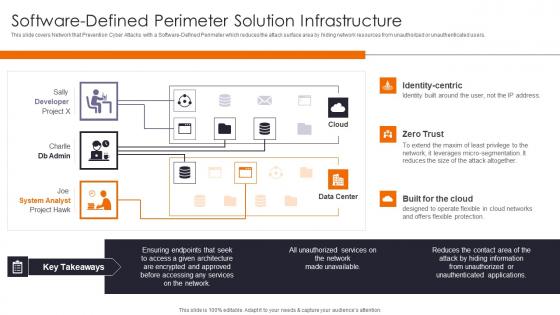
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Present like a pro with Software Defined Perimeter Enhancing Workload Efficiency Through Cloud Architecture Pictures Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
-
Zero Trust Network Access Vs Zero Trust Architecture Software Defined Perimeter SDP
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Presenting this PowerPoint presentation, titled Zero Trust Network Access Vs Zero Trust Architecture Software Defined Perimeter SDP, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Vs. Zero Trust Architecture Software Defined Perimeter SDP. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Vs. Zero Trust Architecture Software Defined Perimeter SDP that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
-
As A Service Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Boost your pitch with our creative As A Service Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
-
Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP
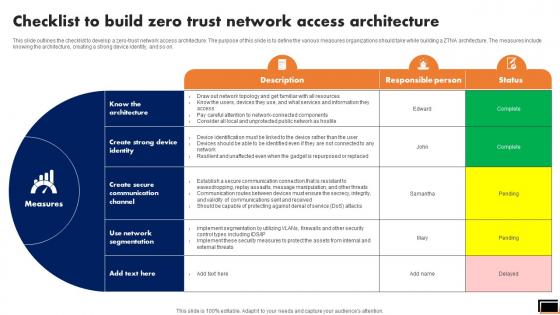
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
-
Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP
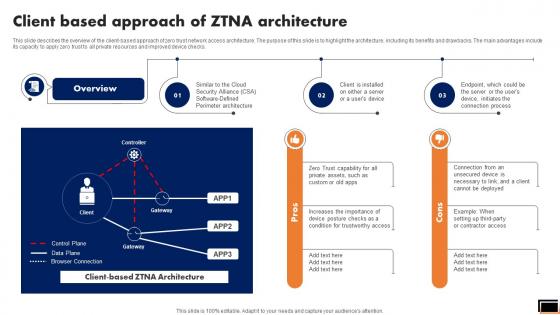
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
-
External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP
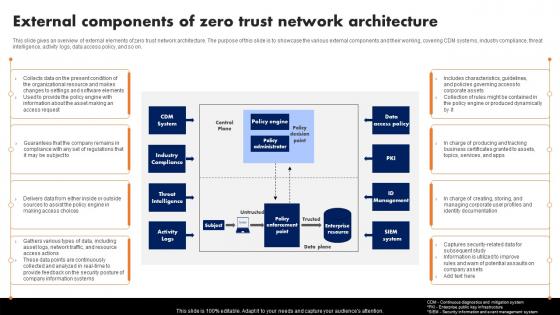
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
-
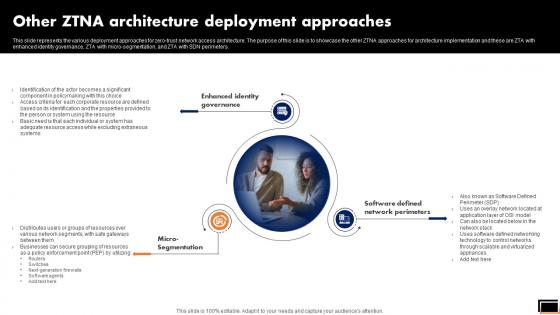
Other Ztna Architecture Deployment Approaches Software Defined Perimeter SDP
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other Ztna Architecture Deployment Approaches Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
-
Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
-
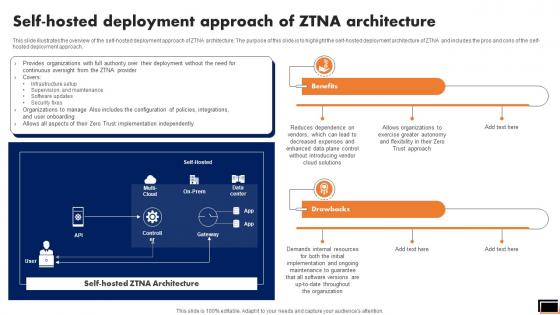
Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Do you know about Slidesgeeks Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
-
Working Functions Of Zero Trust Network Access Architecture Software Defined Perimeter SDP
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Functions Of Zero Trust Network Access Architecture Software Defined Perimeter SDP was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Functions Of Zero Trust Network Access Architecture Software Defined Perimeter SDP.
-
Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
-
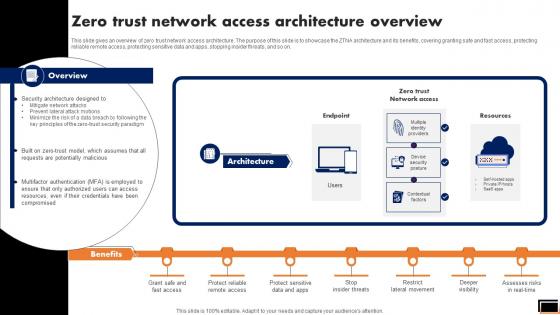
Zero Trust Network Access Architecture Overview Software Defined Perimeter SDP
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Network Access Architecture Overview Software Defined Perimeter SDP. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
-
Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.