It threats PowerPoint Presentation Templates and Google Slides
-
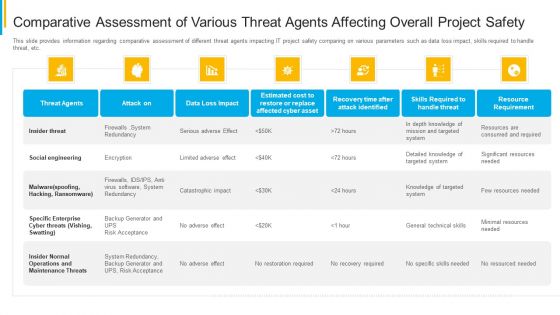
Project Security Administration IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Background PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this project security administration it comparative assessment of various threat agents affecting overall project safety background pdf. Use them to share invaluable insights on resource requirement, maintenance threats, cyber threats, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Project Security Administration IT Contingency Plan For Managing Threats To Ensure It Project Safety Mockup PDF
This slide provides information regarding contingency plan for managing threats to ensure IT project safety with aid of technical equipment ensuring contingency plans. Deliver an awe inspiring pitch with this creative project security administration it contingency plan for managing threats to ensure it project safety mockup pdf bundle. Topics like distributes systems, mainframe systems, wide area network, local area network, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
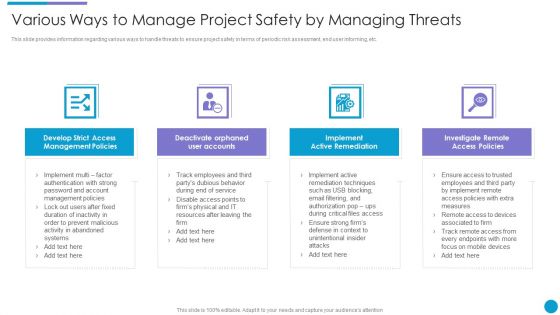
Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Contd Sample PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a project security administration it various ways to manage project safety by managing threats contd sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deactivate orphaned user accounts, develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
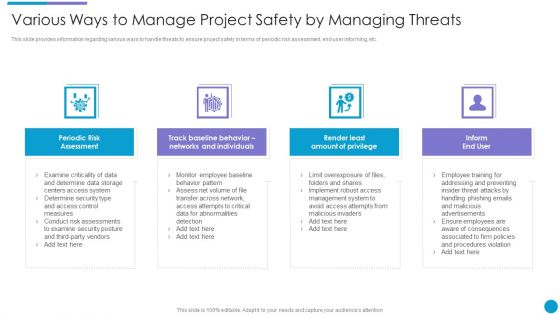
Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
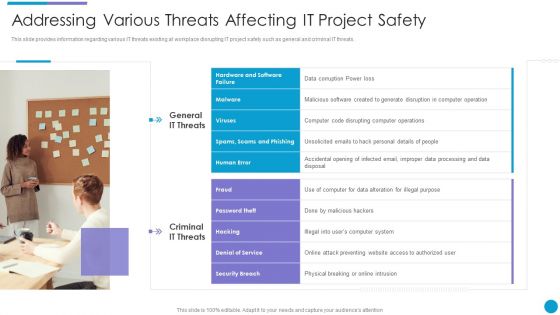
Project Security Administration IT Addressing Various Threats Affecting IT Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Presenting project security administration it addressing various threats affecting it project safety designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like general it threats, criminal it threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Project Security Administration IT Determine Phases Of Threat Attack Disrupting IT Project Safety Brochure PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. This is a project security administration it determine phases of threat attack disrupting it project safety brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
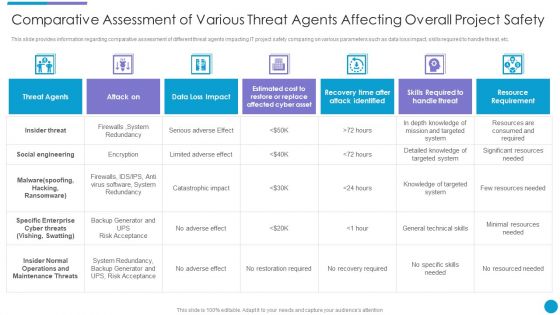
Major Techniques For Project Safety IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Portrait PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative major techniques for project safety it comparative assessment of various threat agents affecting overall project safety portrait pdf bundle. Topics like threat agents, attack on, data loss impact, resource requirement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Major Techniques For Project Safety IT Contingency Plan For Managing Threats To Ensure IT Project Safety Pictures PDF
This slide provides information regarding contingency plan for managing threats to ensure IT project safety with aid of technical equipment ensuring contingency plans. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it contingency plan for managing threats to ensure it project safety pictures pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Major Techniques For Project Safety IT Determine Phases Of Threat Attack Disrupting IT Project Safety Contd Template PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. This is a major techniques for project safety it determine phases of threat attack disrupting it project safety contd template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Major Techniques For Project Safety IT Determine Phases Of Threat Attack Disrupting IT Project Safety Elements PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Presenting major techniques for project safety it determine phases of threat attack disrupting it project safety elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Major Techniques For Project Safety IT Various Ways To Manage Project Safety By Managing Threats Access Structure PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. This is a major techniques for project safety it various ways to manage project safety by managing threats access structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, track baseline behavior networks and individuals, render least amount of privilege, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Major Techniques For Project Safety IT Various Ways To Manage Project Safety By Managing Threats Professional PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting major techniques for project safety it various ways to manage project safety by managing threats professional pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Major Techniques For Project Safety IT Addressing Various Threats Affecting IT Project Safety Structure PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. This is a major techniques for project safety it addressing various threats affecting it project safety structure pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like general it threats, criminal it threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
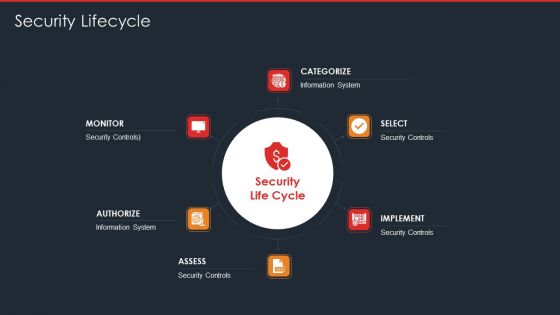
Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Agenda Of Data Safety Initiatives For Effective IT Security Threats Administration Professional PDF
This is a agenda of data safety initiatives for effective it security threats administration professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security program keeping, threat drivers, cybersecurity attacks resulting, business agility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Data Safety Initiatives For Effective IT Security Threats Administration Table Of Contents Themes PDF
Presenting data safety initiatives for effective it security threats administration table of contents themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like global market insights, gap identification, defining business priorities, about security program, companies digitization levels. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
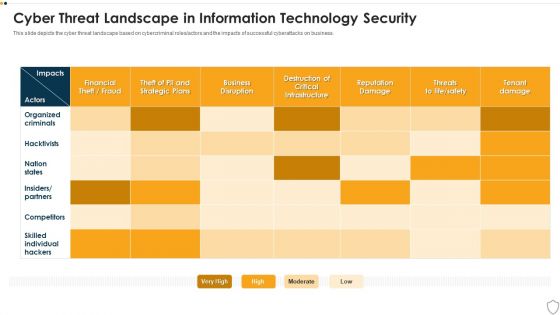
IT Security Cyber Threat Landscape In Information Technology Security Download PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this it security cyber threat landscape in information technology security download pdf. Use them to share invaluable insights on business, competitors, reputation damage, organized criminals and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
IT Security Common Methods Used To Threaten Information Technology Security Ppt Layouts Graphics PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a it security common methods used to threaten information technology security ppt layouts graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
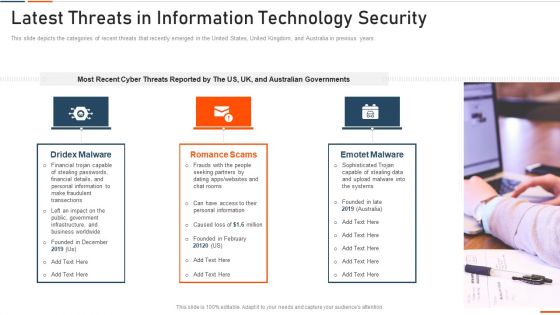
IT Security Latest Threats In Information Technology Security Ppt Slides Visuals PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting it security latest threats in information technology security ppt slides visuals pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dried malware, romance scams, emoted malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
IT Security Types Of Threats In Information Technology Security Ppt Summary Aids PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting it security types of threats in information technology security ppt summary aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
IT Security Dashboard For Threat Tracking In Information Technology Security Ppt Inspiration Gallery PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative it security dashboard for threat tracking in information technology security ppt inspiration gallery pdf bundle. Topics like current risk status, threat report, risk by threats, threats based on role, threats by owners can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Facilitating IT Intelligence Architecture Contingency Plan For Threat Handling In Security Centre Professional PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver and pitch your topic in the best possible manner with this Facilitating IT Intelligence Architecture Contingency Plan For Threat Handling In Security Centre Professional PDF Use them to share invaluable insights on Contingency Solutions, Contingency Considerations, Information Documentation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
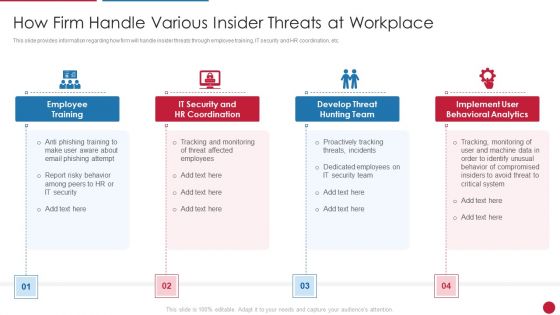
Facilitating IT Intelligence Architecture How Firm Handle Various Insider Threats At Workplace Formats PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a Facilitating IT Intelligence Architecture How Firm Handle Various Insider Threats At Workplace Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training, Develop Threat Hunting Team, Implement User Behavioral Analytics You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Digital Technology Adoption In Banking Industry Case Competition SWOT Analysis Threats Mockup PDF
This slides shows the various threats related to the banking company which includes legal and political framework, high competition, etc.This is a Digital Technology Adoption In Banking Industry Case Competition SWOT Analysis Threats Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Legal And Political Framework, High Competition, Risks Impacting Developing Economies You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
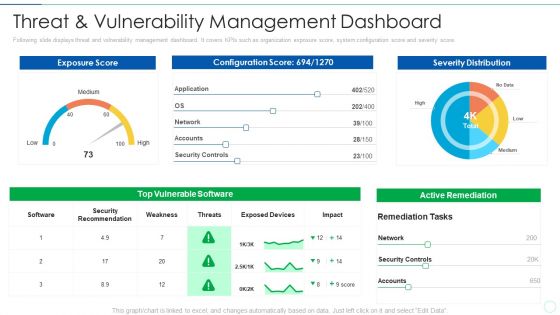
Effective IT Risk Management Process Threat And Vulnerability Management Rules PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this effective it risk management process threat and vulnerability management rules pdf. Use them to share invaluable insights on threat and vulnerability management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Effective IT Risk Management Process Threat Identification And Vulnerability Professional PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative effective it risk management process threat identification and vulnerability professional pdf bundle. Topics like potential vulnerability, system, network, designed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
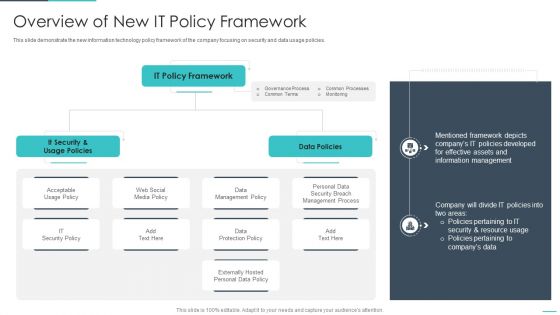
Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
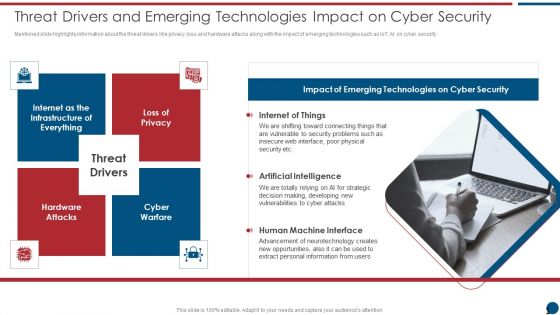
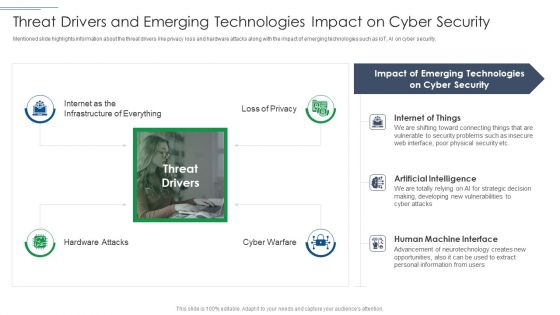
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
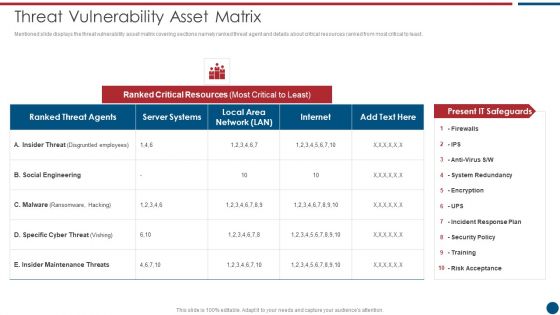
Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF bundle. Topics like Ranked Critical, Server Systems, Social Engineering can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
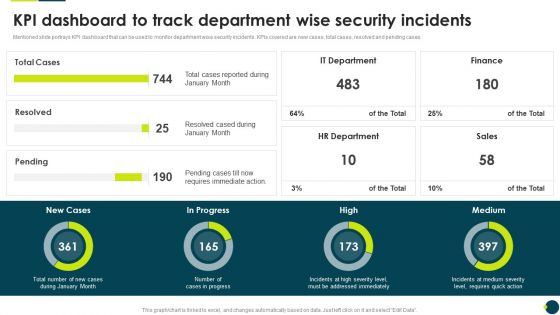
IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF bundle. Topics like It Department, Hr Department, Requires Immediate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
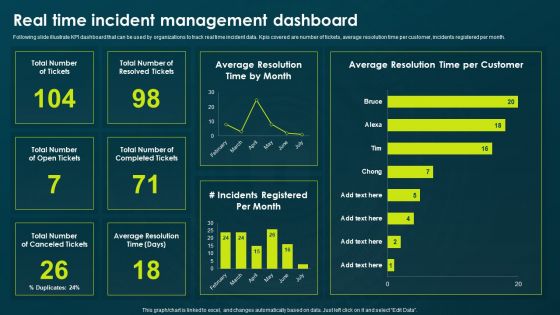
IT Threats Response Playbook Real Time Incident Management Dashboard Formats PDF
Following slide illustrate KPI dashboard that can be used by organizations to track real time incident data. Kpis covered are number of tickets, average resolution time per customer, incidents registered per month. Presenting IT Threats Response Playbook Real Time Incident Management Dashboard Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Resolved Tickets, Average Resolution, Incidents Registered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Information Technology Threat Mitigation Methods Enterprise IT Risk Management Reporting Dashboard Download PDF
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Enterprise IT Risk Management Reporting Dashboard Download PDF bundle. Topics like Enterprise IT Risk, Management Reporting Dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Information Technology Threat Mitigation Methods Impact Of IT Risks On Organization Rules PDF
This slide highlights the impacts of information technology risks on organization which includes graph for overspend project budget and data breach for 2022 year. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Impact Of IT Risks On Organization Rules PDF. Use them to share invaluable insights on Impact Of IT Risks, Organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF bundle. Topics like Organization Systems, Networks, Internal can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Management Dashboard Of IT Department With Threat Frequency Icons PDF
This slide shows dashboard of risk management of IT department representing net critical risks, threat and vulnerability frequency in last 60 days, open audit findings, open and vendor risks etc. Showcasing this set of slides titled Risk Management Dashboard Of IT Department With Threat Frequency Icons PDF. The topics addressed in these templates are Net Critical Risk, Organization, Threat Frequency. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
-
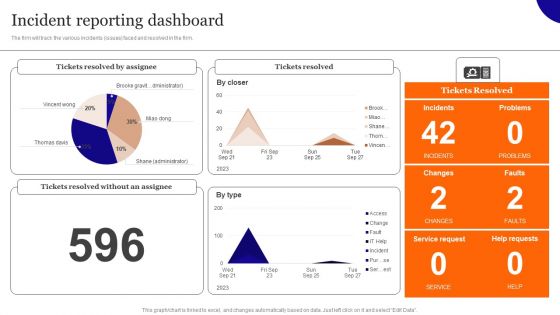
Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF
The firm will track the various incidents issues faced and resolved in the firm. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
-
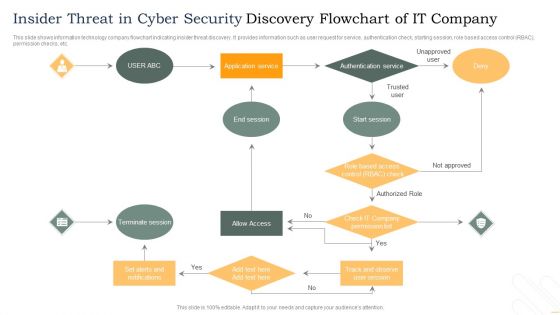
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
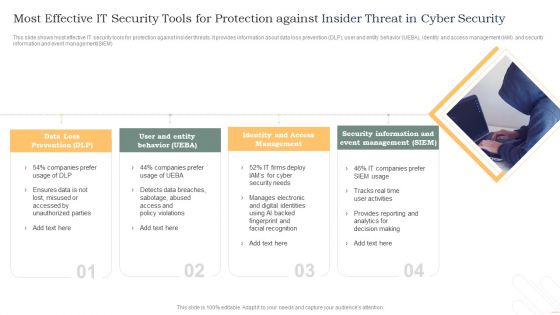
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
IT Security Analysis Plan With Threats And Solutions Infographics PDF
This slide contains the information related to the plan made for the security analysis of the organization and its clients. It also includes the solutions for treating the threats and vulnerabilities. Showcasing this set of slides titled IT Security Analysis Plan With Threats And Solutions Infographics PDF. The topics addressed in these templates are Risk, Applications, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
IT Security Analysis To Prevent Insider Threats Infographics PDF
This slide covers the data on the security by using the technologies to protect the data from the insider threats. It includes the analysis with risk model, CWE, OWASP, SQL injection, misconfiguration, etc. Presenting IT Security Analysis To Prevent Insider Threats Infographics PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Project, Application, Risk Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Icons Slide For IT Threats Response Playbook Download PDF
Download our innovative and attention grabbing Icons Slide For IT Threats Response Playbook Download PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
-
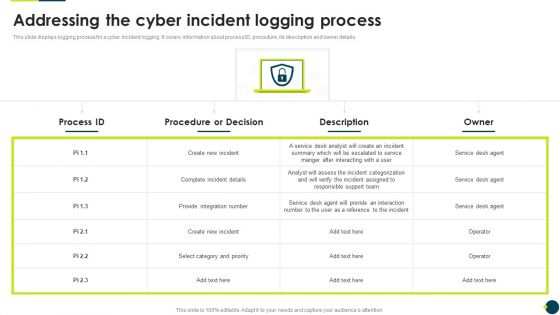
IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF. Use them to share invaluable insights on Provide Integration, Responsible Support, Assess The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.This is a IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Incidents, Security Attacks, Common Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
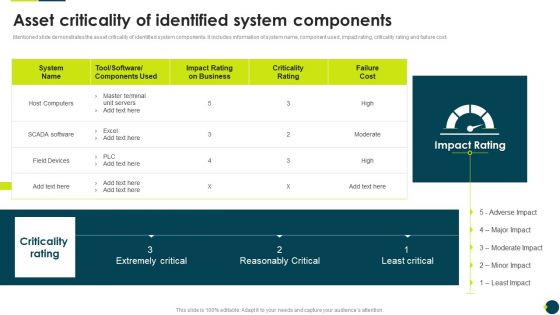
IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF. Use them to share invaluable insights on Master Terminal, Extremely Critical, Reasonably Critical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
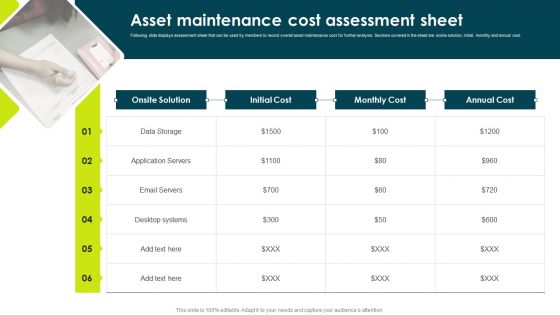
IT Threats Response Playbook Asset Maintenance Cost Assessment Sheet Clipart PDF
Following slide displays assessment sheet that can be used by members to record overall asset maintenance cost for further analysis. Sections covered in the sheet are onsite solution, initial, monthly and annual cost.This is a IT Threats Response Playbook Asset Maintenance Cost Assessment Sheet Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Servers, Desktop Systems, Onsite Solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.Presenting IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Differential, Incremental, Differential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
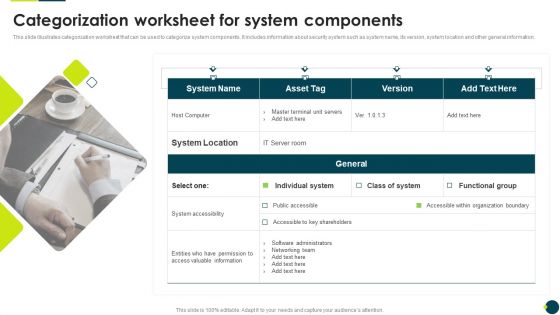
IT Threats Response Playbook Categorization Worksheet For System Components Graphics PDF
This slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information.Presenting IT Threats Response Playbook Categorization Worksheet For System Components Graphics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like System Accessibility, Valuable Information, Organization Boundary. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF bundle. Topics like Safeguard Sensitive, Strong Passwords, Exchange Encrypted can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF. Use them to share invaluable insights on External Issues, Audio Steganography, Malware Injection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.