It risks PowerPoint Presentation Templates and Google Slides
-
Effective IT Risk Management Process Employee Training Schedule Formats PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative effective it risk management process employee training schedule formats pdf bundle. Topics like employee training schedule can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
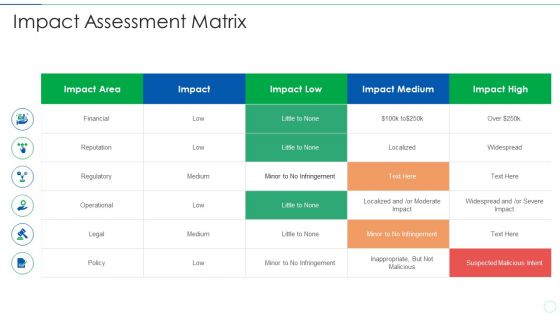
Effective IT Risk Management Process Impact Assessment Matrix Sample PDF
Deliver and pitch your topic in the best possible manner with this effective it risk management process impact assessment matrix sample pdf. Use them to share invaluable insights on impact assessment matrix and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Effective IT Risk Management Process Incident Management Tool We Will Use Professional PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative effective it risk management process incident management tool we will use professional pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Effective IT Risk Management Process Information Security Risk Clipart PDF
Deliver and pitch your topic in the best possible manner with this effective it risk management process information security risk clipart pdf. Use them to share invaluable insights on equipment, software application, service denial, valuable information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
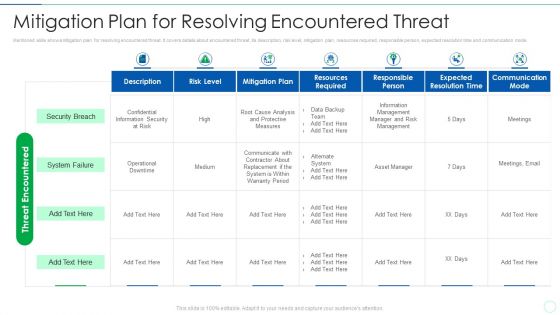
Effective IT Risk Management Process Mitigation Plan For Resolving Infographics PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an awe inspiring pitch with this creative effective it risk management process mitigation plan for resolving infographics pdf bundle. Topics like security breach, system failure, communicate, analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Effective IT Risk Management Process Present Security Management Formats PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this effective it risk management process present security management formats pdf. Use them to share invaluable insights on information, risk, security, plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Effective IT Risk Management Process Risk Reporting And Likelihood Pictures PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative effective it risk management process risk reporting and likelihood pictures pdf bundle. Topics like supply, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Effective IT Risk Management Process System Categorization Worksheet Mockup PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this effective it risk management process system categorization worksheet mockup pdf. Use them to share invaluable insights on valuable information, system location, individual system and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
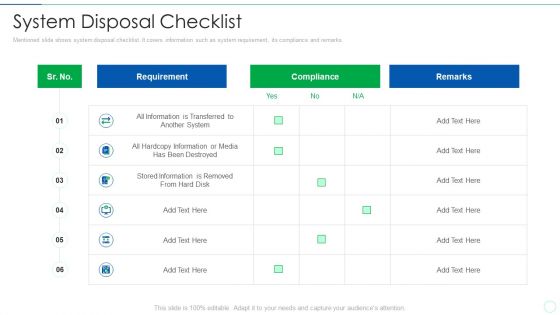
Effective IT Risk Management Process System Disposal Checklist Microsoft PDF
Mentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks. Deliver an awe inspiring pitch with this creative effective it risk management process system disposal checklist microsoft pdf bundle. Topics like information, system, requirement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Effective IT Risk Management Process System Management Checklist Brochure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this effective it risk management process system management checklist brochure pdf. Use them to share invaluable insights on security patches, data backup, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Effective IT Risk Management Process Threat Identification And Vulnerability Professional PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative effective it risk management process threat identification and vulnerability professional pdf bundle. Topics like potential vulnerability, system, network, designed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
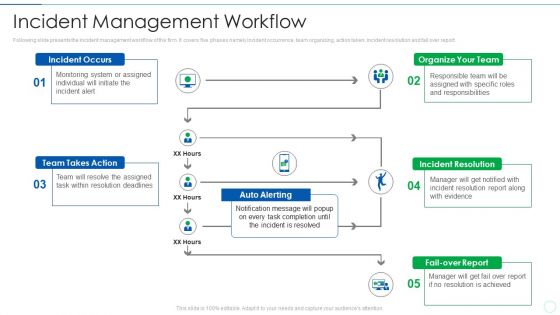
Effective IT Risk Management Process Incident Management Workflow Diagrams PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Deliver an awe inspiring pitch with this creative effective it risk management process incident management workflow diagrams pdf bundle. Topics like system, team, organize can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
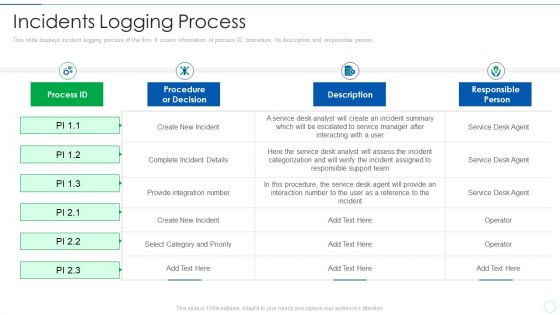
Effective IT Risk Management Process Incidents Logging Process Structure PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver and pitch your topic in the best possible manner with this effective it risk management process incidents logging process structure pdf. Use them to share invaluable insights on service, analyst and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
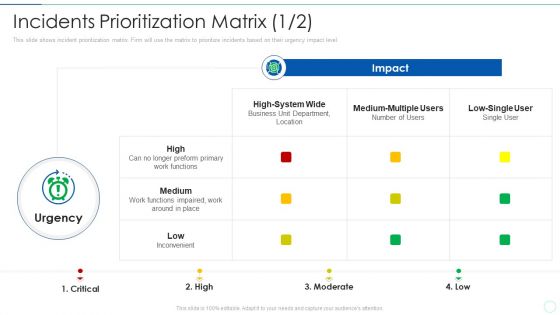
Effective IT Risk Management Process Incidents Prioritization Matrix Site Background PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative effective it risk management process incidents prioritization matrix site background pdf bundle. Topics like incidents prioritization matrix can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
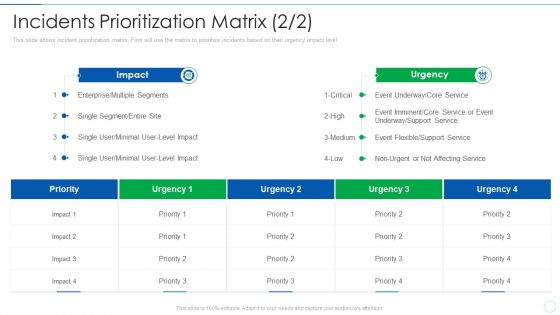
Effective IT Risk Management Process Incidents Prioritization Matrix Summary PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver and pitch your topic in the best possible manner with this effective it risk management process incidents prioritization matrix summary pdf. Use them to share invaluable insights on business, location, system and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
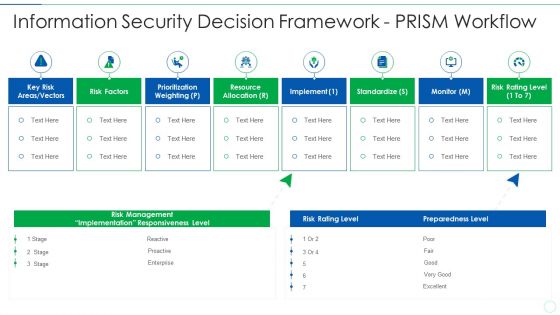
Effective IT Risk Management Process Information Security Decision Template PDF
Presenting effective it risk management process information security decision template pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like implement, resource allocation, risk factors, standardize. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Effective IT Risk Management Process Information Security Risk Assessment Formats PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this NAMEEEEEE. Use them to share invaluable insights on system failure, potential, vulnerability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Effective IT Risk Management Process Introducing Information Security Risk Designs PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an awe inspiring pitch with this creative effective it risk management process information security risk assessment formats pdf bundle. Topics like system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Effective IT Risk Management Process Multitiered Risk Management Microsoft PDF
Presenting effective it risk management process multitiered risk management microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like orgnization, business processes, information systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Icons Slide For Effective Effective IT Risk Management Process Themes PDF
Presenting our innovatively structured icons slide for effective effective it risk management process themes pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
-
Table Of Contents For Effective IT Risk Management Process Summary PDF
Deliver and pitch your topic in the best possible manner with this table of contents for effective it risk management process summary pdf. Use them to share invaluable insights on management, matrix, system, security, analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
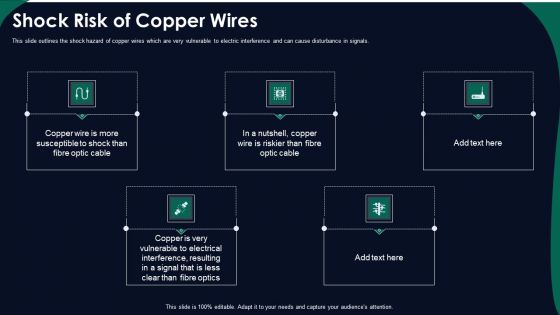
FDDI Network Standard IT Shock Risk Of Copper Wires Ppt Professional Smartart PDF
This slide outlines the shock hazard of copper wires which are very vulnerable to electric interference and can cause disturbance in signals. This is a fddi network standard it shock risk of copper wires ppt professional smartart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like shock risk of copper wires. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Cios Initiative 9 Implementing IT Risk Management Framework Ppt PowerPoint Presentation File Maker PDF
This slide provides information regarding implementation of IT risk management framework with immediate, short term and long term initiatives. Deliver and pitch your topic in the best possible manner with this cios initiative 9 implementing it risk management framework ppt powerpoint presentation file maker pdf. Use them to share invaluable insights on security processes, control environment, enterprise security programand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
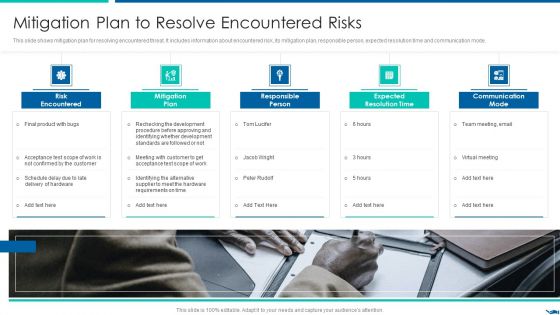
Project QA Through Agile Methodology IT Mitigation Plan To Resolve Encountered Risks Mockup PDF
This slide shows mitigation plan for resolving encountered threat. It includes information about encountered risk, its mitigation plan, responsible person, expected resolution time and communication mode.This is a Project QA Through Agile Methodology IT Mitigation Plan To Resolve Encountered Risks Mockup PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Encountered, Mitigation Plan, Responsible Person You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Project QA Through Agile Methodology IT Risk Event Assessment And Evaluation Form Ideas PDF
Mentioned slide displays risk assessment form covering information about project name, its reference document, project manager name, risk input, causes, assessment ratings and justification.Deliver and pitch your topic in the best possible manner with this Project QA Through Agile Methodology IT Risk Event Assessment And Evaluation Form Ideas PDF Use them to share invaluable insights on Risk Event Assessment And Evaluation Form and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Project QA Through Agile Methodology IT Checklist For Managing Project Risks Elements PDF
This slide illustrates checklist which the firm will use to effectively manage its software project risk events. Section covered in the checklist are type of risk, its description and examined or not examined status.This is a Project QA Through Agile Methodology IT Checklist For Managing Project Risks Elements PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Stakeholder Consensus, Management Methodology, Increased Cost You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Project QA Through Agile Methodology IT Determining The Occurrence Of Risk Information PDF
Following slide provides information on the occurrence of risk events and their impact on the project progress. It covers information about the risk, its probability of occurrence, risk owner, risk category and extended categories.This is a Project QA Through Agile Methodology IT Determining The Occurrence Of Risk Information PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Probability Of Risk Occurrence, Requirement Quality Performance, Extended Categories You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Project QA Through Agile Methodology IT Framework Defining Our Quality Risk Icons PDF
This slide portrays quality risk management process that firm will use in order maintain and ensure its project quality.This is a Project QA Through Agile Methodology IT Framework Defining Our Quality Risk Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Process, Initiate Quality Risk, Result Of The Quality Risk You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
IT Software Risk Assessment Report Ppt PowerPoint Presentation File Infographic Template PDF
This slide depicts risk assessment report for IT software. It covers incidents such as system failure, DDOS attack, human interference, hardware and software attack. Pitch your topic with ease and precision using this IT Software Risk Assessment Report Ppt PowerPoint Presentation File Infographic Template PDF. This layout presents information on Risk Level, Asset, Human Interference. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Fundamental PMP Elements Of IT Projects IT Project Risk Management Action Plan Mockup PDF
This slide provides information regarding project risk management action plan that will help in keeping the track of potential risk that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this fundamental pmp elements of it projects it project risk management action plan mockup pdf. Use them to share invaluable insights on potential risk, risk level, reason for risk rating, action, required resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
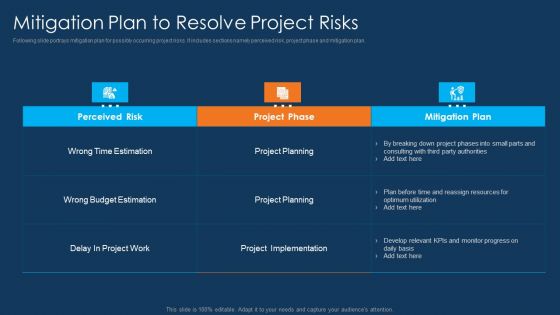
Information Technology Project Initiation Mitigation Plan To Resolve Project Risks Topics PDF
Following slide portrays mitigation plan for possibly occurring project risks. It includes sections namely perceived risk, project phase and mitigation plan. Deliver an awe inspiring pitch with this creative information technology project initiation mitigation plan to resolve project risks topics pdf bundle. Topics like perceived risk, project phase, mitigation plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Information Technology Project Initiation Possible Project Risks And Their Significance Clipart PDF
This slide portrays information about possible project risk occurrence likelihood and their significance. It includes sections namely possible risk, project phase, impact, likelihood and significance. Deliver an awe inspiring pitch with this creative information technology project initiation possible project risks and their significance clipart pdf bundle. Topics like possible risk, project phase, project planning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Information Privacy IT Risk Evaluation Dashboard For Data Privacy Ideas PDF
This slide depicts the risk evaluation dashboard for data privacy based on audits with open findings, GDPR processing per region, control and measure trends, average response time. Deliver an awe inspiring pitch with this creative information privacy it risk evaluation dashboard for data privacy ideas pdf bundle. Topics like risk evaluation dashboard for data privacy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
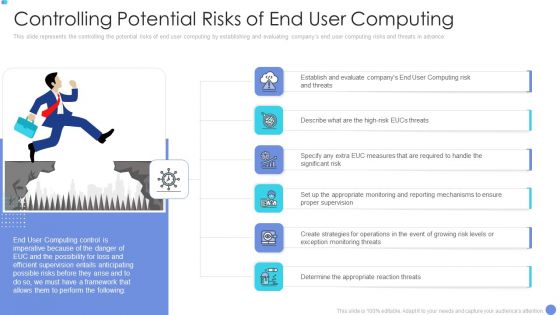
Customer Mesh Computing IT Controlling Potential Risks Of End User Computing Structure PDF
This slide represents the controlling the potential risks of end user computing by establishing and evaluating companys end user computing risks and threats in advance. Presenting customer mesh computing it controlling potential risks of end user computing structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like controlling potential risks of end user computing. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Customer Mesh Computing IT Potential Risks Of End User Computing Summary PDF
This slide depicts the challenges of end user computing and it includes time sharing, enter virtualization, enter PC, re aggregation and complexity reigns supreme. Presenting customer mesh computing it potential risks of end user computing summary pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like time sharing, complexity reigns supreme, enter virtualization. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
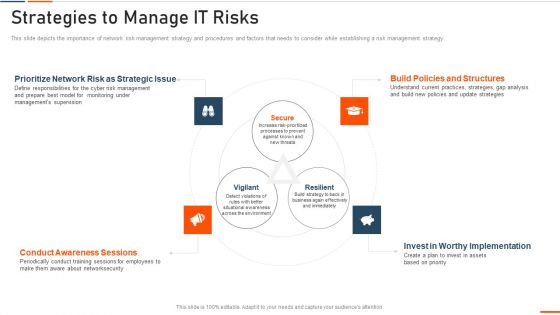
Information Technology Security Strategies To Manage IT Risks Ppt Infographic Template Guidelines PDF
This slide depicts the importance of network risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information technology security strategies to manage it risks ppt infographic template guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct awareness sessions, invest in worthy implementation, build policies and structures, prioritize network . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Digitized Record Book Technology Risks Involved In Public Digital Ledger Infographics PDF
This is a digitized record book technology risks involved in public digital ledger infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, requires, costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
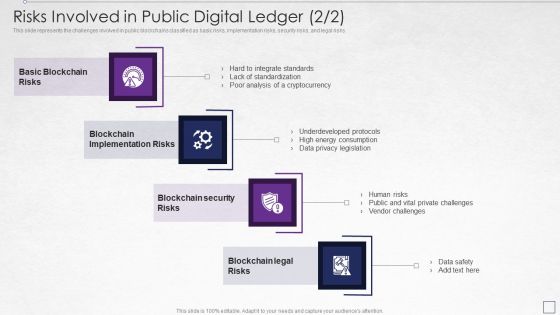
Digitized Record Book Technology Risks Involved In Public Digital Ledger Risks Brochure PDF
This slide represents the challenges involved in public blockchains classified as basic risks, implementation risks, security risks, and legal risks. This is a digitized record book technology risks involved in public digital ledger risks brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, risks, security, analysis, underdeveloped protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Gap Identification Current Approach Process Flaws And Cost Risk Based Procedures To IT Security Topics PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. This is a Gap Identification Current Approach Process Flaws And Cost Risk Based Procedures To IT Security Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cyberrisk Management, Security Organization, Formation Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Addressing The Companies Digitization Levels By Sectors Infographics PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Addressing The Companies Digitization Levels By Sectors Infographics PDF bundle. Topics like Digital Spend, Digitalization Level, Business Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
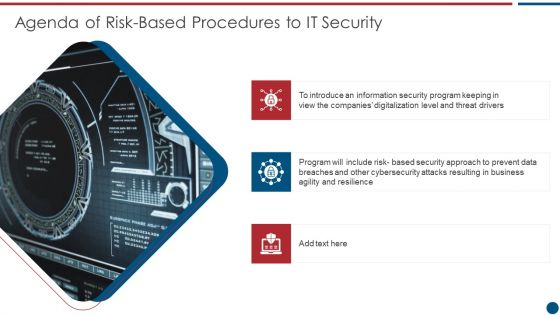
Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF
This is a Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Program Keeping, Threat Drivers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Major Components, Criticality Rating, Failure Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Risk Management, Transparent Communication, Standardized Incident. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
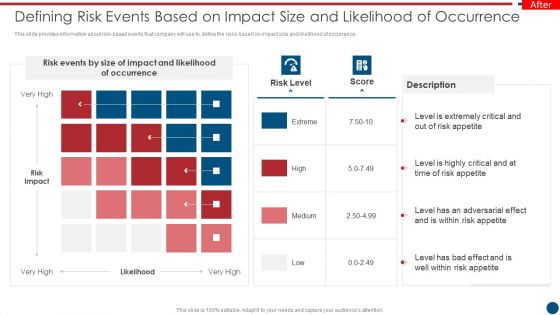
Risk Based Procedures To IT Security Defining Risk Events Based On Impact Size And Likelihood Summary PDF
This slide provides information about risk-based events that company will use to define the risks based on impact size and likelihood of occurrence. This is a Risk Based Procedures To IT Security Defining Risk Events Based On Impact Size And Likelihood Summary PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Events, Risk Impact, Risk Appetite. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manual Vulnerability, Vulnerability Scanning, Automation Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF
Mentioned slide displays a five-day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF bundle. Topics like Assess Security, Gap Analysis, Gap Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Based Procedures To IT Security Encountered Risks Summary And Their Impact Assessment Topics PDF
Mentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Encountered Risks Summary And Their Impact Assessment Topics PDF. Use them to share invaluable insights on Risks Category, High Inherent, Risk Magnitude and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
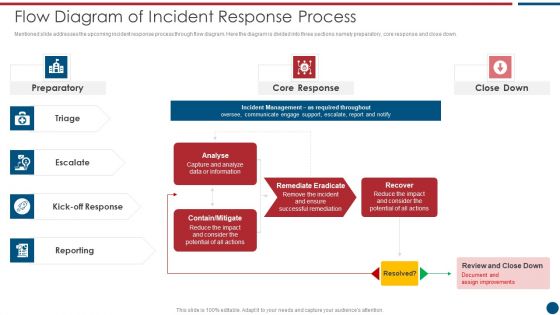
Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF bundle. Topics like Cyberrisk Management, Security Organization, Technology Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. This is a Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Leadership, Evaluation Direction, Change Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
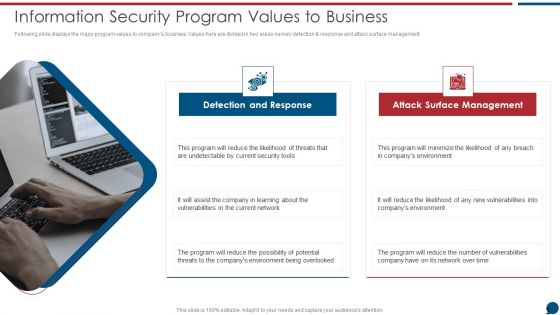
Risk Based Procedures To IT Security Information Security Program Values To Business Infographics PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting Risk Based Procedures To IT Security Information Security Program Values To Business Infographics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Detection Response, Attack Surface, Current Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. This is a Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Desk, Support Team, Provide Integration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
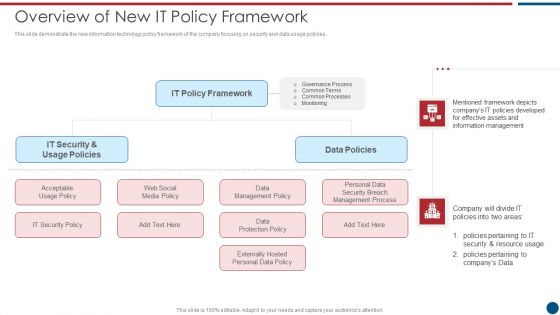
Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like IT Policy, Data Policies, IT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
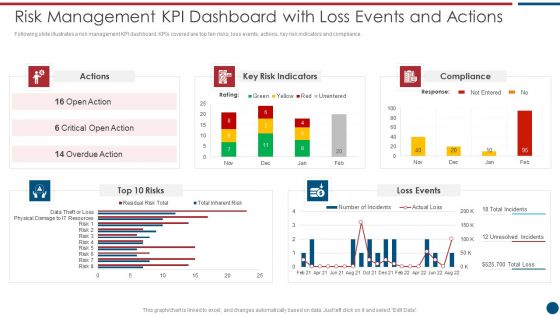
Risk Based Procedures To IT Security Risk Management KPI Dashboard With Loss Events And Actions Mockup PDF
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Risk Management KPI Dashboard With Loss Events And Actions Mockup PDF bundle. Topics like Key Risk, Indicators Compliance, Loss Events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.